Advances in Social Media Research: Past, Present and Future
- Open access
- Published: 06 November 2017
- Volume 20 , pages 531–558, ( 2018 )

Cite this article
You have full access to this open access article

- Kawaljeet Kaur Kapoor 1 ,
- Kuttimani Tamilmani 2 ,
- Nripendra P. Rana 2 ,
- Pushp Patil 2 ,
- Yogesh K. Dwivedi 2 &
- Sridhar Nerur 3
452k Accesses
671 Citations
21 Altmetric
Explore all metrics
Social media comprises communication websites that facilitate relationship forming between users from diverse backgrounds, resulting in a rich social structure. User generated content encourages inquiry and decision-making. Given the relevance of social media to various stakeholders, it has received significant attention from researchers of various fields, including information systems. There exists no comprehensive review that integrates and synthesises the findings of literature on social media. This study discusses the findings of 132 papers (in selected IS journals) on social media and social networking published between 1997 and 2017. Most papers reviewed here examine the behavioural side of social media, investigate the aspect of reviews and recommendations, and study its integration for organizational purposes. Furthermore, many studies have investigated the viability of online communities/social media as a marketing medium, while others have explored various aspects of social media, including the risks associated with its use, the value that it creates, and the negative stigma attached to it within workplaces. The use of social media for information sharing during critical events as well as for seeking and/or rendering help has also been investigated in prior research. Other contexts include political and public administration, and the comparison between traditional and social media. Overall, our study identifies multiple emergent themes in the existing corpus, thereby furthering our understanding of advances in social media research. The integrated view of the extant literature that our study presents can help avoid duplication by future researchers, whilst offering fruitful lines of enquiry to help shape research for this emerging field.
Similar content being viewed by others

Social Media as Online Information Grounds: A Preliminary Conceptual Framework

Bright ICT: Social Media Analytics for Society and Crisis Management

A Literature Review on Application Areas of Social Media Analytics
Explore related subjects.
- Artificial Intelligence
Avoid common mistakes on your manuscript.
1 Introduction
Social media allows relationship forming between users from distinct backgrounds, resulting in a tenacious social structure. A prominent output of this structure is the generation of massive amounts of information, offering users exceptional service value proposition. However, a drawback of such information overload is sometimes evident in users’ inability to find credible information of use to them at the time of need. Social media sites are already so deeply embedded in our daily lives that people rely on them for every need, ranging from daily news and updates on critical events to entertainment, connecting with family and friends, reviews and recommendations on products/services and places, fulfilment of emotional needs, workplace management, and keeping up with the latest in hashion, to name but a few.
When we refer to social media, applications such as Facebook, WhatsApp, Twitter, YouTube, LinkedIn, Pinterest, and Instagram often come to mind. These applications are driven by user-generated content, and are highly influential in a myriad of settings, from purchasing/selling behaviours, entrepreneurship, political issues, to venture capitalism (Greenwood and Gopal 2015 ). As of April 2017, Facebook enjoys the exalted position of being the market leader of the social media world, with 1.97 billion monthly users (Statista 2017 ). In addition to posts, social media sites are bombarded with photo and video uploads, and according to the recent numbers, about 400 million snaps a day have been recorded on Snapchat, with around 9000 photos being shared every second (Lister 2017 ). While 50 million businesses are active on Facebook business pages, two million businesses are using Facebook advertising. Apparently, 88% businesses use Twitter for marketing purposes (Lister 2017 ).
Academics and practitioners have explored and examined the many sides of social media over the past years. Organizations engage in social media mostly with the aim of obtaining feedback from stakeholders (Phang et al. 2015 ). Consumer reviews are another big part of social media, bringing issues of information quality, credibility, and authenticity to the forefront. To a large extent, online communities have been successful in bringing together people with similar interests and goals, making the concept of micro blogging very popular. While most messages exchanged on social media sites are personal statuses or updates on current affairs, some posts are support seeking, where people are looking for assistance and help. Interestingly, these have been recognized as socially exhausting posts that engender social overload, causing other members to experience negative behavioural and psychological consequences, because they feel compelled to respond (Maier et al. 2015a ).
Given the relevance of social media to various stakeholders, and the numerous consequences associated with its use, social media has attracted the attention of researchers from various fields, including information systems. This is evidenced by the large number of scholarly articles that have appeared in various outlets. Researchers have to expend an enormous amount of time and effort in collating, analysing, and synthesising findings from existing works before they embark on a new research project. Given the significant number of studies that have already been published, a comprehensive and systematic review can offer valuable assistance to researchers intending to engage in social medi research. Our literature search suggests that there are reviews on social media in the marketing context (see for example, AlAlwan et al. 2017 ; Dwivedi et al. 2017a ; Dwivedi et al. 2015 ; Ismagilova et al. 2017 ; Kapoor et al. 2016 ; Plume et al. 2016 ). However, there exists no comprehensive review that integrates and synthesises the findings from the articles published in Information Systems journals. Such an endeavour will not only provide a holistic view of the extant research on social media, but will also provide researchers a comprehensive intellectual platform that can be used to pursue fruitful lines of enquiry to help advance research in this rapidly expanding area. To fulfill this goal, this study reviewed relevant articles to elucidate the key thematic areas of research on social media, including its benefits and spill-over effects. The resulting review is expected to serve as a one-stop source, offering insight into what has been accomplished so far in terms of research on social media, what is currently being done, and what challenges and opportunities lie ahead. By doing so, this study explores the following aspects of existing research on social media:
How is social media defined in the IS literature?
How has social media literature evolved from a multidisciplinary perspective?
How have social media technologies, applications, practices, and research evolved over the past 20 years?
Which social media issues and themes have already been examined in IS research?
What are the major limitations of extant literature on social media?
The next section of this paper gives a brief overview of the method employed for carrying out the literature search. The succeeding section discusses citation and text analyses of social media publications. Subsequently, we outline the various ways in which scholars have defined social media. This is followed by a section that focuses on the evolution of social media research from an IS perspective. Next, we articulate the major themes emerging from prior research and use them as a backdrop for our review of the literature on social media. The ensuing section discusses our findings, followed by key conclusions and limitations of the study.
2 Literature Search Method
The literature search for this analysis was conducted in the following two phases: (1) keyword-based search and analysis to explore the overall evolution of social media literature; and (2) manual search across specific IS journals to understand the emerging IS perspectives on this topic.
2.1 Keywords Based Search and Analysis
In order to gain a deeper understanding of social media, we analyzed relevant abstracts that were downloaded from the Web of Science (WOS) database. Our search terms Footnote 1 yielded a total of 13,177 records, out of which 12,597 unique abstracts were obtained. The analysis of these records was undertaken in two steps. First, we used VOSviewer (Van Eck and Waltman 2011 ) to perform a co-citation analysis of first authors in the downloaded corpus. VOSviewer allows visualization of similarities in publications and authors through an examination of bibliometric networks. Furthermore, we used VOSviewer to analyze words derived from titles and abstracts. Second, we used Latent Dirichlet Allocation (LDA) (see Blei 2012 ) to extract key thematic areas latent in the literature on social media. Further details about these analyses and results are presented in section 3 .
2.2 Manual Search and Analysis
Given the inconsistencies in the use of keywords in social media research, a manual search, rather than a keyword-based one, was deemed to be more appropriate for identifying the existing literature on social media. Furthermore, since keywords in the social media literature tend to overlap with topics and/or theories in other related research areas, a keyword search may yield irrelevant articles. For instance, a keyword search for “Social network” returns articles related to social network theories, which are not necessarily part of social media. The articles reviewed in this study are from the following eight Senior Scholars’ Basket of Information Systems journals: European Journal of Information Systems (EJIS); Information Systems Journal (ISJ); Information Systems Research (ISR); Journal of the Association for Information Systems (JAIS); Journal of Information Technology (JIT); Journal of Management Information Systems (JMIS); Journal of Strategic Information Systems (JSIS) and Management Information Systems Quarterly (MISQ)). Along with these eight journals, we have also analysed relevant articles from Information Systems Frontier (ISF) journal. This is because it focuses on examining “new research and development at the interface of information systems (IS) and information technology (IT) from analytical, behavioural, and technological perspectives. It provides a common forum for both frontline industrial developments as well as pioneering academic research”. Footnote 2 ISF enjoys the reputation of a high quality journal across continents. For example, a journal quality ranking by Chartered Association of Business Schools, UK, has given it a three star (high ranking) quality rating, while journal ranking by the Australian Business Deans Council (ABDC) has rated it as an ‘A’ class journal (the second highest quality journal category after A*, which is reserved for premier publications). In light of these observations, it was deemed appropriate to consider articles from ISF along with the aforementioned eight journals.
Relevant articles were then identified and downloaded from each of the target journals by going through their archives. Specifically, all volumes and issues published in these journals between 1997 and 2017 were considered in our analysis. Articles, research notes, introductions, research commentaries, and editorial overviews relevant to social media were downloaded and numbered to prepare an APA style reference list. The first literature search resulted in 181 articles that had some relevance to the social media domain. A closer examination of individual abstracts and full articles led to the elimination of 49 irrelevant articles, thus giving us a total of 132 articles pertinent to the domain of interest (i.e., social media).
3 Citation and Text Analyses of Social Media Publications
3.1 author co-citation analysis (aca).
Author Co-Citation Analysis (ACA) is a bibliometric technique that has been widely used to explicate the conceptual structure of disciplines (for example, see White and Griffith 1981 ; McCain 1984 ; Culnan 1986 ; Nerur et al. 2008 ). The underlying assumption in ACA is that authors who are frequently cited together tend to work on similar concepts. Thus, frequently co-cited authors are likely to cluster together when an ACA is performed. VOSviewer considers only first authors when it performs ACA. Only authors who had 50 or more citations were included in the analysis. Figure 1 shows the results of ACA.
Author clusters from ACA
VOSviewer identified seven distinct clusters:
Cluster 1: Authors in this cluster have contributed to research on Twitter (e.g., Sakaki), social network analysis (e.g., Wasserman), topic modeling (e.g., Blei), sociality and cognition (e.g., Dunbar), sentiment analysis of tweets (e.g., Thelwall), and other related topics.
Cluster 2: Authors in this cluster are well known for their work on technology adoption (e.g., Venkatesh), diffusion of technology (Rogers), culture (Hofstede), theory of planned behavior (Ajzen), marketing/consumer behavior (e.g., Hennig-Thurau), and statistical methods (e.g., Bagozzi, Fornell, Hair).
Cluster 3: This cluster comprises of authors who deal with a variety of issues related to social media (Facebook and Twitter) use. For example, Steinfied and Ellison examined social capital across Facebook; Kuss studied online/social networking addiction (e.g., gaming addiction), and Lenhart focused on teens and technology (e.g., mobile internet use), particularly in the use of social media. Other topics include Bandura’s self-efficacy, use and benefits of Twitter by scholars, and personality and social characteristics of Facebook users (e.g., Ross).
Cluster 4: Prominent social theorists/sociologists who have contributed to social capital theory, structuration theory and modern sociological theory are distinguished members of this cluster. These include Bourdieu, Coleman, Giddens, and Habermas. Papacharissi has written about a variety of topics including the exploration of factors that predict Internet use as well as users’ behaviors, identity, sense of community and culture on social media. Tufekci has studied privacy and disclosure on social media, as well as other topics, including how social networking sites such as Facebook might influence one’s decision to participate in protests.
Cluster 5: In this cluster, there is evidence of the influence of Vygotsky’s socio cultural learning theory as well as Lave and Wenger’s work on communities of practice. In addition to his work on collaborative learning, Kirschner has examined the relationship between Facebook and academic performance. Likewise, Selwyn has explored pedagogical and learning engendered by the use of information and computer technologies (ICT).
Cluster 6: This cluster appears to reflect two broad themes. The first is a range of topics related to medical Internet research, broadly referred to as e-health (Eysenbach) or online health (Duggan). Themes in this category include electronic support groups and health in virtual communities (Eysenbach), and policies and healthcare associated with social media, and professionals among medical students and physicians in the use of social media (Chretien, Greysen). The second main thematic area in this cluster deals with scholarship on social media, scholarly communication, and metrics for evaluating impact of articles on the web (e.g., Weller, Bormann, Priem).
Cluster 7: The dominant theme here is the nature and content of communication. In particular, scholars in this cluster have focused on communication and response in the face of crises (Coombs), including image restoration after a controversy (Benoit), analysis and reliability of content (Krippendorff), and the use of social media sites such as Facebook and Twitter by government agencies and non-profit organizations to engage stakeholders (Waters).
3.2 Text Analysis of Words in Titles and Abstracts
VOSviewer was used to analyze terms (i.e., words) in the titles and abstracts of our corpus to obtain a two-dimensional map showing proximities of words that are likely to be related based on their co-occurrences. Specifically, VOSviewer relies on the Apache OpenNLP Toolkit to identify noun phrases, and then compares their overall co-occurrence distribution with their distribution across other noun phrases to compute a relevance score (Van Eck and Waltman 2011 ). The intuition is that frequently co-occurring noun phrases with high relevance are likely to unravel a topic or theme that is latent in the corpus. The term map from VOSviewer is shown in Fig. 2 . Only terms that occurred 50 times or more were included. Furthermore, relevance scores computed by VOSviewer for every term were used to select the top 80% that met the threshold.
Term map showing clusters of related words/noun phrases
VOSviewer identified five clusters here. It is evident from the clusters that research on social media has dealt with a broad range of topics, including but not restricted to diffusion of information and opinions, spread of diseases (e.g., influenza), identification of social and emotional health concerns and attendant interventions to deal with them, social media as an influence, the use of social media for marketing purposes, and the implications of social media as a tool for pedagogy (i.e., teaching and learning) and medical practice. These have been summarized in Table 1 .
It must be noted that the topics are broad and don’t reveal the nuances of research areas embodied in the abstracts examined in this study. The next sub-section presents the results of topic modeling, which has the potential to unravel more focused themes embodied in the large corpus that we analyzed.
3.3 Topic Modeling
The fact that our search terms yielded over 12,000 abstracts suggests that scholars are investing increased interest on research issues related to social media. While an informed researcher may have a general idea of the nature of research undertaken so far, it is humanly impossible to discern the thematic structure of all scholarly documents available on social media. Recent advances in topic modeling have made this task relatively easy. Topic modeling relies on algorithms and statistical methods to elicit the topics latent in a large corpus (Blei 2012 ). The term topic refers to a specific and often recognizable theme defined by a cohesive set of words that have a high probability of belonging to that topic. There are several options available for topic modeling: non-negative matrix factorization (NNMF), Latent Semantic Analysis/Indexing (LSA/LSI), and Latent Dirichlet Allocation (LDA). In this study, we use LDA, arguably the most widely used topic modeling algorithm. In order to perform topic modeling on a corpus, the researcher has to specify the number of topics to be extracted. In this study, we extracted the top 100 topics reflected in the scholarship on social media. LDA starts with the assumption that each abstract in our study reflects each of these topics to varying degrees (Blei 2012 ). Thus, each abstract has a distribution of the desired 100 topics. The 100 topics that were extracted from our abstracts are shown in Table 2 . The machine learning for language toolkit (MALLET) (McCallum 2002 ) was used for this purpose.
4 Analysis of Social Media Research from an IS Perspective
4.1 how is social media defined in the is literature.
In studying the existing literature on social media, it becomes apparent that the authors in this field have not focussed on defining social media. Of all the studies included in this review, only a handful of studies have come close to defining, or clarifying the concept of social media. For instance, Lundmark et al. ( 2016 , p3) suggest, “social media, as a unique form of communication, integrates multiple sources of legitimacy, and as a result, presents a unique and important context through which to study the topic. Indeed, social media are a means for the dissemination of both internally and externally generated information pertaining to firms, industries, and society in general.” According to Schlagwein and Hu ( 2016 ), social media constitutes internet-based communication and collaboration channels, widely in use since 2005, and, from an IS perspective, social media tools and their surrounding organizational and managerial structures constitute social information systems. Wakefield and Wakefield ( 2016 , p140) describe “social media technologies as an ensemble IS artefact composed of technical, informational, and relational subsystems that interact distinctly according to the context of use.” In their study, they also identify a “recent definition of social media and social networks referring to social media networks as specific types of social media platforms and Internet sites with common attributes such as (1) user profile (2) user access to digital content (3) a user list of relational ties, and (4) user ability to view and traverse relational ties” (Wakefield and Wakefield 2016 ; p144).
In a more relatable and simple definition, Miranda et al. ( 2016 ; p304) explain social media being “mainly conceived of as a medium wherein ordinary people in ordinary social networks (as opposed to professional journalists) can create user-generated news.” A few other authors like Spagnoletti et al. ( 2015 ) and Xu and Zhang ( 2013 ) commonly refer to social media as a set of interned-based technologies/applications, which are aimed at promoting the creation, modification, update and exchange of user-generated content, whilst establishing new links between the content creators themselves. Bharati et al. ( 2014 ; p258) refer to social media as a technology “not focussed on transactions but on collaboration and communication across groups both inside and outside the firm.” Lastly, Tang et al. ( 2012 ; p44) also identify social media as user-generated media, which is a source of “online information created, initiated, circulated, and used by consumers intent on educating each other about products, brands, services, personalities, and issues.”
All of the aforementioned descriptions clearly regard social media as communication tools supported by internet-based technologies for dissemination of information. Most of them acknowledge the high concentration of user generated content across such platforms. Based on our understanding of social media and the aforementioned definitions, we propose the following definition: Social media is made up of various user-driven platforms that facilitate diffusion of compelling content, dialogue creation, and communication to a broader audience. It is essentially a digital space created by the people and for the people, and provides an environment that is conducive for interactions and networking to occur at different levels (for instance, personal, professional, business, marketing, political,and societal) .
4.2 Evolution of Social Media Research in the IS Literature
In the past two decades, various issues related to social media have been examined in line with the rapid evolution of underlying technologies/applications and their appropriation to enable different types of social media usage. An analysis of 132 articles from selected IS journals suggests that publications until 2011 were still examining user-generated content as a new type of online content (Burgess et al. 2011 ). However, in the last six years, research in this field has made tremendous progress, not just in terms of its scope, but also in explicating the highs and lows associated with the use of social media. While it is difficult to pinpoint evolution on a yearly basis, it has been possible to identify the major aspects of social media research that have emerged over time. Publications between 1997 and 2017 have been reviewed here. Interestingly, only one publication of interest to this study (Griffiths and Light 2008 ) was identified between the period 1997 and 2009.
Out of the 132 studies individually reviewed here, about 21 studies examined the behavioural side of social media use. While most of the initial studies (for instance, Massari 2010 ; Garg et al. 2011 ) restricted interest to peer influence and information disclosure willingness (2010–2012), the latter studies (for instance, Gu et al. 2014 ; Krasnova et al. 2015 ) were seen to be more exploratory in examining the positive, dysfunctional, cognitive and affective, heterophily and homophily tendencies of social media users (2012–2016). There were 18 studies investigating the very popular aspect of reviews and recommendations on social networks, with 2013 being a popular year for such studies. Most of these studies (for instance, Hildebrand et al. 2013 ; Zhang and Piramuthu 2016 ) were interested in improving their understanding of the information quality of these reviews and the associated consequences (2010–2016). There were 17 studies (2011–2016) evaluating the integration of social media for varied organizational purposes . While some studies investigated the employee side (e.g., innovativeness, retention, and motivation) of social media use (for instance, Aggarwal et al. 2012 ; Miller and Tucker 2013 ), the others discussed the relationship between social enterprise systems and organizational networking (for instance, Trier and Richter 2015 ; Van Osch and Steinfield 2016 ).
Around 13 publications studied the use of social media as a marketing tool . The early studies here (2010–2013) explored consumer purchase behaviour and firm tactics, such as involving consumers in marketing strategies (for instance, García-Crespo et al. 2010 ; Goh et al. 2013 ). The later studies (2015–2016), however, became more focussed on studying social commerce across networking sites such as Facebook, MySpace, and YouTube (e.g., Chen et al. 2015 ; Sung et al. 2016 ). Ten studies were interested in online communities and blogging (see Singh et al. 2014 ; Dennis et al. 2016 ). These were mostly interested in blogger behaviours, reader retention, online content, contributing capacity, and blog visibility (2011–2016). Nine publications revealed the risks associated with the use of social media. These are either very early studies (2008–2010; for instance, Tow et al. 2010 ) or fairly recent (2014–2016) learning about scamming and farcing issues faced by users. They focus on combating issues of privacy and security, whilst trying to differentiate between fake and authentic online content (for instance, Zhang et al. 2016 ).
Up until 2015, about eight studies analysed the negative stigma attached to using social media at the workplace (for instance, Koch et al. 2013 ). While a couple of studies also revealed the positive side of social media (for instance, Lu et al. 2015 ), most were seen discussing its ill-effects on work outputs, routine performance, and clash of notions in the personal and professional space (for instance, Ali-Hassan et al. 2015 ). About seven studies were interested in exploring the relationship between social media use and value creation (for instance, Luo et al. 2013 ; Barrett et al. 2016 ) in terms of firm equity, customer retention, social position, and firm value (2010–2016). Another seven studies investigated the use of media sites to share and exchange information during natural disasters and critical events (2011–2015). Interestingly, most of the studies documenting this aspect of social media used Twitter data for their analyses (for instance, Oh et al. 2013 ; Lee et al. 2015a ). A very small percentage of studies (five studies) in 2014 and 2015 focussed on analysing the effects of social media posts that were seeking help/support from other social media users (for instance, Spagnoletti et al. 2015 ; Yan et al. 2015a ). Only a handful of studies (five studies), particularly in 2010 and 2016, were examined the use of social media in public administration and political contexts, such as open governance and transparency (for instance, Baur 2017 ; Rosenberger et al. 2017 ). Also, just about three studies (Wattal et al. 2010 ; Dewan and Ramaprasad 2014 ; Miranda et al. 2016 ) dedicated their efforts to comparing traditional media with social media . The last set of studies (2013–2016), around nine in total (for instance, Bharati et al. 2014 ; Chung et al. 2017 ), were identified as those limiting themselves to developing and testing social media constructs in relation to previously established theories and models (technology acceptance model, theory of planned behaviour, and others).
4.3 Literature Synthesis
As outlined in the previous section, social media research is evolving at a fast pace. In reviewing the shortlisted articles, various themes were identified based on the similarities observed across the issues addressed in social media research.
4.3.1 Social Media Use Behaviours and Consequences
Many scholars explore the behavioural side of social media, and interestingly, some find factors that prevent users from continuing its use. Turel and Serenko ( 2012 ) warn against excessive use of social media sites, which can result in strong pathological and maladaptive psychological dependency on social media. In a subsequent study, Turel ( 2015 ) used cognitive theory to reveal that guilt feelings associated with the use of a website can increase discontinuance intentions. Matook et al. ( 2015b ) show that online social networks can be linked with perceived loneliness, which depends on user’s active/passive engagement with social media. Krasnova et al. ( 2015 ) suggest that in response to social information consumption, envy plays a significant role in reducing cognitive and affective wellbeing of a user. However, Maier et al. ( 2015b ) disclose that, while social networking stress creators can increase discontinuance intentions, switching stress-creators and exhaustion (i.e. switching to alternatives) can reduce such intentions. Chang et al. ( 2014 ) find that dissatisfaction and regret, alternative attractiveness, and switching costs affect switching intentions. Xu et al. ( 2014 ) find that dissatisfaction from support and entertainment values, continuity cost and peer influence encourage switching between social networks.
Wakefield and Wakefield ( 2016 ) focus on Facebook and Twitter to show that excitement combined with passion acts as a favourable factor for increased social media engagement. Chiu and Huang ( 2015 ) use media communication theories to show that user gratification from social networking sites positively affects their social media usage intention. In studying virtual investment communities, Gu et al. ( 2014 ) reveal that despite benefits of heterophily, investors are allured by homophily in their interactions. Zeng and Wei ( 2013 ) analyse Flickr data and find that at the time of forming a social tie, members exhibit similar behaviour, which evolves differently later. Shi et al. ( 2014 ) examine retweet relationships and find that those with weak ties have a higher probability of engaging in content sharing. Kreps ( 2010 ) introduces poststructuralist critique to explore how closely an individual’s personality is reflected in their social media profile, such as Facebook.
Chen et al. ( 2014 ) find affective and continuance types of commitments to be good predictors of user behaviours on social media sites. Stieglitz and Dang-Xuan ( 2013 ) examine the relationship between user behaviour and sentiment to conclude that emotional Twitter messages have a higher retweet tendency. Khan and Jarvenpaa ( 2010 ) analyse event creation pages on Facebook to find that the social groups demonstrate differential interactive behaviour prior and post the midpoint of event creation. Chen and Sharma ( 2015 ) disclose that the extent of self-disclosure on social media sites depends on member attitude. Massari ( 2010 ) finds that MySpace users tend to disclose substantial personal details that put them at the risk of security and privacy breach. Xu et al. ( 2016 ) find that one’s image and moral beliefs combined with community policies and peer pressure act as deterrents to aggression on social media. Garg et al. ( 2011 ) measure peer influence in an online music community and find that peers can significantly increase music discovery. Susarla et al. ( 2012 ) examine video and user information dataset from YouTube, and find that the success of a video hugely depends on social interactions, which also determines its impact magnitude.
The review of studies related to this theme suggests that since 2010, IS researchers have focussed on examining the dysfunctional consequences of social media adoption, such as - addiction, stress, information overload, and others. Use behaviour was examined across a variety of platforms like Facebook, Twitter, MySpace, and Flickr. Media content, such as picture, video, and tweets have also been explored by the studies in this category.
4.3.2 Reviews and Recommendations on Social Media Sites
A predominant characteristic of social media networks is product/service reviews and recommendations. People are beginning to rely on others’ experiences, for instance, before making a purchase, visiting a place, or searching for accommodation.. Such online reviews complement product/service information. An early study on online travel information found that consumers invest higher trust in reviews published on government/tourism websites in comparison to those on a social media site (Burgess et al. 2011 ). Hwang et al. ( 2011 ) analysed the social bookmarking sites for impact of positive and negative reviews on collective wisdom and found that negative reviews are capable of stabilizing system performance. Dellarocas et al. ( 2010 ) suggest that online forums looking to increase reviews of lesser-known products should make information on previously posted reviews a less prominent feature. Cheung et al. ( 2012 ) empirically tested a consumer review website to conclude that argument quality, review consistency, and source are critical for assessing review credibility.
Chen et al. ( 2011 ) investigate the effect of moderation and reveal that the commentators generate high quality content to build a stronger reputation. Wei et al. ( 2013 ) developed a multi-collaborative filtering trust network algorithm for Web 2.0 with improved accuracy for filtering information based on user preferences and trusted peer users. Luo and Zhang ( 2013 ) refer to user-generated reviews and recommendations as consumer buzz to find that advocacy and consumer attitude can impact firm value. Hildebrand et al. ( 2013 ) use data from a European car manufacturer allowing self-designed products to reveal that feedback from other community members lessens uniqueness whilst increasing dissatisfaction. Centeno et al. ( 2015 ) address the skewed reputation rankings problem in movie ratings by suggesting the use of comparative user opinions. Ma et al. ( 2013 ) analyse data from Yelp to test bias in online reviews and find that frequent and longer reviews successfully combat such biases. Lukyanenko et al. ( 2014 ) demonstrate that participants tend to provide accurate information in classifying a phenomenon at a general level, and higher accuracy where they are allowed free form data. Shi and Whinston ( 2013 ) explore the possible impact of friend check-ins on social media, and find it has no positive effect in generating new user visits.
Goes et al. ( 2014 ) disclose that user popularity results in increased and objective reviews, while numeric ratings turn more varied and negative with it. Matook et al. ( 2015a ) use relationship theories to show that past recommendation experience, closeness, and excessive posting behaviour positively affect trust and person’s intention to act on the made recommendation. Yan et al. ( 2015b ) evaluate revisit intentions for restaurants, and find that food and service quality, price and value, and the atmosphere govern such intentions. Kuan et al. ( 2015 ) analysed Amazon reviews and observed that certain characteristics such as length, readability, valence, extremity, and reviewer credibility are more likely to be recognized. In a different study, Zhang and Piramuthu ( 2016 ) suggest that product/service information on seller’s websites are often limited, and propose a Latent Dirichlet Allocation model to reveal the useful complementary hidden information in customer reviews. In a parallel conversation, Wu and Gaytán 2013 suggest that buyers integrate product price with seller reviews in configuring their willingness to pay.
The review under this theme suggests that studies as early as 2010 focussed on evaluating the authenticity of product and service reviews/recommendations published online. Overall, these studies reveal that the effect of review volume is often moderated by a buyer’s risk attitude. Most studies identify that the combination of consumer’s interest and available reviews helps users choose products/services that offer best value to them.
4.3.3 Social Media and Associated Organizational Impact
Publications have also shown interest in investigating the effects of user-generated content on entrepreneurial behaviour. For instance, Greenwood and Gopal ( 2015 ) find that discourse in both traditional and user-generated media has a notable influence on IT firm founding rates. Lundmark et al. ( 2016 ) reveal that higher usage of Twitter, alongside follower numbers and retweets result in higher levels of under pricing for initial public offerings (IPO). Trier and Richter ( 2015 ) find that online organizational networking has many unbalanced multiplex relationships, mostly comprising of weak ties and temporal change. They attribute the uneven user contribution in social networking sites to discourse drivers and information retrievers. Schlagwein and Hu ( 2016 ) identify collaboration, broadcast, dialogue, sociability, and knowledge management as the social media types that serve varied organizational purposes. Claussen et al. ( 2013 ) study Facebook to conclude that social media networks can exercise management not only by excluding participants, but also by driving softer changes in incentive/reward systems.
Subramaniam and Nandhakumar ( 2013 ) study enterprise system users and find that integrating social media facilitates user interaction that helps embed relationship ties between virtual actors. Another study concerning social features in enterprise systems reveals that business interactions are less social, and highly context specific (Mettler and Winter 2016 ). Van Osch and Steinfield ( 2016 ) showed that the enterprise system user involved in social network posting will show differences in team boundary spanning activities based on their hierarchical position (leadership, team member, etc.). Benthaus et al. ( 2016 ) analyse Twitter data to find that social media management tools have a catalysing effect on employee output as they enrich the user engagement process. Gray et al. ( 2011 ) study the social bookmarking system to find that social diversity of information sources is a good predictor of employee innovativeness. Kuegler et al. ( 2015 ) show that using enterprise social networking within teams strongly influences task performance and employee innovativeness. Leonardi ( 2014 ) reveals that communication visibility increases meta-knowledge between organizations, which results in innovative products and services minus knowledge duplication. Aggarwal et al. ( 2012 ) interestingly reveal positive effects of negative employee posts on an organization’s reputation, given that such posts attract larger audience.
Miranda et al. ( 2015 ) suggest that diffusion of social media is based on an organization’s vision that offers a well-defined range of moves to choose from, with the freedom to improvise. Xu and Zhang ( 2013 ) regard Wikipedia as a social media platform and conclude that it improves information environment in the financial market and the value of information aggregation. Qiu et al. ( 2014 ) study prediction markets to find that users with increased social connections are less likely to invest in information acquisition from external sources. Miller and Tucker ( 2013 ) study the extent of social media managed by firms to report that most firm postings are centred on firm’s achievement and are not necessarily in clients’ interest. In summary, studies reviewed under this theme are focussed on analysing the impact of integrating social media within work roles in organizations. Effective management and utilization of social media is agreed to provoke employee activity, which helps in employee innovativeness, retention, and motivation. Studies also hint against ignoring social media engagement, which can reportedly have a negative impact on a company’s image.
4.3.4 Social Media for Marketing
Social media sites are now a huge part of marketing tactics, and the documented studies are a good showcase of the extent to which social media is being integrated in marketing strategies. García-Crespo et al. ( 2010 ) study the continuous interaction between customers and organizations, as it impacts the social web environment with implications for marketing and new product development. Goh et al. ( 2013 ) study the user and market generated content for engagement in social media brand community to find that it has a positive impact on purchase expenditures. Rishika et al. ( 2013 ) demonstrate how higher social media activity directly correlates with higher participation and customer patronage. Aggarwal and Singh ( 2013 ) find that blogs help managers with their products in the screening stage, and also offer leverage in negotiating better contract terms. Dou et al. ( 2013 ) research optimizing the strength of a network by adjusting the embedded social media features with the right market seeding and pricing strategies.
Oestreicher-Singer and Zalmanson ( 2013 ) reveal that the firms are more viable when they integrate social media in purchase and consumption experience, rather than using it as a substitute for soft online marketing. Lee et al. ( 2015b ) study the importance of social commerce in marketplace to find that Facebook likes increase sales, drive traffic, and introduce socialization in the shopping experience. Xie and Lee ( 2015 ) scan purchase records on Facebook to find that exposure to owned and earned social media activities positively impacts consumers’ likeliness to purchase brands. Chen et al. ( 2015 ) study music sales on MySpace to find that broadcasting, timing and content of the personal message has significant effect on sales. Qiu et al. ( 2015 ) study YouTube data to find that learning and network mechanisms statistically and economically impact video views. Sung et al. ( 2016 ) use Facebook data of universities and colleges across the US to show that people in the same class year or same major tend to form denser groups/networks. In a slightly different study, Oh et al. ( 2016 ) investigate the pricing models for an online newspaper, and find that charging for previously free online content has a disproportionate impact on word of mouth for niche and popular topics/articles. Susarla et al. ( 2016 ) find that social media initiatives succeed when a sustained conversation with likely adopters is maintained.
Studies within this theme focus on the role of community structure and structural patterns in using social media for marketing purposes. For successful social media implementation, it is important to effectively incorporate social computing with content delivery in the digital content industry with growing user population. Most studies identify meaningful conversations with customers as an important attribute of social media marketing. Also, identifying specific customer segments across social media site, for instance, members of a forum/group or organization, helps e-marketers to target specific customers based on demographic patterns and similar interests.
4.3.5 Social Media and Participation in Online Communities
There are many facets to developing and maintaining an online community, and user participation plays an integral role in it. Ray et al. ( 2014 ) identify that user engagement increases user intention to revisit an online community. Singh et al. ( 2014 ) analyse employee blog reading behaviour and show how reader attraction and retention are influenced by textual characteristics that appeal to reader sentiments. Butler and Wang ( 2012 ) find that changing content in an online discussion community affects member dynamics and community responsiveness, both positively and negatively. An early study on participation in online communities finds that different community commitments impact behaviours differently (Bateman et al. 2011 ). Chau and Xu ( 2012 ) develop a framework capable of gathering, extracting, and analyzing blog information that can be applied to any organization, topic, or product/service.
Goes et al. ( 2016 ) study goal setting and status hierarchy theories to find that glory-based incentives motivate users to contribute more user-generated content only before/until the goal is reached, with the contribution dropping significantly later. Khansa et al. ( 2015 ) examine Yahoo! Answers, and find that artefacts like incentives, membership tenure, and habit or past behaviour hugely influence active online participation. Tang et al. ( 2012 ) examine the concept of incentives on social media, particularly YouTube, for content contribution and find that a user is driven to contribute on social media based on their desire for revenue sharing, exposure, and reputation. Zhang and Wang ( 2012 ) use economic and social role theories in a Wikipedia context to show that in a collaborative network, the editor determines the total contribution towards collaborative work. Dennis et al. ( 2016 ) create a theoretical framework for corporate blogs and analyse Fortune 500 companies to find that a blog’s target audience and the alignment of blog content and its management significantly impact the visibility of that blog. Most of the studies under this theme focus on analyzing data on blogs. They highlight the importance of word of mouth, which is closely associated with user satisfaction. It also emerges from these studies that user engagement and consequent satisfaction play parallel and mediating roles within such online communities.
4.3.6 Risks and Concerns with the Use of Social Media
Social media and its associated risks have captured the attention of many authors. A very early study by Griffiths and Light ( 2008 ) focuses on the problem of media convergence, whereby a gaming website includes social media features, putting vulnerable young audience at the risk of scamming. An Australian study suggests that many users are unaware of the potential risks of disclosing personal information on social media site, or consider themselves as low risk targets (Tow et al. 2010 ). Krasnova et al. ( 2010 ) find that the ease of forming and maintaining relationships on an enjoyable social platform motivates users to disclose personal information. Their study shows that user trust in a service/network provider, and privacy control options on a networking site greatly dismiss user perceptions of associated risk. Vishwanath ( 2015 ) finds that farcing attacks on Facebook occur at two levels – victim to phishers with phony profiles and victim to phishers soliciting personal information directly from them.
To combat the privacy problem of photos, videos, and other content posted online, Fogués et al. ( 2014 ) developed a Best Friend Forever tool that automatically distinguishes friends on a user’s profile by assigning individual values based on relationship ties. Zhang et al. ( 2016 ) find that incorporating non-verbal features of reviewers can massively improve the performance of online fake review detection models. Gerlach et al. ( 2015 ) find that user perception of privacy risks has a mediating effect on the relationship between policy monetization and user willingness to share information. Burtch et al. ( 2016 ) analyse a large online crowd funding platform and report that when campaign contributors control/conceal visibility from public display, there is a negative impact on subsequent visitor’s conversion likelihood and average contributions. In a different study, Choi et al. ( 2015 ) find that information dissemination and network commonality has a high impact on individual’s perception of privacy invasion and relationship bonding that impedes transactional and interpersonal avoidances.
Studies reviewed here discuss a social contagion effect of risks associated with social media use. Recent studies (2014–2016) suggest educating audiences about the threats associated with the extent of personal information being disclosed on social media sites. They recommend government agencies to keep the users informed, and the social media sites to control some of their security features. It is necessary to define and control privacy settings across these many existing social networks.
4.3.7 Negative Stigma Attached to Social Media Use
Some studies suggest that there is a negative stigma associated with the use of social media in the workplace. In a typical case study, Koch et al. ( 2012 ) analyze three employee layers in an organization to find that new hires (users of social media sites) showed improved morale and employee engagement, some middle managers (non users) were frustrated and experienced isolation, while the senior execs were wary of social media use. In a contrasting case, Cao et al. ( 2015 ) suggest that social media has the potential to build employees’ social capital to positively influence their knowledge integration. In discussing the impact of social media on organizational life, Koch et al. ( 2013 ) find that conflicts can stem between workplace values and the values these employees ascribe to social media.
In a gender-based study on social network facilitated team collaboration, Shen et al. ( 2010 ) found that the collective intention in men was influenced by positive emotions, attitude and group norms, while the collective participation intention in women was affected by negative emotions and social identity. Huang et al. ( 2015 ) debate the concept of communicational ambidexterity to understand the conflicting demands of managing internal organization communication in contrast to open and distributed social media communication. Wu ( 2013 ) suggests information-rich networks enabled by social media tend to drive job security and employee performance. Lu et al. ( 2015 ) use the social network theory to conclude that structural and cognitive dimensions of social relationships positively impact job performance. Ali-Hassan et al. ( 2015 ) show social and cognitive use of social media has a positive influence on employee performance, while hedonic use of social media leaves a negative impact on routine performance.
These reviewed studies showcase that social networking encourages shared language and trust between employees in a workspace. Another emerging suggestion highlights that organizations should exercise policy, and use socialization and leadership-based mechanisms to counter any problems resulting from differing workplace values. Some of these studies show interest in the cognitive side of social ties that positively nurture social relationships and innovation performance.
4.3.8 Social Media and Value Creation
Studies in the extant literature have particularly focussed on the aspect of value creation within online communities. As Ridings and Wasko ( 2010 ) have observed, an online discussion group/community is a direct product of its social and structural dynamics. Porter et al. ( 2013 ) investigate firm value and find that a sponsor’s efforts are stronger with positive and direct effect on trust building. Luo et al. ( 2013 ) suggest that social media has faster predictive value than conventional online media, and that the embedded metrics like consumer ratings are leading indicators of a firm’s equity. Hu et al. ( 2015 ) develop a formative model with an aggregate online social value construct and identify factors to increase user benefits and satisfaction, ensuring customer retention via continued usage of online services. In a public organization study focussing on social networking system, Karoui et al. ( 2015 ) suggest that differing perceptions of social capital can result in actors adopting differing strategies for holding their social position within an organization. Barrett et al. ( 2016 ) find that value creation in online communities expands beyond the dyadic relationship between a firm and the community to include a more intricate relationship involving stakeholders of a wider ecosystem. Dong and Wu ( 2015 ) use data from Dell and Starbucks and find substantial evidence for online user innovation-enabled implementation increasing firm value. Overall, the studies on social media and value creation emphasize on influence of social and structural interplay on sustainability, which is visible over longitudinal examination of their relationship to one another.
4.3.9 Role of Social Media During Critical/Extreme Events
Certain authors are more interested in micro-blogging used at the time of critical/extreme events. In an attempt to filter real time news/updates from irrelevant personal messages and spam, Cheng et al. ( 2011 ) propose analysis of information diffusion patterns for a large set of micro-blogs that update emergency news. They claim that their approach (using Twitter data) outperforms other benchmark solutions to offer diverse user preferences and customized results during critical events. Cheong and Lee ( 2011 ) use Twitter data to propose a framework that is useful for Homeland Securities and Law enforcement agencies to record and respond to terror situations. Oh et al. ( 2013 ) also study Twitter data from three extreme events to find that information without any clear source is at the top, personal involvement comes second, with anxiety at third place in the list of rumour causing factors during social crisis events. Wang et al. ( 2014 ) affirm that news spreads widely through online portals. They find that news first posted even on a small news portal can be picked and reposted by a major news portal, forming a hotspot event for the news to rapidly spread over the Internet.
Lee et al. ( 2015a ) performed negative binomial analysis of the 2013 Boston marathon tragedy Tweets to find that follower numbers, reaction time, and hash tagging significantly affected the diffusion of Tweets. Oh et al. ( 2015 ) analysed Twitter data from the 2011 Egypt revolution and found that hash tags played a critical role in gathering information and maintaining situational awareness during such politically unstable phases. Ling et al. ( 2015 ) undertake a qualitative study of 2011 Thailand flooding data to conclude that social media can offer a community: structural, resource, and psychological empowerment to achieve collaborative control and collective participation. In summary, studies since 2011 have been particularly examining Twitter data, and have derived significant insights on their positive effect during critical/extreme events.
4.3.10 Social Media for Help/Support
Some users post updates on social media with an aim to seek help/support from online communities. Maier et al. ( 2015a ) find that such posts cause social overload for other users, and the psychological consequences include feelings of exhaustion, low user satisfaction, and high intentions of reducing/stopping the use of social media sites. Yan et al. ( 2015a ) find that healthcare traits of patients help them establish social connections online, which is influenced by their cognitive abilities. Spagnoletti et al. ( 2015 ) develop a user utility model for integrating social media in personalized elderly healthcare that is capable of challenging traditional organizational boundaries to transform the internal and external stakeholder engagement. Yan and Tan ( 2014 ) propose a partially observed Markov decision process model to find sufficient evidence suggesting emotional support is most significant in improving patient health. Kallinikos and Tempini ( 2014 ) study the ups and downs of having a large unsupervised social network based on patient self-reporting for gathering and examining data on patients’ health.
Limited number of studies has been recorded for this theme. These studies are fairly recent suggesting a new emerging trend, where health/support based communities are being formed. The expanse of such communities seems to be largely dependent on the information processing capacity and the range of social ties that the members of such networks can handle. Using social media to bring together people with similar health conditions suggests that informational and social support can have varying influence on patient health.
4.3.11 Public Bodies and Social Media Interaction
User-generated content from social media is becoming one of the important information channels across public administrative bodies and political contexts. Baur ( 2017 ) has developed a MarketMiner framework that massively improves the utilization of multi-source, multi-language social media content, which can be applied to areas such as open government. Rosenberger et al. ( 2017 ) use abstraction-based modelling to conceptualize the data structure, and conclude that wrapping social network application programming interfaces allow mutual integration of most user activities. Gonzalez-Bailon et al. ( 2010 ) show that political discussions in online networks are larger and deeper compared to other networks. Ameripour et al. ( 2010 ) analyse the restricted Iranian social networks, subject to surveillance and censorship to find that Internet conviviality is not an independent variable with deterministic outcomes, but is a technology shaped by economic and political forces. Although, not published in the list of journals included in this review, Kapoor and Dwivedi ( 2015 ) provided a detailed discussion on how social media was used intensively to transform electoral campaigns during India’s last general election. Similar use has also been reported in other contexts (for example, US presidential elections) by other studies.
Except one study (that is, Ameripour et al. 2010 ), the remaining reviewed under this category are very recent (2015–2016). These studies suggest the use of social media for increasing public engagement and transparency. Most of these studies used technical frameworks and modelling techniques to identify communication clusters and structures to derive insights relevant to open government and political campaigns.
4.3.12 Traditional v/s Social Media
Another set of studies investigate the differences between traditional and social media. A very early study by Wattal et al. ( 2010 ) compares the big money tactics for political campaigning with social media campaigning to reveal that Internet and the blogosphere can majorly influence campaigning and election results. Dewan and Ramaprasad ( 2014 ) examine the importance of new and old media within the music industry; they find radio positively and consistently affecting sales of songs and albums, and sales displacement from free online sampling overpowering positive word of mouth on sales. Miranda et al. ( 2016 ) compare traditional and social media to suggest that there are evils associated with the societal benefits of social media, and mass media has a detrimental effect on public discourse.
4.3.13 Testing Pre-Established Models
Some studies in literature restrict focus to pre-established models and relationships for evaluating varied aspects of social media. Fang et al. ( 2013 ) apply social network theories to suggest positive social influence on adoption probabilities. Levina and Arriaga ( 2014 ) use Bourdieu’s theory to explain the role of status markers and external sources in shaping social dynamics. Bharati et al. ( 2014 ) combine institutional theory and organizational innovation, whereby institutional pressures significantly predict absorptive capacity. Kekolahti et al. ( 2015 ) use Bayesian networks to indicate the decrease in perceived importance of communication with increase in age. Chang et al. ( 2015 ) integrate social distance with clustering methods to show shorter social distance results in satisfactory trust. Chung et al. ( 2017 ) employ the Technology Acceptance Model, and find positive effects between traveller readiness and ease of using geo-tagging. Zhao et al. ( 2016 ) use theory of planned behaviour and attribution theory to find that virtual rewards for sharing knowledge online undermine enjoyment. Yu et al. ( 2015 ) use the causation and heuristic theories to find that affect influences self disclosure indirectly by adjusting perceived benefits. Stanko ( 2016 ) employs Innovation Diffusion Theory, and finds that community interaction influences innovations that are used to aid a further innovation.
5 Discussion
In reviewing the publications gathered for this paper, commonalities have been observed in the myriad aspects of social media chosen for investigation. While many studies focussed their attention on understanding the behaviours of social media users, the others examined entrepreneurial participation and firm behaviour. A number of studies have focussed on the content being posted in online communities, several of which report on the repercussions of some of this content being used as an awareness medium during critical events and tragedies. Interesting revelations were made by authors studying the use of social media as a platform to render and/or receive help or support, and its incorporation in the field of healthcare and public administration. Value creation and the ill-effects associated with the use of social media at the workplace were also discussed. Several studies chose to test previously established hypotheses and models, while others compared traditional media with social media. Prior research has also provided insights into how firms have been using social media to market their products and services. These strategies run in parallel with the reviews and recommendations posted by users on social media sites, which have also received considerable attention in the literature. In summary, given that different types of social media platforms are emerging, and different consequences are associated with their use, research in this field will continue to evolve. This is also evidenced by the increased number of publications related to usage and impact over the past five years.
Social media platforms have essentially redefined the ways in which people choose to communicate and collaborate. An online community is a socio-technological space where a sense of communal identity drives engagement, which, in turn, enhances satisfaction (Ray et al. 2014 ). Intriguingly, social media are facilitating the emergence of virtual knowledge communities and self help networks. These web-based arrangements allow medical practice and research to access patient experience on a daily basis, which was not possible earlier. However, since research in this area is still in its early stages, it is difficult to assess the social complexity involved (e.g., stability of a networking platform that brings together patients with medical experts) in the process (Kallinikos and Tempini 2014 ).
Firms are recognizing social media as a prominent indicator of equity value that not only improves short-term performance, but also brings about long-term productivity benefits (Luo et al. 2013 ). The reviewed studies suggest that incorporatin social media in firms increases meta-knowledge (who’s who in an organization and who does what), which helps avoid knowledge duplication and promotes new ways of managing work (Leonardi 2014 ). Active management of social media has been observed to be more effective when those inside rather than outside a firm are engaged (Miller and Tucker 2013 ).
A specific line of research focuses on consumers, who substantially rely on online reviews before making any purchase decision. The research papers reviewed in this study exhibit diversity in studying authenticity of reviews for travel sites, social bookmarking and review sites, movie ratings, car manufacturing, and social media check-ins. Studies concur that there has been an exponential increase in the number of fake reviews, which is severely damaging the credibility of online reviews and putting business values at risk (Zhang et al. 2016 ). Some studies have also empirically identified consumers’ social media participation as a key metric contributing to the profitability of a business (Rishika et al. 2013 ). There evidently exists a direct correlation between consumer engagement on social media sites and their shopping intentions, which makes the issue of legitimate reviews all the more important for businesses and consumers. Although some studies have proposed models and algorithms that claim to filter authentic reviews from the rest, there is no single and straightforward solution reported yet that can fully combat this problem.
The issue of negative posts has received considerable attention in the literature. Prior research suggests that, overall, the impact of negative posts or electronic word of mouth is much higher than the positive ones that increase readership (Aggarwal et al. 2012 ). This problem is also prevalent in organizations. According to the studies reviewed here, organizations either prohibit employees from posting controversial content online, or employees themselves refrain from doing so, fearing negative repercussions. The same employees also share positive posts, and the adverse effect of the few negative posts is offset by positive ones. It is in a firm’s interests to encourage free will enterprise blogging to break down knowledge silos and yield higher employee productivity (Singh et al. 2014 ).
Businesses looking to monetize online content and social search rely heavily on substantial understanding of consumer behaviour in terms of their interaction and participation in social settings (Susarla et al. 2012 ). As consumers gain access to social platforms that offer free content consumption without an obligatory payment, the relationship between sampling and sales becomes all the more important (Dewan and Ramaprasad 2014 ). There is much research supporting the belief that online word of mouth has a critical role to play in a firm’s overall performance, and introducing a pay-wall (for previously free content) can significantly reduce the volume of word of mouth for popular content in comparison to niche content (Oh et al. 2016 ). Determining consumers’ social influence in an online community is of critical interest to managers, who seek to gain some leverage from the potential of social media (Shi et al. 2014 ). Some researchers find it difficult to distinguish social influence from users’ self selection preferences. From an analysis point of view, it then becomes necessary to separate factors affecting user membership in a social network from various types of social influence (Susarla et al. 2012 ).
The findings on the use of social media in emergencies suggests that a general user response in an online community is very different from that during a crisis, as those responses then become more reflexive. It has been observed that in times of crisis, lack of information sources coupled with too many situation reports being shared by the users of a social media platform can precipitate a rumour mill. It thus becomes incumbent on emergency responders to release reliable information, whilst trying to control collective anxiety in the community, to suppress the rumour threads (Oh et al. 2013 ). Furthermore, security concerns are increasingly common with involuntary online exposure on social media, and research on this subject suggests that information dissemination with network commonality affects privacy invasion and user bonding (Choi et al. 2015 ). It has been learnt that an individual’s or firm’s decision to withhold information in the interest of privacy can have both positive and negative effects on their utility (Burtch et al. 2016 ).
In reviewing the 132 publications on social media and social networking, it was observed that many studies relied primarily on social exchange theory, network theory and organization theory. Table 3 , shown below, lists other theories that have been used by at least two publications. There were several other theories that were used by at least once, including social role theory, game theory, structural holes theory, management and commitment theories, institutional theory, deterrence and mitigation theories, and self determination and self categorization theories. It is noteworthy that dominant IS adoption theories such as Unified Theory of Acceptance and Use of Technology (Dwivedi et al. 2017b , c ; Rana et al. 2017 ; Venkatesh et al. 2003 ), Technology Acceptance Model (Davis 1989 ) and Innovation Diffusion Theory (Kapoor et al. 2015 ) are less widely utilised.
In addition, our review of the literature on social media identified dominant research methods employed by scholars. Qualitative, quantitative, and mixed methods were used by most of these studies. Closer scrutiny of the 132 publications reviewed in this study revealed the multitude of techniques applied for gathering data. Quantitative methods employed in these studies mostly adopted analytical techniques and surveys (Table 4 ). On the other hand, publications using qualitative methods mainly used case studies and interviews to gather the required data (Table 4 ). As expected, studies employing mixed methods used a combination of analytical and conceptual techniques, alongside surveys and content analysis (Table 4 ). Table 4 summarizes the various research approaches used by publications in our corpus.
The reviewed publications were also analyzed to determine the nature of the social network that were studied. Precisely 46 websites emerged, with Facebook, online communities, Twitter, Blogs and YouTube being most frequently targeted. Networks analysed by at least two or more studies have been identified in Table 5 . The other networks that received attention from the reviewed publications include Ebay, Flickr, Flixster, Gtalk, microsoft, MSN Space, Patientslikeme, New York Times, TripAdvisor.com , and Boxofficemojo.com . Studies also focussed on websites related to online news, Q&A websites, discussion groups and forums, online radio and television, and medical sites such as Webmd.com .
5.1 Limitations and Future Research Directions
Studies, such as the one by Cheung et al. ( 2012 ), that examine aspects of popular websites, warn against consumer perceptions being under the influence of brand equity of those websites. They recommend exercising caution while generalizing such findings in the context of other websites (Cheung et al. 2012 ). Rosenberger et al. ( 2017 ) identify a similar problem with relying on publicly available data, in that the underlying abstraction makes findings valid only for the specific social media site that was analyzed, whilst significantly restricting its generalizability to other sites. In a similar vein, other studies (Krasnova et al. 2015 ; Khan and Jarvenpaa 2010 ; Tow et al. 2010 ) have acknowledged the limitation of restricting their research to a single social media site, and recommend future researchers to adopt a cross-platform perspective for drawing significant inferences.
Mettler and Winter ( 2016 ) suggest that there is a paucity of studies on Enterprise Social Systems because of its novelty, and urge researchers to fill this void. Turel and Serenko ( 2012 ) identify the lack of conceptualization in the notion of technology addiction; they recognize that the process of defining it is still in the early stages, and is being debated across communities. For researchers interested in examining aspects of Twitter, Cheng et al. ( 2011 ) recommend incorporating the location metric focused on Twitter’s geo location feature allowing users to trace the latitude and longitude of Tweets. Another recommendation for Twitter related studies comes from Benthaus et al. ( 2016 ), where they suggest researchers should study user involvement differently, based on how often users choose to ‘like’ the content of a company. As for use of social media for marketing in firms, the literature has restricted focus to the resulting marketing benefits, with limited evidence supporting the effectiveness of social platforms for enhancing employee communications (Miller and Tucker 2013 ).
For behavioural studies, researchers need to be wary of the fact that motivation for users to adopt social media is different, often contingent on their culture (Chiu and Huang 2015 ; Shen et al. 2010 . It is also important to note that behavioural reactions are susceptible to change over time, and changing habits have a role to play (Chiu and Huang 2015 ). Longitudinal research is thus always expected to offer a better understanding of the research problem when the intended behavioural reactions transfer into behaviour with time (Maier et al. 2015a ). In studying online reviews and recommendations, researchers can assume that these reviews are independent of one another and remain static over time; however, Zhang and Piramuthu ( 2016 ) suggest that this may not be true and future researchers should now concentrate on how this has evolved, and if herding behaviour exists on such online platforms. In studying behaviours, it has also emerged that users develop discontinuance intentions after continuance intentions, with the latter never being completely replaced by the former. Turel ( 2015 ) thus recommends studying the initiation of discontinuance intentions, whilst identifying the factors leading to its dominance and actual discontinuance attempts.
Matook et al. ( 2015a ) identify that there is a need to study the aspect of trust formation between individuals on social media, where no personal relationships exist (unlike sites such as Facebook). Chung et al. ( 2017 ) identify that researchers often associate the use of certain social media with young users (for instance, Maier et al. 2015b ), and fail to study the usage perceptions across various ages (Vishwanath 2015 ). Van Osch and Steinfield ( 2016 ) suggest that future researchers should explore the potential of Enterprise Social Media to gain insights into the tools that support disentanglement of team boundary spanning. Finally, researchers have established that the lifecycle of information and communication technologies tend to be emancipatory in their infancy but eventually evolve into hegemonic tools. They warn social media policymakers to be wary of reproducing this pattern with digital media; the recommendation is to involve more citizens in the development of Internet governance framework, rather than resting decisions with the members of political or economic power (Miranda et al. 2016 ).
6 Conclusions
This paper discusses the findings of 132 publications contributing to the literature on social media. Multiple emergent themes in this body of literature have been identified to enhance understanding of the advances in social media research. By building on empirical findings of previous social media research, many new studies have been successful in theorizing the nature of most social media platforms. User-generated content allows collective understanding, which is a massive machine-human knowledge processing function capable of managing chaotic volumes of information. Some key conclusions relevant to stakeholders, including researchers, have been identified here.
Social media technologies are no longer perceived just as platforms for socialization and congregation, but are being acknowledged for their ability to encourage aggregation.
In reviewing the 132 publications on social media and social networking, it was observed that most studies used social exchange theory, network theory and organization theory to support their studies.
Facebook, online communities, and twitter are the three most popular networks targeted by publications in the field of social media research.
Publications in 2011 were still reporting user-generated content as a new type of online content. However, the last six years have seen tremendous scholarly progression in discussing the many applications of social networking, highlighting the highs and lows associated with its use.
Majority of the publications reviewed in this study are focussed on behavioural side of social media, reviews, and integration of social media for marketing and organizational purposes.
Many publications in the year 2013 concentrated their efforts in investigating the very popular aspect of reviews and recommendations on social networks.
Publications have become more focussed on studying social commerce across networking sites, particularly, Facebook, MySpace, YouTube and so on between 2015 and 2016.
Publications have not shown much interest in support-seeking posts and negative stigma attached to social media use after the year 2015.
Most studies unanimously acknowledge social media for its information sharing and information exchange capabilities, with a focussed group of studies recognizing its effectiveness during natural disasters and critical events.
Almost all publications studying information sharing during natural disasters and critical events focus on Twitter data.
Publications on administration and political contexts were particularly found in 2010 and 2016, with no interest expressed in these contexts between 2011 and 2015.
With information systems now expanding beyond organizational peripheries to become a part of the larger societal context, it is important for strategic information systems research to delve into the competitive setting of dynamic social systems. Online communities are introducing extrinsic rewards that do not limit users’ intrinsic motivations. Research on such communities should expand to study the interplay between extrinisic and intrinsic rewards, particularly in terms of their ability to cultivate and sustain users’ intrinsic motivations. From an organizational perspective, research on social media should move past the conventional dyadic view of the relationship between an online community and a firm, and focus on reconceptualising online users as an ecosystem of stakeholders. Social media has re-established the dynamics between organizations, employees, and consumers. Given the rise in number of publications focussing on workplace setting since 2014, future researchers should aim to analyze stakeholders’ potential in adopting social media tools to successfully accomplish their work goals. As for the limitations of this collective review, publications reviewed here were limited to only nine journals. This potentially means studies with significant contributions to social media literature published in other journals have been overlooked. Future researchers can look to overcome such exclusions and focus on the overall review of literature on social media platforms. Future reviews may focus on reviewing articles published in a larger number of IS journals related to a specific type of social media (i.e. social networking sites, blogs), or specific issues related to social media use, such as information load, stress, and impact on productivity. Despite these limitations, our study provides a comprehensive and robust intellectual framework for social media research that would be of value to adacemics and practitioners alike.
TITLE: (“Social Media” or “social networking” or “facebook” or “linkedin” or “instagram” or “twitter”)
Refined by: DOCUMENT TYPES: (ARTICLE OR PROCEEDINGS PAPER)
Timespan: All years. Indexes: SCI-EXPANDED, SSCI, A&HCI, CPCI-S, CPCI-SSH, ESCI.
http://www.springer.com/business+%26+management/business+information+systems/journal/10796
Aggarwal, R., & Singh, H. (2013). Differential influence of blogs across different stages of decision making: The case of venture capitalists. MIS Quarterly, 37 (4), 1093–1112.
Article Google Scholar
Aggarwal, R., Gopal, R., Sankaranarayanan, R., & Singh, P. V. (2012). Blog, blogger, and the firm: Can negative employee posts lead to positive outcomes? Information Systems Research, 23 (2), 306–322.
AlAlwan, A., Rana, N. P., Dwivedi, Y. K., & Algharabat, R. (2017). Social Media in Marketing: A review and analysis of the existing literature. Telematics and Informatics Available at http://www.sciencedirect.com/science/article/pii/S0736585317301077 .
Ali-Hassan, H., Nevo, D., & Wade, M. (2015). Linking dimensions of social media use to job performance: The role of social capital. The Journal of Strategic Information Systems, 24 (2), 65–89.
Ameripour, A., Nicholson, B., & Newman, M. (2010). Conviviality of internet social networks: An exploratory study of internet campaigns in Iran. Journal of Information Technology, 25 (2), 244–257.
Baek, H., Ahn, J., & Choi, Y. (2012). Helpfulness of online consumer reviews: Readers' objectives and review cues. International Journal of Electronic Commerce, 17(2), 99-126.
Barrett, M., Oborn, E., & Orlikowski, W. (2016). Creating value in online communities: The sociomaterial configuring of strategy, platform, and stakeholder engagement. Information Systems Research, 27 (4), 704–723.
Bateman, P. J., Gray, P. H., & Butler, B. S. (2011). Research note-the impact of community commitment on participation in online communities. Information Systems Research, 22 (4), 841–854.
Baur, A. W. (2017). Harnessing the social web to enhance insights into people’s opinions in business, government and public administration. Information Systems Frontiers, 19 (2), 231–251.
Benthaus, J., Risius, M., & Beck, R. (2016). Social media management strategies for organizational impression management and their effect on public perception. The Journal of Strategic Information Systems, 25 (2), 127–139.
Bharati, P., Zhang, C., & Chaudhury, A. (2014). Social media assimilation in firms: Investigating the roles of absorptive capacity and institutional pressures. Information Systems Frontiers, 16 (2), 257–272.
Blei, D. M. (2012). Probabilistic topic models. Communications of the ACM, 55 (4), 77–84.
Burgess, S., Sellitto, C., Cox, C., & Buultjens, J. (2011). Trust perceptions of online travel information by different content creators: Some social and legal implications. Information Systems Frontiers, 13 (2), 221–235.
Burtch, G., Ghose, A., & Wattal, S. (2016). Secret admirers: An empirical examination of information hiding and contribution dynamics in online Crowdfunding. Information Systems Research, 27 (3), 478–496.
Butler, B. S., & Wang, X. (2012). The cross-purposes of cross-posting: Boundary reshaping behavior in online discussion communities. Information Systems Research, 23 (3-part-2), 993–1010.
Cao, X., Guo, X., Liu, H., & Gu, J. (2015). The role of social media in supporting knowledge integration: A social capital analysis. Information Systems Frontiers, 17 (2), 351–362.
Centeno, R., Hermoso, R., & Fasli, M. (2015). On the inaccuracy of numerical ratings: Dealing with biased opinions in social networks. Information Systems Frontiers, 17 (4), 809–825.
Chang, I., Liu, C. C., & Chen, K. (2014). The push, pull and mooring effects in virtual migration for social networking sites. Information Systems Journal, 24 (4), 323–346.
Chang, W. L., Diaz, A. N., & Hung, P. C. (2015). Estimating trust value: A social network perspective. Information Systems Frontiers, 17 (6), 1381–1400.
Chau, M., & Xu, J. (2012). Business intelligence in blogs: Understanding consumer interactions and communities. MIS Quarterly, 36 (4), 1189–1216.
Google Scholar
Chen, R., & Sharma, S. K. (2015). Learning and self-disclosure behavior on social networking sites: The case of Facebook users. European Journal of Information Systems, 24 (1), 93–106.
Chen, J., Xu, H., & Whinston, A. B. (2011). Moderated online communities and quality of user-generated content. Journal of Management Information Systems, 28 (2), 237–268.
Chen, A., Lu, Y., Chau, P. Y., & Gupta, S. (2014). Classifying, measuring, and predicting users’ overall active behavior on social networking sites. Journal of Management Information Systems, 31 (3), 213–253.
Chen, H., De, P., & Hu, Y. J. (2015). IT-enabled broadcasting in social media: An empirical study of artists’ activities and music sales. Information Systems Research, 26 (3), 513–531.
Cheng, J., Sun, A., Hu, D., & Zeng, D. (2011). An information diffusion-based recommendation framework for micro-blogging. Journal of the Association for Information Systems, 12 (7), 463–486.
Cheong, M., & Lee, V. C. (2011). A microblogging-based approach to terrorism informatics: Exploration and chronicling civilian sentiment and response to terrorism events via twitter. Information Systems Frontiers, 13 (1), 45–59.
Cheung, C. M. Y., Sia, C. L., & Kuan, K. K. (2012). Is this review believable? A study of factors affecting the credibility of online consumer reviews from an ELM perspective. Journal of the Association for Information Systems, 13 (8), 618.
Chiu, C. M., & Huang, H. Y. (2015). Examining the antecedents of user gratification and its effects on individuals’ social network services usage: The moderating role of habit. European Journal of Information Systems, 24 (4), 411–430.
Choi, B. C., Jiang, Z., Xiao, B., & Kim, S. S. (2015). Embarrassing exposures in online social networks: An integrated perspective of privacy invasion and relationship bonding. Information Systems Research, 26 (4), 675–694.
Chung, N., Tyan, I., & Han, H. (2017). Enhancing the smart tourism experience through geotag. Information Systems Frontiers, 19 (4), 731–742.
Claussen, J., Kretschmer, T., & Mayrhofer, P. (2013). The effects of rewarding user engagement: The case of facebook apps. Information Systems Research, 24 (1), 186–200.
Culnan, M. J. (1986). The intellectual development of management information systems, 1972-1982: A co-citation analysis. Management Science, 32 (2), 156.
Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13 (3), 318–339.
Dellarocas, C., Gao, G., & Narayan, R. (2010). Are consumers more likely to contribute online reviews for hit or niche products? Journal of Management Information Systems, 27 (2), 127–158.
Dennis, A. R., Minas, R. K., & Lockwood, N. S. (2016). Mapping the corporate blogosphere: Linking audience, content, and management to blog visibility. Journal of the Association for Information Systems, 17 (3), 162.
Dewan, S., & Ramaprasad, J. (2014). Social media, traditional media, and music sales. MIS Quarterly, 38 (1), 101–121.
Dong, J. Q., & Wu, W. (2015). Business value of social media technologies: Evidence from online user innovation communities. The Journal of Strategic Information Systems, 24 (2), 113–127.
Dou, Y., Niculescu, M. F., & Wu, D. J. (2013). Engineering optimal network effects via social media features and seeding in markets for digital goods and services. Information Systems Research, 24 (1), 164–185.
Dwivedi, Y. K., Kapoor, K. K., & Chen, H. (2015). Social media marketing and advertising. The Marketing Review, 15 (3), 289–309.
Dwivedi, Y. K., Rana, N. P., & Alryalat, M. (2017a). Affiliate marketing: An overview and analysis of emerging literature. The Marketing Review, 17 (1), 33–50.
Dwivedi, Y. K., Rana, N. P., Jeyaraj, A., Clement, M., & Williams, M. D. (2017b). Re-examining the unified theory of acceptance and use of technology (UTAUT): Towards a revised theoretical model. Information Systems Frontiers , 1–16. Available at. https://doi.org/10.1007/s10796-017-9774-y .
Dwivedi, Y. K., Rana, N. P., Janssen, M., Lal, B., Williams, M. D., & Clement, M. (2017c). An empirical validation of a unified model of electronic government adoption (UMEGA). Government Information Quarterly, 34 (2), 211–230.
Fang, X., Hu, P. J. H., Li, Z., & Tsai, W. (2013). Predicting adoption probabilities in social networks. Information Systems Research, 24 (1), 128–145.
Fogués, R. L., Such, J. M., Espinosa, A., & Garcia-Fornes, A. (2014). BFF: A tool for eliciting tie strength and user communities in social networking services. Information Systems Frontiers, 16 (2), 225–237.
García-Crespo, Á., Colomo-Palacios, R., Gómez-Berbís, J. M., & Ruiz-Mezcua, B. (2010). SEMO: A framework for customer social networks analysis based on semantics. Journal of Information Technology, 25 (2), 178–188.
Garg, R., Smith, M. D., & Telang, R. (2011). Measuring information diffusion in an online community. Journal of Management Information Systems, 28 (2), 11–38.
Gerlach, J., Widjaja, T., & Buxmann, P. (2015). Handle with care: How online social network providers’ privacy policies impact users’ information sharing behavior. The Journal of Strategic Information Systems, 24 (1), 33–43.
Goes, P. B., Lin, M., & Au Yeung, C. M. (2014). “Popularity effect” in user-generated content: Evidence from online product reviews. Information Systems Research, 25 (2), 222–238.
Goes, P. B., Guo, C., & Lin, M. (2016). Do incentive hierarchies induce user effort? Evidence from an online knowledge exchange. Information Systems Research, 27 (3), 497–516.
Goh, K. Y., Heng, C. S., & Lin, Z. (2013). Social media brand community and consumer behavior: Quantifying the relative impact of user-and marketer-generated content. Information Systems Research, 24 (1), 88–107.
Gonzalez-Bailon, S., Kaltenbrunner, A., & Banchs, R. E. (2010). The structure of political discussion networks: A model for the analysis of online deliberation. Journal of Information Technology, 25 (2), 230–243.
Gray, P. H., Parise, S., & Iyer, B. (2011). Innovation impacts of using social bookmarking systems. MIS Quarterly, 35 (3), 629–643.
Greenwood, B. N., & Gopal, A. (2015). Research note—Tigerblood: Newspapers, blogs, and the founding of information technology firms. Information Systems Research, 26 (4), 812–828.
Griffiths, M., & Light, B. (2008). Social networking and digital gaming media convergence: Classification and its consequences for appropriation. Information Systems Frontiers, 10 (4), 447–459.
Gu, B., Konana, P., Raghunathan, R., & Chen, H. M. (2014). Research note—The allure of Homophily in social media: Evidence from investor responses on virtual communities. Information Systems Research, 25 (3), 604–617.
Hildebrand, C., Häubl, G., Herrmann, A., & Landwehr, J. R. (2013). When social media can be bad for you: Community feedback stifles consumer creativity and reduces satisfaction with self-designed products. Information Systems Research, 24 (1), 14–29.
Hu, T., Kettinger, W. J., & Poston, R. S. (2015). The effect of online social value on satisfaction and continued use of social media. European Journal of Information Systems, 24 (4), 391–410.
Huang, J., Baptista, J., & Newell, S. (2015). Communicational ambidexterity as a new capability to manage social media communication within organizations. The Journal of Strategic Information Systems, 24 (2), 49–64.
Hwang, Y. C., Yuan, S. T., & Weng, J. H. (2011). A study of the impacts of positive/negative feedback on collective wisdom—Case study on social bookmarking sites. Information Systems Frontiers, 13 (2), 265–279.
Ismagilova, E., Dwivedi, Y. K., Slade, E. L., & Williams, M. D. (2017). Electronic word of mouth (eWOM) in the marketing context: A state of the art analysis and future directions . Cham: Springer International Publishing.
Book Google Scholar
Kallinikos, J., & Tempini, N. (2014). Patient data as medical facts: Social media practices as a foundation for medical knowledge creation. Information Systems Research, 25 (4), 817–833.
Kapoor, K. K., & Dwivedi, Y. K. (2015). Metamorphosis of Indian electoral campaigns: Modi’s social media experiment. International Journal of Indian Culture & Business Management, 11 (4), 496–516.
Kapoor, K. K., Dwivedi, Y. K., & Williams, M. D. (2015). Examining the role of three sets of innovation attributes for determining adoption of the interbank mobile payment service. Information Systems Frontiers, 17 (5), 1039–1056.
Kapoor, K. K., Dwivedi, Y. K., & Piercy, N. (2016). Pay-per-click advertising: A review of literature. The Marketing Review, 16 (2), 183–202.
Karoui, M., Dudezert, A., & Leidner, D. E. (2015). Strategies and symbolism in the adoption of organizational social networking systems. The Journal of Strategic Information Systems, 24 (1), 15–32.
Kekolahti, P., Karikoski, J., & Riikonen, A. (2015). The effect of an individual’s age on the perceived importance and usage intensity of communications services—A Bayesian network analysis. Information Systems Frontiers, 17 (6), 1313–1333.
Khan, Z., & Jarvenpaa, S. L. (2010). Exploring temporal coordination of events with Facebook. Com. Journal of Information Technology, 25 (2), 137–151.
Khansa, L., Ma, X., Liginlal, D., & Kim, S. S. (2015). Understanding members’ active participation in online question-and-answer communities: A theory and empirical analysis. Journal of Management Information Systems, 32 (2), 162–203.
Koch, H., Gonzalez, E., & Leidner, D. (2012). Bridging the work/social divide: The emotional response to organizational social networking sites. European Journal of Information Systems, 21 (6), 699–717.
Koch, H., Leidner, D. E., & Gonzalez, E. S. (2013). Digitally enabling social networks: Resolving IT–culture conflict. Information Systems Journal, 23 (6), 501–523.
Krasnova, H., Spiekermann, S., Koroleva, K., & Hildebrand, T. (2010). Online social networks: Why we disclose. Journal of Information Technology, 25 (2), 109–125.
Krasnova, H., Widjaja, T., Buxmann, P., Wenninger, H., & Benbasat, I. (2015). Research note—Why following friends can hurt you: An exploratory investigation of the effects of envy on social networking sites among college-age users. Information Systems Research, 26 (3), 585–605.
Kreps, D. (2010). My social networking profile: Copy, resemblance, or simulacrum? A poststructuralist interpretation of social information systems. European Journal of Information Systems, 19 (1), 104–115.
Kuan, K. K., Hui, K. L., Prasarnphanich, P., & Lai, H. Y. (2015). What makes a review voted? An empirical investigation of review voting in online review systems. Journal of the Association for Information Systems, 16 (1), 48.
Kuegler, M., Smolnik, S., & Kane, G. (2015). What’s in IT for employees? Understanding the relationship between use and performance in enterprise social software. The Journal of Strategic Information Systems, 24 (2), 90–112.
Lee, J., Agrawal, M., & Rao, H. R. (2015a). Message diffusion through social network service: The case of rumor and non-rumor related tweets during Boston bombing 2013. Information Systems Frontiers, 17 (5), 997–1005.
Lee, K., Lee, B., & Oh, W. (2015b). Thumbs up, sales up? The contingent effect of Facebook likes on sales performance in social commerce. Journal of Management Information Systems, 32 (4), 109–143.
Leonardi, P. M. (2014). Social media, knowledge sharing, and innovation: Toward a theory of communication visibility. Information Systems Research, 25 (4), 796–816.
Levina, N., & Arriaga, M. (2014). Distinction and status production on user-generated content platforms: Using Bourdieu’s theory of cultural production to understand social dynamics in online fields. Information Systems Research, 25 (3), 468–488.
Ling, C. L. M., Pan, S. L., Ractham, P., & Kaewkitipong, L. (2015). ICT-enabled community empowerment in crisis response: Social media in Thailand flooding 2011. Journal of the Association for Information Systems, 16 (3), 174.
Lister, M. (2017). 40 essential social media marketing statistics for 2017. Available at: http://www.wordstream.com/blog/ws/2017/01/05/social-media-marketing-statistics . Accessed 22 June 2017.
Lu, B., Guo, X., Luo, N., & Chen, G. (2015). Corporate blogging and job performance: Effects of work-related and nonwork-related participation. Journal of Management Information Systems, 32 (4), 285–314.
Lukyanenko, R., Parsons, J., & Wiersma, Y. F. (2014). The IQ of the crowd: Understanding and improving information quality in structured user-generated content. Information Systems Research, 25 (4), 669–689.
Lundmark, L. W., Oh, C., & Verhaal, J. C. (2016). A little Birdie told me: Social media, organizational legitimacy, and underpricing in initial public offerings. Information Systems Frontiers , 1–16. https://doi.org/10.1007/s10796-016-9654-x .
Luo, X., & Zhang, J. (2013). How do consumer buzz and traffic in social media marketing predict the value of the firm? Journal of Management Information Systems, 30 (2), 213–238.
Luo, X., Zhang, J., & Duan, W. (2013). Social media and firm equity value. Information Systems Research, 24 (1), 146–163.
Ma, X., Khansa, L., Deng, Y., & Kim, S. S. (2013). Impact of prior reviews on the subsequent review process in reputation systems. Journal of Management Information Systems, 30 (3), 279–310.
Maier, C., Laumer, S., Eckhardt, A., & Weitzel, T. (2015a). Giving too much social support: Social overload on social networking sites. European Journal of Information Systems, 24 (5), 447–464.
Maier, C., Laumer, S., Weinert, C., & Weitzel, T. (2015b). The effects of technostress and switching stress on discontinued use of social networking services: A study of Facebook use. Information Systems Journal, 25 (3), 275–308.
Massari, L. (2010). Analysis of MySpace user profiles. Information Systems Frontiers, 12 (4), 361–367.
Matook, S., Brown, S. A., & Rolf, J. (2015a). Forming an intention to act on recommendations given via online social networks. European Journal of Information Systems, 24 (1), 76–92.
Matook, S., Cummings, J., & Bala, H. (2015b). Are you feeling lonely? The impact of relationship characteristics and online social network features on loneliness. Journal of Management Information Systems, 31 (4), 278–310.
McCain, K. W. (1984). Longitudinal author Cocitation mapping: The changing structure of macroeconomics. Journal of the American Society for Information Science, 35 (6), 351–359.
McCallum, A. K. (2002). Mallet: A machine learning for language toolkit. From http://mallet.cs.umass.edu
Mettler, T., & Winter, R. (2016). Are business users social? A design experiment exploring information sharing in enterprise social systems. Journal of Information Technology, 31 (2), 101–114.
Miller, A. R., & Tucker, C. (2013). Active social media management: The case of health care. Information Systems Research, 24 (1), 52–70.
Miranda, S. M., Kim, I., & Summers, J. D. (2015). Jamming with social media: How cognitive structuring of organizing vision facets affects it innovation diffusion. MIS Quarterly, 39 (3), 591–614.
Miranda, S. M., Young, A., & Yetgin, E. (2016). Are social media emancipatory or hegemonic? Societal effects of mass media digitization. MIS Quarterly, 40 (2), 303–329.
Nerur, S. P., Rasheed, A. A., & Natarajan, V. (2008). The intellectual structure of the strategic management field: An author co-citation analysis. Strategic Management Journal, 29 (3), 319–336.
Oestreicher-Singer, G., & Zalmanson, L. (2013). Content or community? A digital business strategy for content providers in the social age. MIS Quarterly, 37 (2), 591–616.
Oh, O., Agrawal, M., & Rao, H. R. (2013). Community intelligence and social media services: A rumor theoretic analysis of tweets during social crises. MIS Quarterly, 37 (2), 407–426.
Oh, O., Eom, C., & Rao, H. R. (2015). Research note—Role of social Media in Social Change: An analysis of collective sense making during the 2011 Egypt revolution. Information Systems Research, 26 (1), 210–223.
Oh, W., Moon, J. Y., Hahn, J., & Kim, T. (2016). Research note—Leader influence on sustained participation in online collaborative work communities: A simulation-based approach. Information Systems Research, 27 (2), 383–402.
Phang, C. W., Kankanhalli, A., & Tan, B. C. (2015). What Motivates Contributors vs. Lurkers? An Investigation of Online Feedback Forums. Information Systems Research, 26(4), 773–792
Plume, C. J., Dwivedi, Y. K., & Slade, E. L. (2016). Social Media in the Marketing Context: A state of the art analysis and future directions (1st ed.). Oxford: Chandos Publishing Ltd.
Porter, C. E., Devaraj, S., & Sun, D. (2013). A test of two models of value creation in virtual communities. Journal of Management Information Systems, 30 (1), 261–292.
Qiu, L., Rui, H., & Whinston, A. B. (2014). Effects of social networks on prediction markets: Examination in a controlled experiment. Journal of Management Information Systems, 30 (4), 235–268.
Qiu, L., Tang, Q., & Whinston, A. B. (2015). Two formulas for success in social media: Learning and network effects. Journal of Management Information Systems, 32 (4), 78–108.
Rana, N. P., Dwivedi, Y. K., Lal, B., Williams, M. D., & Clement, M. (2017). Citizens’ adoption of an electronic government system: Towards a unified view. Information Systems Frontiers, 19 (3), 549–568.
Ray, S., Kim, S. S., & Morris, J. G. (2014). The central role of engagement in online communities. Information Systems Research, 25 (3), 528–546.
Ridings, C., & Wasko, M. (2010). Online discussion group sustainability: Investigating the interplay between structural dynamics and social dynamics over time. Journal of the Association for Information Systems, 11 (2), 95.
Rishika, R., Kumar, A., Janakiraman, R., & Bezawada, R. (2013). The effect of customers' social media participation on customer visit frequency and profitability: An empirical investigation. Information Systems Research, 24 (1), 108–127.
Rosenberger, M., Lehrer, C., & Jung, R. (2017). Integrating data from user activities of social networks into public administrations. Information Systems Frontiers, 19 (2), 253–266.
Schlagwein, D., & Hu, M. (2016). How and why organisations use social media: Five use types and their relation to absorptive capacity. Journal of Information Technology, 32 (2), 194–209.
Shen, A. X., Lee, M. K., Cheung, C. M., & Chen, H. (2010). Gender differences in intentional social action: We-intention to engage in social network-facilitated team collaboration. Journal of Information Technology, 25 (2), 152–169.
Shi, Z., & Whinston, A. B. (2013). Network structure and observational learning: Evidence from a location-based social network. Journal of Management Information Systems, 30 (2), 185–212.
Shi, Z., Rui, H., & Whinston, A. B. (2014). Content sharing in a social broadcasting environment: Evidence from twitter. MIS Quarterly, 38 (1), 123–142.
Singh, P. V., Sahoo, N., & Mukhopadhyay, T. (2014). How to attract and retain readers in Enterprise blogging? Information Systems Research, 25 (1), 35–52.
Spagnoletti, P., Resca, A., & Sæbø, Ø. (2015). Design for Social Media Engagement: Insights from elderly care assistance. The Journal of Strategic Information Systems, 24 (2), 128–145.
Stanko, M. A. (2016). Toward a theory of remixing in online innovation communities. Information Systems Research, 27 (4), 773–791.
Statista. (2017). Most famous social network sites worldwide as of April 2017, Ranked by number of active users (in millions). Available at: https://www.statista.com/statistics/272014/global-social-networks-ranked-by-number-of-users/ . Accessed 22 June 2017.
Stieglitz, S., & Dang-Xuan, L. (2013). Emotions and information diffusion in social media—Sentiment of microblogs and sharing behavior. Journal of Management Information Systems, 29 (4), 217–248.
Subramaniam, N., & Nandhakumar, J. (2013). Exploring social network interactions in enterprise systems: The role of virtual co-presence. Information Systems Journal, 23 (6), 475–499.
Sung, Y. S., Wang, D., & Kumara, S. (2016). Uncovering the effect of dominant attributes on community topology: A case of facebook networks. Information Systems Frontiers , 1–12. https://doi.org/10.1007/s10796-016-9696-0 .
Susarla, A., Oh, J. H., & Tan, Y. (2012). Social networks and the diffusion of user-generated content: Evidence from YouTube. Information Systems Research, 23 (1), 23–41.
Susarla, A., Oh, J. H., & Tan, Y. (2016). Influentials, Imitables, or Susceptibles? Virality and word-of-mouth conversations in online social networks. Journal of Management Information Systems, 33 (1), 139–170.
Tang, Q., Gu, B., & Whinston, A. B. (2012). Content contribution for revenue sharing and reputation in social media: A dynamic structural model. Journal of Management Information Systems, 29 (2), 41–76.
Tow, W. N. F. H., Dell, P., & Venable, J. (2010). Understanding information disclosure behaviour in Australian Facebook users. Journal of Information Technology, 25 (2), 126–136.
Trier, M., & Richter, A. (2015). The deep structure of organizational online networking–an actor-oriented case study. Information Systems Journal, 25 (5), 465–488.
Turel, O. (2015). Quitting the use of a habituated hedonic information system: A theoretical model and empirical examination of Facebook users. European Journal of Information Systems, 24 (4), 431–446.
Turel, O., & Serenko, A. (2012). The benefits and dangers of enjoyment with social networking websites. European Journal of Information Systems, 21 (5), 512–528.
Van Eck, N. J., & Waltman, L. (2011). Text mining and visualization using VOSviewer, ISSI . Newsletter, 7 (3), 50–54.
Van Osch, W., & Steinfield, C. W. (2016). Team boundary spanning: Strategic implications for the implementation and use of enterprise social media. Journal of Information Technology, 31 (2), 207–225.
Venkatesh, V., Morris, M. G., Davis, G. B., & Davis, F. D. (2003). User acceptance of information technology: Toward a unified view. MIS Quarterly, 27 (3), 425–478.
Vishwanath, A. (2015). Diffusion of deception in social media: Social contagion effects and its antecedents. Information Systems Frontiers, 17 (6), 1353–1367.
Wakefield, R., & Wakefield, K. (2016). Social media network behavior: A study of user passion and affect. The Journal of Strategic Information Systems, 25 (2), 140–156.
Wang, Y., Zeng, D., Zhu, B., Zheng, X., & Wang, F. (2014). Patterns of news dissemination through online news media: A case study in China. Information Systems Frontiers, 16 (4), 557–570.
Wattal, S., Schuff, D., Mandviwalla, M., & Williams, C. B. (2010). Web 2.0 and politics: The 2008 US presidential election and an e-politics research agenda. MIS Quarterly, 34 (4), 669–688.
Wei, C., Khoury, R., & Fong, S. (2013). Web 2.0 recommendation service by multi-collaborative filtering trust network algorithm. Information Systems Frontiers, 15 (4), 533–551.
White, H. D., & Griffith, B. C. (1981). Author Cocitation: A literature measure of intellectual structure. Journal of the American Society for Information Science, 32 (3), 163–171.
Wu, L. (2013). Social network effects on productivity and job security: Evidence from the adoption of a social networking tool. Information Systems Research, 24 (1), 30–51.
Wu, J., & Gaytán, E. A. A. (2013). The role of online seller reviews and product price on buyers' willingness-to-pay: A risk perspective. European Journal of Information Systems, 22 (4), 416–433.
Xie, K., & Lee, Y. J. (2015). Social media and brand purchase: Quantifying the effects of exposures to earned and owned social media activities in a two-stage decision making model. Journal of Management Information Systems, 32 (2), 204–238.
Xu, S. X., & Zhang, X. M. (2013). Impact of Wikipedia on market information environment: Evidence on management disclosure and investor reaction. MIS Quarterly, 37 (4), 1043–1068.
Xu, Y. C., Yang, Y., Cheng, Z., & Lim, J. (2014). Retaining and attracting users in social networking services: An empirical investigation of cyber migration. The Journal of Strategic Information Systems, 23 (3), 239–253.
Xu, B., Xu, Z., & Li, D. (2016). Internet aggression in online communities: A contemporary deterrence perspective. Information Systems Journal, 26 (6), 641–667.
Yan, L., & Tan, Y. (2014). Feeling blue? Go online: An empirical study of social support among patients. Information Systems Research, 25 (4), 690–709.
Yan, L., Peng, J., & Tan, Y. (2015a). Network dynamics: How can we find patients like us? Information Systems Research, 26 (3), 496–512.
Yan, X., Wang, J., & Chau, M. (2015b). Customer revisit intention to restaurants: Evidence from online reviews. Information Systems Frontiers, 17 (3), 645–657.
Yu, J., Hu, P. J. H., & Cheng, T. H. (2015). Role of affect in self-disclosure on social network websites: A test of two competing models. Journal of Management Information Systems, 32 (2), 239–277.
Zeng, X., & Wei, L. (2013). Social ties and user content generation: Evidence from Flickr. Information Systems Research, 24 (1), 71–87.
Zhang, J., & Piramuthu, S. (2016). Product recommendation with latent review topics. Information Systems Frontiers , 1–9. https://doi.org/10.1007/s10796-016-9697-z .
Zhang, X., & Wang, C. (2012). Network positions and contributions to online public goods: The case of Chinese Wikipedia. Journal of Management Information Systems, 29 (2), 11–40.
Zhang, D., Zhou, L., Kehoe, J. L., & Kilic, I. Y. (2016). What online reviewer behaviors really matter? Effects of verbal and nonverbal behaviors on detection of fake online reviews. Journal of Management Information Systems, 33 (2), 456–481.
Zhao, L., Detlor, B., & Connelly, C. E. (2016). Sharing knowledge in Social Q&a Sites: The unintended consequences of extrinsic motivation. Journal of Management Information Systems, 33 (1), 70–100.
Download references
Author information
Authors and affiliations.
Eastern Gateway Building, Brunel University London, Uxbridge, UB8 3PH, UK
Kawaljeet Kaur Kapoor
Emerging Markets Research Centre (EMaRC), School of Management, Swansea University Bay Campus, Swansea, SA1 8EN, UK
Kuttimani Tamilmani, Nripendra P. Rana, Pushp Patil & Yogesh K. Dwivedi
Information Systems & Operations Management, University of Texas at Arlington, Arlington, TX, 76019, USA
Sridhar Nerur
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Nripendra P. Rana .
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Kapoor, K.K., Tamilmani, K., Rana, N.P. et al. Advances in Social Media Research: Past, Present and Future. Inf Syst Front 20 , 531–558 (2018). https://doi.org/10.1007/s10796-017-9810-y
Download citation
Published : 06 November 2017
Issue Date : June 2018
DOI : https://doi.org/10.1007/s10796-017-9810-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Information systems
- Social networks
- Social media research
- Systematic review
Advertisement
- Find a journal
- Publish with us
- Track your research
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- HHS Author Manuscripts

Social Media and Mental Health: Benefits, Risks, and Opportunities for Research and Practice
John a. naslund.
a Department of Global Health and Social Medicine, Harvard Medical School, Boston, MA
Ameya Bondre
b CareNX Innovations, Mumbai, India
John Torous
c Department of Psychiatry, Beth Israel Deaconess Medical Center, Boston, MA
Kelly A. Aschbrenner
d Department of Psychiatry, Geisel School of Medicine at Dartmouth, Lebanon, NH
Social media platforms are popular venues for sharing personal experiences, seeking information, and offering peer-to-peer support among individuals living with mental illness. With significant shortfalls in the availability, quality, and reach of evidence-based mental health services across the United States and globally, social media platforms may afford new opportunities to bridge this gap. However, caution is warranted, as numerous studies highlight risks of social media use for mental health. In this commentary, we consider the role of social media as a potentially viable intervention platform for offering support to persons with mental disorders, promoting engagement and retention in care, and enhancing existing mental health services. Specifically, we summarize current research on the use of social media among mental health service users, and early efforts using social media for the delivery of evidence-based programs. We also review the risks, potential harms, and necessary safety precautions with using social media for mental health. To conclude, we explore opportunities using data science and machine learning, for example by leveraging social media for detecting mental disorders and developing predictive models aimed at characterizing the aetiology and progression of mental disorders. These various efforts using social media, as summarized in this commentary, hold promise for improving the lives of individuals living with mental disorders.
Introduction
Social media has become a prominent fixture in the lives of many individuals facing the challenges of mental illness. Social media refers broadly to web and mobile platforms that allow individuals to connect with others within a virtual network (such as Facebook, Twitter, Instagram, Snapchat, or LinkedIn), where they can share, co-create, or exchange various forms of digital content, including information, messages, photos, or videos ( Ahmed, Ahmad, Ahmad, & Zakaria, 2019 ). Studies have reported that individuals living with a range of mental disorders, including depression, psychotic disorders, or other severe mental illnesses, use social media platforms at comparable rates as the general population, with use ranging from about 70% among middle-age and older individuals, to upwards of 97% among younger individuals ( Aschbrenner, Naslund, Grinley, et al., 2018 ; M. L. Birnbaum, Rizvi, Correll, Kane, & Confino, 2017 ; Brunette et al., 2019 ; Naslund, Aschbrenner, & Bartels, 2016 ). Other exploratory studies have found that many of these individuals with mental illness appear to turn to social media to share their personal experiences, seek information about their mental health and treatment options, and give and receive support from others facing similar mental health challenges ( Bucci, Schwannauer, & Berry, 2019 ; Naslund, Aschbrenner, Marsch, & Bartels, 2016b ).
Across the United States and globally, very few people living with mental illness have access to adequate mental health services ( Patel et al., 2018 ). The wide reach and near ubiquitous use of social media platforms may afford novel opportunities to address these shortfalls in existing mental health care, by enhancing the quality, availability, and reach of services. Recent studies have explored patterns of social media use, impact of social media use on mental health and wellbeing, and the potential to leverage the popularity and interactive features of social media to enhance the delivery of interventions. However, there remains uncertainty regarding the risks and potential harms of social media for mental health ( Orben & Przybylski, 2019 ), and how best to weigh these concerns against potential benefits.
In this commentary, we summarized current research on the use of social media among individuals with mental illness, with consideration of the impact of social media on mental wellbeing, as well as early efforts using social media for delivery of evidence-based programs for addressing mental health problems. We searched for recent peer reviewed publications in Medline and Google Scholar using the search terms “mental health” or “mental illness” and “social media”, and searched the reference lists of recent reviews and other relevant studies. We reviewed the risks, potential harms, and necessary safety precautions with using social media for mental health. Overall, our goal was to consider the role of social media as a potentially viable intervention platform for offering support to persons with mental disorders, promoting engagement and retention in care, and enhancing existing mental health services, while balancing the need for safety. Given this broad objective, we did not perform a systematic search of the literature and we did not apply specific inclusion criteria based on study design or type of mental disorder.
Social Media Use and Mental Health
In 2020, there are an estimated 3.8 billion social media users worldwide, representing half the global population ( We Are Social, 2020 ). Recent studies have shown that individuals with mental disorders are increasingly gaining access to and using mobile devices, such as smartphones ( Firth et al., 2015 ; Glick, Druss, Pina, Lally, & Conde, 2016 ; Torous, Chan, et al., 2014 ; Torous, Friedman, & Keshavan, 2014 ). Similarly, there is mounting evidence showing high rates of social media use among individuals with mental disorders, including studies looking at engagement with these popular platforms across diverse settings and disorder types. Initial studies from 2015 found that nearly half of a sample of psychiatric patients were social media users, with greater use among younger individuals ( Trefflich, Kalckreuth, Mergl, & Rummel-Kluge, 2015 ), while 47% of inpatients and outpatients with schizophrenia reported using social media, of which 79% reported at least once-a-week usage of social media websites ( Miller, Stewart, Schrimsher, Peeples, & Buckley, 2015 ). Rates of social media use among psychiatric populations have increased in recent years, as reflected in a study with data from 2017 showing comparable rates of social media use (approximately 70%) among individuals with serious mental illness in treatment as compared to low-income groups from the general population ( Brunette et al., 2019 ).
Similarly, among individuals with serious mental illness receiving community-based mental health services, a recent study found equivalent rates of social media use as the general population, even exceeding 70% of participants ( Naslund, Aschbrenner, & Bartels, 2016 ). Comparable findings were demonstrated among middle-age and older individuals with mental illness accessing services at peer support agencies, where 72% of respondents reported using social media ( Aschbrenner, Naslund, Grinley, et al., 2018 ). Similar results, with 68% of those with first episode psychosis using social media daily were reported in another study ( Abdel-Baki, Lal, D.-Charron, Stip, & Kara, 2017 ).
Individuals who self-identified as having a schizophrenia spectrum disorder responded to a survey shared through the National Alliance of Mental Illness (NAMI), and reported that visiting social media sites was one of their most common activities when using digital devices, taking up roughly 2 hours each day ( Gay, Torous, Joseph, Pandya, & Duckworth, 2016 ). For adolescents and young adults ages 12 to 21 with psychotic disorders and mood disorders, over 97% reported using social media, with average use exceeding 2.5 hours per day ( M. L. Birnbaum et al., 2017 ). Similarly, in a sample of adolescents ages 13-18 recruited from community mental health centers, 98% reported using social media, with YouTube as the most popular platform, followed by Instagram and Snapchat ( Aschbrenner et al., 2019 ).
Research has also explored the motivations for using social media as well as the perceived benefits of interacting on these platforms among individuals with mental illness. In the sections that follow (see Table 1 for a summary), we consider three potentially unique features of interacting and connecting with others on social media that may offer benefits for individuals living with mental illness. These include: 1) Facilitate social interaction; 2) Access to a peer support network; and 3) Promote engagement and retention in services.
Summary of potential benefits and challenges with social media for mental health
| Features of Social Media | Examples | Studies |
|---|---|---|
| 1) Facilitate social interaction | • Online interactions may be easier for individuals with impaired social functioning and facing symptoms • Anonymity can help individuals with stigmatizing conditions connect with others • Young adults with mental illness commonly form online relationships • Social media use in individuals with serious mental illness associated with greater community and civic engagement • Individuals with depressive symptoms prefer communicating on social media than in-person • Online conversations do not require iimnediate responses or non-verbal cues | ( ; ; ; ; ; ; ; ) |
| 2) Access to peer support network | • Online peer support helps seek information, discuss symptoms and medication, share experiences, learn to cope and for self-disclosure. • Individuals with mental disorders establish new relationships, feel less alone or reconnect with people. • Various support patterns are noted in these networks (e.g. ‘informational’, ‘esteem’, ‘network’ and ‘emotional’) | ( ; ; ; ; ; ; ; ; ) |
| 3) Promote engagement and retention in services | • Individuals with mental disorders connect with care providers and access evidence-based services • Online peer support augments existing interventions to improve client engagement and compliance. • Peer networks increase social connectedness and empowerment during recovery. • Interactive peer-to-peer features of social media enhance social functioning • Mobile apps can monitor symptoms, prevent relapses and help users set goals • Digital peer-based interventions target fitness and weight loss in people with mental disorders • Online networks support caregivers of those with mental disorders | ( ; ; ; ; ; ; ; ; ; ; ; ; ) |
| 1) Impact on symptoms | • Studies show increased exposure to harm, social isolation, depressive symptoms and bullying • Social comparison pressure and social isolation after being rejected on social media is coimnon • More frequent visits and more nmnber of social media platforms has been linked with greater depressive symptoms, anxiety and suicide • Social media replaces in-person interactions to contribute to greater loneliness and worsens existing mental symptoms | ( ; ; ; ; ; ; ; ; ; ; ; ) |
| 2) Facing hostile interactions | • Cyberbullying is associated with increased depressive and anxiety symptoms • Greater odds of online harassment in individuals with major depressive symptoms than those with mild or no symptoms. | ( ; ; ; ) |
| 3) Consequences for daily life | • Risks pertain to privacy, confidentiality, and unintended consequences of disclosing personal health information • Misleading information or conflicts of interest, when the platforms promote popular content • Individuals have concerns about privacy, threats to employment, stigma and being judged, adverse impact on relationships and online hostility | ( ; ; ; ) |
Facilitate Social Interaction
Social media platforms offer near continuous opportunities to connect and interact with others, regardless of time of day or geographic location. This on demand ease of communication may be especially important for facilitating social interaction among individuals with mental disorders experiencing difficulties interacting in face-to-face settings. For example, impaired social functioning is a common deficit in schizophrenia spectrum disorders, and social media may facilitate communication and interacting with others for these individuals ( Torous & Keshavan, 2016 ). This was suggested in one study where participants with schizophrenia indicated that social media helped them to interact and socialize more easily ( Miller et al., 2015 ). Like other online communication, the ability to connect with others anonymously may be an important feature of social media, especially for individuals living with highly stigmatizing health conditions ( Berger, Wagner, & Baker, 2005 ), such as serious mental disorders ( Highton-Williamson, Priebe, & Giacco, 2015 ).
Studies have found that individuals with serious mental disorders ( Spinzy, Nitzan, Becker, Bloch, & Fennig, 2012 ) as well as young adults with mental illness ( Gowen, Deschaine, Gruttadara, & Markey, 2012 ) appear to form online relationships and connect with others on social media as often as social media users from the general population. This is an important observation because individuals living with serious mental disorders typically have few social contacts in the offline world, and also experience high rates of loneliness ( Badcock et al., 2015 ; Giacco, Palumbo, Strappelli, Catapano, & Priebe, 2016 ). Among individuals receiving publicly funded mental health services who use social media, nearly half (47%) reported using these platforms at least weekly to feel less alone ( Brusilovskiy, Townley, Snethen, & Salzer, 2016 ). In another study of young adults with serious mental illness, most indicated that they used social media to help feel less isolated ( Gowen et al., 2012 ). Interestingly, more frequent use of social media among a sample of individuals with serious mental illness was associated with greater community participation, measured as participation in shopping, work, religious activities or visiting friends and family, as well as greater civic engagement, reflected as voting in local elections ( Brusilovskiy et al., 2016 ).
Emerging research also shows that young people with moderate to severe depressive symptoms appear to prefer communicating on social media rather than in-person ( Rideout & Fox, 2018 ), while other studies have found that some individuals may prefer to seek help for mental health concerns online rather than through in-person encounters ( Batterham & Calear, 2017 ). In a qualitative study, participants with schizophrenia described greater anonymity, the ability to discover that other people have experienced similar health challenges, and reducing fears through greater access to information as important motivations for using the Internet to seek mental health information ( Schrank, Sibitz, Unger, & Amering, 2010 ). Because social media does not require the immediate responses necessary in face-to-face communication, it may overcome deficits with social interaction due to psychotic symptoms that typically adversely affect face-to-face conversations ( Docherty et al., 1996 ). Online social interactions may not require the use of non-verbal cues, particularly in the initial stages of interaction ( Kiesler, Siegel, & McGuire, 1984 ), with interactions being more fluid, and within the control of users, thereby overcoming possible social anxieties linked to in-person interaction ( Indian & Grieve, 2014 ). Furthermore, many individuals with serious mental disorders can experience symptoms including passive social withdrawal, blunted affect and attentional impairment, as well as active social avoidance due to hallucinations or other concerns ( Hansen, Torgalsbøen, Melle, & Bell, 2009 ); thus, potentially reinforcing the relative advantage, as perceived by users, of using social media over in person conversations.
Access to a Peer Support Network
There is growing recognition about the role that social media channels could play in enabling peer support ( Bucci et al., 2019 ; Naslund, Aschbrenner, et al., 2016b ), referred to as a system of mutual giving and receiving where individuals who have endured the difficulties of mental illness can offer hope, friendship, and support to others facing similar challenges ( Davidson, Chinman, Sells, & Rowe, 2006 ; Mead, Hilton, & Curtis, 2001 ). Initial studies exploring use of online self-help forums among individuals with serious mental illnesses have found that individuals with schizophrenia appeared to use these forums for self-disclosure, and sharing personal experiences, in addition to providing or requesting information, describing symptoms, or discussing medication ( Haker, Lauber, & Rössler, 2005 ), while users with bipolar disorder reported using these forums to ask for help from others about their illness ( Vayreda & Antaki, 2009 ). More recently, in a review of online social networking in people with psychosis, Highton-Williamson et al (2015) highlight that an important purpose of such online connections was to establish new friendships, pursue romantic relationships, maintain existing relationships or reconnect with people, and seek online peer support from others with lived experience ( Highton-Williamson et al., 2015 ).
Online peer support among individuals with mental illness has been further elaborated in various studies. In a content analysis of comments posted to YouTube by individuals who self-identified as having a serious mental illness, there appeared to be opportunities to feel less alone, provide hope, find support and learn through mutual reciprocity, and share coping strategies for day-to-day challenges of living with a mental illness ( Naslund, Grande, Aschbrenner, & Elwyn, 2014 ). In another study, Chang (2009) delineated various communication patterns in an online psychosis peer-support group ( Chang, 2009 ). Specifically, different forms of support emerged, including ‘informational support’ about medication use or contacting mental health providers, ‘esteem support’ involving positive comments for encouragement, ‘network support’ for sharing similar experiences, and ‘emotional support’ to express understanding of a peer’s situation and offer hope or confidence ( Chang, 2009 ). Bauer et al. (2013) reported that the main interest in online self-help forums for patients with bipolar disorder was to share emotions with others, allow exchange of information, and benefit by being part of an online social group ( Bauer, Bauer, Spiessl, & Kagerbauer, 2013 ).
For individuals who openly discuss mental health problems on Twitter, a study by Berry et al. (2017) found that this served as an important opportunity to seek support and to hear about the experiences of others ( Berry et al., 2017 ). In a survey of social media users with mental illness, respondents reported that sharing personal experiences about living with mental illness and opportunities to learn about strategies for coping with mental illness from others were important reasons for using social media ( Naslund et al., 2017 ). A computational study of mental health awareness campaigns on Twitter provides further support with inspirational posts and tips being the most shared ( Saha et al., 2019 ). Taken together, these studies offer insights about the potential for social media to facilitate access to an informal peer support network, though more research is necessary to examine how these online interactions may impact intentions to seek care, illness self-management, and clinically meaningful outcomes in offline contexts.
Promote Engagement and Retention in Services
Many individuals living with mental disorders have expressed interest in using social media platforms for seeking mental health information ( Lal, Nguyen, & Theriault, 2018 ), connecting with mental health providers ( M. L. Birnbaum et al., 2017 ), and accessing evidence-based mental health services delivered over social media specifically for coping with mental health symptoms or for promoting overall health and wellbeing ( Naslund et al., 2017 ). With the widespread use of social media among individuals living with mental illness combined with the potential to facilitate social interaction and connect with supportive peers, as summarized above, it may be possible to leverage the popular features of social media to enhance existing mental health programs and services. A recent review by Biagianti et al (2018) found that peer-to-peer support appeared to offer feasible and acceptable ways to augment digital mental health interventions for individuals with psychotic disorders by specifically improving engagement, compliance, and adherence to the interventions, and may also improve perceived social support ( Biagianti, Quraishi, & Schlosser, 2018 ).
Among digital programs that have incorporated peer-to-peer social networking consistent with popular features on social media platforms, a pilot study of the HORYZONS online psychosocial intervention demonstrated significant reductions in depression among patients with first episode psychosis ( Alvarez-Jimenez et al., 2013 ). Importantly, the majority of participants (95%) in this study engaged with the peer-to-peer networking feature of the program, with many reporting increases in perceived social connectedness and empowerment in their recovery process ( Alvarez-Jimenez et al., 2013 ). This moderated online social therapy program is now being evaluated as part of a large randomized controlled trial for maintaining treatment effects from first episode psychosis services ( Alvarez-Jimenez et al., 2019 ).
Other early efforts have demonstrated that use of digital environments with the interactive peer-to-peer features of social media can enhance social functioning and wellbeing in young people at high risk of psychosis ( Alvarez-Jimenez et al., 2018 ). There has also been a recent emergence of several mobile apps to support symptom monitoring and relapse prevention in psychotic disorders. Among these apps, the development of PRIME (Personalized Real-time Intervention for Motivational Enhancement) has involved working closely with young people with schizophrenia to ensure that the design of the app has the look and feel of mainstream social media platforms, as opposed to existing clinical tools ( Schlosser et al., 2016 ). This unique approach to the design of the app is aimed at promoting engagement, and ensuring that the app can effectively improve motivation and functioning through goal setting and promoting better quality of life of users with schizophrenia ( Schlosser et al., 2018 ).
Social media platforms could also be used to promote engagement and participation in in-person services delivered through community mental health settings. For example, the peer-based lifestyle intervention called PeerFIT targets weight loss and improved fitness among individuals living with serious mental illness through a combination of in-person lifestyle classes, exercise groups, and use of digital technologies ( Aschbrenner, Naslund, Shevenell, Kinney, & Bartels, 2016 ; Aschbrenner, Naslund, Shevenell, Mueser, & Bartels, 2016 ). The intervention holds tremendous promise as lack of support is one of the largest barriers toward exercise in patients with serious mental illness ( Firth et al., 2016 ) and it is now possible to use social media to counter such. Specifically, in PeerFIT, a private Facebook group is closely integrated into the program to offer a closed platform where participants can connect with the lifestyle coaches, access intervention content, and support or encourage each other as they work towards their lifestyle goals ( Aschbrenner, Naslund, & Bartels, 2016 ; Naslund, Aschbrenner, Marsch, & Bartels, 2016a ). To date, this program has demonstrate preliminary effectiveness for meaningfully reducing cardiovascular risk factors that contribute to early mortality in this patient group ( Aschbrenner, Naslund, Shevenell, Kinney, et al., 2016 ), while the Facebook component appears to have increased engagement in the program, while allowing participants who were unable to attend in-person sessions due to other health concerns or competing demands to remain connected with the program ( Naslund, Aschbrenner, Marsch, McHugo, & Bartels, 2018 ). This lifestyle intervention is currently being evaluated in a randomized controlled trial enrolling young adults with serious mental illness from a variety of real world community mental health services settings ( Aschbrenner, Naslund, Gorin, et al., 2018 ).
These examples highlight the promise of incorporating the features of popular social media into existing programs, which may offer opportunities to safely promote engagement and program retention, while achieving improved clinical outcomes. This is an emerging area of research, as evidenced by several important effectiveness trials underway ( Alvarez-Jimenez et al., 2019 ; Aschbrenner, Naslund, Gorin, et al., 2018 ), including efforts to leverage online social networking to support family caregivers of individuals receiving first episode psychosis services ( Gleeson et al., 2017 ).
Challenges with Social Media for Mental Health
The science on the role of social media for engaging persons with mental disorders needs a cautionary note on the effects of social media usage on mental health and well being, particularly in adolescents and young adults. While the risks and harms of social media are frequently covered in the popular press and mainstream news reports, careful consideration of the research in this area is necessary. In a review of 43 studies in young people, many benefits of social media were cited, including increased self-esteem, and opportunities for self-disclosure ( Best, Manktelow, & Taylor, 2014 ). Yet, reported negative effects were an increased exposure to harm, social isolation, depressive symptoms and bullying ( Best et al., 2014 ). In the sections that follow (see Table 1 for a summary), we consider three major categories of risk related to use of social media and mental health. These include: 1) Impact on symptoms; 2) Facing hostile interactions; and 3) Consequences for daily life.
Impact on Symptoms
Studies consistently highlight that use of social media, especially heavy use and prolonged time spent on social media platforms, appears to contribute to increased risk for a variety of mental health symptoms and poor wellbeing, especially among young people ( Andreassen et al., 2016 ; Kross et al., 2013 ; Woods & Scott, 2016 ). This may partly be driven by the detrimental effects of screen time on mental health, including increased severity of anxiety and depressive symptoms, which have been well documented ( Stiglic & Viner, 2019 ). Recent studies have reported negative effects of social media use on mental health of young people, including social comparison pressure with others and greater feeling of social isolation after being rejected by others on social media ( Rideout & Fox, 2018 ). In a study of young adults, it was found that negative comparisons with others on Facebook contributed to risk of rumination and subsequent increases in depression symptoms ( Feinstein et al., 2013 ). Still, the cross sectional nature of many screen time and mental health studies makes it challenging to reach causal inferences ( Orben & Przybylski, 2019 ).
Quantity of social media use is also an important factor, as highlighted in a survey of young adults ages 19 to 32, where more frequent visits to social media platforms each week were correlated with greater depressive symptoms ( Lin et al., 2016 ). More time spent using social media is also associated with greater symptoms of anxiety ( Vannucci, Flannery, & Ohannessian, 2017 ). The actual number of platforms accessed also appears to contribute to risk as reflected in another national survey of young adults where use of a large number of social media platforms was associated with negative impact on mental health ( Primack et al., 2017 ). Among survey respondents using between 7 and 11 different social media platforms compared to respondents using only 2 or fewer platforms, there was a 3 times greater odds of having high levels of depressive symptoms and a 3.2 times greater odds of having high levels of anxiety symptoms ( Primack et al., 2017 ).
Many researchers have postulated that worsening mental health attributed to social media use may be because social media replaces face-to-face interactions for young people ( Twenge & Campbell, 2018 ), and may contribute to greater loneliness ( Bucci et al., 2019 ), and negative effects on other aspects of health and wellbeing ( Woods & Scott, 2016 ). One nationally representative survey of US adolescents found that among respondents who reported more time accessing media such as social media platforms or smartphone devices, there was significantly greater depressive symptoms and increased risk of suicide when compared to adolescents who reported spending more time on non-screen activities, such as in-person social interaction or sports and recreation activities ( Twenge, Joiner, Rogers, & Martin, 2018 ). For individuals living with more severe mental illnesses, the effects of social media on psychiatric symptoms have received less attention. One study found that participation in chat rooms may contribute to worsening symptoms in young people with psychotic disorders ( Mittal, Tessner, & Walker, 2007 ), while another study of patients with psychosis found that social media use appeared to predict low mood ( Berry, Emsley, Lobban, & Bucci, 2018 ). These studies highlight a clear relationship between social media use and mental health that may not be present in general population studies ( Orben & Przybylski, 2019 ), and emphasize the need to explore how social media may contribute to symptom severity and whether protective factors may be identified to mitigate these risks.
Facing Hostile Interactions
Popular social media platforms can create potential situations where individuals may be victimized by negative comments or posts. Cyberbullying represents a form of online aggression directed towards specific individuals, such as peers or acquaintances, which is perceived to be most harmful when compared to random hostile comments posted online ( Hamm et al., 2015 ). Importantly, cyberbullying on social media consistently shows harmful impact on mental health in the form of increased depressive symptoms as well as worsening of anxiety symptoms, as evidenced in a review of 36 studies among children and young people ( Hamm et al., 2015 ). Furthermore, cyberbullying disproportionately impacts females as reflected in a national survey of adolescents in the United States, where females were twice as likely to be victims of cyberbullying compared to males ( Alhajji, Bass, & Dai, 2019 ). Most studies report cross-sectional associations between cyberbullying and symptoms of depression or anxiety ( Hamm et al., 2015 ), though one longitudinal study in Switzerland found that cyberbullying contributed to significantly greater depression over time ( Machmutow, Perren, Sticca, & Alsaker, 2012 ).
For youth ages 10 to 17 who reported major depressive symptomatology, there was over 3 times greater odds of facing online harassment in the last year compared to youth who reported mild or no depressive symptoms ( Ybarra, 2004 ). Similarly, in a 2018 national survey of young people, respondents ages 14 to 22 with moderate to severe depressive symptoms were more likely to have had negative experiences when using social media, and in particular, were more likely to report having faced hostile comments, or being “trolled”, from others when compared to respondents without depressive symptoms (31% vs. 14%) ( Rideout & Fox, 2018 ). As these studies depict risks for victimization on social media and the correlation with poor mental health, it is possible that individuals living with mental illness may also experience greater hostility online compared to individuals without mental illness. This would be consistent with research showing greater risk of hostility, including increased violence and discrimination, directed towards individuals living with mental illness in in-person contexts, especially targeted at those with severe mental illnesses ( Goodman et al., 1999 ).
A computational study of mental health awareness campaigns on Twitter reported that while stigmatizing content was rare, it was actually the most spread (re-tweeted) demonstrating that harmful content can travel quickly on social media ( Saha et al., 2019 ). Another study was able to map the spread of social media posts about the Blue Whale Challenge, an alleged game promoting suicide, over Twitter, YouTube, Reddit, Tumblr and other forums across 127 countries ( Sumner et al., 2019 ). These findings show that it is critical to monitor the actual content of social media posts, such as determining whether content is hostile or promotes harm to self or others. This is pertinent because existing research looking at duration of exposure cannot account for the impact of specific types of content on mental health and is insufficient to fully understand the effects of using these platforms on mental health.
Consequences for Daily Life
The ways in which individuals use social media can also impact their offline relationships and everyday activities. To date, reports have described risks of social media use pertaining to privacy, confidentiality, and unintended consequences of disclosing personal health information online ( Torous & Keshavan, 2016 ). Additionally, concerns have been raised about poor quality or misleading health information shared on social media, and that social media users may not be aware of misleading information or conflicts of interest especially when the platforms promote popular content regardless of whether it is from a trustworthy source ( Moorhead et al., 2013 ; Ventola, 2014 ). For persons living with mental illness there may be additional risks from using social media. A recent study that specifically explored the perspectives of social media users with serious mental illnesses, including participants with schizophrenia spectrum disorders, bipolar disorder, or major depression, found that over one third of participants expressed concerns about privacy when using social media ( Naslund & Aschbrenner, 2019 ). The reported risks of social media use were directly related to many aspects of everyday life, including concerns about threats to employment, fear of stigma and being judged, impact on personal relationships, and facing hostility or being hurt ( Naslund & Aschbrenner, 2019 ). While few studies have specifically explored the dangers of social media use from the perspectives of individuals living with mental illness, it is important to recognize that use of these platforms may contribute to risks that extend beyond worsening symptoms and that can affect different aspects of daily life.
In this commentary we considered ways in which social media may yield benefits for individuals living with mental illness, while contrasting these with the possible harms. Studies reporting on the threats of social media for individuals with mental illness are mostly cross-sectional, making it difficult to draw conclusions about direction of causation. However, the risks are potentially serious. These risks should be carefully considered in discussions pertaining to use of social media and the broader use of digital mental health technologies, as avenues for mental health promotion, or for supporting access to evidence-based programs or mental health services. At this point, it would be premature to view the benefits of social media as outweighing the possible harms, when it is clear from the studies summarized here that social media use can have negative effects on mental health symptoms, can potentially expose individuals to hurtful content and hostile interactions, and can result in serious consequences for daily life, including threats to employment and personal relationships. Despite these risks, it is also necessary to recognize that individuals with mental illness will continue to use social media given the ease of accessing these platforms and the immense popularity of online social networking. With this in mind, it may be ideal to raise awareness about these possible risks so that individuals can implement necessary safeguards, while also highlighting that there could also be benefits. For individuals with mental illness who use social media, being aware of the risks is an essential first step, and then highlighting ways that use of these popular platforms could also contribute to some benefits, ranging from finding meaningful interactions with others, engaging with peer support networks, and accessing information and services.
To capitalize on the widespread use of social media, and to achieve the promise that these platforms may hold for supporting the delivery of targeted mental health interventions, there is need for continued research to better understand how individuals living with mental illness use social media. Such efforts could inform safety measures and also encourage use of social media in ways that maximize potential benefits while minimizing risk of harm. It will be important to recognize how gender and race contribute to differences in use of social media for seeking mental health information or accessing interventions, as well as differences in how social media might impact mental wellbeing. For example, a national survey of 14- to 22-year olds in the United States found that female respondents were more likely to search online for information about depression or anxiety, and to try to connect with other people online who share similar mental health concerns, when compared to male respondents ( Rideout & Fox, 2018 ). In the same survey, there did not appear to be any differences between racial or ethnic groups in social media use for seeking mental health information ( Rideout & Fox, 2018 ). Social media use also appears to have a differential impact on mental health and emotional wellbeing between females and males ( Booker, Kelly, & Sacker, 2018 ), highlighting the need to explore unique experiences between gender groups to inform tailored programs and services. Research shows that lesbian, gay, bisexual or transgender individuals frequently use social media for searching for health information and may be more likely compared to heterosexual individuals to share their own personal health experiences with others online ( Rideout & Fox, 2018 ). Less is known about use of social media for seeking support for mental health concerns among gender minorities, though this is an important area for further investigation as these individuals are more likely to experience mental health problems and more likely to experience online victimization when compared to heterosexual individuals ( Mereish, Sheskier, Hawthorne, & Goldbach, 2019 ).
Similarly, efforts are needed to explore the relationship between social media use and mental health among ethnic and racial minorities. A recent study found that exposure to traumatic online content on social media showing violence or hateful posts directed at racial minorities contributed to increases in psychological distress, PTSD symptoms, and depression among African American and Latinx adolescents in the United States ( Tynes, Willis, Stewart, & Hamilton, 2019 ). These concerns are contrasted by growing interest in the potential for new technologies including social media to expand the reach of services to underrepresented minority groups ( Schueller, Hunter, Figueroa, & Aguilera, 2019 ). Therefore, greater attention is needed to understanding the perspectives of ethnic and racial minorities to inform effective and safe use of social media for mental health promotion efforts.
Research has found that individuals living with mental illness have expressed interest in accessing mental health services through social media platforms. A survey of social media users with mental illness found that most respondents were interested in accessing programs for mental health on social media targeting symptom management, health promotion, and support for communicating with health care providers and interacting with the health system ( Naslund et al., 2017 ). Importantly, individuals with serious mental illness have also emphasized that any mental health intervention on social media would need to be moderated by someone with adequate training and credentials, would need to have ground rules and ways to promote safety and minimize risks, and importantly, would need to be free and easy to access.
An important strength with this commentary is that it combines a range of studies broadly covering the topic of social media and mental health. We have provided a summary of recent evidence in a rapidly advancing field with the goal of presenting unique ways that social media could offer benefits for individuals with mental illness, while also acknowledging the potentially serious risks and the need for further investigation. There are also several limitations with this commentary that warrant consideration. Importantly, as we aimed to address this broad objective, we did not conduct a systematic review of the literature. Therefore, the studies reported here are not exhaustive, and there may be additional relevant studies that were not included. Additionally, we only summarized published studies, and as a result, any reports from the private sector or websites from different organizations using social media or other apps containing social media-like features would have been omitted. Though it is difficult to rigorously summarize work from the private sector, sometimes referred to as “gray literature”, because many of these projects are unpublished and are likely selective in their reporting of findings given the target audience may be shareholders or consumers.
Another notable limitation is that we did not assess risk of bias in the studies summarized in this commentary. We found many studies that highlighted risks associated with social media use for individuals living with mental illness; however, few studies of programs or interventions reported negative findings, suggesting the possibility that negative findings may go unpublished. This concern highlights the need for a future more rigorous review of the literature with careful consideration of bias and an accompanying quality assessment. Most of the studies that we described were from the United States, as well as from other higher income settings such as Australia or the United Kingdom. Despite the global reach of social media platforms, there is a dearth of research on the impact of these platforms on the mental health of individuals in diverse settings, as well as the ways in which social media could support mental health services in lower income countries where there is virtually no access to mental health providers. Future research is necessary to explore the opportunities and risks for social media to support mental health promotion in low-income and middle-income countries, especially as these countries face a disproportionate share of the global burden of mental disorders, yet account for the majority of social media users worldwide ( Naslund et al., 2019 ).
Future Directions for Social Media and Mental Health
As we consider future research directions, the near ubiquitous social media use also yields new opportunities to study the onset and manifestation of mental health symptoms and illness severity earlier than traditional clinical assessments. There is an emerging field of research referred to as ‘digital phenotyping’ aimed at capturing how individuals interact with their digital devices, including social media platforms, in order to study patterns of illness and identify optimal time points for intervention ( Jain, Powers, Hawkins, & Brownstein, 2015 ; Onnela & Rauch, 2016 ). Given that most people access social media via mobile devices, digital phenotyping and social media are closely related ( Torous et al., 2019 ). To date, the emergence of machine learning, a powerful computational method involving statistical and mathematical algorithms ( Shatte, Hutchinson, & Teague, 2019 ), has made it possible to study large quantities of data captured from popular social media platforms such as Twitter or Instagram to illuminate various features of mental health ( Manikonda & De Choudhury, 2017 ; Reece et al., 2017 ). Specifically, conversations on Twitter have been analyzed to characterize the onset of depression ( De Choudhury, Gamon, Counts, & Horvitz, 2013 ) as well as detecting users’ mood and affective states ( De Choudhury, Gamon, & Counts, 2012 ), while photos posted to Instagram can yield insights for predicting depression ( Reece & Danforth, 2017 ). The intersection of social media and digital phenotyping will likely add new levels of context to social media use in the near future.
Several studies have also demonstrated that when compared to a control group, Twitter users with a self-disclosed diagnosis of schizophrenia show unique online communication patterns ( Michael L Birnbaum, Ernala, Rizvi, De Choudhury, & Kane, 2017 ), including more frequent discussion of tobacco use ( Hswen et al., 2017 ), symptoms of depression and anxiety ( Hswen, Naslund, Brownstein, & Hawkins, 2018b ), and suicide ( Hswen, Naslund, Brownstein, & Hawkins, 2018a ). Another study found that online disclosures about mental illness appeared beneficial as reflected by fewer posts about symptoms following self-disclosure (Ernala, Rizvi, Birnbaum, Kane, & De Choudhury, 2017). Each of these examples offers early insights into the potential to leverage widely available online data for better understanding the onset and course of mental illness. It is possible that social media data could be used to supplement additional digital data, such as continuous monitoring using smartphone apps or smart watches, to generate a more comprehensive ‘digital phenotype’ to predict relapse and identify high-risk health behaviors among individuals living with mental illness ( Torous et al., 2019 ).
With research increasingly showing the valuable insights that social media data can yield about mental health states, greater attention to the ethical concerns with using individual data in this way is necessary ( Chancellor, Birnbaum, Caine, Silenzio, & De Choudhury, 2019 ). For instance, data is typically captured from social media platforms without the consent or awareness of users ( Bidargaddi et al., 2017 ), which is especially crucial when the data relates to a socially stigmatizing health condition such as mental illness ( Guntuku, Yaden, Kern, Ungar, & Eichstaedt, 2017 ). Precautions are needed to ensure that data is not made identifiable in ways that were not originally intended by the user who posted the content, as this could place an individual at risk of harm or divulge sensitive health information ( Webb et al., 2017 ; Williams, Burnap, & Sloan, 2017 ). Promising approaches for minimizing these risks include supporting the participation of individuals with expertise in privacy, clinicians, as well as the target individuals with mental illness throughout the collection of data, development of predictive algorithms, and interpretation of findings ( Chancellor et al., 2019 ).
In recognizing that many individuals living with mental illness use social media to search for information about their mental health, it is possible that they may also want to ask their clinicians about what they find online to check if the information is reliable and trustworthy. Alternatively, many individuals may feel embarrassed or reluctant to talk to their clinicians about using social media to find mental health information out of concerns of being judged or dismissed. Therefore, mental health clinicians may be ideally positioned to talk with their patients about using social media, and offer recommendations to promote safe use of these sites, while also respecting their patients’ autonomy and personal motivations for using these popular platforms. Given the gap in clinical knowledge about the impact of social media on mental health, clinicians should be aware of the many potential risks so that they can inform their patients, while remaining open to the possibility that their patients may also experience benefits through use of these platforms. As awareness of these risks grows, it may be possible that new protections will be put in place by industry or through new policies that will make the social media environment safer. It is hard to estimate a number needed to treat or harm today given the nascent state of research, which means the patient and clinician need to weigh the choice on a personal level. Thus offering education and information is an important first step in that process. As patients increasingly show interest in accessing mental health information or services through social media, it will be necessary for health systems to recognize social media as a potential avenue for reaching or offering support to patients. This aligns with growing emphasis on the need for greater integration of digital psychiatry, including apps, smartphones, or wearable devices, into patient care and clinical services through institution-wide initiatives and training clinical providers ( Hilty, Chan, Torous, Luo, & Boland, 2019 ). Within a learning healthcare environment where research and care are tightly intertwined and feedback between both is rapid, the integration of digital technologies into services may create new opportunities for advancing use of social media for mental health.
As highlighted in this commentary, social media has become an important part of the lives of many individuals living with mental disorders. Many of these individuals use social media to share their lived experiences with mental illness, to seek support from others, and to search for information about treatment recommendations, accessing mental health services, and coping with symptoms ( Bucci et al., 2019 ; Highton-Williamson et al., 2015 ; Naslund, Aschbrenner, et al., 2016b ). As the field of digital mental health advances, the wide reach, ease of access, and popularity of social media platforms could be used to allow individuals in need of mental health services or facing challenges of mental illness to access evidence-based treatment and support. To achieve this end and to explore whether social media platforms can advance efforts to close the gap in available mental health services in the United States and globally, it will be essential for researchers to work closely with clinicians and with those affected by mental illness to ensure that possible benefits of using social media are carefully weighed against anticipated risks.
Acknowledgements
Dr. Naslund is supported by a grant from the National Institute of Mental Health (U19MH113211). Dr. Aschbrenner is supported by a grant from the National Institute of Mental Health (1R01MH110965-01).
Publisher's Disclaimer: This Author Accepted Manuscript is a PDF file of a an unedited peer-reviewed manuscript that has been accepted for publication but has not been copyedited or corrected. The official version of record that is published in the journal is kept up to date and so may therefore differ from this version.
Conflict of Interest
The authors have nothing to disclose.
- Abdel-Baki A, Lai S, D.-Charron O, Stip E, & Kara N, (2017). Understanding access and use of technology among youth with first - episode psychosis to inform the development of technology - enabled therapeutic interventions . Early intervention in psychiatry , 77 ( 1 ), 72–76. [ PubMed ] [ Google Scholar ]
- Ahmed YA, Ahmad MN, Ahmad N, & Zakaria NH (2019). Social media for knowledge-sharing: A systematic literature review . Telematics and informatics , 37 , 72–112 . [ Google Scholar ]
- Alhajji M, Bass S, & Dai T (2019). Cyberbullying, mental health, and violence in adolescents and associations with sex and race: data from the 2015 Youth Risk Behavior Survey . Global pediatric health , 6 , 2333794X19868887. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Alvarez-Jimenez M, Bendall S, Koval P, Rice S, Cagliarini D, Valentine L, … Penn DL (2019). HORYZONS trial: protocol for a randomised controlled trial of a moderated online social therapy to maintain treatment effects from first-episode psychosis services . BMJ open , 9 ( 2 ), e024104. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Alvarez-Jimenez M, Bendall S, Lederman R, Wadley G, Chinnery G, Vargas S, … Gleeson JF (2013). On the HORYZON: moderated online social therapy for long-term recovery in first episode psychosis . Schizophrenia research , 143 ( 1 ), 143–149. [ PubMed ] [ Google Scholar ]
- Alvarez-Jimenez M, Gleeson J, Bendall S, Penn D, Yung A, Ryan R, … Miles C (2018). Enhancing social functioning in young people at Ultra High Risk (UHR) for psychosis: A pilot study of a novel strengths and mindfulness-based online social therapy . Schizophrenia research , 202 , 369–377. [ PubMed ] [ Google Scholar ]
- Andreassen CS, Billieux J, Griffiths MD, Kuss DJ, Demetrovics Z, Mazzoni E, & Pallesen S (2016). The relationship between addictive use of social media and video games and symptoms of psychiatric disorders: A large-scale cross-sectional study . Psychology of Addictive Behaviors , 30 ( 2 ), 252. [ PubMed ] [ Google Scholar ]
- Aschbrenner KA, Naslund JA, & Bartels SJ (2016). A mixed methods study of peer-to-peer support in a group-based lifestyle intervention for adults with serious mental illness . Psychiatric rehabilitation journal , 39 ( 4 ), 328. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Aschbrenner KA, Naslund JA, Gorin AA, Mueser KT, Scherer EA, Viron M, … Bartels SJ, (2018). Peer support and mobile health technology targeting obesity-related cardiovascular risk in young adults with serious mental illness: Protocol for a randomized controlled trial . Contemporary clinical trials , 74 , 97–106. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Aschbrenner KA, Naslund JA, Grinley T, Bienvenida JCM, Bartels SJ, & Brunette M (2018). A Survey of Online and Mobile Technology Use at Peer Support Agencies . Psychiatric Quarterly , 1–10. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Aschbrenner KA, Naslund JA, Shevenell M, Kinney E, & Bartels SJ (2016). A pilot study of a peer-group lifestyle intervention enhanced with mHealth technology and social media for adults with serious mental illness . The Journal of nervous and mental disease , 204 ( 6 ), 483–486. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Aschbrenner KA, Naslund JA, Shevenell M, Mueser KT, & Bartels SJ (2016). Feasibility of behavioral weight loss treatment enhanced with peer support and mobile health technology for individuals with serious mental illness . Psychiatric Quarterly , 57 ( 3 ), 401–415. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Aschbrenner KA, Naslund JA, Tomlinson EF, Kinney A, Pratt SI, & Brunette MF (2019). Adolescents’ Use of Digital Technologies and Preferences for Mobile Health Coaching in Mental Health Settings . Frontiers in Public Health . [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Badcock JC, Shah S, Mackinnon A, Stain HJ, Galletly C, Jablensky A, & Morgan VA (2015). Loneliness in psychotic disorders and its association with cognitive function and symptom profile . Schizophrenia research , 169 ( 1-3 ), 268–273. [ PubMed ] [ Google Scholar ]
- Batterham PJ, & Calear AJ (2017). Preferences for internet-based mental health interventions in an adult online sample: Findings from ann online community survey . JMIR mental health , 4 ( 2 ), e26. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Bauer R, Bauer M, Spiessl H, & Kagerbauer T (2013). Cyber-support: an analysis of online self-help forums (online self-help forums in bipolar disorder) . Nordic journal of psychiatry , 67 ( 3 ), 185–190. [ PubMed ] [ Google Scholar ]
- Berger M, Wagner TH, & Baker LC (2005). Internet use and stigmatized illness . Social science & medicine , 67 ( 8 ), 1821–1827. [ PubMed ] [ Google Scholar ]
- Berry N, Emsley R, Lobban F, & Bucci S (2018). Social media and its relationship with mood, self - esteem and paranoia in psychosis . Acta Psychiatrica Scandinavica , 138 , 558–570. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Berry N, Lobban F, Belousov M, Emsley R, Nenadic G, & Bucci S (2017). # Why We Tweet MH: understanding why people use Twitter to discuss mental health problems . Journal of medical Internet research , 19 ( 4 ), e107. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Best P, Manktelow R, & Taylor B (2014). Online communication, social media and adolescent wellbeing: A systematic narrative review . Children and Youth Services Review , 41 , 27–36. [ Google Scholar ]
- Biagianti B, Quraishi SH, & Schlosser DA (2018). Potential benefits of incorporating peer-to-peer interactions into digital interventions for psychotic disorders: a systematic review . Psychiatric Services , 69 ( 4 ), 377–388. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Bidargaddi N, Musiat P, Makinen V-P, Ermes M, Schrader G, & Licinio J (2017). Digital footprints: facilitating large-scale environmental psychiatric research in naturalistic settings through data from everyday technologies . Molecular psychiatry , 22 ( 2 ), 164. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Birnbaum ML, Emala SK, Rizvi AF, De Choudhury M, & Kane JM (2017). A Collaborative Approach to Identifying Social Media Markers of Schizophrenia by Employing Machine Learning and Clinical Appraisals . Journal of medical Internet research , 79 ( 8 ), e289. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Birnbaum ML, Rizvi AF, Correll CU, Kane JM, & Confino J (2017). Role of social media and the Internet in pathways to care for adolescents and young adults with psychotic disorders and non - psychotic mood disorders . Early intervention in psychiatry , 77 ( 4 ), 290–295. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Booker CL, Kelly YJ, & Sacker A (2018). Gender differences in the associations between age trends of social media interaction and well-being among 10-15 year olds in the UK . BMC public health , 18 ( 1 ), 321. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Brunette M, Achtyes E, Pratt S, Stilwell K, Opperman M, Guarino S, & Kay-Lambkin F (2019). Use of smartphones, computers and social media among people with SMI: opportunity for intervention . Community mental health journal , 1–6. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Brusilovskiy E, Townley G, Snethen G, & Salzer MS (2016). Social media use, community participation and psychological well-being among individuals with serious mental illnesses . Computers in Human Behavior , 65 , 232–240. [ Google Scholar ]
- Bucci S, Schwannauer M, & Berry N (2019). The digital revolution and its impact on mental health care . Psychology and Psychotherapy: Theory, Research and Practice , 1–21. [ PubMed ] [ Google Scholar ]
- Chancellor S, Birnbaum ML, Caine ED, Silenzio V, & De Choudhury M (2019). A taxonomy of ethical tensions in inferring mental health states from social media . Paper presented at the Proceedings of the Conference on Fairness, Accountability, and Transparency. [ Google Scholar ]
- Chang HJ (2009). Online supportive interactions: Using a network approach to examine communication patterns within a psychosis social support group in Taiwan . Journal of the American Society for Information Science and Technology , 60 ( 7 ), 1504–1517. [ Google Scholar ]
- Davidson L, Chinman M, Sells D, & Rowe M (2006). Peer support among adults with serious mental illness: a report from the field . Schizophrenia bulletin , 32 ( 3 ), 443–450. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- De Choudhury M, Gamon M, & Counts S (2012). Happy, nervous or surprised? classification of human affective states in social media . Paper presented at the Sixth International AAAI Conference on Weblogs and Social Media. [ Google Scholar ]
- De Choudhury M, Gamon M, Counts S, & Horvitz E (2013). Predicting Depression via Social Media . Paper presented at the Association for the Advancement of Artificial Intelligence. [ Google Scholar ]
- Docherty NM, Hawkins KA, Hoffman RE, Quinlan DM, Rakfeldt J, & Sledge WH (1996). Working memory, attention, and communication disturbances in schizophrenia . Journal of Abnormal Psychology , 105 ( 2 ), 212. [ PubMed ] [ Google Scholar ]
- Emala SK, Rizvi AF, Birnbaum ML, Kane JM, & De Choudhury M (2017). Linguistic Markers Indicating Therapeutic Outcomes of Social Media Disclosures of Schizophrenia . Proc. ACMHum.-Comput. Interact , 1 ( 1 ), 43. [ Google Scholar ]
- Feinstein BA, Hershenberg R, Bhatia V, Latack JA, Meuwly N, & Davila J (2013). Negative social comparison on Facebook and depressive symptoms: Rumination as a mechanism . Psychology of Popular Media Culture , 2 ( 3 ), 161. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Firth J, Cotter J, Torous J, Bucci S, Firth JA, & Yung AR (2015). Mobile phone ownership and endorsement of “mHealth” among people with psychosis: a meta-analysis of cross-sectional studies . Schizophrenia bulletin , 42 ( 2 ), 448–455. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Firth J, Rosenbaum S, Stubbs B, Gorczynski P, Yung AR, & Vancampfort D (2016). Motivating factors and barriers towards exercise in severe mental illness: a systematic review and meta-analysis . Psychological medicine , 46 ( 14 ), 2869–2881. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Gay K, Torous J, Joseph A, Pandya A, & Duckworth K (2016). Digital technology use among individuals with schizophrenia: results of an online survey . JMIR mental health , 3 ( 2 ), el5. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Giacco D, Palumbo C, Strappelli N, Catapano F, & Priebe S (2016). Social contacts and loneliness in people with psychotic and mood disorders . Comprehensive Psychiatry , 66 , 59–66. [ PubMed ] [ Google Scholar ]
- Gleeson J, Lederman R, Herrman H, Koval P, Eleftheriadis D, Bendall S, … Alvarez-Jimenez M (2017). Moderated online social therapy for carers of young people recovering from first-episode psychosis: study protocol for a randomised controlled trial . Trials , 75 ( 1 ), 27. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Glick G, Druss B, Pina J, Lally C, & Conde M (2016). Use of mobile technology in a community mental health setting . Journal of telemedicine and telecare , 22 ( 7 ), 430–435. [ PubMed ] [ Google Scholar ]
- Goodman LA, Thompson KM, Weinfurt K, Corl S, Acker P, Mueser KT, & Rosenberg SD (1999). Reliability of reports of violent victimization and posttraumatic stress disorder among men and women with serious mental illness . Journal of Traumatic Stress: Official Publication of the International Society for Traumatic Stress Studies , 12 ( 4 ), 587–599. [ PubMed ] [ Google Scholar ]
- Gowen K, Deschaine M, Gruttadara D, & Markey D (2012). Young adults with mental health conditions and social networking websites: seeking tools to build community . Psychiatric rehabilitation journal , 35 ( 3 ), 245–250. [ PubMed ] [ Google Scholar ]
- Guntuku SC, Yaden DB, Kern ML, Ungar LH, & Eichstaedt JC (2017). Detecting depression and mental illness on social media: an integrative review . Current Opinion in Behavioral Sciences , 18 , 43–49. [ Google Scholar ]
- Haker EL, Lauber C, & Rossler W (2005). Internet forums: a self - help approach for individuals with schizophrenia? Acta Psychiatrica Scandinavica , 112 ( 6 ), 474–477. [ PubMed ] [ Google Scholar ]
- Hamm MP, Newton AS, Chisholm A, Shulhan J, Milne A, Sundar P, … Hartling L (2015). Prevalence and effect of cyberbullying on children and young people: A scoping review of social media studies . JAMA pediatrics , 769 ( 8 ), 770–777. [ PubMed ] [ Google Scholar ]
- Hansen CF, Torgalsboen A-K, Melle I, & Bell MD (2009). Passive/apathetic social withdrawal and active social avoidance in schizophrenia: difference in underlying psychological processes . The Journal of nervous and mental disease , 197 ( 4 ), 274–277. [ PubMed ] [ Google Scholar ]
- Highton-Williamson E, Priebe S, & Giacco D (2015). Online social networking in people with psychosis: a systematic review . International Journal of Social Psychiatry , 61 ( 1 ), 92–101. [ PubMed ] [ Google Scholar ]
- Hilty DM, Chan S, Torous J, Luo J, & Boland RJ (2019). Mobile health, smartphone/device, and apps for psychiatry and medicine: competencies, training, and faculty development issues . Psychiatric Clinics , 42 ( 2 ), 513–534. [ PubMed ] [ Google Scholar ]
- Hswen Y, Naslund JA, Brownstein JS, & Hawkins JB (2018a). Monitoring online discussions about suicide among Twitter users with schizophrenia: exploratory study . JMIR mental health , 5 ( 4 ), e11483. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Hswen Y, Naslund JA, Brownstein JS, & Hawkins JB (2018b). Online communication about depression and anxiety among twitter users with schizophrenia: preliminary findings to inform a digital phenotype using social media . Psychiatric Quarterly , 89 ( 3 ), 569–580. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Hswen Y, Naslund JA, Chandrashekar P, Siegel R, Brownstein JS, & Hawkins JB (2017). Exploring online communication about cigarette smoking among Twitter users who self-identify as having schizophrenia . Psychiatry research , 257 , 479–484. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Indian M, & Grieve R (2014). When Facebook is easier than face-to-face: social support dervied from Facebook in socially anxious individuals . Personality and Individual Differences , 59 , 102–106. [ Google Scholar ]
- Jain SH, Powers BW, Hawkins JB, & Brownstein JS (2015). The digital phenotype . Nature Biotechnology , 33 ( 5 ), 462. [ PubMed ] [ Google Scholar ]
- Kiesler S, Siegel J, & McGuire TW (1984). Social psychological aspects of computer-mediated communication . American Psychologist , 39 , 1123–1134. [ Google Scholar ]
- Kross E, Verduyn P, Demiralp E, Park J, Lee DS, Lin N, … Ybarra O (2013). Facebook use predicts declines in subjective well-being in young adults . PloS one , 5 ( 8 ), e69841. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Lai S, Nguyen V, & Theriault J (2018). Seeking mental health information and support online: experiences and perspectives of young people receiving treatment for first - episode psychosis . Early intervention in psychiatry , 72 ( 3 ), 324–330. [ PubMed ] [ Google Scholar ]
- Lin LY, Sidani JE, Shensa A, Radovic A, Miller E, Colditz JB, … Primack BA (2016). Association between social media use and depression among US young adults . Depression and anxiety , 22 ( 4 ), 323–331. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Machmutow K, Perren S, Sticca F, & Alsaker FD (2012). Peer victimisation and depressive symptoms: can specific coping strategies buffer the negative impact of cybervictimisation? Emotional and Behavioural Difficulties , 17 ( 3-4 ), 403–420. [ Google Scholar ]
- Manikonda L, & De Choudhury M (2017). Modeling and understanding visual attributes of mental health disclosures in social media . Paper presented at the Proceedings of the 2017 CHI Conference on Human Factors in Computing Systems. [ Google Scholar ]
- Mead S, Hilton D, & Curtis L (2001). Peer support: A theoretical perspective . Psychiatric rehabilitation journal , 25 ( 2 ), 134. [ PubMed ] [ Google Scholar ]
- Mereish EH, Sheskier M, Hawthorne DJ, & Goldbach JT (2019). Sexual orientation disparities in mental health and substance use among Black American young people in the USA: effects of cyber and bias-based victimisation . Culture, health & sexuality , 21 ( 9 ), 985–998. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Miller BJ, Stewart A, Schrimsher J, Peeples D, & Buckley PF (2015). How connected are people with schizophrenia? Cell phone, computer, email, and social media use . Psychiatry research , 225 ( 3 ), 458–463. [ PubMed ] [ Google Scholar ]
- Mittal VA, Tessner KD, & Walker EF (2007). Elevated social Internet use and schizotypal personality disorder in adolescents . Schizophrenia research , 94 ( 1-3 ), 50–57. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Moorhead SA, Hazlett DE, Harrison L, Carroll JK, Irwin A, & Hoving C (2013). A new dimension of health care: systematic review of the uses, benefits, and limitations of social media for health communication . Journal of medical Internet research , 15 ( 4 ), e85. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, & Aschbrenner KA (2019). Risks to privacy with use of social media: understanding the views of social media users with serious mental illness . Psychiatric Services , appi. ps. 201800520. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Aschbrenner KA, & Bartels SJ (2016). How people living with serious mental illness use smartphones, mobile apps, and social media . Psychiatric rehabilitation journal , 39 ( 4 ), 364–367. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Aschbrenner KA, Marsch LA, & Bartels SJ (2016a). Feasibility and acceptability of Facebook for health promotion among people with serious mental illness . Digital health , 2 , 2055207616654822. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Aschbrenner KA, Marsch LA, & Bartels SJ (2016b). The future of mental health care: peer-to-peer support and social media . Epidemiology and Psychiatric Sciences , 25 ( 2 ), 113–122. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Aschbrenner KA, Marsch LA, McHugo GJ, & Bartels SJ (2018). Facebook for supporting a lifestyle intervention for people with major depressive disorder, bipolar disorder, and schizophrenia: an exploratory study . Psychiatric Quarterly , 59 ( 1 ), 81–94. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Aschbrenner KA, McHugo GJ, Unutzer J, Marsch LA, & Bartels SJ (2017). Exploring opportunities to support mental health care using social media: A survey of social media users with mental illness . Early intervention in psychiatry . [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Gonsalves PP, Gruebner O, Pendse SR, Smith SL, Sharma A, & Raviola G (2019). Digital innovations for global mental health: opportunities for data science, task sharing, and early intervention . Current Treatment Options in Psychiatry , 1–15. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Naslund JA, Grande SW, Aschbrenner KA, & Elwyn G (2014). Naturally occurring peer support through social media: the experiences of individuals with severe mental illness using YouTube . PloS one , 9 ( 10 ), e110171. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Onnela J-P, & Rauch SL (2016). Harnessing smartphone-based digital phenotyping to enhance behavioral and mental health . Neuropsychopharmacology , 41 ( 7 ), 1691. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Orben A, & Przybylski AK (2019). The association between adolescent well-being and digital technology use . Nature Human Behaviour , 3 ( 2 ), 173. [ PubMed ] [ Google Scholar ]
- Patel V, Saxena S, Lund C, Thornicroft G, Baingana F, Bolton P, … Eaton J (2018). The Lancet Commission on global mental health and sustainable development . The Lancet . [ PubMed ] [ Google Scholar ]
- Primack BA, Shensa A, Escobar-Viera CG, Barrett EL, Sidani JE, Colditz JB, & James AE (2017). Use of multiple social media platforms and symptoms of depression and anxiety: A nationally-representative study among US young adults . Computers in Human Behavior , 69 , 1–9. [ Google Scholar ]
- Reece AG, & Danforth CM (2017). Instagram photos reveal predictive markers of depression . EPJ Data Science , 6 ( 1 ), 15. [ Google Scholar ]
- Reece AG, Reagan AJ, Lix KL, Dodds PS, Danforth CM, & Langer EJ (2017). Forecasting the onset and course of mental illness with Twitter data . Scientific reports , 7 ( 1 ), 13006. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Rideout V, & Fox S (2018). Digital health practices, social media use, and mental well-being among teens and young adults in the U.S Retrieved from San Francisco, CA: https://www.hopelab.org/reports/pdf/a-national-survey-by-hopelab-and-well-being-trust-2018.pdf [ Google Scholar ]
- Saha K, Torous J, Ernala SK, Rizuto C, Stafford A, & De Choudhury M (2019). A computational study of mental health awareness campaigns on social media . Translational behavioral medicine . [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Schlosser DA, Campellone T, Kim D, Truong B, Vergani S, Ward C, & Vinogradov S (2016). Feasibility of PRIME: a cognitive neuroscience-informed mobile app intervention to enhance motivated behavior and improve quality of life in recent onset schizophrenia . JMIR research protocols , 5 ( 2 ). [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Schlosser DA, Campellone TR, Truong B, Etter K, Vergani S, Komaiko K, & Vinogradov S (2018). Efficacy of PRIME, a mobile app intervention designed to improve motivation in young people with schizophrenia . Schizophrenia bulletin , 44 ( 5 ), 1010–1020. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Schrank B, Sibitz I, Unger A, & Amering M (2010). How patients with schizophrenia use the internet: qualitative study . Journal of medical Internet research , 12 ( 5 ), e70. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Schueller SM, Hunter JF, Figueroa C, & Aguilera A (2019). Use of digital mental health for marginalized and underserved populations . Current Treatment Options in Psychiatry , 6 ( 3 ), 243–255. [ Google Scholar ]
- Shatte AB, Hutchinson DM, & Teague SJ (2019). Machine learning in mental health: a scoping review of methods and applications . Psychological medicine , 49 ( 9 ), 1426–1448. [ PubMed ] [ Google Scholar ]
- Spinzy Y, Nitzan U, Becker G, Bloch Y, & Fennig S (2012). Does the Internet offer social opportunities for individuals with schizophrenia? a cross-sectional pilot study . Psychiatry research , 198 ( 2 ), 319–320. [ PubMed ] [ Google Scholar ]
- Stiglic N, & Viner RM (2019). Effects of screentime on the health and well-being of children and adolescents: a systematic review of reviews . BMJopen , 9 ( 1 ), e023191. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Sumner SA, Galik S, Mathieu J, Ward M, Kiley T, Bartholow B, … Mork P (2019). Temporal and geographic patterns of social media posts about an emerging suicide game . Journal of Adolescent Health . [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Torous J, Chan SR, Tan SY-M, Behrens J, Mathew I, Conrad EJ, … Keshavan M (2014). Patient smartphone ownership and interest in mobile apps to monitor symptoms of mental health conditions: a survey in four geographically distinct psychiatric clinics . JMIR mental health , 1 ( 1 ), e5. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Torous J, Friedman R, & Keshavan M (2014). Smartphone ownership and interest in mobile applications to monitor symptoms of mental health conditions . JMIR mHealth and uHealth , 2 ( 1 ), e2. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Torous J, & Keshavan M (2016). The role of social media in schizophrenia: evaluating risks, benefits, and potential . Current opinion in psychiatry , 29 ( 3 ), 190–195. [ PubMed ] [ Google Scholar ]
- Torous J, Wisniewski H, Bird B, Carpenter E, David G, Elejalde E, … Henson P (2019). Creating a digital health smartphone app and digital phenotyping platform for mental health and diverse healthcare needs: an interdisciplinary and collaborative approach . Journal of Technology in Behavioral Science , 1–13. [ Google Scholar ]
- Trefflich F, Kalckreuth S, Mergl R, & Rummel-Kluge C (2015). Psychiatric patients’ internet use corresponds to the internet use of the general public . Psychiatry research , 226 , 136–141. [ PubMed ] [ Google Scholar ]
- Twenge JM, & Campbell WK (2018). Associations between screen time and lower psychological well-being among children and adolescents: Evidence from a population-based study . Preventive medicine reports , 12 , 271–283. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Twenge JM, Joiner TE, Rogers ML, & Martin GN (2018). Increases in depressive symptoms, suicide-related outcomes, and suicide rates among US adolescents after 2010 and links to increased new media screen time . Clinical Psychological Science , 6 ( 1 ), 3–17. [ Google Scholar ]
- Tynes BM, Willis HA, Stewart AM, & Hamilton MW (2019). Race-related traumatic events online and mental health among adolescents of color . Journal of Adolescent Health , 65 ( 3 ), 371–377. [ PubMed ] [ Google Scholar ]
- Vannucci A, Flannery KM, & Ohannessian CM (2017). Social media use and anxiety in emerging adults . Journal of affective disorders , 207 , 163–166. [ PubMed ] [ Google Scholar ]
- Vayreda A, & Antaki C (2009). Social support and unsolicited advice in a bipolar disorder online forum . Qualitative health research , 19 ( 7 ), 931–942. [ PubMed ] [ Google Scholar ]
- Ventola CL (2014). Social media and health care professionals: benefits, risks, and best practices . Pharmacy and Therapeutics , 39 ( 7 ), 491. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- We Are Social. (2020). Digital in 2020 . Retrieved from https://wearesocial.com/global-digital-report-2019
- Webb H, Jirotka M, Stahl BC, Housley W, Edwards A, Williams M, … Burnap P (2017). The ethical challenges of publishing Twitter data for research dissemination . Paper presented at the Proceedings of the 2017 ACM on Web Science Conference. [ Google Scholar ]
- Williams ML, Burnap P, & Sloan L (2017). Towards an ethical framework for publishing Twitter data in social research: Taking into account users’ views, online context and algorithmic estimation . Sociology , 57 ( 6 ), 1149–1168. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Woods HC, & Scott H (2016). # Sleepyteens: Social media use in adolescence is associated with poor sleep quality, anxiety, depression and low self-esteem . Journal of adolescence , 57 , 41–49. [ PubMed ] [ Google Scholar ]
- Ybarra ML (2004). Linkages between depressive symptomatology and Internet harassment among young regular Internet users . Cyber Psychology & Behavior , 7 ( 2 ), 247–257. [ PubMed ] [ Google Scholar ]
Information
- Author Services

Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
The role of social network analysis in social media research.

1. Introduction
2. the significance of this study, 3. works related to social media usage, 4. the related works of social network analysis, 5. possible hypotheses regarding structural features of social media usage, 6. conclusions, author contributions, conflicts of interest.
- We Are Social. Available online: https://wearesocial.com/uk/blog/2023/04/the-global-state-of-digital-in-april-2023 (accessed on 14 April 2023).
- Hofstede, G. What did GLOBE really measure? Researchers’ minds versus respondents’ minds. J. Int. Bus. Stud. 2006 , 37 , 882–896. [ Google Scholar ] [ CrossRef ]
- Granovetter, M. Threshold models of Collective Behavior. Am. J. Sociol. 1978 , 83 , 1420–1443. [ Google Scholar ] [ CrossRef ]
- Castells, M. Communication, power and counter-power in the network society. Int. J. Commun. 2007 , 1 , 29. [ Google Scholar ]
- McQuail, D. The future of communication studies: A contribution to the debate. Media Commun. Stud. Int Erventions Intersect. 2010 , 27 , 27–35. [ Google Scholar ]
- Sheppard, B.H.; Hartwick, J.; Warshaw, P.R. The theory of reasoned action: A meta-analysis of past research with recommendations for modifications and future research. J. Consum. Res. 1988 , 15 , 325–343. [ Google Scholar ] [ CrossRef ]
- Knoke, D.; Yang, S. Social Network Analysis ; SAGE Publications: London, UK, 2019. [ Google Scholar ]
- Cloudlancer. Available online: https://cloudlancer.com/social-media-statistics-2023/?utm_source=Search&utm_medium=ppc&utm_campaign=0003Stats&utm_id=0003&utm_term=statssocial&utm_content=2023statssocial&gclid=CjwKCAjwlJimBhAsEiwA1hrp5gKoTxnqL5DyzzD_RMvBKFLpWXPH9naQlMwN6hB1PDShB20iYgJoXhoCqvwQAvD_BwE (accessed on 30 July 2023).
- Ngai, E.W.T.; Tao, S.S.C.; Moon, K.K.L. Social media research: Theories, constructs, and conceptual frameworks. Int. J. Inf. Manag. 2015 , 35 , 33–44. [ Google Scholar ] [ CrossRef ]
- Tuten, T.L.; Solomon, M.R. Social Media Marketing ; Sage: Los Angeles, CA, USA, 2018; p. 4. [ Google Scholar ]
- Bandura, A. Gauging the relationship between self-efficacy judgment and action. Cogn. Ther. Res. 1980 , 4 , 263–268. [ Google Scholar ] [ CrossRef ]
- Anderson, M. Intelligence and Development: A Cognitive Theory ; Blackwell Publishing: Hoboken, NJ, USA, 1992. [ Google Scholar ]
- Burke, M.; Kraut, R.; Marlow, C. Social capital on Facebook: Differentiating uses and users. In SIGCHI Conference on Human Factors in Computing Systems ; SIGCHI: Tokyo, Japan, 2011; pp. 571–580. [ Google Scholar ]
- Bateson, G. Steps to an Ecology of Mind: Collected Essays in Anthropology, Psychiatry, Evolution and Epistemology ; Granada: London, UK, 1973. [ Google Scholar ]
- Colliander, J.; Dahlén, M. Following the fashionable friend: The power of social media. J. Advert. Res. 2011 , 51 , 313–320. [ Google Scholar ] [ CrossRef ]
- Berry, D.M. Understanding Digital Humanities ; Palgrave Macmillan: New York, NY, USA, 2012. [ Google Scholar ]
- Tabassum, S.; Pereira, F.S.F.; Fernandes, S.; Gama, J. Social network analysis: An overview. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 2018 , 8 , e1256. [ Google Scholar ] [ CrossRef ]
- Kwon, O.; Wen, Y. An empirical study of the factors affecting social network service use. Comput. Hum. Behav. 2010 , 26 , 254–263. [ Google Scholar ] [ CrossRef ]
- Sassenberg, K.; Vliek, M.L.W. Social Psychology in Action: Evidence-Based Interventions from Theory to Practice , 1st ed.; Springer: Cham, Switzerland, 2020. [ Google Scholar ]
- Zhong, B.; Hardin, M.; Sun, T. Less effortful thinking leads to more social networking? The associations between the use of social network sites and personality traits. Comput. Hum. Behav. 2011 , 27 , 1265–1271. [ Google Scholar ] [ CrossRef ]
- Latané, B.; Williams, K.; Harkins, S. Many hands make light the work: The causes and consequences of social loafing. J. Personal. Soc. Psychol. 1979 , 37 , 822–832. [ Google Scholar ] [ CrossRef ]
- Montano, D.E.; Kasprzyk, D. Theory of reasoned action, theory of planned behavior, and the integrated behavioral model. Health Behav. Theory Res. Pract. 2015 , 70 , 231. [ Google Scholar ]
- Vallerand, R.J.; Pelletier, L.G.; Blais, M.R. The Academic Motivation Scale: A measure of intrinsic, extrinsic, and amotivation in education. Educ. Psychol. Meas. 1992 , 52 , 1003–1017. [ Google Scholar ] [ CrossRef ]
- Wei, L. Filter blogs vs. personal journals: Understanding the knowledge production gap on the internet. J. Comput. Mediat. Commun. 2009 , 14 , 532–559. [ Google Scholar ] [ CrossRef ]
- Chen, G.M. Tweet this: A uses and gratifications perspective on how active Twitter use gratifies a need to connect with others. Comput. Hum. Behav. 2010 , 27 , 755–762. [ Google Scholar ] [ CrossRef ]
- White, E.L.; Parsons, A.L.; Wong, B.; White, A. Building a socially responsible global community? Communication B Corps on social media. Corp. Commun. Int. J. 2023 , 28 , 86–102. [ Google Scholar ] [ CrossRef ]
- Granovetter, M. The Strength of Weak Ties: A Network Theory Revisited. Sociol. Theory 1973 , 1 , 201. [ Google Scholar ] [ CrossRef ]
- Gudka, M.; Gardiner, K.L.K.; Lomas, T. Towards a framework for flourishing through social media: A systematic review of 118 research studies. J. Posit. Psychol. 2023 , 18 , 86–105. [ Google Scholar ] [ CrossRef ]
- Pang, H.; Qin, K.; Ji, M. Can social network sites facilitate civic engagement? Assessing dynamic relationship between social media and civic activities among young people. Soc. Media Civ. Act. 2022 , 46 , 79–94. [ Google Scholar ] [ CrossRef ]
- Stalder, F. Manuel Castells: The Theory of the Network Society ; Polity: Cambridge, UK, 2006. [ Google Scholar ]
- Ajzen, I. Perceived behavioral control, self-efficacy, locus of control, and the theory of planned behavior. J. Appl. Soc. Psychol. 2002 , 32 , 665–683. [ Google Scholar ] [ CrossRef ]
- Ajzen, I. The theory of planned behavior: Reactions and reflections. Psychol. Health 2011 , 26 , 1113–1127. [ Google Scholar ] [ CrossRef ] [ PubMed ]
- Albert, R.; Barabási, A.L. Statistical mechanics of complex networks. Rev. Mod. Phys. 2002 , 74 , 47. [ Google Scholar ] [ CrossRef ]
- Gonzalez, M.C.; Hidalgo, C.A.; Barabási, A.L. Understanding individual human mobility patterns. Nature 2008 , 453 , 779–782. [ Google Scholar ] [ CrossRef ]
- Mahalingham, T.; McEvoy, P.M.; Clarke, P.J.F. Assessing the validity of self-report social media use: Evidence of No relationship with objective smartphone use. Comput. Hum. Behav. 2023 , 140 , 107567. [ Google Scholar ] [ CrossRef ]
- Robins, G.; Pattison, P.; Kalish, Y.; Lusher, D. An introduction to exponential random graph (p*) models for social networks. Soc. Netw. 2007 , 29 , 173–191. [ Google Scholar ] [ CrossRef ]
- Pettegrew, L.S.; Carolyn, D. Smart phones and mediated relationships: The changing face of relational communication. Rev. Commun. 2015 , 15 , 122–139. [ Google Scholar ] [ CrossRef ]
- Lee, M.J.; Lee, E.; Lee, B.; Jeong, H.; Lee, D.-S.; Lee, S.H. Uncovering hidden dependency in weighted networks via information entropy. Phys. Rev. Res. 2021 , 3 , 043136. [ Google Scholar ] [ CrossRef ]
- Anderson, C.J.; Wasserman, S.; Crouch, B. A p* primer: Logit models for social networks. Soc. Netw. 1999 , 21 , 37–66. [ Google Scholar ] [ CrossRef ]
- Wasserman, S.; Faust, K. Social Network Analysis: Methods and Applications ; Cambridge University Press: London, UK, 1994. [ Google Scholar ]
- Fisher, D. Using egocentric networks to understand communication. IEEE Internet Comput. 2005 , 9 , 20–28. [ Google Scholar ] [ CrossRef ]
- Wasserman, S.; Robins, G. An introduction to random graphs, dependence graphs, and p*. In Models and Methods in Social Network Analysis ; Cambridge University Press: New York, NY, USA, 2005; pp. 148–161. [ Google Scholar ]
- Watzlawick, P.; Weakland, J.H. (Eds.) The Interactional View ; Norton: New York, NY, USA, 1977. [ Google Scholar ]
- Corradini, E.; Virsino, D.; Virgili, L. Investigating negative reviews and detecting negative influencers in Yelp through a multi-dimensional social network based model. Int. J. Inf. Manag. 2021 , 60 , 102377. [ Google Scholar ] [ CrossRef ]
- Corradini, E.; Virsino, D.; Virgili, L. Investigating the phenomenon of NSFW posts in Reddit. Inf. Sci. 2021 , 566 , 140–164. [ Google Scholar ] [ CrossRef ]
- Top Social Media Statistics and Trends of 2023. Available online: https://www.forbes.com/advisor/business/social-media-statistics/ (accessed on 30 July 2023).
Click here to enlarge figure
| Parameter | Structural Features | Estimate (Standard Error) |
|---|---|---|
| θ (Edge) | −3.12 (1.36) | |
| σ2 (Two Stars) | 0.06 (1.84) | |
| σ3 (Tree Stars) | −0.02 (0.13) | |
| τ (Triangle) | 1.06 (8.4) |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Nie, Z.; Waheed, M.; Kasimon, D.; Wan Abas, W.A.B. The Role of Social Network Analysis in Social Media Research. Appl. Sci. 2023 , 13 , 9486. https://doi.org/10.3390/app13179486
Nie Z, Waheed M, Kasimon D, Wan Abas WAB. The Role of Social Network Analysis in Social Media Research. Applied Sciences . 2023; 13(17):9486. https://doi.org/10.3390/app13179486
Nie, Zhou, Moniza Waheed, Diyana Kasimon, and Wan Anita Binti Wan Abas. 2023. "The Role of Social Network Analysis in Social Media Research" Applied Sciences 13, no. 17: 9486. https://doi.org/10.3390/app13179486
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
CONCEPTUAL ANALYSIS article
The effect of social media on the development of students’ affective variables.

- 1 Science and Technology Department, Nanjing University of Posts and Telecommunications, Nanjing, China
- 2 School of Marxism, Hohai University, Nanjing, Jiangsu, China
- 3 Government Enterprise Customer Center, China Mobile Group Jiangsu Co., Ltd., Nanjing, China
The use of social media is incomparably on the rise among students, influenced by the globalized forms of communication and the post-pandemic rush to use multiple social media platforms for education in different fields of study. Though social media has created tremendous chances for sharing ideas and emotions, the kind of social support it provides might fail to meet students’ emotional needs, or the alleged positive effects might be short-lasting. In recent years, several studies have been conducted to explore the potential effects of social media on students’ affective traits, such as stress, anxiety, depression, and so on. The present paper reviews the findings of the exemplary published works of research to shed light on the positive and negative potential effects of the massive use of social media on students’ emotional well-being. This review can be insightful for teachers who tend to take the potential psychological effects of social media for granted. They may want to know more about the actual effects of the over-reliance on and the excessive (and actually obsessive) use of social media on students’ developing certain images of self and certain emotions which are not necessarily positive. There will be implications for pre- and in-service teacher training and professional development programs and all those involved in student affairs.
Introduction
Social media has turned into an essential element of individuals’ lives including students in today’s world of communication. Its use is growing significantly more than ever before especially in the post-pandemic era, marked by a great revolution happening to the educational systems. Recent investigations of using social media show that approximately 3 billion individuals worldwide are now communicating via social media ( Iwamoto and Chun, 2020 ). This growing population of social media users is spending more and more time on social network groupings, as facts and figures show that individuals spend 2 h a day, on average, on a variety of social media applications, exchanging pictures and messages, updating status, tweeting, favoring, and commenting on many updated socially shared information ( Abbott, 2017 ).
Researchers have begun to investigate the psychological effects of using social media on students’ lives. Chukwuere and Chukwuere (2017) maintained that social media platforms can be considered the most important source of changing individuals’ mood, because when someone is passively using a social media platform seemingly with no special purpose, s/he can finally feel that his/her mood has changed as a function of the nature of content overviewed. Therefore, positive and negative moods can easily be transferred among the population using social media networks ( Chukwuere and Chukwuere, 2017 ). This may become increasingly important as students are seen to be using social media platforms more than before and social networking is becoming an integral aspect of their lives. As described by Iwamoto and Chun (2020) , when students are affected by social media posts, especially due to the increasing reliance on social media use in life, they may be encouraged to begin comparing themselves to others or develop great unrealistic expectations of themselves or others, which can have several affective consequences.
Considering the increasing influence of social media on education, the present paper aims to focus on the affective variables such as depression, stress, and anxiety, and how social media can possibly increase or decrease these emotions in student life. The exemplary works of research on this topic in recent years will be reviewed here, hoping to shed light on the positive and negative effects of these ever-growing influential platforms on the psychology of students.
Significance of the study
Though social media, as the name suggests, is expected to keep people connected, probably this social connection is only superficial, and not adequately deep and meaningful to help individuals feel emotionally attached to others. The psychological effects of social media on student life need to be studied in more depth to see whether social media really acts as a social support for students and whether students can use social media to cope with negative emotions and develop positive feelings or not. In other words, knowledge of the potential effects of the growing use of social media on students’ emotional well-being can bridge the gap between the alleged promises of social media and what it actually has to offer to students in terms of self-concept, self-respect, social role, and coping strategies (for stress, anxiety, etc.).
Exemplary general literature on psychological effects of social media
Before getting down to the effects of social media on students’ emotional well-being, some exemplary works of research in recent years on the topic among general populations are reviewed. For one, Aalbers et al. (2018) reported that individuals who spent more time passively working with social media suffered from more intense levels of hopelessness, loneliness, depression, and perceived inferiority. For another, Tang et al. (2013) observed that the procedures of sharing information, commenting, showing likes and dislikes, posting messages, and doing other common activities on social media are correlated with higher stress. Similarly, Ley et al. (2014) described that people who spend 2 h, on average, on social media applications will face many tragic news, posts, and stories which can raise the total intensity of their stress. This stress-provoking effect of social media has been also pinpointed by Weng and Menczer (2015) , who contended that social media becomes a main source of stress because people often share all kinds of posts, comments, and stories ranging from politics and economics, to personal and social affairs. According to Iwamoto and Chun (2020) , anxiety and depression are the negative emotions that an individual may develop when some source of stress is present. In other words, when social media sources become stress-inducing, there are high chances that anxiety and depression also develop.
Charoensukmongkol (2018) reckoned that the mental health and well-being of the global population can be at a great risk through the uncontrolled massive use of social media. These researchers also showed that social media sources can exert negative affective impacts on teenagers, as they can induce more envy and social comparison. According to Fleck and Johnson-Migalski (2015) , though social media, at first, plays the role of a stress-coping strategy, when individuals continue to see stressful conditions (probably experienced and shared by others in media), they begin to develop stress through the passage of time. Chukwuere and Chukwuere (2017) maintained that social media platforms continue to be the major source of changing mood among general populations. For example, someone might be passively using a social media sphere, and s/he may finally find him/herself with a changed mood depending on the nature of the content faced. Then, this good or bad mood is easily shared with others in a flash through the social media. Finally, as Alahmar (2016) described, social media exposes people especially the young generation to new exciting activities and events that may attract them and keep them engaged in different media contexts for hours just passing their time. It usually leads to reduced productivity, reduced academic achievement, and addiction to constant media use ( Alahmar, 2016 ).
The number of studies on the potential psychological effects of social media on people in general is higher than those selectively addressed here. For further insights into this issue, some other suggested works of research include Chang (2012) , Sriwilai and Charoensukmongkol (2016) , and Zareen et al. (2016) . Now, we move to the studies that more specifically explored the effects of social media on students’ affective states.
Review of the affective influences of social media on students
Vygotsky’s mediational theory (see Fernyhough, 2008 ) can be regarded as a main theoretical background for the support of social media on learners’ affective states. Based on this theory, social media can play the role of a mediational means between learners and the real environment. Learners’ understanding of this environment can be mediated by the image shaped via social media. This image can be either close to or different from the reality. In the case of the former, learners can develop their self-image and self-esteem. In the case of the latter, learners might develop unrealistic expectations of themselves by comparing themselves to others. As it will be reviewed below among the affective variables increased or decreased in students under the influence of the massive use of social media are anxiety, stress, depression, distress, rumination, and self-esteem. These effects have been explored more among school students in the age range of 13–18 than university students (above 18), but some studies were investigated among college students as well. Exemplary works of research on these affective variables are reviewed here.
In a cross-sectional study, O’Dea and Campbell (2011) explored the impact of online interactions of social networks on the psychological distress of adolescent students. These researchers found a negative correlation between the time spent on social networking and mental distress. Dumitrache et al. (2012) explored the relations between depression and the identity associated with the use of the popular social media, the Facebook. This study showed significant associations between depression and the number of identity-related information pieces shared on this social network. Neira and Barber (2014) explored the relationship between students’ social media use and depressed mood at teenage. No significant correlation was found between these two variables. In the same year, Tsitsika et al. (2014) explored the associations between excessive use of social media and internalizing emotions. These researchers found a positive correlation between more than 2-h a day use of social media and anxiety and depression.
Hanprathet et al. (2015) reported a statistically significant positive correlation between addiction to Facebook and depression among about a thousand high school students in wealthy populations of Thailand and warned against this psychological threat. Sampasa-Kanyinga and Lewis (2015) examined the relationship between social media use and psychological distress. These researchers found that the use of social media for more than 2 h a day was correlated with a higher intensity of psychological distress. Banjanin et al. (2015) tested the relationship between too much use of social networking and depression, yet found no statistically significant correlation between these two variables. Frison and Eggermont (2016) examined the relationships between different forms of Facebook use, perceived social support of social media, and male and female students’ depressed mood. These researchers found a positive association between the passive use of the Facebook and depression and also between the active use of the social media and depression. Furthermore, the perceived social support of the social media was found to mediate this association. Besides, gender was found as the other factor to mediate this relationship.
Vernon et al. (2017) explored change in negative investment in social networking in relation to change in depression and externalizing behavior. These researchers found that increased investment in social media predicted higher depression in adolescent students, which was a function of the effect of higher levels of disrupted sleep. Barry et al. (2017) explored the associations between the use of social media by adolescents and their psychosocial adjustment. Social media activity showed to be positively and moderately associated with depression and anxiety. Another investigation was focused on secondary school students in China conducted by Li et al. (2017) . The findings showed a mediating role of insomnia on the significant correlation between depression and addiction to social media. In the same year, Yan et al. (2017) aimed to explore the time spent on social networks and its correlation with anxiety among middle school students. They found a significant positive correlation between more than 2-h use of social networks and the intensity of anxiety.
Also in China, Wang et al. (2018) showed that addiction to social networking sites was correlated positively with depression, and this correlation was mediated by rumination. These researchers also found that this mediating effect was moderated by self-esteem. It means that the effect of addiction on depression was compounded by low self-esteem through rumination. In another work of research, Drouin et al. (2018) showed that though social media is expected to act as a form of social support for the majority of university students, it can adversely affect students’ mental well-being, especially for those who already have high levels of anxiety and depression. In their research, the social media resources were found to be stress-inducing for half of the participants, all university students. The higher education population was also studied by Iwamoto and Chun (2020) . These researchers investigated the emotional effects of social media in higher education and found that the socially supportive role of social media was overshadowed in the long run in university students’ lives and, instead, fed into their perceived depression, anxiety, and stress.
Keles et al. (2020) provided a systematic review of the effect of social media on young and teenage students’ depression, psychological distress, and anxiety. They found that depression acted as the most frequent affective variable measured. The most salient risk factors of psychological distress, anxiety, and depression based on the systematic review were activities such as repeated checking for messages, personal investment, the time spent on social media, and problematic or addictive use. Similarly, Mathewson (2020) investigated the effect of using social media on college students’ mental health. The participants stated the experience of anxiety, depression, and suicidality (thoughts of suicide or attempts to suicide). The findings showed that the types and frequency of using social media and the students’ perceived mental health were significantly correlated with each other.
The body of research on the effect of social media on students’ affective and emotional states has led to mixed results. The existing literature shows that there are some positive and some negative affective impacts. Yet, it seems that the latter is pre-dominant. Mathewson (2020) attributed these divergent positive and negative effects to the different theoretical frameworks adopted in different studies and also the different contexts (different countries with whole different educational systems). According to Fredrickson’s broaden-and-build theory of positive emotions ( Fredrickson, 2001 ), the mental repertoires of learners can be built and broadened by how they feel. For instance, some external stimuli might provoke negative emotions such as anxiety and depression in learners. Having experienced these negative emotions, students might repeatedly check their messages on social media or get addicted to them. As a result, their cognitive repertoire and mental capacity might become limited and they might lose their concentration during their learning process. On the other hand, it should be noted that by feeling positive, learners might take full advantage of the affordances of the social media and; thus, be able to follow their learning goals strategically. This point should be highlighted that the link between the use of social media and affective states is bi-directional. Therefore, strategic use of social media or its addictive use by students can direct them toward either positive experiences like enjoyment or negative ones such as anxiety and depression. Also, these mixed positive and negative effects are similar to the findings of several other relevant studies on general populations’ psychological and emotional health. A number of studies (with general research populations not necessarily students) showed that social networks have facilitated the way of staying in touch with family and friends living far away as well as an increased social support ( Zhang, 2017 ). Given the positive and negative emotional effects of social media, social media can either scaffold the emotional repertoire of students, which can develop positive emotions in learners, or induce negative provokers in them, based on which learners might feel negative emotions such as anxiety and depression. However, admittedly, social media has also generated a domain that encourages the act of comparing lives, and striving for approval; therefore, it establishes and internalizes unrealistic perceptions ( Virden et al., 2014 ; Radovic et al., 2017 ).
It should be mentioned that the susceptibility of affective variables to social media should be interpreted from a dynamic lens. This means that the ecology of the social media can make changes in the emotional experiences of learners. More specifically, students’ affective variables might self-organize into different states under the influence of social media. As for the positive correlation found in many studies between the use of social media and such negative effects as anxiety, depression, and stress, it can be hypothesized that this correlation is induced by the continuous comparison the individual makes and the perception that others are doing better than him/her influenced by the posts that appear on social media. Using social media can play a major role in university students’ psychological well-being than expected. Though most of these studies were correlational, and correlation is not the same as causation, as the studies show that the number of participants experiencing these negative emotions under the influence of social media is significantly high, more extensive research is highly suggested to explore causal effects ( Mathewson, 2020 ).
As the review of exemplary studies showed, some believed that social media increased comparisons that students made between themselves and others. This finding ratifies the relevance of the Interpretation Comparison Model ( Stapel and Koomen, 2000 ; Stapel, 2007 ) and Festinger’s (1954) Social Comparison Theory. Concerning the negative effects of social media on students’ psychology, it can be argued that individuals may fail to understand that the content presented in social media is usually changed to only represent the attractive aspects of people’s lives, showing an unrealistic image of things. We can add that this argument also supports the relevance of the Social Comparison Theory and the Interpretation Comparison Model ( Stapel and Koomen, 2000 ; Stapel, 2007 ), because social media sets standards that students think they should compare themselves with. A constant observation of how other students or peers are showing their instances of achievement leads to higher self-evaluation ( Stapel and Koomen, 2000 ). It is conjectured that the ubiquitous role of social media in student life establishes unrealistic expectations and promotes continuous comparison as also pinpointed in the Interpretation Comparison Model ( Stapel and Koomen, 2000 ; Stapel, 2007 ).
Implications of the study
The use of social media is ever increasing among students, both at school and university, which is partly because of the promises of technological advances in communication services and partly because of the increased use of social networks for educational purposes in recent years after the pandemic. This consistent use of social media is not expected to leave students’ psychological, affective and emotional states untouched. Thus, it is necessary to know how the growing usage of social networks is associated with students’ affective health on different aspects. Therefore, we found it useful to summarize the research findings in recent years in this respect. If those somehow in charge of student affairs in educational settings are aware of the potential positive or negative effects of social media usage on students, they can better understand the complexities of students’ needs and are better capable of meeting them.
Psychological counseling programs can be initiated at schools or universities to check upon the latest state of students’ mental and emotional health influenced by the pervasive use of social media. The counselors can be made aware of the potential adverse effects of social networking and can adapt the content of their inquiries accordingly. Knowledge of the potential reasons for student anxiety, depression, and stress can help school or university counselors to find individualized coping strategies when they diagnose any symptom of distress in students influenced by an excessive use of social networking.
Admittedly, it is neither possible to discard the use of social media in today’s academic life, nor to keep students’ use of social networks fully controlled. Certainly, the educational space in today’s world cannot do without the social media, which has turned into an integral part of everybody’s life. Yet, probably students need to be instructed on how to take advantage of the media and to be the least affected negatively by its occasional superficial and unrepresentative content. Compensatory programs might be needed at schools or universities to encourage students to avoid making unrealistic and impartial comparisons of themselves and the flamboyant images of others displayed on social media. Students can be taught to develop self-appreciation and self-care while continuing to use the media to their benefit.
The teachers’ role as well as the curriculum developers’ role are becoming more important than ever, as they can significantly help to moderate the adverse effects of the pervasive social media use on students’ mental and emotional health. The kind of groupings formed for instructional purposes, for example, in social media can be done with greater care by teachers to make sure that the members of the groups are homogeneous and the tasks and activities shared in the groups are quite relevant and realistic. The teachers cannot always be in a full control of students’ use of social media, and the other fact is that students do not always and only use social media for educational purposes. They spend more time on social media for communicating with friends or strangers or possibly they just passively receive the content produced out of any educational scope just for entertainment. This uncontrolled and unrealistic content may give them a false image of life events and can threaten their mental and emotional health. Thus, teachers can try to make students aware of the potential hazards of investing too much of their time on following pages or people that publish false and misleading information about their personal or social identities. As students, logically expected, spend more time with their teachers than counselors, they may be better and more receptive to the advice given by the former than the latter.
Teachers may not be in full control of their students’ use of social media, but they have always played an active role in motivating or demotivating students to take particular measures in their academic lives. If teachers are informed of the recent research findings about the potential effects of massively using social media on students, they may find ways to reduce students’ distraction or confusion in class due to the excessive or over-reliant use of these networks. Educators may more often be mesmerized by the promises of technology-, computer- and mobile-assisted learning. They may tend to encourage the use of social media hoping to benefit students’ social and interpersonal skills, self-confidence, stress-managing and the like. Yet, they may be unaware of the potential adverse effects on students’ emotional well-being and, thus, may find the review of the recent relevant research findings insightful. Also, teachers can mediate between learners and social media to manipulate the time learners spend on social media. Research has mainly indicated that students’ emotional experiences are mainly dependent on teachers’ pedagogical approach. They should refrain learners from excessive use of, or overreliance on, social media. Raising learners’ awareness of this fact that individuals should develop their own path of development for learning, and not build their development based on unrealistic comparison of their competences with those of others, can help them consider positive values for their activities on social media and, thus, experience positive emotions.
At higher education, students’ needs are more life-like. For example, their employment-seeking spirits might lead them to create accounts in many social networks, hoping for a better future. However, membership in many of these networks may end in the mere waste of the time that could otherwise be spent on actual on-campus cooperative projects. Universities can provide more on-campus resources both for research and work experience purposes from which the students can benefit more than the cyberspace that can be tricky on many occasions. Two main theories underlying some negative emotions like boredom and anxiety are over-stimulation and under-stimulation. Thus, what learners feel out of their involvement in social media might be directed toward negative emotions due to the stimulating environment of social media. This stimulating environment makes learners rely too much, and spend too much time, on social media or use them obsessively. As a result, they might feel anxious or depressed. Given the ubiquity of social media, these negative emotions can be replaced with positive emotions if learners become aware of the psychological effects of social media. Regarding the affordances of social media for learners, they can take advantage of the potential affordances of these media such as improving their literacy, broadening their communication skills, or enhancing their distance learning opportunities.
A review of the research findings on the relationship between social media and students’ affective traits revealed both positive and negative findings. Yet, the instances of the latter were more salient and the negative psychological symptoms such as depression, anxiety, and stress have been far from negligible. These findings were discussed in relation to some more relevant theories such as the social comparison theory, which predicted that most of the potential issues with the young generation’s excessive use of social media were induced by the unfair comparisons they made between their own lives and the unrealistic portrayal of others’ on social media. Teachers, education policymakers, curriculum developers, and all those in charge of the student affairs at schools and universities should be made aware of the psychological effects of the pervasive use of social media on students, and the potential threats.
It should be reminded that the alleged socially supportive and communicative promises of the prevalent use of social networking in student life might not be fully realized in practice. Students may lose self-appreciation and gratitude when they compare their current state of life with the snapshots of others’ or peers’. A depressed or stressed-out mood can follow. Students at schools or universities need to learn self-worth to resist the adverse effects of the superficial support they receive from social media. Along this way, they should be assisted by the family and those in charge at schools or universities, most importantly the teachers. As already suggested, counseling programs might help with raising students’ awareness of the potential psychological threats of social media to their health. Considering the ubiquity of social media in everybody’ life including student life worldwide, it seems that more coping and compensatory strategies should be contrived to moderate the adverse psychological effects of the pervasive use of social media on students. Also, the affective influences of social media should not be generalized but they need to be interpreted from an ecological or contextual perspective. This means that learners might have different emotions at different times or different contexts while being involved in social media. More specifically, given the stative approach to learners’ emotions, what learners emotionally experience in their application of social media can be bound to their intra-personal and interpersonal experiences. This means that the same learner at different time points might go through different emotions Also, learners’ emotional states as a result of their engagement in social media cannot be necessarily generalized to all learners in a class.
As the majority of studies on the psychological effects of social media on student life have been conducted on school students than in higher education, it seems it is too soon to make any conclusive remark on this population exclusively. Probably, in future, further studies of the psychological complexities of students at higher education and a better knowledge of their needs can pave the way for making more insightful conclusions about the effects of social media on their affective states.
Suggestions for further research
The majority of studies on the potential effects of social media usage on students’ psychological well-being are either quantitative or qualitative in type, each with many limitations. Presumably, mixed approaches in near future can better provide a comprehensive assessment of these potential associations. Moreover, most studies on this topic have been cross-sectional in type. There is a significant dearth of longitudinal investigation on the effect of social media on developing positive or negative emotions in students. This seems to be essential as different affective factors such as anxiety, stress, self-esteem, and the like have a developmental nature. Traditional research methods with single-shot designs for data collection fail to capture the nuances of changes in these affective variables. It can be expected that more longitudinal studies in future can show how the continuous use of social media can affect the fluctuations of any of these affective variables during the different academic courses students pass at school or university.
As already raised in some works of research reviewed, the different patterns of impacts of social media on student life depend largely on the educational context. Thus, the same research designs with the same academic grade students and even the same age groups can lead to different findings concerning the effects of social media on student psychology in different countries. In other words, the potential positive and negative effects of popular social media like Facebook, Snapchat, Twitter, etc., on students’ affective conditions can differ across different educational settings in different host countries. Thus, significantly more research is needed in different contexts and cultures to compare the results.
There is also a need for further research on the higher education students and how their affective conditions are positively and negatively affected by the prevalent use of social media. University students’ psychological needs might be different from other academic grades and, thus, the patterns of changes that the overall use of social networking can create in their emotions can be also different. Their main reasons for using social media might be different from school students as well, which need to be investigated more thoroughly. The sorts of interventions needed to moderate the potential negative effects of social networking on them can be different too, all requiring a new line of research in education domain.
Finally, there are hopes that considering the ever-increasing popularity of social networking in education, the potential psychological effects of social media on teachers be explored as well. Though teacher psychology has only recently been considered for research, the literature has provided profound insights into teachers developing stress, motivation, self-esteem, and many other emotions. In today’s world driven by global communications in the cyberspace, teachers like everyone else are affecting and being affected by social networking. The comparison theory can hold true for teachers too. Thus, similar threats (of social media) to self-esteem and self-worth can be there for teachers too besides students, which are worth investigating qualitatively and quantitatively.
Probably a new line of research can be initiated to explore the co-development of teacher and learner psychological traits under the influence of social media use in longitudinal studies. These will certainly entail sophisticated research methods to be capable of unraveling the nuances of variation in these traits and their mutual effects, for example, stress, motivation, and self-esteem. If these are incorporated within mixed-approach works of research, more comprehensive and better insightful findings can be expected to emerge. Correlational studies need to be followed by causal studies in educational settings. As many conditions of the educational settings do not allow for having control groups or randomization, probably, experimental studies do not help with this. Innovative research methods, case studies or else, can be used to further explore the causal relations among the different features of social media use and the development of different affective variables in teachers or learners. Examples of such innovative research methods can be process tracing, qualitative comparative analysis, and longitudinal latent factor modeling (for a more comprehensive view, see Hiver and Al-Hoorie, 2019 ).
Author contributions
Both authors listed have made a substantial, direct, and intellectual contribution to the work, and approved it for publication.
This study was sponsored by Wuxi Philosophy and Social Sciences bidding project—“Special Project for Safeguarding the Rights and Interests of Workers in the New Form of Employment” (Grant No. WXSK22-GH-13). This study was sponsored by the Key Project of Party Building and Ideological and Political Education Research of Nanjing University of Posts and Telecommunications—“Research on the Guidance and Countermeasures of Network Public Opinion in Colleges and Universities in the Modern Times” (Grant No. XC 2021002).
Conflict of interest
Author XX was employed by China Mobile Group Jiangsu Co., Ltd.
The remaining author declares that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
Publisher’s note
All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article, or claim that may be made by its manufacturer, is not guaranteed or endorsed by the publisher.
Aalbers, G., McNally, R. J., Heeren, A., de Wit, S., and Fried, E. I. (2018). Social media and depression symptoms: A network perspective. J. Exp. Psychol. Gen. 148, 1454–1462. doi: 10.1037/xge0000528
PubMed Abstract | CrossRef Full Text | Google Scholar
Abbott, J. (2017). Introduction: Assessing the social and political impact of the internet and new social media in Asia. J. Contemp. Asia 43, 579–590. doi: 10.1080/00472336.2013.785698
CrossRef Full Text | Google Scholar
Alahmar, A. T. (2016). The impact of social media on the academic performance of second year medical students at College of Medicine, University of Babylon, Iraq. J. Med. Allied Sci. 6, 77–83. doi: 10.5455/jmas.236927
Banjanin, N., Banjanin, N., Dimitrijevic, I., and Pantic, I. (2015). Relationship between internet use and depression: Focus on physiological mood oscillations, social networking and online addictive behavior. Comp. Hum. Behav. 43, 308–312. doi: 10.1016/j.chb.2014.11.013
Barry, C. T., Sidoti, C. L., Briggs, S. M., Reiter, S. R., and Lindsey, R. A. (2017). Adolescent social media use and mental health from adolescent and parent perspectives. J. Adolesc. 61, 1–11. doi: 10.1016/j.adolescence.2017.08.005
Chang, Y. (2012). The relationship between maladaptive perfectionism with burnout: Testing mediating effect of emotion-focused coping. Pers. Individ. Differ. 53, 635–639. doi: 10.1016/j.paid.2012.05.002
Charoensukmongkol, P. (2018). The impact of social media on social comparison and envy in teenagers: The moderating role of the parent comparing children and in-group competition among friends. J. Child Fam. Stud. 27, 69–79. doi: 10.1007/s10826-017-0872-8
Chukwuere, J. E., and Chukwuere, P. C. (2017). The impact of social media on social lifestyle: A case study of university female students. Gender Behav. 15, 9966–9981.
Google Scholar
Drouin, M., Reining, L., Flanagan, M., Carpenter, M., and Toscos, T. (2018). College students in distress: Can social media be a source of social support? Coll. Stud. J. 52, 494–504.
Dumitrache, S. D., Mitrofan, L., and Petrov, Z. (2012). Self-image and depressive tendencies among adolescent Facebook users. Rev. Psihol. 58, 285–295.
PubMed Abstract | Google Scholar
Fernyhough, C. (2008). Getting Vygotskian about theory of mind: Mediation, dialogue, and the development of social understanding. Dev. Rev. 28, 225–262. doi: 10.1016/j.dr.2007.03.001
Festinger, L. (1954). A Theory of social comparison processes. Hum. Relat. 7, 117–140. doi: 10.1177/001872675400700202
Fleck, J., and Johnson-Migalski, L. (2015). The impact of social media on personal and professional lives: An Adlerian perspective. J. Individ. Psychol. 71, 135–142. doi: 10.1353/jip.2015.0013
Fredrickson, B. L. (2001). The role of positive emotions in positive psychology: The broaden-and-build theory of positive emotions. Am. Psychol. 56, 218–226. doi: 10.1037/0003-066X.56.3.218
Frison, E., and Eggermont, S. (2016). Exploring the relationships between different types of Facebook use, perceived online social support, and adolescents’ depressed mood. Soc. Sci. Compu. Rev. 34, 153–171. doi: 10.1177/0894439314567449
Hanprathet, N., Manwong, M., Khumsri, J., Yingyeun, R., and Phanasathit, M. (2015). Facebook addiction and its relationship with mental health among Thai high school students. J. Med. Assoc. Thailand 98, S81–S90.
Hiver, P., and Al-Hoorie, A. H. (2019). Research Methods for Complexity Theory in Applied Linguistics. Bristol: Multilingual Matters. doi: 10.21832/HIVER5747
Iwamoto, D., and Chun, H. (2020). The emotional impact of social media in higher education. Int. J. High. Educ. 9, 239–247. doi: 10.5430/ijhe.v9n2p239
Keles, B., McCrae, N., and Grealish, A. (2020). A systematic review: The influence of social media on depression, anxiety and psychological distress in adolescents. Int. J. Adolesc. Youth 25, 79–93. doi: 10.1080/02673843.2019.1590851
Ley, B., Ogonowski, C., Hess, J., Reichling, T., Wan, L., and Wulf, V. (2014). Impacts of new technologies on media usage and social behavior in domestic environments. Behav. Inform. Technol. 33, 815–828. doi: 10.1080/0144929X.2013.832383
Li, J.-B., Lau, J. T. F., Mo, P. K. H., Su, X.-F., Tang, J., Qin, Z.-G., et al. (2017). Insomnia partially mediated the association between problematic Internet use and depression among secondary school students in China. J. Behav. Addict. 6, 554–563. doi: 10.1556/2006.6.2017.085
Mathewson, M. (2020). The impact of social media usage on students’ mental health. J. Stud. Affairs 29, 146–160.
Neira, B. C. J., and Barber, B. L. (2014). Social networking site use: Linked to adolescents’ social self-concept, self-esteem, and depressed mood. Aus. J. Psychol. 66, 56–64. doi: 10.1111/ajpy.12034
O’Dea, B., and Campbell, A. (2011). Online social networking amongst teens: Friend or foe? Ann. Rev. CyberTher. Telemed. 9, 108–112.
Radovic, A., Gmelin, T., Stein, B. D., and Miller, E. (2017). Depressed adolescents positive and negative use of social media. J. Adolesc. 55, 5–15. doi: 10.1016/j.adolescence.2016.12.002
Sampasa-Kanyinga, H., and Lewis, R. F. (2015). Frequent use of social networking sites is associated with poor psychological functioning among children and adolescents. Cyberpsychol. Behav. Soc. Network. 18, 380–385. doi: 10.1089/cyber.2015.0055
Sriwilai, K., and Charoensukmongkol, P. (2016). Face it, don’t Facebook it: Impacts of social media addiction on mindfulness, coping strategies and the consequence on emotional exhaustion. Stress Health 32, 427–434. doi: 10.1002/smi.2637
Stapel, D. A. (2007). “In the mind of the beholder: The interpretation comparison model of accessibility effects,” in Assimilation and Contrast in Social Psychology , eds D. A. Stapel and J. Suls (London: Psychology Press), 143–164.
Stapel, D. A., and Koomen, W. (2000). Distinctiveness of others, mutability of selves: Their impact on self-evaluations. J. Pers. Soc. Psychol. 79, 1068–1087. doi: 10.1037//0022-3514.79.6.1068
Tang, F., Wang, X., and Norman, C. S. (2013). An investigation of the impact of media capabilities and extraversion on social presence and user satisfaction. Behav. Inform. Technol. 32, 1060–1073. doi: 10.1080/0144929X.2013.830335
Tsitsika, A. K., Tzavela, E. C., Janikian, M., Ólafsson, K., Iordache, A., Schoenmakers, T. M., et al. (2014). Online social networking in adolescence: Patterns of use in six European countries and links with psychosocial functioning. J. Adolesc. Health 55, 141–147. doi: 10.1016/j.jadohealth.2013.11.010
Vernon, L., Modecki, K. L., and Barber, B. L. (2017). Tracking effects of problematic social networking on adolescent psychopathology: The mediating role of sleep disruptions. J. Clin. Child Adolesc. Psychol. 46, 269–283. doi: 10.1080/15374416.2016.1188702
Virden, A., Trujillo, A., and Predeger, E. (2014). Young adult females’ perceptions of high-risk social media behaviors: A focus-group approach. J. Commun. Health Nurs. 31, 133–144. doi: 10.1080/07370016.2014.926677
Wang, P., Wang, X., Wu, Y., Xie, X., Wang, X., Zhao, F., et al. (2018). Social networking sites addiction and adolescent depression: A moderated mediation model of rumination and self-esteem. Pers. Individ. Differ. 127, 162–167. doi: 10.1016/j.paid.2018.02.008
Weng, L., and Menczer, F. (2015). Topicality and impact in social media: Diverse messages, focused messengers. PLoS One 10:e0118410. doi: 10.1371/journal.pone.0118410
Yan, H., Zhang, R., Oniffrey, T. M., Chen, G., Wang, Y., Wu, Y., et al. (2017). Associations among screen time and unhealthy behaviors, academic performance, and well-being in Chinese adolescents. Int. J. Environ. Res. Public Health 14:596. doi: 10.3390/ijerph14060596
Zareen, N., Karim, N., and Khan, U. A. (2016). Psycho-emotional impact of social media emojis. ISRA Med. J. 8, 257–262.
Zhang, R. (2017). The stress-buffering effect of self-disclosure on Facebook: An examination of stressful life events, social support, and mental health among college students. Comp. Hum. Behav. 75, 527–537. doi: 10.1016/j.chb.2017.05.043
Keywords : affective variables, education, emotions, social media, post-pandemic, emotional needs
Citation: Chen M and Xiao X (2022) The effect of social media on the development of students’ affective variables. Front. Psychol. 13:1010766. doi: 10.3389/fpsyg.2022.1010766
Received: 03 August 2022; Accepted: 25 August 2022; Published: 15 September 2022.
Reviewed by:
Copyright © 2022 Chen and Xiao. This is an open-access article distributed under the terms of the Creative Commons Attribution License (CC BY) . The use, distribution or reproduction in other forums is permitted, provided the original author(s) and the copyright owner(s) are credited and that the original publication in this journal is cited, in accordance with accepted academic practice. No use, distribution or reproduction is permitted which does not comply with these terms.
*Correspondence: Miao Chen, [email protected] ; Xin Xiao, [email protected]
Disclaimer: All claims expressed in this article are solely those of the authors and do not necessarily represent those of their affiliated organizations, or those of the publisher, the editors and the reviewers. Any product that may be evaluated in this article or claim that may be made by its manufacturer is not guaranteed or endorsed by the publisher.
- Open access
- Published: 16 March 2020
Exploring the role of social media in collaborative learning the new domain of learning
- Jamal Abdul Nasir Ansari 1 &
- Nawab Ali Khan 1
Smart Learning Environments volume 7 , Article number: 9 ( 2020 ) Cite this article
390k Accesses
197 Citations
19 Altmetric
Metrics details
This study is an attempt to examine the application and usefulness of social media and mobile devices in transferring the resources and interaction with academicians in higher education institutions across the boundary wall, a hitherto unexplained area of research. This empirical study is based on the survey of 360 students of a university in eastern India, cognising students’ perception on social media and mobile devices through collaborative learning, interactivity with peers, teachers and its significant impact on students’ academic performance. A latent variance-based structural equation model approach was followed for measurement and instrument validation. The study revealed that online social media used for collaborative learning had a significant impact on interactivity with peers, teachers and online knowledge sharing behaviour.
Additionally, interactivity with teachers, peers, and online knowledge sharing behaviour has seen a significant impact on students’ engagement which consequently has a significant impact on students’ academic performance. Grounded to this finding, it would be valuable to mention that use of online social media for collaborative learning facilitate students to be more creative, dynamic and research-oriented. It is purely a domain of knowledge.
Introduction
The explosion of Information and Communication Technology (ICT) has led to an increase in the volume and smoothness in transferring course contents, which further stimulates the appeasement of Digital Learning Communities (DLCs). The millennium and naughtiness age bracket were Information Technology (IT) centric on web space where individual and geopolitical disperse learners accomplished their e-learning goals. The Educause Center for Applied Research [ECAR] ( 2012 ) surveyed students in higher education mentioned that students are pouring the acceptance of mobile computing devices (cellphones, smartphones, and tablet) in Higher Education Institutions (HEIs), roughly 67% surveyed students accepted that mobile devices and social media play a vital role in their academic performance and career enhancement. Mobile devices and social media provide excellent educational e-learning opportunities to the students for academic collaboration, accessing in course contents, and tutors despite the physical boundary (Gikas & Grant, 2013 ). Electronic communication technologies accelerate the pace of their encroachment of every aspect of life, the educational institutions incessantly long decades to struggle in seeing the role of such devices in sharing the contents, usefulness and interactivity style. Adoption and application of mobile devices and social media can provide ample futuristic learning opportunities to the students in accessing course contents as well as interaction with peers and experts (Cavus & Ibrahim, 2008 , 2009 ; Kukulska-Hulme & Shield, 2008 ; Nihalani & Mayrath, 2010 ; Richardson & Lenarcic, 2008 , Shih, 2007 ). Recently Pew Research Center reported that 55% American teenage age bracket of 15–17 years using online social networking sites, i.e. Myspace and Facebook (Reuben, 2008 ). Social media, the fast triggering the mean of virtual communication, internet-based technologies changed the life pattern of young youth.
Use of social media and mobile devices presents both advantages as well as challenges, mostly its benefits seen in terms of accessing course contents, video clip, transfer of the instructional notes etc. Overall students feel that social media and mobile devices are the cheap and convenient tools of obtaining relevant information. Studies in western countries have confronted that online social media use for collaborative learning has a significant contribution to students’ academic performance and satisfaction (Zhu, 2012 ). The purpose of this research project was to explore how learning and teaching activities in higher education institutions were affected by the integration and application of mobile devices in sharing the resource materials, interaction with colleagues and students’ academic performance. The broad goal of this research was to contemporise the in-depth perspectives of students’ perception of mobile devices and social media in learning and teaching activities. However, this research paper paid attention to only students’ experiences, and their understanding of mobile devices and social media fetched changes and its competency in academic performance. The fundamental research question of this research was, what are the opinions of students on social media and mobile devices when it is integrating into higher education for accessing, interacting with peers.
A researcher of the University of Central Florida reported that electronic devices and social media create an opportunity to the students for collaborative learning and also allowed the students in sharing the resource materials to the colleagues (Gikas & Grant, 2013 ). The result of the eight Egyptian universities confirmed that social media have the significant impact on higher education institutions especially in term of learning tools and teaching aids, faculty members’ use of social media seen at a minimum level due to several barriers (internet accessibility, mobile devices etc.).
Social media and mobile devices allow the students to create, edit and share the course contents in textual, video or audio forms. These technological innovations give birth to a new kind of learning cultures, learning based on the principles of collective exploration and interaction (Selwyn, 2012 ). Social media the phenomena originated in 2005 after the Web2.0 existence into the reality, defined more clearly as “a group of Internet-based applications that build on the ideological and technological foundation of web 2.0 and allow creation and exchange of user-generated contents (Kaplan & Haenlein, 2010 ). Mobile devices and social media provide opportunities to the students for accessing resources, materials, course contents, interaction with mentor and colleagues (Cavus & Ibrahim, 2008 , 2009 ; Richardson & Lenarcic, 2008 ).
Social media platform in academic institutions allows students to interact with their mentors, access their course contents, customisation and build students communities (Greenhow, 2011a , 2011b ). 90% school going students currently utilise the internet consistently, with more than 75% teenagers using online networking sites for e-learning (DeBell & Chapman, 2006 ; Lenhart, Arafeh, & Smith, 2008 ; Lenhart, Madden, & Hitlin, 2005 ). The result of the focus group interview of the students in 3 different universities in the United States confirmed that use of social media created opportunities to the learners for collaborative learning, creating and engaging the students in various extra curriculum activities (Gikas & Grant, 2013 ).
Research background and hypotheses
The technological innovation and increased use of the internet for e-learning by the students in higher education institutions has brought revolutionary changes in communication pattern. A report on 3000 college students in the United States revealed that 90% using Facebook while 37% using Twitter to share the resource materials as cited in (Elkaseh, Wong, & Fung, 2016 ). A study highlighted that the usage of social networking sites in educational institutions has a practical outcome on students’ learning outcomes (Jackson, 2011 ). The empirical investigation over 252 undergraduate students of business and management showed that time spent on twitter and involvement in managing social lives and sharing information, course-related influences their performance (Evans, 2014 ).
Social media for collaborative learning, interactivity with teachers, interactivity with peers
Many kinds of research confronted on the applicability of social media and mobile devices in higher education for interaction with colleagues.90% of faculty members use some social media in courses they were usually teaching or professional purposes out of the campus life. Facebook and YouTube are the most visited sites for the professional outcomes, around 2/3rd of the all-faculty use some medium fora class session, and 30% posted contents for students engagement in reading, view materials (Moran, Seaman, & Tinti-Kane, 2011 ). Use of social media and mobile devices in higher education is relatively new phenomena, completely hitherto area of research. Research on the students of faculty of Economics at University of Mortar, Bosnia, and Herzegovina reported that social media is already used for the sharing the materials and exchanges of information and students are ready for active use of social networking site (slide share etc.) for educational purposes mainly e-learning and communication (Mirela Mabić, 2014 ).
The report published by the U.S. higher education department stated that the majority of the faculty members engaged in different form of the social media for professional purposes, use of social media for teaching international business, sharing contents with the far way students, the use of social media and mobile devices for sharing and the interactive nature of online and mobile technologies build a better learning environment at international level. Responses on 308 graduate and postgraduate students in Saudi Arabia University exhibited that positive correlation between chatting, online discussion and file sharing and knowledge sharing, and entertainment and enjoyment with students learning (Eid & Al-Jabri, 2016 ). The quantitative study on 168 faculty members using partial least square (PLS-SEM) at Carnegie classified Doctoral Research University in the USA confirmed that perceived usefulness, external pressure and compatibility of task-technology have positive effect on social media use, the higher the degree of the perceived risk of social media, the less likely to use the technological tools for classroom instruction, the study further revealed that use of social media for collaborative learning has a positive effect on students learning outcome and satisfaction (Cao, Ajjan, & Hong, 2013 ). Therefore, the authors have hypothesized:
H1: Use of social media for collaborative learning is positively associated with interactivity with teachers.
Additionally, Madden and Zickuhr ( 2011 ) concluded that 83% of internet user within the age bracket of 18–29 years adopting social media for interaction with colleagues. Kabilan, Ahmad, and Abidin ( 2010 ) made an empirical investigation on 300 students at University Sains Malaysia and concluded that 74% students found to be the same view that social media infuses constructive attitude towards learning English (Fig. 1 ).
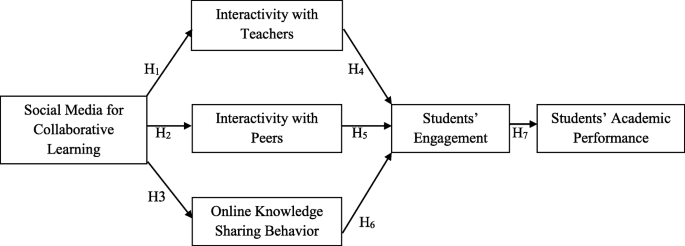
Research Model
Reuben ( 2008 ) concluded in his study on social media usage among professional institutions revealed that Facebook and YouTube used over half of 148 higher education institutions. Nevertheless, a recent survey of 456 accredited United States institutions highlighted 100% using some form of social media, notably Facebook 98% and Twitter 84% for e-learning purposes, interaction with mentors (Barnes & Lescault, 2011 ).
Information and communication technology (ICT), such as web-based application and social networking sites enhances the collaboration and construction of knowledge byway of instruction with outside experts (Zhu, 2012 ). A positive statistically significant relationship was found between student’s use of a variety of social media tools and the colleague’s fellow as well as the overall quality of experiences (Rutherford, 2010 ). The potential use of social media leads to collaborative learning environments which allow students to share education-related materials and contents (Fisher & Baird, 2006 ). The report of 233 students in the United States higher educations confirmed that more recluse students interact through social media, which assist them in collaborative learning and boosting their self-confidence (Voorn & Kommers, 2013 ). Thus hypotheses as
H2: Use of social media for collaborative learning is positively associated with interactivity with peers.
Social media for collaborative learning, interactivity with peers, online knowledge sharing behaviour and students’ engagement
Students’ engagement in social media and its types represent their physical and mental involvement and time spent boost to the enhancement of educational Excellency, time spent on interaction with peers, teachers for collaborative learning (Kuh, 2007 ). Students’ engagement enhanced when interacting with peers and teacher was in the same direction, shares of ideas (Chickering & Gamson, 1987 ). Engagement is an active state that is influenced by interaction or lack thereof (Leece, 2011 ). With the advancement in information technology, the virtual world becomes the storehouse of the information. Liccardi et al. ( 2007 ) concluded that 30% students were noted to be active on social media for interaction with their colleagues, tutors, and friends while more than 52% used some social media forms for video sharing, blogs, chatting, and wiki during their class time. E-learning becomes now sharp and powerful tools in information technology and makes a substantial impact on the student’s academic performance. Sharing your knowledge will make you better. Social network ties were shown to be the best predictors of online knowledge sharing intention, which in turn associated with knowledge sharing behaviour (Chen, Chen, & Kinshuk, 2009 ). Social media provides the robust personalised, interactive learning environment and enhances in self-motivation as cited in (Al-Mukhaini, Al-Qayoudhi, & Al-Badi, 2014 ). Therefore, it was hypothesised that:
H3: Use of social media for collaborative learning is positively associated with online knowledge sharing behaviour.
Broadly Speaking social media/sites allow the students to interact, share the contents with colleagues, also assisting in building connections with others (Cain, 2008 ). In the present era, the majority of the college-going students are seen to be frequent users of these sophisticated devices to keep them informed and updated about the external affair. Facebook reported per day 1,00,000 new members join; Facebook is the most preferred social networking sites among the students of the United States as cited in (Cain, 2008 ). The researcher of the school of engineering, Swiss Federal Institute of Technology Lausanne, Switzerland, designed and developed Grasp, a social media platform for their students’ collaborative learning, sharing contents (Bogdanov et al., 2012 ). The utility and its usefulness could be seen in the University of Geneva and Tongji University at both two educational places students were satisfied and accept ‘ Grasp’ to collect, organised and share the contents. Students use of social media will interact ubiquity, heterogeneous and engaged in large groups (Wankel, 2009 ). So we hypotheses
H4: More interaction with teachers leads to higher students’ engagement.
However, a similar report published on 233 students revealed that social media assisted in their collaborative learning and self-confidence as they prefer communication technology than face to face communication. Although, the students have the willingness to communicate via social media platform than face to face (Voorn & Kommers, 2013 ). The potential use of social media tools facilitates in achieving higher-level learning through collaboration with colleagues and other renewed experts in their field (Junco, Heiberger, & Loken, 2011 ; Meyer, 2010 ; Novak, Razzouk, & Johnson, 2012 ; Redecker, Ala-Mutka, & Punie, 2010 ). Academic self-efficacy and optimism were found to be strongly related to performance, adjustment and consequently both directly impacted on student’s academic performance (Chemers, Hu, & Garcia, 2001 ). Data of 723 Malaysian researchers confirmed that both male and female students were satisfied with the use of social media for collaborative learning and engagement was found positively affected with learning performance (Al-Rahmi, Alias, Othman, Marin, & Tur, 2018 ). Social media were seen as a powerful driver for learning activities in terms of frankness, interactivity, and friendliness.
Junco et al. ( 2011 ) conducted research on the specific purpose of the social media; how Twitter impacted students’ engagement, found that it was extent discussion out of class, their participation in panel group (Rodriguez, 2011 ). A comparative study conducted by (Roblyer, McDaniel, Webb, Herman, & Witty, 2010 ) revealed that students were more techno-oriented than faculty members and more likely using Facebook and such similar communication technology to support their class-related task. Additionally, faculty members were more likely to use traditional techniques, i.e. email. Thus hypotheses framed is that:
H5: More interaction with peers ultimately leads to better students’ engagement.
Social networking sites and social media are closely similar, which provide a platform where students can interact, communicate, and share emotional intelligence and looking for people with other attitudes (Gikas & Grant, 2013 ). Facebook and YouTube channel use also increased in the skills/ability and knowledge and outcomes (Daniel, Isaac, & Janet, 2017 ). It was highlighted that 90% of faculty members were using some sort of social media in their courses/ teaching. Facebook was the most visited social media sites as per study, 40% of faculty members requested students to read and views content posted on social media; majority reports that videos, wiki, etc. the primary source of acquiring knowledge, social networking sites valuable tool/source of collaborative learning (Moran et al., 2011 ). However, more interestingly, in a study which was carried out on 658 faculty members in the eight different state university of Turkey, concluded that nearly half of the faculty member has some social media accounts.
Further reported that adopting social media for educational purposes, the primary motivational factor which stimulates them to use was effective and quick means of communication technology (Akçayır, 2017 ). Thus hypotheses formulated is:
H6: Online knowledge sharing behaviour is positively associated with the students’ engagement.
Using multiple treatment research design, following act-react to increase students’ academic performance and productivity, it was observed when self–monitoring record sheet was placed before students and seen that students engagement and educational productivity was increased (Rock & Thead, 2007 ). Student engagement in extra curriculum activities promotes academic achievement (Skinner & Belmont, 1993 ), increases grade rate (Connell, Spencer, & Aber, 1994 ), triggering student performance and positive expectations about academic abilities (Skinner & Belmont, 1993 ). They are spending time on online social networking sites linked to students engagement, which works as the motivator of academic performance (Fan & Williams, 2010 ). Moreover, it was noted in a survey of over 236 Malaysian students that weak association found between the online game and student’s academic performance (Eow, Ali, Mahmud, & Baki, 2009 ). In a survey of 671 students in Jordan, it was revealed that student’s engagement directly influences academic performance, also seen the indirect effect of parental involvement over academic performance (Al-Alwan, 2014 ). Engaged students are perceptive and highly active in classroom activities, ready to participate in different classroom extra activities and expose motivation to learn, which finally leads in academic achievement (Reyes, Brackett, Rivers, White, & Salovey, 2012 ). A mediated role of students engagement seen in 1399 students’ classroom emotional climate and grades (Reyes et al., 2012 ). A statistically significant relation was noticed between online lecture and exam performance.
Nonetheless, intelligence quotient, personality factors, students must be engaged in learning activities as cited in (Bertheussen & Myrland, 2016 ). The report of the 1906 students at 7 universities in Colombia confirmed that the weak correlation between collaborative learning, students faculty interaction with academic performance (Pineda-Báez et al., 2014 ) Thus, the hypothesis
H7: Student's Engagement is positively associated with the student's academic performance.
Methodology
To check the students’ perception on social media for collaborative learning in higher education institutions, Data were gathered both offline and online survey administered to students from one public university in Eastern India (BBAU, Lucknow). For the sake of this study, indicators of interactivity with peers and teachers, the items of students engagement, the statement of social media for collaborative learning, and the elements of students’ academic performance were adopted from (AL-Rahmi & Othman, 2013 ). The statement of online knowledge sharing behaviour was taken from (Ma & Yuen, 2011 ).
The indicators of all variables which were mentioned above are measured on the standardised seven-point Likert scale with the anchor (1-Strongly Disagree, to 7-Strongly Agree). Interactivity with peers was measured using four indicators; the sample items using social media in class facilitates interaction with peers ; interactivity with teachers was measured using four symbols, the sample item is using social media in class allows me to discuss with the teacher. ; engagement was measured using three indicators by using social media I felt that my opinions had been taken into account in this class ; social media for collaborative learning was measured using four indicators collaborative learning experience in social media environment is better than in a face-to-face learning environment ; students’ academic performance was measured using five signs using social media to build a student-lecturer relationship with my lecturers, and this improves my academic performance ; online knowledge sharing behaviour was assessed using five symbols the counsel was received from other colleague using social media has increased our experience .
Procedure and measurement
A sample of 360 undergraduate students was collected by convenience sampling method of a public university in Eastern India. The proposed model of study was measured and evaluated using variance based structured equation model (SEM)-a latent multi variance technique which provides the concurrent estimation of structural and measurement model that does not meet parametric assumption (Coelho & Duarte, 2016 ; Haryono & Wardoyo, 2012 ; Lee, 2007 ; Moqbel, Nevo, & Kock, 2013 ; Raykov & Marcoulides, 2000 ; Williams, Rana, & Dwivedi, 2015 ). The confirmatory factor analysis (CFA) was conducted to ensure whether the widely accepted criterion of discriminate and convergent validity met or not. The loading of all the indicators should be 0.50 or more (Field, 2011 ; Hair, Anderson, Tatham, & Black, 1992 ). And it should be statistically significant at least at the 0.05.
Demographic analysis (Table 1 )
The majority of the students in this study were females (50.8%) while male students were only 49.2% with age 15–20 years (71.7%). It could be pointed out at this juncture that the majority of the students (53.9%) in BBAU were joined at least 1–5 academic pages for their getting information, awareness and knowledge. 46.1% of students spent 1–5 h per week on social networking sites for collaborative learning, interaction with teachers at an international level. The different academic pages followed for accessing material, communication with the faculty members stood at 44.4%, there would be various forms of the social networking sites (LinkedIn, Slide Share, YouTube Channel, Researchgate) which provide the facility of online collaborative learning, a platform at which both faculty members and students engaged in learning activities.
As per report (Nasir, Khatoon, & Bharadwaj, 2018 ), most of the social media user in India are college-going students, 33% girls followed by 27% boys students, and this reports also forecasted that India is going to become the highest 370.77 million internet users in 2022. Additionally, the majority of the faculty members use smartphone 44% to connect with the students for sharing material content. Technological advantages were the pivotal motivational force which stimulates faculty members and students to exploits the opportunities of resource materials (Nasir & Khan, 2018 ) (Fig. 2 ).
Reasons for Using Social Media
When the students were asked for what reason did they use social media, it was seen that rarely using for self-promotion, very frequently using for self-education, often used for passing the time with friends, and so many fruitful information the image mentioned above depicting.
Instrument validation
The structural model was applied to scrutinize the potency and statistically significant relationship among unobserved variables. The present measurement model was evaluated using Confirmatory Factor Analysis (CFA), and allied procedures to examine the relationship among hypothetical latent variables has acceptable reliability and validity. This study used both SPSS 20.0 and AMOS to check measurement and structural model (Field, 2013 ; Hair, Anderson, et al., 1992 ; Mooi & Sarstedt, 2011 ; Norusis, 2011 ).
The Confirmatory Factor Analysis (CFA) was conducted to ensure whether the widely accepted criterion of discriminant and convergent validity met or not. The loading of all the indicators should be 0.70 or more it should be statistically significant at least at the 0.05 (Field, 2011 ; Hair, Anderson, et al., 1992 ).
CR or CA-based tests measured the reliability of the proposed measurement model. The CA provides an estimate of the indicators intercorrelation (Henseler & Sarstedt, 2013 . The benchmark limits of the CA is 0.7 or more (Nunnally & Bernstein, 1994 ). As per Table 2 , all latent variables in this study above the recommended threshold limit. Although, Average Variance Extracted (AVE) has also been demonstrated which exceed the benchmark limit 0.5. Thus all the above-specified values revealed that our instrument is valid and effective. (See Table 2 for the additional information) (Table 3 ).
In a nutshell, the measurement model clear numerous stringent tests of convergent validity, discriminant validity, reliability, and absence of multi-collinearity. The finding demonstrated that our model meets widely accepted data validation criteria. (Schumacker & Lomax, 2010 ).
The model fit was evaluated through the Chi-Square/degree of freedom (CMIN/DF), Root Mean Residual (RMR), Root Mean Square Error of Approximation (RMSEA), Comparative Fit Index (CFI), and Goodness of fit index (GFI) and Tucker-Lewis Index (TLI). The benchmark limit of the CFI, TLI, and GFI 0.90or more (Hair et al., 2016 ; Kock, 2011 ). The model study demonstrated in the table, as mentioned above 4 that the minimum threshold limit was achieved (See Table 4 for additional diagnosis).
Path coefficient of several hypotheses has been demonstrated in Fig. 3 , which is a variable par relationship. β (beta) Coefficients, standardised partial regression coefficients signify the powers of the multivariate relationship among latent variables in the model. Remarkably, it was observed that seven out of the seven proposed hypotheses were accepted and 78% of the explained variance in students’ academic performance, 60% explained variance in interactivity with teachers, 48% variance in interactivity with peers, 43% variance in online knowledge sharing behaviour and 79% variance in students’ engagement. Social media collaborative learning has a significant association with teacher interactivity(β = .693, P < 0.001), demonstrating that there is a direct effect on interaction with the teacher by social media when other variables are controlled. On the other hand, use of social media for collaborative learning has noticed statistically significant positive relationship with peers interactivity (β = .704, p < 0.001) meaning thereby, collaborative learning on social media by university students, leads to the high degree of interaction with peers, colleagues. Implied 10% rise in social media use for learning purposes, expected 7.04% increase in interaction with peers.
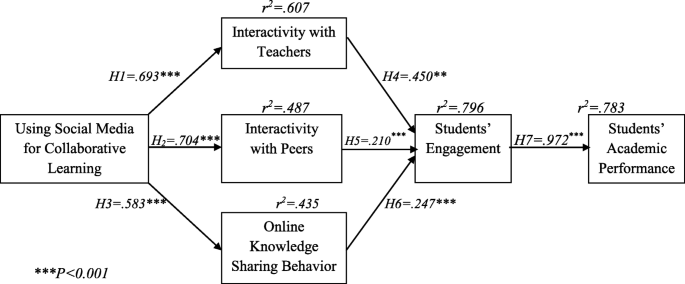
Path Diagram
Use of social media for collaborating learning has a significant positive association with online knowledge sharing behaviour (β = .583, p < 0.001), meaning thereby that the more intense use of social media for collaborative learning by university students, the more knowledge sharing between peers and colleagues. Also, interaction with the teacher seen the significant statistical positive association with students engagement (β = .450, p < 0.001), telling that the more conversation with teachers, leads to a high level of students engagement. Similarly, the practical interpretation of this result is that there is an expected 4.5% increase in student’s participation for every 10% increase in interaction with teachers. Interaction with peers has a significant positive association with students engagement (β = .210, p < 0.001). Practically, the finding revealed that 10% upturn in student’s involvement, there is a 2.1% increase in peer’s interaction. There is a significant positive association between online knowledge sharing behaviour and students engagement (β = 0.247, p < 0.001), and finally students engagement has been a statistically significant positive relationship with students’ academic performance (β = .972, p < 0.001), this is the clear indication that more engaged students in collaborative learning via social media leads to better students’ academic performance.
Discussion and implication
There is a continuing discussion in the academic literature that use of such social media and social networking sites would facilitate collaborative learning. It is human psychology generally that such communication media technology seems only for entertainment, but it should be noted here carefully that if such communication technology would be followed with due attention prove productive. It is essential to acknowledge that most university students nowadays adopting social media communication to interact with colleagues, teachers and also making the group be in touch with old friends and even a convenient source of transferring the resources. In the present era, the majority of the university students having diversified social media community groups like Whatsapp, Facebook pages following different academic web pages to upgrade their knowledge.
Practically for every 10% rise in students’ engagement, expected to be 2.1% increase in peer interaction. As the study suggested that students engage in different sites, they start discussing with colleagues. More engaged students in collaborative learning through social media lead better students’ academic performance. The present study revealed that for every 10% increase in student’s engagement, there would be an expected increase in student academic performance at a rate of 9.72. This extensive research finding revealed that the application of online social media would facilitate the students to become more creative, dynamics and connect to the worldwide instructor for collaborative learning.
Accordingly, the use of online social media for collaborative learning, interaction with mentors and colleagues leadbetter student’s engagement which consequently affects student’s academic performance. The higher education authority should provide such a platform which can nurture the student’s intellectual talents. Based on the empirical investigation, it would be said that students’ engagement, social media communication devices facilitate students to retrieve information and interact with others in real-time regarding sharing teaching materials contents. Additionally, such sophisticated communication devices would prove to be more useful to those students who feel too shy in front of peers; teachers may open up on the web for the collaborative learning and teaching in the global scenario and also beneficial for physically challenged students. It would also make sense that intensive use of such sophisticated technology in teaching pedagogical in higher education further facilitates the teachers and students to interact digitally, web-based learning, creating discussion group, etc. The result of this investigation confirmed that use of social media for collaborative learning purposes, interaction with peers, and teacher affect their academic performance positively, meaning at this moment that implementation of such sophisticated communication technology would bring revolutionary, drastic changes in higher education for international collaborative learning (Table 5 ).
Limitations and future direction
Like all the studies, this study is also not exempted from the pitfalls, lacunas, and drawbacks. The first and foremost research limitation is it ignores the addiction of social media; excess use may lead to destruction, deviation from the focal point. The study only confined to only one academic institution. Hence, the finding of the project cannot be generalised as a whole. The significant positive results were found in this study due to the fact that the social media and mobile devices are frequently used by the university going students not only as a means of gratification but also for educational purposes.
Secondly, this study was conducted on university students, ignoring the faculty members, it might be possible that the faculty members would not have been interested in interacting with the students. Thus, future research could be possible towards faculty members in different higher education institutions. To the authors’ best reliance, this is the first and prime study to check the usefulness and applicability of social media in the higher education system in the Indian context.
Concluding observations
Based on the empirical investigation, it could be noted that application and usefulness of the social media in transferring the resource materials, collaborative learning and interaction with the colleagues as well as teachers would facilitate students to be more enthusiastic and dynamic. This study provides guidelines to the corporate world in formulating strategies regarding the use of social media for collaborative learning.
Availability of data and materials
The corresponding author declared here all types of data used in this study available for any clarification. The author of this manuscript ready for any justification regarding the data set. To make publically available of the data used in this study, the seeker must mail to the mentioned email address. The profile of the respondents was completely confidential.
Akçayır, G. (2017). Why do faculty members use or not use social networking sites for education? Computers in Human Behavior, 71 , 378–385.
Article Google Scholar
Al-Alwan, A. F. (2014). Modeling the relations among parental involvement, school engagement and academic performance of high school students. International Education Studies, 7 (4), 47–56.
Al-Mukhaini, E. M., Al-Qayoudhi, W. S., & Al-Badi, A. H. (2014). Adoption of social networking in education: A study of the use of social networks by higher education students in Oman. Journal of International Education Research, 10 (2), 143–154.
Google Scholar
Al-Rahmi, W. M., Alias, N., Othman, M. S., Marin, V. I., & Tur, G. (2018). A model of factors affecting learning performance through the use of social media in Malaysian higher education. Computers & Education, 121 , 59–72.
Al-Rahmi, W. M., & Othman, M. S. (2013). Evaluating student’s satisfaction of using social media through collaborative learning in higher education. International Journal of Advances in Engineering & Technology, 6 (4), 1541–1551.
Arbuckle, J. (2008). Amos 17.0 user's guide . Chicago: SPSS Inc..
Barnes, N. G., & Lescault, A. M. (2011). Social media adoption soars as higher-ed experiments and reevaluates its use of new communications tools . North Dartmouth: Center for Marketing Research. University of Massachusetts Dartmouth.
Bertheussen, B. A., & Myrland, Ø. (2016). Relation between academic performance and students’ engagement in digital learning activities. Journal of Education for Business, 91 (3), 125–131.
Bogdanov, E., Limpens, F., Li, N., El Helou, S., Salzmann, C., & Gillet, D. (2012). A social media platform in higher education. In Proceedings of the 2012 IEEE Global Engineering Education Conference (EDUCON) (pp. 1–8). IEEE.
Byrne, B. M. (1994). Structural equation modeling with EQS and EQS/windows: basic concepts, applications, and programming . Thousand Oaks: Sage.
Cain, J. (2008). Online social networking issues within academia and pharmacy education. American Journal of Pharmaceutical Education. https://doi.org/10.5688/aj720110 .
Cao, Y., Ajjan, H., & Hong, P. (2013). Using social media applications for educational outcomes in college teaching: a structural equation analysis. British Journal of Educational Technology, 44 (4), 581–593. https://doi.org/10.1111/bjet.12066 .
Cavus, N., & Ibrahim, D. (2008). A mobile tool for learning English words, Online Submission (pp. 6–9) Retrieved from http://libezproxy.open.ac.uk/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=eric&AN=ED504283&site=ehost-live&scope=site .
Cavus, N., & Ibrahim, D. (2009). M-learning: An experiment in using SMS to support learning new English language words. British Journal of Educational Technology, 40 (1), 78–91.
Chemers, M. M., Hu, L. T., & Garcia, B. F. (2001). Academic self-efficacy and first-year college student performance and adjustment. Journal of Educational Psychology, 93 (1), 55–64. https://doi.org/10.1037/0022-0663.93.1.55 .
Chen, I. Y. L., Chen, N.-S., & Kinshuk. (2009). International forum of Educational Technology & Society Examining the factors influencing participants’ knowledge sharing behavior in virtual learning communities published by : International forum of Educational Technology & Society Examining the factor. Educational Technology & Society, 12 (1), 134–148.
Chickering, A. W., & Gamson, Z. F. (1987). Seven principles for good practise in undergraduate education. AAHE bulletin, 3 , 7.
Coelho, J., & Duarte, C. (2016). A literature survey on older adults' use of social network services and social applications. Computers in Human Behavior, 58 , 187–205.
Connell, J. P., Spencer, M. B., & Aber, J. L. (1994). Educational risk and resilience in African-American youth: Context, self, action, and outcomes in school. Child Development, 65 (2), 493–506.
Daniel, E. A., Isaac, E. N., & Janet, A. K. (2017). Influence of Facebook usage on employee productivity: A case of university of cape coast staff. African Journal of Business Management, 11 (6), 110–116. https://doi.org/10.5897/AJBM2017.8265 .
DeBell, M., & Chapman, C. (2006). Computer and internet use by students in 2003. Statistical analysis report. NCES 2006-065. National Center for education statistics.
Dziuban, C., & Walker, J. D. (2012). ECAR Study of Undergraduate Students and Information Technology, 2012 (Research Report) . Louisville: EDUCAUSE Centre for Applied Research.
Eid, M. I. M., & Al-Jabri, I. M. (2016). Social networking, knowledge sharing, and student learning: The case of university students. Computers and Education, 99 , 14–27. https://doi.org/10.1016/j.compedu.2016.04.007 .
Elkaseh, A. M., Wong, K. W., & Fung, C. C. (2016). Perceived ease of use and perceived usefulness of social media for e-learning in Libyan higher education: A structural equation modeling analysis. International Journal of Information and Education Technology, 6 (3), 192.
Eow, Y. L., Ali, W. Z. b. W., Mahmud, R. b., & Baki, R. (2009). Form one students’ engagement with computer games and its effect on their academic achievement in a Malaysian secondary school. Computers and Education, 53 (4), 1082–1091. https://doi.org/10.1016/j.compedu.2009.05.013 .
Evans, C. (2014). Twitter for teaching: Can social media be used to enhance the process of learning? British Journal of Educational Wiley Online Library, 45 (5), 902–915. https://doi.org/10.1111/bjet.12099 .
Fan, W., & Williams, C. M. (2010). The effects of parental involvement on students’ academic self-efficacy, engagement and intrinsic motivation. Educational Psychology, 30 (1), 53–74. https://doi.org/10.1080/01443410903353302 .
Field, A. (2011). Discovering statistics using SPSS: (and sex and drugs and rock'n'roll) (Vol. 497). London: Sage.
Field, A. (2013). Factor analysis using SPSS. Scientific Research and Essays, 22 (June), 1–26. https://doi.org/10.1016/B978-0-444-52272-6.00519-5 .
Fisher, M., & Baird, D. E. (2006). Making mLearning work: Utilizing mobile technology for active exploration, collaboration, assessment, and reflection in higher education. Journal of Educational Technology Systems, 35 (1), 3–30.
Gikas, J., & Grant, M. M. (2013). Mobile computing devices in higher education: Student perspectives on learning with cellphones, smartphones & social media. Internet and Higher Education Mobile, 19 , 18–26. https://doi.org/10.1016/j.iheduc.2013.06.002 .
Greenhow, C. (2011a). Online social networks and learning. On the horizon, 19 (1), 4–12.
Greenhow, C. (2011b). Youth, learning, and social media. Journal of Educational Computing Research, 45 (2), 139–146. https://doi.org/10.2190/EC.45.2.a .
Hair Anderson, R. E., Tatham, R. L., & Black, W. C. (1992). Multivariate data analysis. International Journal of Pharmaceutics . https://doi.org/10.1016/j.ijpharm.2011.02.019 .
Hair Jr., J. F., Sarstedt, M., Matthews, L. M., & Ringle, C. M. (2016). Identifying and treating unobserved heterogeneity with FIMIX-PLS: part I–method. European Business Review.
Harrington, D. (2009). Confirmatory factor analysis . Oxford university press.
Haryono, S., & Wardoyo, P. (2012). Structural Equation Modeling (Vol. 331).
Henseler, J., & Sarstedt, M. (2013). Goodness-of-fit indices for partial least squares path modeling. Computational Statistics, 28 (2), 565–580.
Jackson, C. (2011). Your students love social media… and so can you. Teaching Tolerance, 39 , 38–41.
Junco, R., Heiberger, G., & Loken, E. (2011). The effect of twitter on college student engagement and grades. Journal of Computer Assisted Learning, 27 (2), 119–132.
Kabilan, M. K., Ahmad, N., & Abidin, M. J. Z. (2010). Facebook: An online environment for learning of English in institutions of higher education? The Internet and Higher Education, 13 (4), 179–187.
Kaplan, A. M., & Haenlein, M. (2010). Users of the world, unite! The challenges and opportunities of social media. Business Horizons, 53 (1), 59–68.
Kock, N. (2011). Using WarpPLS in e-collaboration studies: Mediating effects, control and second order variables, and algorithm choices. International Journal of e-Collaboration (IJeC), 7 (3), 1–13.
Kuh, G. D. (2007). What student engagement data tell us about college readiness. Peer Review, 9 (1), 4–8.
Kukulska-Hulme, A., & Shield, L. (2008). An overview of mobile assisted language learning: From content delivery to supported collaboration and interaction. ReCALL, 20 (3), 271–289.
Lee, S.-Y. (2007). Structural equation modeling: A Bayesian approach (Wiley series in probability and statistics). Ecotoxicology and Environmental Safety, 73 . https://doi.org/10.1016/j.ecoenv.2009.09.012 .
Leece, R. (2011). Engaging students through social media. Journal of the Australian and New Zealand Student Services Association, 38 , 10–14 Retrieved from https://www.researchgate.net/profile/Anthony_Jorm/publication/235003484_Introduction_to_guidelines_for_tertiary_education_institutions_to_assist_them_in_supporting_students_with_mental_health_problems/links/0c96052ba5314e1202000000.pdf#page=67 .
Lenhart, A., Arafeh, S., & Smith, A. (2008). Writing, technology and teens . Pew Internet & American Life Project.
Lenhart, A., Madden, M., & Hitlin, P. (2005). Teens and technology (p. 2008). Washington, DC: Pew Charitable Trusts Retrieved September 29.
Liccardi, I., Ounnas, A., Pau, R., Massey, E., Kinnunen, P., Lewthwaite, S., …, Sarkar, C. (2007). The role of social networks in students’ learning experiences. In ACM Sigcse Bulletin (39, 4, 224–237).
Ma, W. W. K., & Yuen, A. H. K. (2011). Understanding online knowledge sharing: An interpersonal relationship perspective. Computers & Education, 56 (1), 210–219.
Madden, M., & Zickuhr, K. (2011). 65% of online adults use social networking sites. Pew Internet & American Life Project, 1 , 14.
Meyer, K. A. (2010). A comparison of web 2.0 tools in a doctoral course. The Internet and Higher Education, 13 (4), 226–232.
Mirela Mabić, D. G. (2014). Facebook as a learning tool. Igarss, 2014 (1), 1–5. https://doi.org/10.1007/s13398-014-0173-7.2 .
Mooi, E., & Sarstedt, M. (2011). A concise guide to market research: The process, data, and methods using IBM SPSS statistics . Springeringer. https://doi.org/10.1007/978-3-642-12541-6 .
Moqbel, M., Nevo, S., & Kock, N. (2013). Organizational members’ use of social networking sites and job performance. Information Technology & People, 26 (3), 240–264. https://doi.org/10.1108/ITP-10-2012-0110 .
Moran, M., Seaman, J., & Tinti-Kane, H. (2011). Teaching, learning, and sharing: How Today’s higher education faculty use social media (pp. 1–16). Babson survey research group, (April. https://doi.org/10.1016/j.chb.2013.06.015 .
Nasir, J. A., & Khan, N. A. (2018). Faculty member usage of social media and mobile devices in higher education institution. International Journal of Advance and Innovative Research, 6 (1), 17–25.
Nasir, J. A., Khatoon, A., & Bharadwaj, S. (2018). Social media users in India: A futuristic approach. International Journal of Research and Analytical Reviews, 5 (4), 762–765 Retrieved from http://ijrar.com/ .
Nihalani, P. K., & Mayrath, M. C. (2010). Statistics I. Findings from using an iPhone app in a higher education course. In White Paper .
Norusis, M. (2011). IBM SPSS statistics 20 brief guide (pp. 1–170). IBM Corporation Retrieved from http://www.ibm.com/support .
Novak, E., Razzouk, R., & Johnson, T. E. (2012). The educational use of social annotation tools in higher education: A literature review. The Internet and Higher Education, 15 (1), 39–49.
Nunnally, J. C., & Bernstein, I. H. (1994). Psychological theory .
Pineda-Báez, C., José-Javier, B. A., Rubiano-Bello, Á., Pava-García, N., Suárez-García, R., & Cruz-Becerra, F. (2014). Student engagement and academic performance in the Colombian University context. RELIEVE-Revista Electrónica de Investigación y Evaluación Educativa, 20 (2), 1–19.
Raykov, T., & Marcoulides, G. A. (2000). A First Course in Structural Equation Modeling .
Redecker, C., Ala-Mutka, K., & Punie, Y. (2010). Learning 2.0-the impact of social media on learning in Europe. Policy brief. JRC scientific and technical report. EUR JRC56958 EN, Available from http://bit.ly/cljlpq . Accessed 6 Feb 2011.
Reuben, B. R. (2008). The use of social Media in Higher Education for marketing and communications : A guide for professionals in higher education (Vol. 5) Retrieved from httpdoteduguru comwpcontentuploads200808socialmediainhighereducation pdf)). https://doi.org/10.1108/S2044-9968(2012)0000005018 .
Book Google Scholar
Reyes, M. R., Brackett, M. A., Rivers, S. E., White, M., & Salovey, P. (2012). Classroom emotional climate, student engagement, and academic achievement. Journal of Educational Psychology, 104 (3), 700–712. https://doi.org/10.1037/a0027268 .
Richardson, J., & Lenarcic, J. (2008). Text Messaging as a Catalyst for Mobile Student Administration: The “Trigger” Experience. International Journal of Emerging Technologies & Society, 6 (2), 140–155.
Roblyer, M. D., McDaniel, M., Webb, M., Herman, J., & Witty, J. V. (2010). Findings on Facebook in higher education: A comparison of college faculty and student uses and perceptions of social networking sites. The Internet and Higher Education, 13 (3), 134–140.
Rock, M. L., & Thead, B. K. (2007). The effects of fading a strategic self-monitoring intervention on students’ academic engagement, accuracy, and productivity. Journal of Behavioral Education, 16 (4), 389–412. https://doi.org/10.1007/s10864-007-9049-7 .
Rodriguez, J. E. (2011). Social media use in higher education : Key areas to consider for educators. MERLOT Journal of Online Learning and Teaching, 7 (4), 539–550 https://doi.org/ISSN1558-9528 .
Rutherford, C. (2010). Using online social media to support Preservice student engagement. MERLOT Journal of Online Learning and Teaching, 6 (4), 703–711 Retrieved from http://jolt.merlot.org/vol6no4/rutherford_1210.pdf .
Schumacker, R. E., & Lomax, R. G. (2010). A Beginner’s Guide to structural equation modeling (3rd ed.). New York: Taylor & Francis Group.
Selwyn, N. (2012). Making sense of young people, education and digital technology: The role of sociological theory. Oxford Review of Education, 38 (1), 81–96.
Shih, Y. E. (2007). Setting the new standard with mobile computing in online learning. The International Review of Research in Open and Distributed Learning, 8 (2), 1–16.
Skinner, E. A., & Belmont, M. J. (1993). Motivation in the classroom: Reciprocal effects of teacher behavior and student engagement across the school year. Journal of educational psychology, 85 (4), 571.
Tabachnick, B. G., Fidell, L. S., & Ullman, J. B. (2007). Using multivariate statistics (Vol. 5). Boston: Pearson.
Voorn, R. J., & Kommers, P. A. (2013). Social media and higher education: Introversion and collaborative learning from the student’s perspective. International Journal of Social Media and Interactive Learning Environments, 1 (1), 59–73.
Wankel, C. (2009). Management education using social media. Organization Management Journal, 6 (4), 251–262.
Williams, M. D., Rana, N. P., & Dwivedi, Y. K. (2015). The unified theory of acceptance and use of technology (UTAUT): a literature review. Journal of Enterprise Information Management, 28 (3), 443–488.
Zhu, C. (2012). Student satisfaction, performance, and knowledge construction in online collaborative learning. Journal of Educational Technology & Society, 15 (1), 127–136.
Download references
Acknowledgements
We want to express our special gratitude to the Almighty who has blessed us with such hidden talent to give the shape of this research paper.
The authors of this manuscript, solemnly declared that no funding agency was supported to execute this research project.
Author information
Authors and affiliations.
Department of Commerce, Aligarh Muslim University, Aligarh, 202002, India
Jamal Abdul Nasir Ansari & Nawab Ali Khan
You can also search for this author in PubMed Google Scholar
Contributions
Jamal Abdul Nasir Ansari: The first author of this manuscript has performed all sorts of necessary works like the collection of data from respondents, administration of the questionnaire. Collection of information from the respondents was quite challenging. The author faced a lot of difficulties while collecting data. The main contribution of the author in this manuscript is that the entire work, like data analysis and its interpretation performed by him. Additionally, the author has tried to explore and usefulness of social media and its applicability in transferring the course contents. Nawab Ali Khan: The second author of this manuscript has checked all types of grammatical issues, and necessary corrections wherever required. The author(s) read and approved the final manuscript.
Corresponding author
Correspondence to Jamal Abdul Nasir Ansari .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests.
Additional information
Publisher’s note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License ( http://creativecommons.org/licenses/by/4.0/ ), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
Reprints and permissions
About this article
Cite this article.
Ansari, J.A.N., Khan, N.A. Exploring the role of social media in collaborative learning the new domain of learning. Smart Learn. Environ. 7 , 9 (2020). https://doi.org/10.1186/s40561-020-00118-7
Download citation
Received : 27 November 2019
Accepted : 18 February 2020
Published : 16 March 2020
DOI : https://doi.org/10.1186/s40561-020-00118-7
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Social media
- Higher education
- Faculty members

Best Social Media Research Topics | Inspiration & Ideas

Introduction
What distinguishes social media from other communication, why research social media, what can i research about social media, conducting research on social media.
Social media has become an integral part of modern communication, influencing how people connect, share information, and interact with the world. As a rapidly evolving field, it presents a wealth of opportunities for research that can offer valuable insights into societal trends, behavioral patterns, and technological advancements. This article aims to provide inspiration and ideas for selecting compelling social media research topics. We’ll explore what makes social media unique, the importance of studying it, and offer suggestions for areas you can investigate.

Social media is a unique form of communication that differs significantly from traditional methods such as face-to-face interactions, phone calls, or even emails. Several key characteristics set social media apart, making it a fascinating area for research.
Interactivity and user-generated content
One of the most distinctive features of social media is its interactivity. Unlike traditional media, where communication is typically one-way, social media platforms enable two-way interactions between users. This interactivity allows users to not only consume content but also to create and share their own, leading to an environment rich in user-generated content. This aspect of social media fosters a participatory culture where individuals can contribute to discussions, share their perspectives, and engage with others in real-time.
Networked communication
Social media operates on a networked model of communication, where information is shared across a web of interconnected users. This networked nature allows content to spread rapidly through shares, likes, comments, and other forms of engagement. The viral potential of social media content is a key characteristic that distinguishes it from other forms of communication, where information dissemination is often more controlled and linear.

Personalization and algorithms
Another defining feature of social media is the use of algorithms to personalize user experiences. These algorithms analyze user behavior, preferences, and interactions to curate content that is most relevant to each individual. This level of personalization is unmatched by traditional communication methods and has profound implications for how people receive information, form opinions, and engage with the world around them. The algorithm-driven nature of social media also raises important questions about echo chambers, filter bubbles, and the impact of personalized content on societal discourse.
Multimedia integration
Social media platforms seamlessly integrate various forms of multimedia, including text, images, videos , and live streams. This multimedia approach enhances the richness of social media communication and allows users to express themselves in diverse and creative ways. The ability to combine different media types in a single platform sets social media apart from other communication methods, which may be more limited in their use of media.

Global reach and immediacy
Finally, a solid social media presence offers unprecedented global reach and immediacy. With social media exposure, users can connect with others across the world instantly, breaking down geographical barriers and enabling cross-cultural communication. The real-time nature of social media allows for immediate responses and updates, making it a powerful tool for sharing news, organizing events, and mobilizing movements for marketing endeavors, political campaigns, and other collective efforts.

Researching social media is crucial because of its pervasive influence on various aspects of society, including communication, culture, politics, and even mental health. As social media continues to evolve and integrate into everyday life, understanding its impact becomes increasingly important for several reasons.
First, social media shapes public opinion and discourse in ways that traditional media cannot. The speed at which information spreads on platforms like Twitter/X, Facebook, and Instagram can amplify voices and ideas, often creating significant cultural or political movements. Studying these phenomena can reveal insights into how public opinion is formed, how misinformation spreads, and how social movements gain traction.
Second, social media platforms collect vast amounts of data about user behavior, preferences, and interactions. This data offers a unique opportunity for researchers to analyze trends, understand user engagement, and explore the effects of algorithmic content curation. By examining these aspects, researchers can shed light on how social media influences decision-making, consumer behavior, and even voting patterns.
Moreover, social media has a profound impact on mental health and well-being. The constant connectivity and exposure to curated lives can lead to issues such as anxiety, depression, and feelings of inadequacy. Research in this area can help identify the factors contributing to these mental health challenges and guide the development of interventions or policies to mitigate them.
Finally, as social media becomes a key tool for marketing, education, and even governance, understanding its mechanisms and effects is vital for professionals across various fields. Whether it’s to improve social media marketing strategies, enhance educational outreach, or design more effective public policies, social media research papers provide valuable insights that can inform practice and policy.
Make the most of your data with ATLAS.ti
For the most powerful data analysis, turn to ATLAS.ti. Get started with a free trial.
Choosing a social media research topic can be a difficult decision among numerous research opportunities across various disciplines. Here are three key areas to consider when selecting a research topic related to social media: societal impact, psychological effects, and technological advancements.
Societal impact of social media
One of the most significant aspects of social media is its profound impact on society. Researching this area can provide valuable insights into how social media influences cultural norms, political movements, and social behavior.
- Social media and political movements : Social media platforms have played a crucial role in organizing and mobilizing political movements around the world. From the Arab Spring to the Black Lives Matter movement, these platforms have facilitated the rapid spread of information and coordination among activists. Researching the role of social media in political movements can reveal how these platforms influence public opinion, empower grassroots movements, and even shape election outcomes. Additionally, you can explore the potential downsides, such as the spread of misinformation or the role of bots and fake accounts in manipulating political discourse.
- Cultural diversity and social media : Social media platforms are global in reach, connecting people from different cultures and backgrounds. This connectivity can promote cultural diversity by exposing users to new ideas, traditions, and perspectives. However, it can also lead to cultural homogenization, where dominant cultures overshadow minority voices. Researching the impact of social media on cultural diversity can explore how these platforms either promote or hinder cultural exchange and the preservation of cultural identities. You might also investigate the role of social media in fostering cross-cultural understanding or exacerbating cultural tensions.
- Social media and public health campaigns : Social media has become a vital tool for public health communication, particularly during global crises like the COVID-19 pandemic. Platforms like Twitter/X and Facebook have been used to disseminate important health information, raise awareness about preventive measures, and combat misinformation. Researching the effectiveness of social media in public health campaigns can provide insights into how these platforms can be used to promote healthy behaviors, increase vaccination rates, and improve public health outcomes. Additionally, you can examine the challenges of combating health misinformation and the social media strategies that have been successful in addressing it.

Psychological effects of social media
In studying social media, psychology has many potential theoretical and practical research questions . Understanding how these platforms influence mental health, self-esteem, and social interactions is crucial for developing strategies to mitigate negative impacts and enhance positive outcomes.
- Social media and mental health : One of the most extensively studied areas is the relationship between social media use and mental health. Research has shown that excessive use of social media can lead to negative outcomes such as anxiety, depression, and loneliness. However, these effects can vary depending on factors like age, personality, and the type of content consumed. Researching the impact of social media on mental health can involve exploring the specific mechanisms through which social media affects well-being, such as comparison with others, cyberbullying, or the pressure to present a perfect image online. You might also investigate the potential benefits of social media, such as providing support networks for individuals with mental health challenges.
- The role of social media in shaping self-identity : Social media platforms provide users with the tools to curate and present their identities online. This process of identity construction can have both positive and negative effects. On the one hand, social media can empower individuals to express themselves and connect with like-minded communities. On the other hand, the pressure to conform to societal standards and the constant exposure to idealized images can lead to issues like low self-esteem and body image concerns. Researching the role of social media in shaping self-identity can involve examining how different groups (e.g., teenagers, adults, marginalized communities) use social media to explore and express their identities. Additionally, you can study the impact of social media on self-perception and the ways in which online interactions influence offline behaviors and attitudes.
- Social media addiction : As social media becomes increasingly integrated into daily life, the phenomenon of social media addiction has garnered significant attention. Social media addiction is characterized by excessive use of social media platforms, leading to negative consequences in an individual's personal, academic, or professional life. Researching social media addiction can involve exploring the factors that contribute to addictive behaviors, such as the design of social media platforms, individual personality traits, and social influences. Additionally, you can investigate the impact of social media addiction on mental health, relationships, and productivity, as well as potential interventions to address this issue.

Technological advancements and social media
Technological advancements play a pivotal role in shaping the evolution of social media platforms. Understanding these advancements and their implications can offer valuable insights into the future of social media and its impact on society.
- Artificial intelligence and social media algorithms : Artificial intelligence (AI) is increasingly being used to power the algorithms that drive content curation on social media platforms. These algorithms analyze user behavior, preferences, and interactions to deliver personalized content, ads, and recommendations. While AI can enhance user experience by providing relevant content, it also raises concerns about privacy, echo chambers, and the manipulation of information. Researching the role of AI in social media can involve exploring how these algorithms work, their impact on user behavior, and the ethical implications of AI-driven content curation. Additionally, you can study the potential of AI to combat issues like misinformation, hate speech, and online harassment.
- The evolution of social media platforms : Social media platforms are constantly evolving, with new features, tools, and platforms emerging regularly. Understanding the technological trends driving these changes can provide insights into the future of social media. Researching the evolution of social media platforms can involve examining how new technologies, such as augmented reality (AR), virtual reality (VR), and live streaming, are being integrated into social media. You can also explore the impact of these technologies on user engagement, content creation, and social interactions. Additionally, consider investigating the rise of niche social media platforms and how they cater to specific communities or interests.
- Data privacy and security on social media : As social media platforms collect vast amounts of user data, concerns about data privacy and security have become increasingly prominent. Researching data privacy on social media can involve exploring the ways in which platforms collect, store, and use user data, as well as the potential risks associated with data breaches and unauthorized access. Additionally, you can examine the impact of data privacy regulations, such as the General Data Protection Regulation (GDPR), on social media platforms and their practices. Studying user perceptions of data privacy and their behaviors in response to privacy concerns can also provide valuable insights into how social media platforms can build trust with their users.

Conducting research on social media requires careful consideration of the methodologies employed, the ethical implications involved, and the approaches to data analysis. Each of these factors plays a crucial role in ensuring that the research is both rigorous and responsible.
Choosing appropriate methodologies
Selecting the appropriate research methodology is a foundational step in addressing social media research questions . The choice of methodology largely depends on the research questions and objectives. Qualitative methods, such as in-depth interviews , focus groups , and content analysis , offer valuable insights into the subjective experiences and perceptions of social media users.
For example, interviews can reveal how individuals construct and present their identities online, while content analysis allows researchers to explore patterns and themes within social media interactions, such as how users discuss specific topics or respond to particular events.
On the other hand, quantitative methods, like surveys and experiments, are essential for gathering data that can be measured and analyzed statistically. Surveys can provide a broad overview of user behaviors and attitudes across large populations, enabling researchers to identify trends and correlations. Experiments, meanwhile, are useful for testing specific hypotheses, such as the impact of social media use on academic performance or mental health.
In some cases, combining qualitative and quantitative methods in a mixed-methods approach can offer a more comprehensive understanding of the phenomena being studied, allowing researchers to explore both the depth and breadth of social media interactions.

Accounting for ethical issues
Ethical considerations are paramount in social media research, given the sensitive nature of the data often involved. One of the primary ethical challenges is obtaining informed consent from participants , especially in environments where users may not be fully aware that their posts or interactions are being analyzed.
Researchers must navigate this challenge by ensuring that their methods of obtaining consent are clear and transparent, particularly when dealing with content that users might consider private, despite being posted on public platforms.
Protecting the privacy and confidentiality of participants is another critical concern. This involves anonymizing data to prevent the identification of individuals and securing the data to protect it from unauthorized access. Researchers must also be sensitive to the potential risks associated with their studies, particularly when dealing with vulnerable populations or sensitive topics such as mental health or political beliefs.
Transparency in the research process is essential; researchers should openly communicate their intentions, methods, and any potential conflicts of interest, ensuring that participants understand how their data will be used. Engaging with the communities involved in the research can also help to mitigate ethical concerns, as it fosters trust and collaboration, making the research process more inclusive and respectful of participants' rights and perspectives.
Conducting data analysis
The analysis of social media data presents its own set of challenges, given the vast amount of information that can be generated on these platforms. Effective data analysis requires not only technical proficiency but also a deep understanding of the social context in which the data is produced.
Data cleaning and preparation are crucial initial steps, as social media data often contains noise and irrelevant information that can skew results. Researchers must carefully filter and organize their data to ensure that the analysis is accurate and meaningful. Once the data is prepared, researchers can apply various analytical techniques, depending on the research objectives.
For qualitative data , thematic analysis can be used to identify recurring themes and patterns within the content, providing insights into user behaviors and perceptions. Quantitative data , on the other hand, may require statistical analysis to uncover correlations, trends, or causal relationships.
Throughout the analysis process, it is important for researchers to remain mindful of the limitations of their data and the potential biases that may influence their findings. This includes being aware of the algorithms that social media platforms use to curate content, which can impact the data collected and the conclusions drawn from it.

Collect, organize, and analyze data with ATLAS.ti
Turn qualitative data into insights with our intuitive and powerful platform. Download a free trial today.


IMAGES
VIDEO
COMMENTS
Social networking is a global phenomenon that. has revolution ized how people interact with each other. It. affects nearly every aspect of our life: education, communication, employment, politics ...
Literature Review. Putnam (1995, p. 664-665) defined social capital as "features of social life - networks, norms, and trust - that enable participants to act together more effectively to pursue shared objectives."Li and Chen (2014, p. 117) further explained that social capital encompasses "resources embedded in one's social network, which can be assessed and used for instrumental ...
Depression, anxiety, catfishing, bullying, terro rism, and. criminal activities are some of the negative side s of social media on societies. Generall y, when peoples use social. media for ...
Abstract. Social media are responsible for aggravating mental health problems. This systematic study summarizes the effects of social network usage on mental health. Fifty papers were shortlisted from google scholar databases, and after the application of various inclusion and exclusion criteria, 16 papers were chosen and all papers were ...
Introduction. The term "social media" (SM) was first used in 1994 on a Tokyo online media environment, called Matisse. 1 It was in these early days of the commercial Internet that the first SM platforms were developed and launched. Over time, both the number of SM platforms and the number of active SM users have increased significantly, making it one of the most important applications of ...
With the dawn of social network sites, this issue is more important than ever. A close examination of the extensive body of research on social network sites suggests that conflicting results can be reconciled by a single theoretical approach: the interpersonal-connection-behaviors framework. Specifically, we suggest that social network sites ...
Social media has been defined as web-based communication platforms with three distinct features, in which the platform 1) allows users to create unique profiles and content to share with other users, 2) creates a visible network connection between users that can be navigated by other users, and 3) provides users with a space to broadcast ...
Introduction. The use of social media has grown substantially in recent years (Leong et al., 2019; Kemp, 2020).Social media refers to "the websites and online tools that facilitate interactions between users by providing them opportunities to share information, opinions, and interest" (Swar and Hameed, 2017, p. 141).Individuals use social media for many reasons, including entertainment ...
This entry explores the ways in which social media influences social life, including its impact on individual identity, culture, the economy, and politics, and examines systematic methods for studyin...
Social media. The term 'social media' refers to the various internet-based networks that enable users to interact with others, verbally and visually (Carr & Hayes, Citation 2015).According to the Pew Research Centre (Citation 2015), at least 92% of teenagers are active on social media.Lenhart, Smith, Anderson, Duggan, and Perrin (Citation 2015) identified the 13-17 age group as ...
Introduction. The past years have witnessed a staggering increase in empirical studies into the effects of social media use (SMU) on adolescents' mental health (e.g. [1∗∗, 2∗, 3]), defined as the absence of mental illness and the presence of well-being [4].This rapid increase may be due to at least two reasons.
Social media comprises communication websites that facilitate relationship forming between users from diverse backgrounds, resulting in a rich social structure. User generated content encourages inquiry and decision-making. Given the relevance of social media to various stakeholders, it has received significant attention from researchers of various fields, including information systems. There ...
Congruent with the growth of social media use, there are also increasing worries that social media might lead to social anxiety in users (Jelenchick et al., 2013).Social anxiety is one's state of avoiding social interactions and appearing inhibited in such interactions with other people (Schlenker & Leary, 1982).Scholars indicated that social anxiety could arise from managing a large network ...
The purpose of this study is to understand the role of social media content on users' engagement behavior. More specifically, we investigate: (i)the direct effects of format and platform on users' passive and active engagement behavior, and (ii) we assess the moderating effect of content context on the link between each content type (rational, emotional, and transactional content) and ...
negative emotions seem to indicate that addictive behaviors are on the rise and are closely related. to overuse of social media. On the other side of the coin, social media use also produces positive effects on. emotional well-being such as happiness, Mudita, humor, support, validation, and a more frequent.
Introduction. Social media has become a prominent fixture in the lives of many individuals facing the challenges of mental illness. Social media refers broadly to web and mobile platforms that allow individuals to connect with others within a virtual network (such as Facebook, Twitter, Instagram, Snapchat, or LinkedIn), where they can share, co-create, or exchange various forms of digital ...
Previous studies regarding social interactions commonly adopt research methods that investigate causal relationships between variables. The existing approaches often utilize variables derived from general contexts, aiming to apply them universally across diverse situations. However, social interactions, including the usage of social media, are intricately woven within the immediate social context.
Social media use confers many benefits by providing access to a wide range of information sources, which facilitate learning (Greenhow and Robelia, 2009). However, instead of using social networking sites for academic purposes, students tend to be actively involved in online shopping, gaming, and entertainment during the day and at night.
Social network analysis (SNA) is a theoretical framework that conceptualizes the structure of social networks by focusing on the characteristics of the ties connecting members rather than the characteristics of the individual (Otte & Rousseau, Citation 2002). SNA uses mathematical models to determine the structural relationships between nodes ...
1 Science and Technology Department, Nanjing University of Posts and Telecommunications, Nanjing, China; 2 School of Marxism, Hohai University, Nanjing, Jiangsu, China; 3 Government Enterprise Customer Center, China Mobile Group Jiangsu Co., Ltd., Nanjing, China; The use of social media is incomparably on the rise among students, influenced by the globalized forms of communication and the post ...
A Study on Positive and Negative Effects of Socia l Media on Society. W.Akram 1*, R.Kumar2. 1* Department of Computer Applications, GDC Mendhar, Poonch, India. 2 Department of Computer ...
Kaplan and Haenlein (2010) defined social media as "… a group of Internet-based applications that build on the ideological and technological foundations of Web 2.0, and that allow the creation and exchange of User Generated Content" (p. 61). The emergence of social media technologies has been embraced by a growing number of users who post text messages, pictures, and videos online ...
Some of them are positive, such as the improvement of important communication skills, making students more sociable online. In addition, social networking extends students' knowledge and helps them to be active in creating and sharing information. Nevertheless, social networks have been found to have negative effects, such as the lowering of ...
This study is an attempt to examine the application and usefulness of social media and mobile devices in transferring the resources and interaction with academicians in higher education institutions across the boundary wall, a hitherto unexplained area of research. This empirical study is based on the survey of 360 students of a university in eastern India, cognising students' perception on ...
Introduction. Social media has become an integral part of modern communication, influencing how people connect, share information, and interact with the world. As a rapidly evolving field, it presents a wealth of opportunities for research that can offer valuable insights into societal trends, behavioral patterns, and technological advancements.
Beatriz Jordá is a PhD candidate in the Department of Communication at Carlos III University of Madrid and an adjunct professor in the Department of English at Saint Louis University, Madrid campus. She has also been a visiting scholar at University of Gothenburg. Her research focuses on the study of persuasion in the context of politics and social media.
The lock-up period prohibiting Trump from selling or even borrowing against his $2.3 billion stake in Truth Social owner Trump Media & Technology Group is scheduled to expire by September 25 ...