- Business Essentials
- Leadership & Management
- Credential of Leadership, Impact, and Management in Business (CLIMB)
- Entrepreneurship & Innovation
- Digital Transformation
- Finance & Accounting
- Business in Society
- For Organizations
- Support Portal
- Media Coverage
- Founding Donors
- Leadership Team

- Harvard Business School →
- HBS Online →
- Business Insights →

Business Insights
Harvard Business School Online's Business Insights Blog provides the career insights you need to achieve your goals and gain confidence in your business skills.
- Career Development
- Communication
- Decision-Making
- Earning Your MBA
- Negotiation
- News & Events
- Productivity
- Staff Spotlight
- Student Profiles
- Work-Life Balance
- AI Essentials for Business
- Alternative Investments
- Business Analytics
- Business Strategy
- Business and Climate Change
- Creating Brand Value
- Design Thinking and Innovation
- Digital Marketing Strategy
- Disruptive Strategy
- Economics for Managers
- Entrepreneurship Essentials
- Financial Accounting
- Global Business
- Launching Tech Ventures
- Leadership Principles
- Leadership, Ethics, and Corporate Accountability
- Leading Change and Organizational Renewal
- Leading with Finance
- Management Essentials
- Negotiation Mastery
- Organizational Leadership
- Power and Influence for Positive Impact
- Strategy Execution
- Sustainable Business Strategy
- Sustainable Investing
- Winning with Digital Platforms
What Is Risk Management & Why Is It Important?

- 24 Oct 2023
Businesses can’t operate without risk. Economic, technological, environmental, and competitive factors introduce obstacles that companies must not only manage but overcome.
According to PwC’s Global Risk Survey , organizations that embrace strategic risk management are five times more likely to deliver stakeholder confidence and better business outcomes and two times more likely to expect faster revenue growth.
If you want to enhance your job performance and identify and mitigate risk more effectively, here’s a breakdown of what risk management is and why it’s important.
Access your free e-book today.
What Is Risk Management?
Risk management is the systematic process of identifying, assessing, and mitigating threats or uncertainties that can affect your organization. It involves analyzing risks’ likelihood and impact, developing strategies to minimize harm, and monitoring measures’ effectiveness.
“Competing successfully in any industry involves some level of risk,” says Harvard Business School Professor Robert Simons, who teaches the online course Strategy Execution . “But high-performing businesses with high-pressure cultures are especially vulnerable. As a manager, you need to know how and why these risks arise and how to avoid them.”
According to Strategy Execution , strategic risk has three main causes:
- Pressures due to growth: This is often caused by an accelerated rate of expansion that makes staffing or industry knowledge gaps more harmful to your business.
- Pressures due to culture: While entrepreneurial risk-taking can come with rewards, executive resistance and internal competition can cause problems.
- Pressures due to information management: Since information is key to effective leadership , gaps in performance measures can result in decentralized decision-making.
These pressures can lead to several types of risk that you must manage or mitigate to avoid reputational, financial, or strategic failures. However, risks aren’t always obvious.
“I think one of the challenges firms face is the ability to properly identify their risks,” says HBS Professor Eugene Soltes in Strategy Execution .
Therefore, it’s crucial to pinpoint unexpected events or conditions that could significantly impede your organization’s business strategy .
Related: Business Strategy vs. Strategy Execution: Which Course Is Right for Me?
According to Strategy Execution , strategic risk comprises:
- Operations risk: This occurs when internal operational errors interrupt your products or services’ flow. For example, shipping tainted products can negatively affect food distribution companies.
- Asset impairment risk: When your company’s assets lose a significant portion of their current value because of a decreased likelihood of receiving future cash flows . For instance, losing property assets, like a manufacturing plant, due to a natural disaster.
- Competitive risk: Changes in the competitive environment can interrupt your organization’s ability to create value and differentiate its offerings—eventually leading to a significant loss in revenue.
- Franchise risk: When your organization’s value erodes because stakeholders lose confidence in its objectives. This primarily results from failing to control any of the strategic risk sources listed above.
Understanding these risks is essential to ensuring your organization’s long-term success. Here’s a deeper dive into why risk management is important.
4 Reasons Why Risk Management Is Important
1. protects organization’s reputation.
In many cases, effective risk management proactively protects your organization from incidents that can affect its reputation.
“Franchise risk is a concern for all businesses,“ Simons says in Strategy Execution . “However, it's especially pressing for businesses whose reputations depend on the trust of key constituents.”
For example, airlines are particularly susceptible to franchise risk because of unforeseen events, such as flight delays and cancellations caused by weather or mechanical failure. While such incidents are considered operational risks, they can be incredibly damaging.
In 2016, Delta Airlines experienced a national computer outage, resulting in over 2,000 flight cancellations. Delta not only lost an estimated $150 million but took a hit to its reputation as a reliable airline that prided itself on “canceling cancellations.”
While Delta bounced back, the incident illustrates how mitigating operational errors can make or break your organization.
2. Minimizes Losses
Most businesses create risk management teams to avoid major financial losses. Yet, various risks can still impact their bottom lines.
A Vault Platform study found that dealing with workplace misconduct cost U.S. businesses over $20 billion in 2021. In addition, Soltes says in Strategy Execution that corporate fines for misconduct have risen 40-fold in the U.S. over the last 20 years.
One way to mitigate financial losses related to employee misconduct is by implementing internal controls. According to Strategy Execution , internal controls are the policies and procedures designed to ensure reliable accounting information and safeguard company assets.
“Managers use internal controls to limit the opportunities employees have to expose the business to risk,” Simons says in the course.
One company that could have benefited from implementing internal controls is Volkswagen (VW). In 2015, VW whistle-blowers revealed that the company’s engineers deliberately manipulated diesel vehicles’ emissions data to make them appear more environmentally friendly.
This led to severe consequences, including regulatory penalties, expensive vehicle recalls, and legal settlements—all of which resulted in significant financial losses. By 2018, U.S. authorities had extracted $25 billion in fines, penalties, civil damages, and restitution from the company.
Had VW maintained more rigorous internal controls to ensure transparency, compliance, and proper oversight of its engineering practices, perhaps it could have detected—or even averted—the situation.
Related: What Are Business Ethics & Why Are They Important?
3. Encourages Innovation and Growth
Risk management isn’t just about avoiding negative outcomes. It can also be the catalyst that drives your organization’s innovation and growth.
“Risks may not be pleasant to think about, but they’re inevitable if you want to push your business to innovate and remain competitive,” Simons says in Strategy Execution .
According to PwC , 83 percent of companies’ business strategies focus on growth, despite risks and mixed economic signals. In Strategy Execution , Simons notes that competitive risk is a challenge you must constantly monitor and address.
“Any firm operating in a competitive market must focus its attention on changes in the external environment that could impair its ability to create value for its customers,” Simons says.
This requires incorporating boundary systems —explicit statements that define and communicate risks to avoid—to ensure internal controls don’t extinguish innovation.
“Boundary systems are essential levers in businesses to give people freedom,” Simons says. “In such circumstances, you don’t want to stifle innovation or entrepreneurial behavior by telling people how to do their jobs. And if you want to remain competitive, you’ll need to innovate and adapt.”

Netflix is an example of how risk management can inspire innovation. In the early 2000s, the company was primarily known for its DVD-by-mail rental service. With growing competition from video rental stores, Netflix went against the grain and introduced its streaming service. This changed the market, resulting in a booming industry nearly a decade later.
Netflix’s innovation didn’t stop there. Once the steaming services market became highly competitive, the company shifted once again to gain a competitive edge. It ventured into producing original content, which ultimately helped differentiate its platform and attract additional subscribers.
By offering more freedom within internal controls, you can encourage innovation and constant growth.
4. Enhances Decision-Making
Risk management also provides a structured framework for decision-making. This can be beneficial if your business is inclined toward risks that are difficult to manage.
By pulling data from existing control systems to develop hypothetical scenarios, you can discuss and debate strategies’ efficacy before executing them.
“Interactive control systems are the formal information systems managers use to personally involve themselves in the decision activities of subordinates,” Simons says in Strategy Execution . “Decision activities that relate to and impact strategic uncertainties.”
JPMorgan Chase, one of the most prominent financial institutions in the world, is particularly susceptible to cyber risks because it compiles vast amounts of sensitive customer data . According to PwC , cybersecurity is the number one business risk on managers’ minds, with 78 percent worried about more frequent or broader cyber attacks.
Using data science techniques like machine learning algorithms enables JPMorgan Chase’s leadership not only to detect and prevent cyber attacks but address and mitigate risk.

Start Managing Your Organization's Risk
Risk management is essential to business. While some risk is inevitable, your ability to identify and mitigate it can benefit your organization.
But you can’t plan for everything. According to the Harvard Business Review , some risks are so remote that no one could have imagined them. Some result from a perfect storm of incidents, while others materialize rapidly and on enormous scales.
By taking an online strategy course , you can build the knowledge and skills to identify strategic risks and ensure they don’t undermine your business. For example, through an interactive learning experience, Strategy Execution enables you to draw insights from real-world business examples and better understand how to approach risk management.
Do you want to mitigate your organization’s risks? Explore Strategy Execution —one of our online strategy courses —and download our free strategy e-book to gain the insights to build a successful strategy.

About the Author
- SUGGESTED TOPICS
- The Magazine
- Newsletters
- Managing Yourself
- Managing Teams
- Work-life Balance
- The Big Idea
- Data & Visuals
- Reading Lists
- Case Selections
- HBR Learning
- Topic Feeds
- Account Settings
- Email Preferences
Managing Risks: A New Framework
- Robert S. Kaplan
- Anette Mikes

Risk management is too often treated as a compliance issue that can be solved by drawing up lots of rules and making sure that all employees follow them. Many such rules, of course, are sensible and do reduce some risks that could severely damage a company. But rules-based risk management will not diminish either the likelihood or the impact of a disaster such as Deepwater Horizon, just as it did not prevent the failure of many financial institutions during the 2007–2008 credit crisis.
In this article, Robert S. Kaplan and Anette Mikes present a categorization of risk that allows executives to understand the qualitative distinctions between the types of risks that organizations face. Preventable risks, arising from within the organization, are controllable and ought to be eliminated or avoided. Examples are the risks from employees’ and managers’ unauthorized, unethical, or inappropriate actions and the risks from breakdowns in routine operational processes. Strategy risks are those a company voluntarily assumes in order to generate superior returns from its strategy. External risks arise from events outside the company and are beyond its influence or control. Sources of these risks include natural and political disasters and major macroeconomic shifts. Risk events from any category can be fatal to a company’s strategy and even to its survival.
Companies should tailor their risk management processes to these different risk categories. A rules-based approach is effective for managing preventable risks, whereas strategy risks require a fundamentally different approach based on open and explicit risk discussions. To anticipate and mitigate the impact of major external risks, companies can call on tools such as war-gaming and scenario analysis.
Smart companies match their approach to the nature of the threats they face.
Editors’ note: Since this issue of HBR went to press, JP Morgan, whose risk management practices are highlighted in this article, revealed significant trading losses at one of its units. The authors provide their commentary on this turn of events in their contribution to HBR’s Insight Center on Managing Risky Behavior.
- Robert S. Kaplan is a senior fellow and the Marvin Bower Professor of Leadership Development emeritus at Harvard Business School. He coauthored the McKinsey Award–winning HBR article “ Accounting for Climate Change ” (November–December 2021).
- Anette Mikes is a fellow at Hertford College, Oxford University, and an associate professor at Oxford’s Saïd Business School.
Partner Center

- Predict! Software Suite
- Training and Coaching
- Predict! Risk Controller
- Rapid Deployment
- Predict! Risk Analyser
- Predict! Risk Reporter
- Predict! Risk Visualiser
- Predict! Cloud Hosting
- BOOK A DEMO
- Risk Vision
- Win Proposals with Risk Analysis
- Case Studies
- Video Gallery
- White Papers
- Upcoming Events
- Past Events

Fehmarnbelt case study
. . . . . learn more

Lend Lease case study

ASC case study

Tornado IPT case study

LLW Repository case study

OHL case study

Babcock case study

HUMS case study

UK Chinook case study

- EMEA: +44 (0) 1865 987 466
- Americas: +1 (0) 437 269 0697
- APAC: +61 499 520 456

Subscribe for Updates
Copyright © 2024 risk decisions. All rights reserved.
- Privacy Policy
- Cookie Policy
- Terms and Conditions
- Company Registration No: 01878114
Powered by The Communications Group

- Project Management
- Quality Management
- Human Resources
- Procurement & Supply Chain
- About Red Learning
- Student testimonials
- Corporate Training
- Payment link

Risk Management in Action: Case Studies for Project Managers
- Posted by Red Learning
- Categories Project Management
- Date April 20, 2024
- Comments 0 comment
The theoretical aspects of risk management are crucial, but seeing them applied in real-world scenarios brings the concepts to life. Here are two case studies that showcase how Project Managers identified, assessed, and mitigated risks to achieve project success:
Case Study 1: Launching a New Software Product
Project: Developing and launching a new web-based project management software application.
Identified Risks:
- Technical Issues: Potential delays due to software bugs or integration challenges with third-party applications.
- Market Adoption: The target market might not be receptive to a new project management solution.
- Scope Creep: New feature requests during development could lead to project delays and budget overruns.
Risk Mitigation Strategies:
- Thorough Testing: Implemented a rigorous testing process to identify and fix bugs before launch.
- Market Research: Conducted extensive market research to understand customer needs and preferences.
- Change Management Process: Established a clear change management process to evaluate and prioritize new feature requests, mitigating scope creep.
Outcome: The project was completed on time and within budget. The software was well-received by the target market, achieving successful market adoption.
Key Learnings:
- Proactive identification of potential risks is essential.
- Implementing a mitigation plan can significantly improve project outcomes.
- Adaptability and continuous risk monitoring are crucial throughout the project lifecycle.
Case Study 2: Building a New Manufacturing Facility
Project: Construction of a new manufacturing facility for a consumer goods company.
- Labor Shortages: Difficulty finding qualified workers to complete the construction project on schedule.
- Material Price Fluctuations: Rising costs of raw materials could impact the project budget.
- Unforeseen Weather Events: Adverse weather conditions could cause delays and disrupt the construction schedule.
- Strategic Workforce Planning: Partnered with recruitment agencies and offered competitive wages to attract and retain skilled workers.
- Contract Negotiation: Negotiated fixed-price contracts with material suppliers to minimize the impact of price fluctuations.
- Contingency Plans: Developed contingency plans to address potential weather disruptions, including alternative work schedules and materials sourcing.
Outcome: The manufacturing facility was constructed on schedule and within budget despite encountering some labor shortages and minor weather delays. The contingency plans proved effective in mitigating these challenges.
- A diverse set of risks can arise in construction projects.
- Having mitigation plans in place for various risk categories is crucial.
- Effective communication and collaboration with stakeholders (contractors, suppliers) are essential for successful risk management .
These case studies highlight the importance of risk management in project success. By proactively identifying potential risks, developing mitigation plans, and continuously monitoring the project environment, project managers can navigate challenges, ensure project delivery, and achieve their goals.

Previous post
Delegation Strategies for Increased Project Efficiency
Building a culture of innovation in your project teams, you may also like, pmp certification: your path to project management mastery with red learning.
Understanding the PMP Certification The Project Management Professional (PMP)® certification is globally recognized as the gold standard in project management. Administered by the Project Management Institute (PMI), the PMP credential validates a project manager’s experience, education, and competency across a …
The Future of Work: How PMI CPs Can Stay Relevant in the Evolving Industry Landscape
The construction industry is undergoing a rapid metamorphosis. Technological advancements, sustainability concerns, and evolving client demands are reshaping how projects are planned, executed, and delivered. To navigate this dynamic landscape and remain relevant, PMI Certified Professionals (PMPs) must embrace continuous …
Construction Project Management in a Remote and Hybrid Work Environment
The construction industry is undergoing a metamorphosis, transitioning from a traditionally hands-on approach to a world of remote and hybrid work models. This shift presents both challenges and opportunities for Project Management Institute (PMI) Certified Professionals (PMPs). Here’s a comprehensive …
- Procurement & Supply Chain
- Accreditations
- Student Complaint Procedure
- Terms and Conditions
- Cancellation Policy
- Privacy Policy
- Payment Link
Information
- Author Services
Initiatives
You are accessing a machine-readable page. In order to be human-readable, please install an RSS reader.
All articles published by MDPI are made immediately available worldwide under an open access license. No special permission is required to reuse all or part of the article published by MDPI, including figures and tables. For articles published under an open access Creative Common CC BY license, any part of the article may be reused without permission provided that the original article is clearly cited. For more information, please refer to https://www.mdpi.com/openaccess .
Feature papers represent the most advanced research with significant potential for high impact in the field. A Feature Paper should be a substantial original Article that involves several techniques or approaches, provides an outlook for future research directions and describes possible research applications.
Feature papers are submitted upon individual invitation or recommendation by the scientific editors and must receive positive feedback from the reviewers.
Editor’s Choice articles are based on recommendations by the scientific editors of MDPI journals from around the world. Editors select a small number of articles recently published in the journal that they believe will be particularly interesting to readers, or important in the respective research area. The aim is to provide a snapshot of some of the most exciting work published in the various research areas of the journal.
Original Submission Date Received: .
- Active Journals
- Find a Journal
- Proceedings Series
- For Authors
- For Reviewers
- For Editors
- For Librarians
- For Publishers
- For Societies
- For Conference Organizers
- Open Access Policy
- Institutional Open Access Program
- Special Issues Guidelines
- Editorial Process
- Research and Publication Ethics
- Article Processing Charges
- Testimonials
- Preprints.org
- SciProfiles
- Encyclopedia

Article Menu

- Subscribe SciFeed
- Recommended Articles
- Google Scholar
- on Google Scholar
- Table of Contents
Find support for a specific problem in the support section of our website.
Please let us know what you think of our products and services.
Visit our dedicated information section to learn more about MDPI.
JSmol Viewer
Triangulating risk profile and risk assessment: a case study of implementing enterprise risk management system.

1. Introduction
2. background on the firm, 3. erm literature review, 4. sample and questionnaire data, 5. risk profile and risk assessment, 6. mitigation strategies, 7. conclusions, 8. case requirements.
- Using the average coded responses to selected questions in each of the five risk areas in Table 7 , provide a 500-word summary of the firm’s risk profile.
- Complete the risk matrix in Table A1 , below, by using the input measures from Table 8 : average of likelihood, impact on annual revenue growth, and level of control, along with variance of the expected impact and average control.
- rank the ten risk categories by (i) their expected impact, (ii) by an equally weighted index of expected impact and average control, and (iii) by an equally weighted index of three indices: expected impact, opinion convergence on expected impact, and opinion convergence on control.
- create an equally weighted consolidated ranking of the above three rankings and re-rank the ten risk categories.
- Develop a risk map of all ten risks identified for the firm.
- Using the input in Table 1 , the questionnaire results, and quantitative risk metrics in Table 7 and Table 8 , along with the discussion on key sources and drivers of risk in Section 6 , propose mitigation strategies for the top six risks selected by the board.
Author Contributions
Data availability statement, conflicts of interest, appendix a. instructor’s notes, appendix a.1. background and introduction, appendix a.2. case requirements: implementation.
| Risk Category | Average Expected Impact | Opinion Convergence (Expected Impact) | Opinion Convergence (Control) |
|---|---|---|---|
| Strategic Risk | |||
| Innovation Risk | |||
| Information and Security Risk | |||
| Geopolitical Risk | |||
| Financial Risk | |||
| Regulatory and Legal Risk | |||
| Operational Risk | |||
| Credit and Product Risk | |||
| Human Resources Risk | |||
| Reputation Risk |
| Risk Category | Average Probability | Average Expected Impact | Average Control | Opinion Convergence (Expected Impact) | Opinion Convergence (Control) |
|---|---|---|---|---|---|
| Strategic Risk | 46.46% | −0.16 | 4.23 | 0.71 | 0.1313 |
| Innovation Risk | 54.26% | −0.15 | 4.30 | 0.4 | 0.1271 |
| Information and Security Risk | 61.67% | −0.14 | 4.00 | 0.74 | 0.1428 |
| Geopolitical Risk | 51.30% | −0.15 | 3.95 | 0.63 | 0.1427 |
| Financial Risk | 48.10% | −0.17 | 4.05 | 0.28 | 0.1042 |
| Regulatory and Legal Risk | 45.56% | −0.14 | 3.95 | 0.22 | 0.1227 |
| Operational Risk | 44.81% | −0.16 | 3.76 | 0.36 | 0.0949 |
| Credit and Product Risk | 57.14% | −0.19 | 3.76 | 0.51 | 0.1282 |
| Human Resources Risk | 53.33% | −0.15 | 3.65 | 0.3 | 0.1185 |
| Reputation Risk | 42.08% | −0.16 | 3.35 | 0.6 | 0.1282 |
| Risk Category | Rank (1) | Rank (2) | Rank (3) | Consolidated Ranking |
|---|---|---|---|---|
| Strategic Risk | 3 | 5 | 7 | 6 |
| Innovation Risk | 4 | 6 | 5 | 6 |
| Information and Security Risk | 5 | 5 | 9 | 7 |
| Geopolitical Risk | 4 | 3 | 8 | 6 |
| Financial Risk | 2 | 3 | 1 | 1 |
| Regulatory and Legal Risk | 5 | 4 | 3 | 5 |
| Operational Risk | 3 | 2 | 2 | 2 |
| Credit and Product Risk | 1 | 1 | 4 | 1 |
| Human Resources Risk | 4 | 2 | 3 | 3 |
| Reputation Risk | 3 | 1 | 6 | 4 |
| Risk Categories | Key Drivers of Risks | Mitigation Strategies |
|---|---|---|
| Strategic | Developed a new 5-year, 2017–2022, strategic plan establishing more clearly the firm’s mission and vision, creating strategies and tactics aligning the firm’s operational, financial, risk management, and marketing/communication goals. Created a stand-alone risk committee as a sub-committee of the board. Provided regular progress reports to the board on realizing the goals of the plan. Used risk-adjusted criteria to assess the valuation implications of new projects. Produced quarterly global economic and environmental scans to review the plan’s goals and strategies, recommending possible changes. | |
| Innovation | Established a portfolio approach whereby the financial and human resources are allocated strategically and optimally to enhance innovation in core offerings, adjacent opportunities, and, particularly, transformational territories achieved through geographic diversification. Promoted a more effective dialog between staff, senior executives, and the board on new initiatives. Incentivized staff to experiment with new ideas. Aligned the R&D budget with best practices by comparable entities. Used risk-adjusted approaches to measure the value proposal of R&D projects. | |
| Informational and Security | Hired a Chief Informational Officer (CIO) who was responsible for developing and executing policies to manage the global network of information. Key steps included the synchronization and consolidation of email platforms, launching software and hardware for document management, establishing effective patches to detect and defuse cyber-attacks, and aligning information technology policies with strategic planning. | |
| Geopolitical | Incorporated country risk analysis information regularly published by the International Monetary Fund (IMF) and the World Bank (WB) to better assess geographic risks and their implications for ongoing and new initiatives. Established quarterly country-based reports from foreign field offices. Secured a global insurance contract against losses occurring from travel bans, visa restrictions, kidnappings, and nationalizations. | |
| Financial | Systematically shifted revenue sources, such that the contribution of non-governmental projects would increase to 30% from its existing level of 5% of annual revenues in 5 years. Planned to increase liquidity ratios by 30% over 5 years. Established quarterly revenue scenario exercises to stress test the financial health of the firm. Implemented an optimal currency model to manage the FX risk of foreign revenues. Developed and implemented risk-adjusted valuation approaches related to R&D investments. | |
| Regulatory | Reported and regularly updated U.S. Federal/State- and country-specific compliance measures. Established quarterly country-based regulatory reports from foreign field offices. Secured a global insurance contract to cover the losses due to third-party liability. |
| 1 | |
| 2 | |
| 3 | |
| 4 | ( ) for an approach to estimating the cost of capital for privately held firms. |
- Aabo, Tom, John Fraser, and Betty Simkins. 2005. The Rise and Evolution of the Chief Risk Officer: Enterprise Risk Management at Hydro One. Journal of Applied Corporate Finance 17: 62–75. [ Google Scholar ] [ CrossRef ]
- Beasley, Mark, Richard Clune, and Dana Hermanson. 2005. Enterprise Risk Management: An Empirical Analysis of Factors Associated with the Extent of Implementation. Journal of Accounting and Public Policy 24: 521–31. [ Google Scholar ] [ CrossRef ]
- Fabrigar, Leandre, Duane Wegener, Robert MacCallum, and Erin Strahan. 1999. Evaluating the use of exploratory factor analysis in psychological research. Psychological Methods 4: 272–99. [ Google Scholar ] [ CrossRef ]
- Farrell, Mark, and Ronan Gallagher. 2014. The Valuation Implications of Enterprise Risk Management Maturity. The Journal of Risk and Insurance 82: 625–67. [ Google Scholar ] [ CrossRef ]
- Fraser, J., and B. Simkins. 2010. Enterprise Risk Management . Hoboken: John Wiley and Sons. ISBN 9780470499085. [ Google Scholar ]
- Fraser, John, Betty Simkins, and Kristina Narvaez. 2014. Implementing Enterprise Risk Management: Case Studies and Best Practices . Hoboken: John Wiley and Sons. [ Google Scholar ]
- Froot, Kenneth, David Scharfstein, and Jeremy Stein. 1993. Risk Management: Coordinating Investment and Financing Policies. Journal of Finance 48: 1629–58. [ Google Scholar ] [ CrossRef ]
- Grace, Martin, J. Tyler Leverty, Richard Phillips, and Prakash Shimpy. 2014. The Value of Investing in Enterprise Risk Management. The Journal of Risk and Insurance 82: 289–316. [ Google Scholar ] [ CrossRef ]
- Harrington, Scott, Greg Niehaus, and Kenneth J. Risko. 2002. Enterprise Risk Management: The Case of United Grain Growers. Journal of Applied Corporate Finance 14: 71–81. [ Google Scholar ] [ CrossRef ]
- Hoyt, Robert E., and Andre P. Liebenberg. 2011. The Value of Enterprise Risk Management. Journal of Risk and Insurance 78: 795–822. [ Google Scholar ] [ CrossRef ]
- Hristov, Ivo, Riccardo Camilli, Antonio Chirico, and Alessandro Mechelli. 2022. The Integration between Enterprise Risk Management and Performance Management System: Managerial Analysis and Conceptual Model to Support Strategic Decision-Making Process. Production Planning & Control , 1–14. [ Google Scholar ] [ CrossRef ]
- Jalilvand, Abol, and John W. Kostolansky. 2016. Le Beau Footwear: A Business Valuation Case for a Privately Held Firm. Issues in Accounting Education 31: 439–47. [ Google Scholar ] [ CrossRef ]
- Jalilvand, Abol, and Sidharth Moorthy. 2022. Enterprise Risk Management (ERM) Maturity: A Clinical Study of a U.S. Multinational Nonprofit Firm” (with S. Moorthy). Journal of Accounting, Auditing, and Finance . [ Google Scholar ] [ CrossRef ]
- Jensen, Michael C., and William H. Meckling. 1976. Theory of the Firm: Managerial Behavior, Agency Costs and Ownership Structure. Journal of Financial Economics 3: 305–60. [ Google Scholar ] [ CrossRef ]
- Kraus, Alan, and Robert Litzenberger. 1973. A State Preference Model of Optimal Financial Leverage. Journal of Finance 28: 911–22. [ Google Scholar ]
- Leland, Hayne E., and David H. Pyle. 1977. Informational Asymmetries, Financial Structure, and Financial Intermediation. Journal of Finance 32: 371–88. [ Google Scholar ] [ CrossRef ]
- Lindberg, Deborah L., and Deborah L. Seifert. 2011. A Comparison of U.S. Auditing Standards with International Standards on Auditing. The CPA Journal 81: 17–21. [ Google Scholar ]
- McShane, Michael K., Anil Nair, and Elzotbek Rustambekov. 2011. Does Enterprise Risk Management Increase Firm Value? Journal of Accounting, Auditing and Finance 26: 641–58. [ Google Scholar ] [ CrossRef ]
- Miller, Merton. 1977. Debt and Taxes. Journal of Finance 32: 261–75. [ Google Scholar ]
- Miller, Merton H., and Franco Modigliani. 1958. The Cost of Capital, Corporation Finance and the Theory of Investment. American Economic Review 48: 261–97. [ Google Scholar ]
- Miller, Merton H., and Franco Modigliani. 1963. Corporate Income Taxes and the Cost of Capital: A Correction. American Economic Review 53: 433–43. [ Google Scholar ]
- Nocco, Brian W., and René M. Stulz. 2006. Enterprise Risk Management: Theory and Practice. Journal of Applied Corporate Finance 18: 8–20. [ Google Scholar ] [ CrossRef ]
- Rosenburg, Joshua V., and Til Schuermann. 2006. A General Approach to Integrated Risk Management with Skewed, Fat-Tailed Risks. Journal of Financial Economics 79: 569–614. [ Google Scholar ] [ CrossRef ]
- Ross, Stephen A. 1977. The Determination of Financial Structure: The Incentive Signaling Approach. Bell Journal of Economics 8: 23–40. [ Google Scholar ] [ CrossRef ]
- Samanta, P., T. Azarchs, and J. Martinez. 2004. The PIM Approach to Assessing the TRM Practices of Financial Institutions . New York: Standard and Poor’s/McGraw-Hill. [ Google Scholar ]
- Shad, Muhammad Kashif, Fong-Woon Lai, Amjad Shamin, Michael McShane, and Sheikh Muhammad Zahid. 2022. The relationship between enterprise risk management and cost of capital. Asian Academy of Management Journal 27: 79–103. [ Google Scholar ]
| Revenues | 2017 | 2016 | 2015 | 2015–2017 Change |
|---|---|---|---|---|
| Government Grant | 275.0614 | 295.4502 | 313.2000 | −12.18% |
| Non-Government Grant | 22.0650 | 23.6250 | 25.0000 | −11.74% |
| Tuitions | 92.1876 | 98.7053 | 104.4500 | −11.74% |
| Administrative Fees | 41.9235 | 44.8875 | 47.5000 | −11.74% |
| Fund Raising | 1.8700 | 2.2500 | 2.7500 | −32.00% |
| Investment Income | 3.2500 | 2.2900 | 1.5000 | 116.67% |
| Other Income | 4.9426 | 5.2920 | 5.6000 | −11.74% |
| Total Revenues | 441.3000 | 472.5000 | 500.0000 | −11.74% |
| Student Exchanges | 143.0067 | 147.2570 | 156.8825 | −8.84% |
| Program Expenses | 153.1890 | 169.8350 | 170.8000 | −10.31% |
| Salary and Pension | 88.6176 | 92.2720 | 98.2000 | −9.76% |
| Depreciation and Amortization | 2.2654 | 2.2700 | 2.3846 | −5.00% |
| Repair and Maintenance | 1.2180 | 1.3100 | 1.4329 | −15.00% |
| Transportation | 33.1757 | 37.2810 | 43.3500 | −23.47% |
| Taxes | 1.1900 | 1.3000 | 1.2000 | −0.83% |
| Miscellaneous Expenses | 5.9378 | 6.5250 | 8.7500 | −32.14% |
| Total Expenses | 428.600 | 458.050 | 483.000 | −11.26% |
| Net Surplus (Deficit) | 12.7000 | 14.4500 | 17.0000 | −25.29% |
| Sample of Risk Owners | Identify a representative and diverse group of functional risk owners (managers/executives in field offices with major P/L responsibilities), senior executives, and board members. |
| Education | Develop and deliver a short educational module for the sample group to create a uniform level of understanding on the dynamics and application of ERM. |
| Questionnaire | Administer and analyze a focused questionnaire covering multiple risk management areas including risk culture, risk recognition, risk organization, risk governance, risk control, and risk measurement. |
| Synthesis and Risk Assessment | Synthesize and compile the results obtained from the questionnaire. Develop a detailed multidimensional risk table identifying and prioritizing the existing and potential risks. |
| Mitigation | Develop mitigation strategies for the top risks. |
| Review | Review and assess, on an ongoing basis, the effectiveness of the proposed risk management system. |
| Risk Areas | Definition |
|---|---|
| Risk Culture | The questions in this segment are designed to elucidate the interplay between the organization’s strategy, goals, decision-making processes, risk appetite, and risk management philosophy. |
| Risk Governance | The questions in this segment focus on the board structure, processes, and levels, and the effectiveness of the board’s involvement, knowledge, and transparency in devising strategies to carry out risk management decisions. |
| Risk Organization | This section focuses on the administrative and operational nature of capturing, communicating, reporting, monitoring, and compliance related to risk management actions. |
| Risk Recognition | This segment is designed to elucidate the organization’s ability to identify risks, distinguish risks from opportunities, recognize risk metrics, and increase awareness of fraudulent activities. |
| Risk Control | The questions in this segment have been designed to gauge the firm’s level of existing control regarding overall risk exposure. |
| Risk Assessment | Devise and implement consistent multi-dimensional risk indices, which are used to assess and prioritize potential categories of risks. |
| Maturity (Level) | Maturity-Level Characteristics |
|---|---|
| Ad hoc (1) | This implies an extremely primitive level of ERM maturity, where risk management typically depends on the actions of specific individuals, with improvised procedures and poorly understood processes. |
| Initial (2) | Risk is managed in silos, with little integration or risk aggregation.Processes typically lack discipline and rigor. Risk definitions often vary across the silos. |
| Repeatable (3) | A risk assessment framework is generally in place, with the Board of Directors being provided with risk overviews. Approaches to risk management are established and repeatable. |
| Managed (4) | Enterprise-wide risk management activities, such as monitoring, measurement, and reporting, are integrated and harmonized, with measures and controls established. |
| Leadership (5) | Risk-based discussions are embedded at a strategic level, such as long-term planning, capital allocation, and decision-making. Risk appetite and tolerances are clearly understood, with alerts in place to ensure that the board of directors and the executive management are made aware when risk thresholds are exceeded. |
| Operational Risk | Risks resulting from inadequate or failed procedures, systems, processes, or policies. It includes employee errors, business interruptions, fraud or other criminal activity, equipment failure, logistical bottlenecks, third-party liability, employee safety, timeliness, and accuracy. |
| Financial and Market Risk | Risks resulting from a shortfall in revenues and/or cost escalation, accumulated losses, diminished liquidity, problems in meeting financial obligations, diminished credit rating, forecasting and valuation errors, audit problems, portfolio losses, and poor hedging against market volatility (interest rates, exchange rates, and stock prices). |
| Regulatory and Legal Risk | Risks resulting from lawsuits and unpredictable changes in the local and global regulatory environment and from noncompliance with statutory and accreditation rules. |
| Strategic Risk | Risks resulting from poor articulation and communication of goals and strategies, misalignment of the strategic plan and corporate governance, an uninformed board, and a lack of established and effective review processes. |
| Human Resources Risk | Risks resulting from problems in employee recruitment and retention, low labor productivity, and a sub-optimal compensation system. |
| Innovation Risk | Risks resulting from inertia in identifying and implementing new products and services in local and foreign markets in response to political, macroeconomic, and market changes. |
| Geopolitical Risk | Risks resulting from political changes, sanctions, travel bans, economic and political retaliation, and the nationalization of foreign assets and establishments. |
| Credit Risk | Risks resulting from competition, economic slowdown/slow recovery, supply chain disruption, embargoes, customer attrition, changes in customers’ expectations and demand, and changes in customers’ financial capacity. |
| Informational/Security Risk | Risks resulting from cyber security attacks and hacking, using outdated and inefficient information systems (technology obsolescence), and communication system failure. |
| Reputation Risk | Risks resulting from a decline in or lack of brand and image, the loss of customers’ trust, negative publicity, recruitment challenges, and fundraising problems. |
| Very Low p < 0.15 | Low 0.15 < p < 0.3 | Medium 0.3 < p < 0.5 | High 0.5 < p < 0.75 | Very high p > 0.75 | Ad hoc | Initial | Repeatable | Managed | Leadership |
| Very Negative −25% < G < −50% | Negative 0% > G < −25% | Neutral 0% | Positive 0% < G < 40% | Very Positive G > 40% | |||||
| Risk Areas | Average Score | Sectional Average |
|---|---|---|
| Risk Culture | ||
| Overall, is the firm willing to take any magnitude of risk in order to achieve strategic objectives? | 2.37 | 2.70 |
| How are the critical competencies of the firm structured, in a range from “Operational” to “Entrepreneurial”? | 2.61 | |
| How do you describe the reward structure of the company, in a range from “Margins and Productivity” to “Milestones and Growth”? | 2.63 | |
| Is the organizational culture: | 2.98 | |
| -“Efficiency, Low Risk, Quality, Customers”, | ||
| -“Risk Taking, Speed, Flexibility, and Experimentation”, or | ||
| -somewhere in between? | ||
| Rate the leadership role from being “Authoritative and Top Down” to “Visionary and Involved”. | 2.77 | |
| How would you rank the strategic and related objectives defined by the organization, in a range from “Unclear and Unfocused” to “Planned and Transparent”? | 2.82 | |
| Based on the reflection above, rate the firm’s overall risk management culture. | 2.75 | |
| Risk Recognition | ||
| What type of forces, internal and external, impact the risk management culture described above, in a range from “Entirely Internal” to “Entirely External”? | 2.85 | 2.85 |
| Rate the organization’s ability to distinguish risk vs. opportunity. | 2.19 | |
| What are the most relevant assessment metrics for quantifying significant measurable risks and incorporating them into the decision-making process, in a range from “Entirely Qualitative” to “Entirely Quantitative”? | 3.05 | |
| How susceptible is the firm to fraud? Which areas are most susceptible to the same? | 3.45 | |
| Based on the reflection above, rate your department’s overall risk recognition capabilities. | 2.69 | |
| Risk Organization | ||
| How effective is the organization in capturing risk information and communicating it to various constituencies (government, donors, clients, staff, and the board)? | 1.82 | 2.70 |
| Do communication barriers exist within the organization when addressing risk? | 3.42 | |
| How often do you think the senior management involves the board and staff during the strategy-setting process, including when making decisions to accept or reject risk factors? | 2.93 | |
| Rate the activities of writing down, prioritizing, and disseminating risk. | 3.56 | |
| Rate the risk monitoring and reporting system within the organization. | 2.36 | |
| Based on the reflection above, rate the firm’s risk management organizational capacity. | 2.12 | |
| Risk Governance | ||
| Rate the board’s understanding of the organization’s priority risks and how those risks should be addressed. | 2.37 | 2.47 |
| How much do the senior executives involve the board in the assessment of strategic risks? | 3.07 | |
| Rate the frequency with which the company revisits its risk assessment to determine whether the circumstances and conditions have changed or whether there are new emerging risks. | 2.56 | |
| How confident are you about the organization not taking significant risks without the board’s knowledge? | 1.79 | |
| How effective do you consider the organization’s risk management culture and governance functioning to be? | 2.73 | |
| Based on the reflection above, rate the alignment between risk management and governance at the firm. | 2.32 | |
| Risk Control | ||
| How well-defined are the risk management goals in terms of ongoing strategic activities: in a range from “Unclear and Unfocused” to “Planned and Transparent”? | 3.12 | 3.10 |
| How do you rate the quality, reliability, and relevance of the risk reporting? | 2.76 | |
| How effective are the ongoing monitoring activities (e.g., compliance monitoring, risk management group, board monitoring, etc.)? | 2.93 | |
| Rate the risk measuring methodology adopted by the firm when each risk is measured, on an individual level. | 3.20 | |
| Rate the risk measuring methodology adopted by the firm when each risk is measured, on an enterprise level. | 2.09 | |
| Does the company have a rising learning curve with regard to its risk assessment and management process? | 4.47 |
| Risk Category | Average Probability | Average Impact | Average Control | Variance Expected Impact | Variance Control |
|---|---|---|---|---|---|
| Strategic Risk | 46.46% | −0.3444 | 4.23 | 0.0129 | 0.3085 |
| Innovation Risk | 54.26% | −0.2764 | 4.30 | 0.0036 | 0.2987 |
| Information and Security Risk | 61.67% | −0.2270 | 4.00 | 0.0107 | 0.3263 |
| Geopolitical Risk | 51.30% | −0.2924 | 3.95 | 0.0089 | 0.3177 |
| Financial Risk | 48.10% | −0.3534 | 4.05 | 0.0023 | 0.1781 |
| Credit and Product Risk | 57.14% | −0.3325 | 3.76 | 0.0094 | 0.2324 |
| Operational Risk | 44.81% | −0.3571 | 3.76 | 0.0057 | 0.1273 |
| Regulatory and Legal Risk | 45.56% | −0.3073 | 3.95 | 0.0009 | 0.2349 |
| Human Resources Risk | 53.33% | −0.2813 | 3.65 | 0.0020 | 0.1871 |
| Reputation Risk | 42.08% | −0.3802 | 3.35 | 0.0092 | 0.1844 |
| The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
Share and Cite
Jalilvand, A.; Moorthy, S. Triangulating Risk Profile and Risk Assessment: A Case Study of Implementing Enterprise Risk Management System. J. Risk Financial Manag. 2023 , 16 , 473. https://doi.org/10.3390/jrfm16110473
Jalilvand A, Moorthy S. Triangulating Risk Profile and Risk Assessment: A Case Study of Implementing Enterprise Risk Management System. Journal of Risk and Financial Management . 2023; 16(11):473. https://doi.org/10.3390/jrfm16110473
Jalilvand, Abol, and Sidharth Moorthy. 2023. "Triangulating Risk Profile and Risk Assessment: A Case Study of Implementing Enterprise Risk Management System" Journal of Risk and Financial Management 16, no. 11: 473. https://doi.org/10.3390/jrfm16110473
Article Metrics
Article access statistics, further information, mdpi initiatives, follow mdpi.

Subscribe to receive issue release notifications and newsletters from MDPI journals
Open Access is an initiative that aims to make scientific research freely available to all. To date our community has made over 100 million downloads. It’s based on principles of collaboration, unobstructed discovery, and, most importantly, scientific progression. As PhD students, we found it difficult to access the research we needed, so we decided to create a new Open Access publisher that levels the playing field for scientists across the world. How? By making research easy to access, and puts the academic needs of the researchers before the business interests of publishers.
We are a community of more than 103,000 authors and editors from 3,291 institutions spanning 160 countries, including Nobel Prize winners and some of the world’s most-cited researchers. Publishing on IntechOpen allows authors to earn citations and find new collaborators, meaning more people see your work not only from your own field of study, but from other related fields too.
Brief introduction to this section that descibes Open Access especially from an IntechOpen perspective
Want to get in touch? Contact our London head office or media team here
Our team is growing all the time, so we’re always on the lookout for smart people who want to help us reshape the world of scientific publishing.
Home > Books > Risk Management - Current Issues and Challenges
Importance of Risk Analysis and Management – The Case of Australian Real Estate Market
Submitted: 18 April 2012 Published: 12 September 2012
DOI: 10.5772/50669
Cite this chapter
There are two ways to cite this chapter:
From the Edited Volume
Risk Management - Current Issues and Challenges
Edited by Nerija Banaitiene
To purchase hard copies of this book, please contact the representative in India: CBS Publishers & Distributors Pvt. Ltd. www.cbspd.com | [email protected]
Chapter metrics overview
7,973 Chapter Downloads
Impact of this chapter
Total Chapter Downloads on intechopen.com
Total Chapter Views on intechopen.com
Overall attention for this chapters
Author Information
Gurudeo anand tularam, gowri sameera attili.
*Address all correspondence to:
1. Introduction
Life is full of risks for example risk is involved in simple things like turning on the gas at home or when dealing with life threatening medical emergency decisions. Risk plays an important role in the way we manage our economy, organization or our family. Risk can be rather complex when household money is involved; such as for individuals or families – for example, mums and dads stand to either gain or lose large sums of money. The types of risks involved influence decisions on how to manage or invest money in shares, bonds or property. When faced with risks, the challenge is how well prepared are we to overcome risks. Risk awareness may be limited in which case there is a high likelihood of risk turning into hazard -leading to disastrous outcomes. Successful businesses make constant efforts to change or update their in house administrative polices and frameworks to allow for possible risks in their business requirements. Some decisions that are likely to have been factored into the component of risk are: rigid corporate governance requirement, human resource planning, succession planning, training and development, merger and acquisitions, adapting to different cultures, foregoing or discontinuing some existing products, outsourcing, new market development etc. No matter how important a decision is made, strategic alignment is critical in business decision making. New ideas should be implemented according to the business needs a company. The introducing of novel ideas should involve all personnel particularly during the decision making processes of development and setting of targets. A well-managed business is also well prepared one and thus able to confront challenges of the modern dynamic business environments.
Yet managing risk is rather challenging for the world is mostly unpredictable. The processes are continuously changing and evolving in terms of resources that are available - technology, innovation, human resources and time to name a few. In order to adequately address an impending risk, it is important to gather as much factual information as possible for analysis to help manage and thus minimize risk.
Risk can be classified into both voluntary and involuntary [ 1 ]. This classification depends on how an individual or an organization judges the situation. For example, a person with a habit of smoking or drinking fails to associate the habits as involving risks; yet often the habit becomes hazardous and they can significantly affect a person’s quality life. Involuntary risk places a person or the organization in a state of ambiguity, where the people involved in the decision making process have not been exposed to a particular circumstance or they lack knowledge and awareness of the particular risk situation. The ability to deal with such risks is a crucial factor in determining successful outcomes irrespective of the stature of an individual or an organization.
For some individuals, the ability to deal with risk appears to be built in their character but for the rest of us it seems, it is knowledge that can be acquired through training. In order to gain the skill set required so that one to deal with risk, it is important to step out of one’s comfort zone and be willing to change, learn, develop new skills, or be challenged to manage risk. Risk management is a methodical approach that could be taught and learnt by most. The general process and steps involved is presented in Figure 1 .

The process of risk management
This paper is organized in the following manner: In the next few sections risk is defined and risk management explored focusing on types of risks associated with real estate market. The Australian real estate market is then reviewed and possible risks involved are explored in some depth particularly in terms the global financial crisis. The paper compares the market with the rest of the world and summaries investor risks and rewards in Australian real estate market.
1.1. Definition of risk
In the international context, the ISO 31000/ISO Guide 73: 2009 [ 2 ] defines risk as the “effect of uncertainty on objectives” (p. 1). When there is a lack of knowledge or exposure to a certain event then such a situation can be termed uncertain. Taking decision on an uncertain event or situation may or may not be successful, which is what risk is about. Many definitions of risk exist in common usage [ 3 - 4 ]; however the ISO definition of risk was developed by an international committee representing over 30 countries and is based on the input of several thousand subject matter experts.
Risk is defined in Australia by the Australia/New Zealand standard for risk management [ 2 ] as “the possibility of something happening that impacts on your objectives. It is the chance to either make a gain or a loss. It is measured in terms of likelihood and consequence…” (p. 2). Risk can also be defined as the uncertainty of future events that might influence the achievement of one or more objectives such as an organization’s strategic, operational and financial objectives [ 3 ]. Risk management may produce positive opportunities for developers although the negative aspects of risk are usually the once that are emphasized [ 4 ].
Likelihood of risk occurring varies from industry to industry and how complex a job maybe. Some areas where there is a high chance of risk are construction, transport, mining, health care, sports, finance and banking, insurance and superannuation.
Risk can be broadly understood and explained in three different scenarios [ 5 ]: risk versus probability; risk versus threat; and all outcomes versus negative outcomes. It is believed that any risk can be managed through the engagement of a proper risk management process.
1.2. Risk management
There seems to be an increasing demand of organizations to meet and exceed the financial expectations of shareholders. In the pursuit of growth, many organizations (for example: Toyota) have adapted and responded to expectations of the shareholders by becoming lean and efficient. It is always easy to think that risks and their potential consequences could have been predicted and managed. This is clearly not true when it comes to success in a business. Business success usually requires some acceptance of risk and, as such any risky strategy undertaken may lead to a failure.
In large organizations and corporations there are designated personnel; namely, risk managers. Hillson [ 6 ] argued that risk is mostly managed “continuously, both consciously an unconsciously, though rarely systematically” (p. 240). Risk manager’s main role is to be aware of the market, collect data and predict forthcoming threats so that a company can manage the risks in a successful manner. Risk manager duties include developing and communicating risk polices and process, building risk models involving market, conducting credit and operational risk analysis, coordinating with concerned stakeholders involved in the process and creating a risk awareness culture in the organization.
Risk management not only prevents organizations from entering a dangerous and uncertain territory, which could lead to a catastrophic failures, but also ensure the development and growth of the business. The depth and clarity with which a risk is defined is critical for risk management. In an event where an organization has a low risk situation at hand and decides to postpone rather than resolve the issue involved for financial or other reasons, the risk may eventually become a threat of moderate to high level and this could prove to be disastrous for management. Ignoring the risks that apply to the business activities or the events that have been planned could impact on the following:
customer and public confidence in the organization;
credibility, reputation and status;
equipment and the environment;
financial position of the concerned; and
health and safety of employees, customers, volunteers and participants.
A systematic approach to managing risk is now regarded as best management practice. The approach taken almost always benefits the organization irrespective of type of risk involved. Once the risk is identified it is documented in detail; subsequently the concerned stakeholders undertake possible risk management and mitigation processes. A comprehensive review of the situation and critical feedback are usually required that may ultimately lead to changes in the organizational polices and structures; particularly in case of a major events.
Organizations that thrive to be successful constantly monitor themselves and willfully undertake only calculated risks. In doing so, they enjoy a competitive advantage in addition to meeting their business objectives. In era of globalization, companies are often expanding their business opportunities and in the process, they may undertake challenging and ambitious projects. In most cases, they need to take a number of risks. In this regard, businesses such as Microsoft, Google, and Wal-Mart appear to have been successful global players mainly because they were able to manage risk in a timely manner.
Risk management decisions should be a part of business objectives. Every new project, policy or invention should include all the possible anticipated risks that one may possibly confront. Decision making process needs to consider threats identified, its impact and reaction on the business. By making a careful analysis, companies will have fewer surprises and thus may in the end spend less time recovering from the losses that may be inevitable at times. When companies do not have “a keen eye on the kind of risk”, risk retention can become a legitimate way of managing the risk. Figure 2 shows the six steps involved in the risk management process: establish the context, identify the risk, analyze the risk, evaluate the risk, and manage and review the risk.
1.3. The steps involved in managing risk

The steps in risk management
1.3.1. Establish goals and context
To establish context and define goals is an important step. Once the context is established it is critical that the risk is defined and the objectives are set. Also important is to know the limitations of the risk strategies proposed. An effective risk management team understands the needs of the organization and the way it operates. Once the goal is defined there is a need to identify the scope of the context. In general, these factors can be classified into strategic and operational risks. Strategic risk management includes economic, social, environmental, political, legal and public issues; while operational risk management includes technological, human resource, financial, reputation and other relevant strategic issues. Clearly, management may not be able to totally control the many factors but the risks posed by them could indeed be minimized.
The process of risk management has to be simple, precise and effective. For it to be effective, organizations should consider strength, weakness, opportunities and threats (SWOT) type analysis of the situation. By conducting SWOT analysis, the management can identify and analyze different situations [ 7 ]. Once threats are identified, appropriate measures and decisions may then be taken to convert the threat into an opportunity. The organizational context provides an understanding of the organization, its capability and goals, objectives and strategies. In establishing the context the identification of stakeholders is critical; these are individuals who may affect, or be affected by decisions made by the risk management team. For example, stakeholders may be employees, volunteers, visitors, insurance organizations, government agencies or suppliers etc. Each stakeholder will have different needs, concerns and opinions; therefore it is important to communicate with the stakeholders involved in the process of addressing risks.
1.3.2. Identify risks
Identification of risk involves a systematic process of examining situations and finding solutions. The process includes stages such as group discussions and brainstorming sessions to generate a variety of ideas. While all the ideas or issues generated may or may not be relevant, it is important to document all problems, possible impacts and solutions identified. There are four primary areas in which risk can occur in a general business environment:
financial: this could mean loss of funding, insurance costs, fraud, theft, fees etc.;
physical: this involves physical assets of the organization, personal injuries and environmental;
ethical or moral: involves a perpetuated, actual or potential harm to the reputation or beliefs of an individual or organization; and
legal: this includes responsibilities and adherence to the law, rules and regulations of governing bodies such as the federal, state or local governments.
Risks can be identified by examining records of previous activities or events. Other ways in which risks could be identified are results from past experiences (personal, local or overseas) [ 8 ], through conduction interviews of stakeholders (example: Susilawati and Armitage [ 8 ]) or by analyzing specific real life or generated scenarios.
1.3.3. Analyse risks
This step determines and addresses the impact of threats that have been documented. Threats identified are rated according to the likelihood of occurrence. The potential of an identified risk can be estimated by the effect it has on financial and other resources. When analyzing a risk, one decides on the relationship between the likelihood of a risk occurring and the consequences of the risk identified. The level of risk is then defined and management of it is then explored. Managing risk can be done in several ways such as contingency planning, using existing assets or making an investment in new resources. The levels of the risks can be classified into
extreme: an extreme risk requires immediate action as the potential could be devastating to the enterprise;
high: a high level of risk requires action, as it has the potential to be damaging to the enterprise;
moderate: allocate specific responsibility to a moderate risk and implement monitoring or response procedures; and
low: can manage a low level of risk with routine procedures.
The tools most commonly employed to measure risks include qualitative techniques [ 10 ]. Melton [ 11 ] described the tools as probability and impact analysis tools and Webb [ 4 ] called these likelihood and consequences tools. A risk matrix presentation tool (qualitative technique) can provide better insights to the nature of a risk. Risk matrix is often used as a tool to display different risks once they have been analyzed. It allows an organization to mark a threshold above which risks will not be tolerated; or will receive additional treatment from the board or delegated staff. In Figure 3 the threshold is set at risks score of 5 or above. It is then important to ask the following questions in relation to each of the identified risks:
What is the likelihood of the risk occurring?
Are there any controls currently in place to manage the risk - if yes then, are there any remaining risks?
What are the consequences if the risk should occur? and
What is the level of the risk?

Risk matrix Source: adapted from Austrac
1.3.4. Evaluate risks
In this step the tolerance of the risk is determined; that is, whether the identified risk is acceptable or unacceptable. The evaluation takes into account the following:
importance of risk management and possible outcomes of a risky activity;
potential and actual losses that may arise from the risk;
benefits and opportunities presented by the risk; and
degree of control one has over the risk.
An acceptable risk is a type of risk that that a business can tolerate; a loss for example- the risk does not have major impact on business. An acceptable risk has to be constantly monitored, reviewed and documented so that it remains tolerable. A risk is deemed to be an acceptable risk because of following reasons:
risk level is low and the benefits presented by the risk outweigh the cost of managing it;
risk level is so low that it does not warrant spending time and money to manage it; and
risk presents opportunities that are much greater than the threats posed by it.
A unacceptable risk is when a business is bound to experience significant losses and such losses cannot be tolerated. In such an event it is important to address and treat the risk in an appropriate manner.
1.3.5. Treatments of risks
Risks may be dealt with in several ways; it can be avoided, reduced, shared or retained. Risk is avoided when appropriate decisions are taken to eliminate all possible pitfalls thereby preventing the situation from occurrence. In most decision making processes, calculations are made and ideas are contemplated to strike a balance between the cost and effect. In such situations calculated risks are accepted and a high risk situation may be reduced by:
identifying options to treat the risk;
selecting the best treatment option;
preparing a risk treatment plan; and
implementing a risk treatment plan.
In other cases, risk is shared between the stake holders in terms of how profits and losses are shared. This is done mainly to share the impact of a risky event when it occurs. For example, in the era of globalization it is challenging for the companies to enter new markets and countries. In order to minimize uncertainty and exploit business situations that may exist, companies often decide to share risk; careful consideration and research undertaken by the companies often suggest risk sharing. Risk sharing develops opportunities while engaging all partners in achieving strategic goals and the gains and loss are then shared accordingly. The nature of strategies to mitigate risk often depends on the experience of the risk manager who may consider one or more of the following [ 3 ]:
avoid the risk by deciding not to proceed with the activity or choosing another way to achieve the same outcome;
control the risk by reducing the likelihood of the risk occurring, the consequences of the risk or both;
transfer the risk by shifting all or part of the responsibility of the risk to another party who is best able to control it; and
retain the risk after accepting that the risk cannot be avoided, controlled or transferred.
It seems the simplest of all methods of addressing a risk is by retaining an identified risk that may not potentially impact upon the operations of a business. It is important to continuously monitor such risks for in the absence of careful monitoring, the risks may become threats in due time.
A dedication towards risk management often projects a wiser professional image to the community. In doing so, the stake holders recognize the fact that the concerned organization has a keen interest in safeguarding its assets as well as that of its employees, visitors and volunteers among others. In the process of identifying, analyzing and evaluating risks an organization improves its management team’s ability to make educated decisions.
1.3.6. Monitor and report effectiveness of risk treatments
Every organization irrespective of size clearly strives to reduce the risks involved. In order to reduce risk organizations have to align their policies and structures in a consistent manner and constantly monitor business activities. Also, there is a need to allocate resources (financial, human resource, technology etc.) efficiently to improve performance and to win the approval of all stake holders. It is also important to ensure personnel working at different levels in the organization report to the appropriate authorities when a risk is identified. Such a culture enables an organization to document and then undertake suitable and timely measures to avert risks. In the risk management process, data capture and reporting can provide valuable insights into the risk management process. A sample risk management planning template is shown in Table 1 . As discussed, risk management team play a vital role in identifying and addressing risks.
Risk management planning template
It is necessary to constantly monitor and evaluate the strategies that are employed to manage risks. This is because risks do not remain the same - new risks are created, existing risks are increased or decreased, some risks may no longer exist and previous or existing risk management strategies may no longer be effective. In the end risks can originate from accidents, legal liabilities, natural causes and disasters, uncertainty in financial markets, credit risk, project failures (at any phase in design, development, production, or sustainment life-cycles), or events of unpredictable root-cause. Several risk management standards exist including those from the Project Management Institute, National Institute of Science and Technology, Actuarial Societies, and ISO standards. The risk management definitions, methods and goals vary widely according to the context of project management, security, engineering, industrial processes, financial portfolios, actuarial assessments, public health and safety and real estate.
An important aim of the paper is to study and review the real estate market in Australia to identify risk and rewards as well as compare the Australian market conditions and performance with the rest of the world. Therefore, the focus of the next section is on risks in the real estate market.
1.4. Types of risk associated real estate market

Types of risk in real estate market
As is the case with every other industry, there are several risks in the real estate market. For example, there exists a risk factor in land procurement; housing development; asset management; property management; tenancy management to name a few [ 13 ]. The risks may be classified as internal or external risks ( Figure 4 ). In turn, the internal and external risks can be divided into various other risk categories shown in Figure 5 and Figure 6 [ 14 ]. Builders, project managers, owners and investors who plan to make an investment or hold an investment in the property market may need to consider one or more of the following risks and then implement appropriate strategies for their projects to be successful.
1.4.1. Internal risk
Internal risk can be divided into financial management, human resources, property management, legislative compliance, corporate governance and housing management as shown in Figure 5 .
Financial management: A detailed analysis of any proposed or existing projects need to be conducted for project viability. It is also important to plan the cash flow and management of the same. A poor cost control may lead to a budget over shoot and the project may run into un-chartered territories. When it comes to servicing the debt due care needs to be given to income streams - to take into account either reduction or loss of future income streams. In this regard, banking organisations need to be diligent in testing the capacity to repay the loans that are being offered. Fraud often occurs in real estate market mainly involving the use of false documents regarding number of properties, outgoing fees or rates, income streams and so on.

Internal risk Source: adapted from Sheryl and Adam [ 14 ]
Insurance also plays a vital role in financial management of a project or investment. Adequate insurance is needed to cover the various risks that may be involved such as the type of property, its location, exposure to natural calamities etc. to name a few. Insurance also need to be updated with the changes in conditions.
Property management of a construction project: During the construction of a new project the builders needs to plan their inventory and keep control of their stocks irrespective of the size of the project. Stock control starts from buying goods to using and maintaining them, and also reusing or reordering as required. Quality of the stock also plays a vital role in real estate business. To maintained quality several techniques are adapted. Just in time technique (where items are ordered when necessary and used immediately), minimum stock level technique and stock review technique.
Contractors play an important role in success of a construction project. They are responsible for recruitment and supervision of employees working on the project. Contractors are also responsible for material management coordinating with suppliers thus acquiring necessary goods in time for the construction phases. Poor response from the contractors or failure to perform their duties will delay the project and overshoot budgets.
Legislation compliance: Often a property holder has to disclose his personal and financial information to third party. Protecting information plays a key issue in this business. Once all the parties are ready to proceed it is necessary to have a privacy act is in place so that all information is secure. The corporation act provides the guidelines for conflicts or issues arising in construction or maintenance of a property. There are several agencies that provide comprehensive legal services to better understand the litigations involved. Anti-discrimination law and disability service act also play an important role in real-estate. Property owners are liable for any discriminatory acts.
Occupational health and safety (OH&S) also arises in real-estate and a number of OH&S compliance officers are usually assigned to monitor the safety and health; for example, conditions provided to the workers at construction sites. OH&S officer duties include inspecting construction sites and providing support to internal clients. It is important to report any hazard or incident and all incidents should be attended to and documented for future reference.
Corporate governance: Corporate governance plays an important role in risk management in the real estate industry. It is important to properly align the ideas, interests and decisions of managers to the interests of both internal and external shareholders. For example, failure to recruit appropriate personnel may lead to conflicts of interest. If the conflicts are not managed effectively they may have a substantial impact on the company bottom line. It is required and expected of the managements or boards of construction companies always carefully analyze performance in terms of the market so that they are able to keep track of their company’s performance and progress in a dynamic environment. It is also expected that the managements re-inspect and update their policies and procedures to meet the market trends and demands of all concerned stakeholders.
Housing management: A holistic management of the investment made in real estate can be defined as housing management. Housing management includes keeping track of maintenance and financial arrangements. As a common and popular practice the management of an investment property is outsourced to property management companies who appoint property managers to manage and oversee duties as required. Property managers on a daily basis are responsible for taking maintenance requests, collecting rent, dues or other fees and are responsible for the overall upkeep of the property. They also perform routine property inspections and organize inspections for the owners. Poor performance of the property managers leads to more grievances for the tenants as well as the owners.
1.4.2. External risk
External risk depends on a number of factors such as economic risk, funding, regulation, environment, reputation, competition, partnerships and natural disasters ( Figure 2 .6). Each of the factors noted are discussed briefly in turn.

Eternal risks Source: adapted from Sheryl V and Adam W, 2008
Funding: The availability of funding depends on a number of aspects such as the economic situation in general, market performance, and credit based upon any future cash flow. Some factors that influence economic performance are: change in political regime, rise in the price of raw materials, emergence of a new competitor and disruptions in production process. Market performance usually depends on changes in interest rates, changes in laws, and political and financial market factors. The risk of loss of principal or loss of a financial reward stemming from a borrower's failure to repay a loan or otherwise meet a contractual obligation falls under the funding risk. It is important to take into consideration as many of the previously mentioned factors while undertaking an investment decision, even when one already has an investment portfolio. Investors often anticipate future cash flow situations while borrowing money to pay a current debt. The failure of the anticipated cash flow leads to credit risk. However credit risk can be considered less likely since most often the investors are compensated by way of interest payments made by the borrower in end.
Regulatory environment: Investors in real estate projects should be aware of the local, state and federal laws and regulations. These laws depend on economic, credit and market risk as explained above. Failure to comply with the rules and regulation often leads to delays or in the worst case - complete scrapping of the project; all of which may lead to a complete or partial loss of capital invested.
Reputation: The reputation of a project developer often attracts investor attention and also provides favorable environment for investments. Joint ventures and partnerships are possible if the reputations are well known and have been built over time - providing partners the opportunities to win potentially new clients and investors, as well greater opportunities for new investments. An investor has to study the “people” perception of the organization and the credit history and rating of the project developer. An investment made into a company with poor credit history may end up losses of the principle amount invested. It could also be wise for an investor to know the value of the tangible and intangible assets and the market value of the organization into which an investment is being planned.
Competition: Property market plays an important role in the economy. There are several players in the market who usually try to attract investors. While a healthy competition is good for growth in the industry, it is important for the investors to research exactly what they are being offered because the agents often utilize high pressure selling strategies to gain client’s cash. It is possible that in the process the investors may receive inappropriate financial advice. For example, consumers may not be aware of non-disclosed information pertaining to advice they receive.
Partnership: Partnership plays an important role in investing, as it reduces the impact of potential risk on the individual or company investment. For an investor to be successful in a real-estate partnership it is important to know the partner well and therefore trust plays a vital role. The role of each partner does need to be well defined and documented. Having a clear legal document will protect the interest of all partners. It also important to plan and document an exit strategy for all involved, because personal situations may change over time. Clearly, before a partnership agreement is made it is necessary to conduct a detail research to become self-confident about the deal.
Natural disasters: In the real real-estate market, location plays an important factor in the investment decision. A property purchased at an appropriate location is expected to provide a good return on the investment. One of the main factors affecting location is the potential exposure to natural calamities such as bushfires, floods, sea level raise and erosion to name a few. If the location has a history or is likely to be exposed to a natural disaster it can be expected that the property prices will eventually be exposed to the risk. Therefore, it is wise to not be enticed into such toxic locations. Other factors that need to be accounted for are the costs of maintenance of properties and the nature and level of insurance required for risky locations, if chosen.
1.5. Risk and reward
The nature of risk definition and management process is such that it should be integrated into “the philosophies, practices and business plans” of any individual investor or large organization’s culture (Hillson [ 5 ], p.240). It is certain that there are many risks involved in real-estate market as mentioned. While real-estate provides variety of investment options every investor has to find their comfort level upon taking risks involved. It is not easy to decide if a selected property for investment is appropriate, but the decision should be made based on the consideration of all the factors discussed earlier. In the end however, the willingness to take risks largely depends upon individual preferences and circumstances.
The elements that usually determine the scale of risk or reward are the amount of money that is invested, length of time investment, rate of return or property appreciation, depreciation, fees, taxes, inflation etc. While it is natural for the individual and organizations to invest and expect returns it is important the investors make the informed choice to reduce the odds of losing the principle invested. The potential risks and rewards in investing in the Australian real estate market are investigated next.
2. Real estate scenario in Australia
The speculation about Australian housing market has been intense since 2003. First it was the international monitory fund (IMF) which warned of the housing bubble in Australia “would bust” [ 15 ]. In mid-2008, IMF stated that the Australian property market was overvalued by about 25% [ 16 ]. In more recent times (April 2010), “The Economist” house price indicators estimated Australian house prices were the most overpriced in the world (56.1% overpriced - against long-run average of price to rents ratio) [ 17 ]. The US based analysts Jeremy Grantham (Boston-based hedge fund GMO analysts co-founder) and Heather Hagerty (Fidelity Investments), were also speculating whether or not the Australian residential market is experienced a housing bubble, after the US housing crisis. According to Edward Chancellor [ 18 ], a US-based investment strategist and financial author, Australia was "in the midst of an unsustainable housing bubble that could burst at any time" and the "house prices are more than 50% above their fair value - a once in 40-year event." (p.1). In 2011 Morgan Stanley’s global strategist Gerard Minack said that "we've had 20 years where the Australian consumers have been willing to borrow more to buy an asset that they believe always goes up in value. The classic sign of an asset bubble." and that "home prices are 30 to 40% above fair value [p.1, 19].
The house price-to-income ratio has been the main focus in Australia. The house price-to-income ratio is comparatively high when compared to other countries. Also, the price-to-income ratio in Australia since has been more than 40% higher than the long term average. In the next sections a discussion of the fundamentals that govern the house prices in Australian residential housing market is examined. Also, the potential risks and rewards to the investors are explored in terms of the risk analysis framework presented earlier.
2.1. Introduction: How Australian real estate compares to the rest of the world.
Since the U.S. housing crisis, analysts have been speculating about the potential housing bubble in the Australian residential property market. A report by Real Estate Institute of Australia (REIA) argued that analysts primarily focused their attention on the higher house price-to-income ratio in Australia as compared to other countries (REIA 2010). Moreover, it is observed that the house price-to-income ratio levels are at levels that are similar to that in the US before the housing market there crashed in 2008. The raise in the price-to-income ratio in Australia since 2003 by over 40% higher than the long term average adds fuels the speculation. However, it is important to analyze the fundamentals that govern Australian residential market price growth against the rest of world.
2.1.1. Some aspects of the residential finance system in the U.S. and Australia
In the US, the residential finance system played a significant role in the housing bubble of 2008. The regulation, residential finance institutional arrangements, and mortgage characteristics aided the excessive demand for housing finance. Housing finance was available and offered to borrowers with poor borrowing capacities. Consequently, excessive borrowing led to the housing bubble and the collapse of the financial system in the U.S in 2008. There are some fundamental differences in the lending practice in Australia when compared to the US [ 21 ].
In Australia the lending process is highly regulated by the institutional arrangement. The lending practices enforce the regulatory provisions on financial institutions forcing them to avoid excessive risk taking behavior. Table 2 outlines the characteristics of housing loans both in the U.S and in Australia. The table highlights the systemic susceptibility to riskier mortgages in the US and that availability of such funds to finance the mortgages were more common than in Australia.
| Regulation is high on mortgage loans | No full recourse of mortgages |
| No negative amortisation of loans | yes |
| Securitization is low in housing finance | Securitization is high in housing finance |
| Non-conforming loans | Subprime loans |
| Full recourse of mortgages | No full recourse of mortgages |
Mortgage characteristics of Australia as compared to US
In the US, the non-conforming housing loans represent 13% compared to 1% in Australia [ 21 ]. Negative amortization loans are common in the US but no such loans existed in Australia at the time of the crisis. In Australia the mortgages are “full recourse” lenders and hence the incentive that is offered to households to take out loans they cannot repay is reduced. This is also deters financial institutions from offering risky loans. These primary differences stand out to support and contribute to a relatively strong performance of the housing loans in Australia when compared to the US. It is important to note that the share of non-performing loans in Australia were less than 1.5% even during the financial crisis.
Another fundamental difference is that there is no government sponsored enterprise (GSE) in Australia while they exist in the US. The GSE in the US holds a guarantee of the loans that are offered. This potentially provides an impression that bad loans offered to borrowers with poor repayment capacity would be covered by the Federal Government [ 23 ]. This is not so in Australia where commercial banks provide 90% of all housing loans. The commercial banks are mainly funded by the bank deposits, short term and long-term wholesale debt [ 24 ]. The absence of the so called Federal guarantee restricts Australian banks from any excessive risk taking behavior. In 2007, at the beginning of the financial crisis, GSE’s possessed 90% of these securities. The shadow banking system in which the financial institutions have a greater participation and the GSE’s can be said to have led the excessive risk taking behavior and practices in the US [ 21 ]. In addition, according to the RBA [ 21 ], the regulation level of financial institutions in Australia is about 80% while in the US only 50% of all the financial institutions are regulated [ 21 ].

Non-performing housing loans Source: Real estate Institute of Housing America
The Loan to Value Ratio (LVR) refers to the amount of money borrowed against the total value of the property in a home equity loan. For example, a $50,000 loan against a home worth $200,000 has a Loan to Value Ratio of 25%. In Australia, loans with an LVR exceeding 80% require mortgage insurance - the risk of the borrower defaulting is far too great for the lender. The value of the property is determined by the lender and is often significantly less than the purchase price, which often surprise first-time borrowers. Typically, the amount that lenders have been prepared to lend for housing has been restricted by one or both of the following:
scheduled repayments should not exceed some fixed share of the borrower’s income – the repayment-to-income, or serviceability, constraint; and
the loan should not exceed a certain proportion, most commonly 80% [ 21 ] of the property’s purchase price – the LVR constraint.
2.2. Australian real estate market compared to the rest of the world
The analysis presented in the previous section shows that Australia is fundamentally different to the US when it comes to the residential housing market. But, how does Australia compare to the other countries in the world? New research conducted by Lloyds TSB [ 27 ] - International Global Housing Market Review, shows that Australia just made it into the top 10 list of countries with the highest house price increases over the past decade ( Table 3) . Four of the six top performing housing markets since 2001 were in the emerging economies of the world. India with a booming real estate market tops the list - house prices rise by 284% over the last decade; Russia coming second - house price increase of 209% over the same period. China faired only marginally when compared to other major economies - ranked 14th with a 47% growth rate since 2001.
| 8.7 | 284 | 14.4 | |
| -24.3 | 209 | 12 | |
| -1.1 | 161 | 10.1 | |
| -1.3 | 143 | 9.3 | |
| 13.6 | 125 | 8.4 | |
| -10 | 106 | 7.5 | |
| 4.3 | 82 | 6.2 | |
| -2.1 | 79 | 6 | |
| 6.9 | 72 | 5.5 | |
| 0.4 | 69 | 5.4 |
Real house price changes – A global comparison.
According to the findings of the report Australian house prices increased by 76% and had the ninth fastest growing house prices during 2001-2011. During the same period house price declines were seen in the world’s largest economies such as Germany, Japan and the United States. Japan registered the largest house prices fall of 30%, while house prices in Germany and US were down 17% and 2% respectively during the same time. Other major findings of the research include:
housing markets have typically risen fastest in countries with the fastest growing economies. On average, the countries with the biggest rises in house prices since 2001 have seen GDP increase by more than 100%. Countries that had large rises in pre-crisis times lost the most after the GFC affected their economies; and
house prices within countries that form part of the Euro have climbed an average of 23 percent since 2001. France saw the largest increase with 82%, Belgium rose 69%, Spain 26% and Italy was up 31%. But Spain has seen a major decline in 2012.
The performance of the established house prices in Australian housing market provided by the Australian Bureau of Statistics (ABS) is presented in Figure 8 . The Australian housing over the past five years has seen some corrections. The period can be divided into pre-global financial crisis (GFC), during GFC and post GFC. Prior to GFC, there has been a considerable growth in the established housing prices. This growth pattern however changed course and reached the worst levels in August 2008 when the GFC was setting in. However, the prices of established homes climbed steeply during the peak of the GFC when markets around the world were playing havoc. This defiance could be mainly attributed to the management initiatives taken by the RBA [ 21 ] and government of Australia. The RBA drastically reduced the interest rates to a record low of 3.25% supported by the federal government incentives such as economic stimulus plan, which included substantial increase in first home grants among others.
This financial incentive was “too good to miss” for anyone considering their first home purchase. This led to flood of first home buyers entering the market that drove the prices up against all odds. Since the time the incentives have been wound back, and the market and investor sentiment took over. This led to a fall in the growth when compared to the preceding three years and has been mostly in the low sentiment in the past two years. Therefore, although Australian market prices are influenced by the global events, a collapse similar to that seen in markets elsewhere seems appears a distant possibility. This can be attributed to the underlying government incentives to manage the risks during the crisis. Other micro-economics aspects also helped manage the downturn.
2.6. Australian house prices and the fundamental influences
Australian housing demand has been strong and can be also attributed to the following:
strong overseas migration from 2004 to 2007;
housing shortages due to a rapidly growing population;
Australian household sizes are shrinking;
lending standards stricter than most advanced economies including the US; and
interest rates at record lows.

Australian annual house price change in the last decade
2.6.1. Trend of net population increase and net overseas migration increase
House prices have been underpinned by a chronic housing shortage in Australia. This was brought about by an ever increasing population and constraints placed on housing supply over time. Figure 9 shows the increase in population growth from both natural growth and migration since 2006. From 2006 to September 2010 natural population growth has only seen a marginal increase, but during the same period the net overseas migration growth has been substantial.

Trend of natural population increase and net overseas migration
Figure 10 shows that there has been an increase in the total population by about 1.6 million people 2006–2010. During the same period, the Net Overseas Migration (NOM) accounted for 1.02 million people compared to only 600 000 increase in natural population. However, given that there has been a large influx of people into Australia, the question was whether there was enough housing infrastructure in place.

Net overseas migration and components of population change
2.7. Trend in the number of dwellings commenced and population
Figure 11 shows the trend in the population and dwellings commenced from January 2007 to October 2010. As shown earlier, the population growth showed an upward trend over the entire period. The number of dwellings commenced shows a rather distressing trend. Figure 11 shows the commencement of new dwellings significantly fell short and did not keep pace with the rapid growth in population. For an addition of 1.25 million people during this period only about 235 000 new homes were built demonstrating a significant shortage in the housing market. Interestingly, this situation presents a case for more property investment as people search for a place to live.
2.8. Demand and supply scenario
Historically, Australia has been behind in the demand versus supply of residential dwellings, but more so in the last decade than any time earlier. Figure 12 shows the dwelling gap in the previous decade. Australia continues to run large annual deficits in housing supply - the underlying demand for dwellings and the completion of dwellings has not matched. In view of this it can be expected that in the longer term Australia’s housing market is underpinned by insufficient supply in addition to robust underlying demand.

Trend in the number of dwellings commenced and population

Estimated dwelling gap in the last decade
National housing supply council (NHSC) estimates a demand versus supply gap of approximately 640 000 houses in 2030; and an increase in the gap from 250 000 in 2012. Figure 13 shows the projections in the supply gap to 2030. The figure shows an increase over time till 2015, and indeed a higher rate of increase predicted from 2015 till 2030.

Supply and demand gap projections to 2030
To examine whether the situation is the same throughout Australia or mainly confined to a few states, data from all the states are explored in more depth. Figure 12 and Figure 14 both show that not all states have an acute shortage of housing such as South Australia (SA), Tasmania (Tas) and Australian Commonwealth Territory (ACT). Their data runs against the trend for the last decade but more so during 2009-2010. The larger states of New South Wales (NSW), Victoria (Vic), Queensland (Qld) and Western Australia (WA) all continue to have high deficits year after year and the deficit is increasing – however, Victoria being an exception in 2009-2010 where it managed to go against the trend temporarily ( Figure 14) . To further understand the nature of the differences between states, the net population increase in the demand across states needs to be compared. Figure 15 shows the state by state net change in population as well as housing issues. The states with a high influx of population showed higher dwelling demand.
Not surprisingly, the high demand has led to a rather strong rental market particularly in the larger states and this has provided an impetus for higher rental returns and an ideal time for new investors to consider for the longer term. With recent housing approvals declining, this demand supply gap can only be expected to widen. Clearly, the population increase cannot only be driving the market. Therefore, other aspects need investigation such as house price to income ratio; and house hold debt to income ratio.

Housing demand and supply by states

Net population change - state by state over 2000-2011
2.9. House price-to-income ratio
The house price-to-income ratio is generally calculated using average income of the whole population. This method of calculating house price may not be appropriate in that a set of buyers whose incomes are above the average income of the wider population, and have the ability to service the loans tend to bid in the auctions there by inflating house prices [ 28 ]. Such competition is visible across all capital cities but more so in Sydney, Melbourne, Perth and Canberra than other cities. Figure 16 shows the median change in the house prices across eight capital cities since 2007.
Figure 16 shows that the increase in house prices in the major capital cities have been greater than those of other cities. This suggests the increase in house prices in Australia over the past five years was driven mostly by house prices in the most expensive cities, where home buyers tend to be higher income earners. The house price-to-income ratio does not seem to pick up the distributional differences. The household debt to disposable income ratio can provide valuable insights while assessing the vulnerabilities. Therefore, disposable incomes of people need to be considered when assessing the vulnerability of an average mum and dad investor.

Dwelling prices in capital cities in Australia Source: ABS
2.10. Owner- Occupier debt
Figure 17 shows the distribution of debt to income since 2006. The data indicates that the debt to income ratios has been fairly high – but consistent around 160% for the total debt, of which close to 140% is towards the mortgage. An indication to the scale of vulnerability can become salient when the house hold income to debt and the annual change in established home price are compared. Figure 18 shows that there has been a somewhat volatile situation in the housing market in all capital cities during 2006-2011; yet, during the same period, the debt to income ratio seem to be approximately constant over time. The comparison shows the average households are not so vulnerable to at least a change in their income situation given there was volatility in house price changes over time.

Owner occupier debt Source: RBA

Annual change in established home prices Source: ABS
3. Conclusion
The aim of this paper was to define risk and risk management in terms of real estate investment thus demonstrating the in depth nature and complexity of the process. Another aim was to conduct risk analysis of the Australian real estate market in particular, in terms of the global financial crisis – pre GFC, during GFC and post GFC. The review shows that risk analysis involves a number of steps with each step in turn involving another set of procedures. Risk analysis is a process that it is often ignored by investors particularly by the individual or smaller investors who tend to be more vulnerable. Similarly, risk management involves a number of processes and stages with steps and these have been outlined in the paper. A risk analysis is conducted here for investors in Australia real estate market. The results are rather interesting in that several conditional differences exist between Australia and the rest of the world. The factors identified that influence Australia’s house price are different from the rest of the world; including for example the rather stricter and well regulated lending practices of Australia’s financial institutions. A tight financial system regulation in Australia means a highly disciplined financial sector. The tougher regulation of the industry therefore prevents financial institutions from taking on excessive risks, contrary to the US counterparts. In fact, increasing house prices was identified in Australia after the crises of 2007-8; and this was associated with the changes in mortgage lending rates, rising family income, increasing overseas migration demand, government incentives to name a few. Together the market situation suggests that Australia is unlikely to face a US style housing bubble. The results of the risk analysis show that:
rising incomes and population growth ensure the demand for housing outpaces current supply, thereby increasing the prices;
high capital growth in larger cities where there has been large population migration such as Perth, Sydney and Melbourne;
high demand still exists for residential and commercial real estate to accommodate growing expatriate working community;
increased property prices has to many Australians increasingly seeking rental accommodation, making housing investment a healthy growth area for investors;
higher growth rate in property investment in Australia - superior to most OECD countries, including the UK, Spain and the US; and
foreign exchange rate changes have been favorable, making property purchase in Australia a valuable option; that in turn driving property prices higher. This has changed in 2011-12 when the higher Australian dollar has posed interesting challenges for the Australian investments.
The findings are in line and relate to that of the Australian housing and urban research institute’s findings [ 29 ], which further suggest:
investors are motivated to invest in the private rental market for a number of reasons such as financial factors, personal goals (retirement or future home for children at university), and household circumstances (proximity to their own dwelling);
investors use their own measures of quality and personal preference when selecting a dwelling even though they will not be living in the property;
investors perceive property as a long-term, safe and stable investment that is low risk and will produce guaranteed returns;
investors largely expect capital gains from investing rather that rental yield only and this is how success is measured; and
informality characterizes investor approaches to the housing market where property is considered familiar, relatively easy to invest in when compared to other investments.
In summary, Australian housing industry continues to experience significant housing shortages in major cities due to a rapidly growing population; in particular, the growth has been fueled by strong overseas migration during 2004-2007, but the Australian current government immigration laws suggest that the strong levels of immigration will continue for some time due to the lack of skills in the labor market. The housing demand is further supported by the fact that the size of the Australian household appears to be shrinking adding to the pressure on housing both in rental and investment. The demand of rental housing together with somewhat lower house prices in recent times (buyer marker) has lured many new investors in the market. This aspect, the negative gearing benefits, and the first home ownership schemes supported by significantly lower interest rates have all led to a favorable and stronger real estate market in Australia. All of this has occurred within a framework of a stronger, tightly regulated financial sector that has been more-stricter than most advanced economies including the US. Such a regulated real estate market appears to have kept the mortgage repayment failure and housing related bad debts at a minimum in Australia.
- 2. Standards Australia/Standards New Zealand. AS/NZS Risk management. 3rd ed. Sydney: Standards Australia International Ltd and Standards New Zealand. 2004
- 3. International Standard Organization. Guide 73: Risk management- Vocabulary. 2009 cited 2012 March 4] [about 24 screens] Available from: http://pqm-online.com/assets/files/standards/iso_iec_guide_ 73 2009 .pdf
- 4. Comcover Insurance & Risk Management. The Introduction of AS/NZS/ISO 31000 2009 2009 Risk Management Principles and Guidelines. 32 cited 2012 March 17] [about 2 screens] Available from: http://finance.gov.au/comcover/docs/IB_Issue32_Oct09.pdf
- 9. ACT Insurance Authority. Guide to Risk Management. 2004 February; [cited 2012 March 10] [about 10 screens] Available from: http://treasury.act.gov.au/actia/guide.doc
- 16. http://pandora.nla.gov.au/pan/105045/20090903-1455/www.nchf.org.au/downloads/risk_management_summary.pdf
- 18. ABC [homepage on the internet]. ABC Materials; [updated 2003 Apr 13; cited 2012 March 8]. IMF predicts Australia housing bust; [about 3 screens]. Available from: http://abc.net.au/news/2003-04-13/imf-predicts-aust-housing-bust/1835644
- 19. Smart Company [homepage on the internet]. Smart Company.com.au Pty Ltd; [updated 2008 Apr 4; cited 2012 February 28]. Australian property bubble could be about to burst: IMF; [about 3 screens]. Available from: http://smartcompany.com.au/
- 20. The Economist [homepage on the internet]. London: The Economist Newspaper Ltd; [updated 2010 Apr 15; cited 2012 March 25].You can’t keep ‘em down; [about 3 screens]. Available from: http://economist.com/node/15911113?story_id=15911113
- 21. The Australian [homepage on the internet]. News Pty Ltd [updated 2010 May 3; cited 2012 March 15]. Housing tipped for price implosion; [about 4 screens]. Available from: http://theaustralian.com.au/archive/business-old/housing-tipped-for-price-implosion/story-e6frg9gx-1225861304871?from=public_rss
- 22. ABC [homepage on the internet]. ABC Materials [updated 2011 Mar 11; cited 2012 March 8]. Australian house prices 56 per cent over valued: The Economist; Available from: http://abc.net.au/pm/content/2011/s3155728.htm
- 23. Real Estate Institute of Australia. Australian house prices: bursting the bubble myth. 2010 cited 2012 April 5]. Available from: http://reia.com.au/search-result.php
- 24. Reserve Bank of Australia [homepage on the Internet]. Reserve Bank of Australia C 2001 2012 cited 2012 March 7]. Available from: http://rba.gov.au/
- 25. Research Institute of Housing America [homepage on the Internet]. Washington: mortgage bankers association; c 2008 2012 updated 2011 March 30; cited 2012 March 12]. Available from: http://housingamerica.org/default.htm
- 28. Reserve Bank of Australia. Financial Stability Review. 2010 September 29.
- 29. Reserve Bank of Australia. Recent Developments in Margin Lending in Australia. Bulletin. 2009 December: 11 17
- 30. Lloyds banking group [homepage on the internet]. Lloyds banking group plc [cited 2012 March 15]. Emerging markets top global house price league over the past decade. Available from: http://lloydsbankinggroup.com/media/pdfs/LTSB/2012/1703_global.pdf
- 31. OECD. Recent house price developments: the role of fundamentals. OECD economic outlook. 2006 Jan 19; 2005 2 123 154
© 2012 The Author(s). Licensee IntechOpen. This chapter is distributed under the terms of the Creative Commons Attribution 3.0 License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.
Continue reading from the same book
Risk management.
Published: 12 September 2012
By Jordi Botet
7126 downloads
By Pedro Maria-Sanchez
7252 downloads
By Nerija Banaitiene and Audrius Banaitis
105163 downloads
IntechOpen Author/Editor? To get your discount, log in .
Discounts available on purchase of multiple copies. View rates
Local taxes (VAT) are calculated in later steps, if applicable.

Table of Contents
Understanding project risk management, definition and explanation of project risk management, 4 key components of project risk management, risk identification, risk assessment, risk response planning, risk monitoring and control, 5 project risk management case studies, gordie howe international bridge project, fujitsu’s early-career project managers, vodafone’s complex technology project, fehmarnbelt project, lend lease project, project risk management at designveloper, how we manage project risks, advancements in project risk management, project risk management: 5 case studies you should not miss.
May 21, 2024

Exploring project risk management, one can see how vital it is in today’s business world. This article from Designveloper, “Project Risk Management: 5 Case Studies You Should Not Miss”, exists in order to shed light on this important component of project management.
We’ll reference some new numbers and facts that highlight the significance of risk management in projects. These data points are based on legit reports and will help create a good basis of understanding on the subject matter.
In addition, we will discuss specific case studies when risk management was successfully applied and when it was not applied in project management. These real world examples are very much important for project managers and teams.
It is also important to keep in mind that each project has associated risks. However through project risk management these risks can be identified, analyzed, prioritized and managed in order to make the project achieve its objectives. Well then, let’s take this journey of understanding together. Watch out for an analysis of the five case studies you must not miss.
Risk management is a very critical component of any project. Risk management is a set of tools that allow determining the potential threats to the success of a project and how to address them. Let’s look at some more recent stats and examples to understand this better.

Statistics show that as high as 70% of all projects are unsuccessful . This high failure rate highlights the need for efficient project risk management. Surprisingly, organizations that do not attach much importance to project risk management face 50% chances of their project failure. This results in huge losses of money and untapped business potential.
Additionally, poor performance leads to approximated 10% loss of every dollar spent on projects. This translates to a loss of $99 for every $1 billion invested. These statistics demonstrate the importance of project risk management in improving project success rates and minimizing waste.
Let us consider a project management example to demonstrate the relevance of the issue discussed above. Consider a new refinery being constructed in the Middle East. The project is entering a key phase: purchasing. Poor risk management could see important decisions surrounding procurement strategy, or the timing of the tendering process result in project failure.
Project risk management in itself is a process that entails the identification of potential threats and their mitigation. It is not reactionary but proactive.
This process begins with the identification of potential risks. These could be any time from budget overruns to delayed deliveries. After the risks are identified they are then analyzed. This involves estimating the probability of each risk event and the potential consequences to the project.
The next stage is risk response planning. This could be in the form of risk reduction, risk shifting or risk acceptance. The goal here is to reduce the impact of risks on the project.
Finally, the process entails identifying and tracking these risks throughout the life of a project. This helps in keeping the project on course and any new risks that might arise are identified and managed.
Let’s dive into the heart of project risk management: its four key components. These pillars form the foundation of any successful risk management strategy. They are risk identification, risk analysis, risk response planning, and risk monitoring and control. Each plays a crucial role in ensuring project success. This section will provide a detailed explanation of each component, backed by data and real-world examples. So, let’s embark on this journey to understand the four key components of project risk management.
Risk identification is the first process in a project risk management process. It’s about proactively identifying risks that might cause a project to fail. This is very important because a recent study has shown that 77% of companies had operational surprises due to unidentified risks.
There are different approaches to risk identification such as brainstorming, Delphi technique, SWOT analysis, checklist analysis, flowchart. These techniques assist project teams in identifying all potential risks.
Risk identification is the second stage of the project risk management process. It is a systematic approach that tries to determine the probability of occurrence and severity of identified risks. This step is very important; it helps to rank the identified risks and assists in the formation of risk response strategies.
Risk assessment involves two key elements: frequency and severity of occurrence. As for risk probability, it estimates the chances of a risk event taking place, and risk impact measures the impact associated with the risk event.
This is the third component of project risk management. It deals with planning the best ways to deal with the risks that have been identified. This step is important since it ensures that the risk does not have a substantial effect on the project.
One of the statistics stated that nearly three-quarters of organizations have an incident response plan and 63 percent of these organizations conduct the plan regularly. This explains why focusing only on risks’ identification and analysis without a plan of action is inadequate.
Risk response planning involves four key strategies: risk acceptance, risk sharing, risk reduction, and risk elimination. Each strategy is selected depending on the nature and potential of the risk.
Risk monitoring and control is the last step of project risk management. It’s about monitoring and controlling the identified risks and making sure that they are being addressed according to the plan.
Furthermore, risk control and management involve managing identified risks, monitoring the remaining risk, identifying new risks, implementing risk strategies, and evaluating their implementation during the project life cycle.
It is now high time to approach the practical side of project risk management. This section provides selected five case studies that explain the need and application of project risk management. Each case study gives an individual approach revealing how risk management can facilitate success of the project. Additionally, these case studies include construction projects, technology groups, among other industries. They show how effective project risk management can be, by allowing organizations to respond to uncertainties and successfully accomplish their project objectives. Let us now examine these case studies and understand the concept of risk in project management.
The Gordie Howe International Bridge is one of the projects that demonstrate the principles of project risk management. This is one of the biggest infrastructure projects in North America which includes the construction of a 6 lane bridge at the busiest commercial border crossing point between the U.S. and Canada.

The project scope can be summarized as: New Port of Entry and Inspection facilities for the Canadian and US governments; Tolls Collection Facilities; Projects and modifications to multiple local bridges and roadways. The project is administered via Windsor-Detroit Bridge Authority, a nonprofit Canadian Crown entity.
Specifically, one of the project challenges associated with the fact that the project was a big one in terms of land size and the community of interests involved in the undertaking. Governance and the CI were fundamental aspects that helped the project team to overcome these challenges.
The PMBOK® Guide is the contractual basis for project management of the project agreement. This dedication to following the best practices for project management does not end with bridge construction: It spreads to all other requirements.
However, the project is making steady progress to the objective of finishing the project in 2024. This case study clearly demonstrates the role of project risk management in achieving success with large and complicated infrastructure projects.
Fujitsu is an international company that deals with the provision of a total information and communication technology system as well as its products and services. The typical way was to employ a few college and school leavers and engage them in a two-year manual management training and development course. Nevertheless, this approach failed in terms of the following.

Firstly, the training was not comprehensive in its coverage of project management and was solely concerned with generic messaging – for example, promoting leadership skills and time management. Secondly it was not effectively reaching out to the need of apprentices. Thirdly the two year time frame was not sufficient to allow for a deep approach to the development of the required project management skills for this job. Finally the retention problems of employees in the train program presented a number of issues.
To tackle these issues, Fujitsu UK adopted a framework based on three dimensions: structured learning, learning from others, and rotation. This framework is designed to operate for the first five years of a participant’s career and is underpinned by the 70-20-10 model for learning and development. Rogers’ model acknowledges that most learning occurs on the job.
The initial training process starts with a three-week formal learning and induction program that includes the initial orientation to the organization and its operations, the fundamentals of project management, and business in general. Lastly, the participants are put on a rotational assignment in the PMO of the program for the first six to eight months.
Vodafone is a multinational mobile telecommunications group that manages telecommunications services in 28 countries across five continents and decided to undertake a highly complex technology project to replace an existing network with a fully managed GLAN in 42 locations. This project was much complex and thus a well grounded approach to risk management was needed.

The project team faced a long period of delay in signing the contract and frequent changes after the contract was signed until the project is baselined. These challenges stretched the time frame of the project and enhanced the project complexity.
In order to mitigate the risks, Vodafone employed PMI standards for their project management structure. This approach included conducting workshops, developing resource and risk management plan and tailoring project documentations as well as conducting regular lesson learned.
Like any other project, the Vodafone GLAN project was not an easy one either but it was completed on time and in some cases ahead of the schedule that the team had anticipated to complete the project. At the first stage 90% of migrated sites were successfully migrated at the first attempt and 100% – at second.
The Fehmarnbelt project is a real-life example of the strategic role of project risk management. It provides information about a mega-project to construct the world’s longest immersed tunnel between Germany and Denmark. It will be a four-lane highway and two-rail electrified tunnel extending for 18 kilometers and it will be buried 40 meters under the Baltic Sea.

This project is managed by Femern A/S which is a Danish government-owned company with construction value over more than €7 billion (£8. 2 billion). It is estimated to provide jobs for 3,000 workers directly in addition to 10,000 in the suppliers. Upon its completion, its travel between Denmark and Germany will be cut to 10 minutes by automobile and 7 minutes by rail.
The Femern risk management functions and controls in particular the role of Risk Manager Bo Nygaard Sørensen then initiated the process and developed some clear key strategic objectives for the project. They formulated a simple, dynamic, and comprehensive risk register to give a more complete risk view of the mega-project. They also created a risk index in order to assess all risks in a consistent and predictable manner, classify them according to their importance, and manage and overcome the risks in an appropriate and timely manner.
Predict! is a risk assessment and analysis tool that came in use by the team, which helps determine the effect of various risks on the cost of the construction of the link and to calculate the risk contingency needed for the project. This way they were able to make decisions on whether an immersed tunnel could be constructed instead of a bridge.
Lend Lease is an international property and infrastructure group that operates in over 20 countries in the world; the company offers a better example of managing project risks. The company has established a complex framework called the Global Minimum Requirements (GMRs) to identify risks to which it is exposed.

The GMRs have scope for the phase of the project before a decision to bid for a job is taken. This framework includes factors related to flooding, heat, biodiversity, land or soil subsidence, water, weathering, infrastructure and insurance.
The GMRs are organized into five main phases in line with the five main development stages of a project. These stages guarantee that vital decisions are made at the ideal time. The stages include governance, investment, design and procurement, establishment, and delivery.
For instance, during the design and procurement stage, the GMRs identify requisite design controls that will prevent environment degradation during design as well as fatal risk elimination during planning and procurement. This approach aids in effective management of risks and delivery of successful projects in Lend Lease.
Let’s take a closer look at what risk management strategies are used here at Designveloper – a top web & software development firm in Vietnam. We also provide a range of other services, so it is essential that we manage risks on all our projects in similar and effective ways. The following part of the paper will try to give a glimpse of how we manage project risk in an exemplary manner using research from recent years and include specific cases.
The following steps explain the risk management process that we use—from the identification of potential risks to managing them: Discovering the risks. We will also mention here how our experience and expertise has helped us in this area.
Risk management as a function in project delivery is well comprehended at Designveloper. Our method of managing the project risk is proactive and systematic, which enables us to predict possible problems and create successful solutions to overcome them.
One of the problems we frequently encounter is the comprehension of our clients’ needs. In most cases, clients come to us with a basic idea or concept. To convert these ideas into particular requirements and feature lists, the business analysts of our company have to collaborate with the client. The whole process is often a time-waster, and having a chance is missed.
To solve this problem, we’ve created a library of features with their own time and cost estimate. This library is based on data of previous projects that we have documented, arranged, and consolidated. At the present time when a client approaches us with a request, we can search for similar features in our library and give an initial quote. This method has considerably cut the period of providing the first estimations to our clients and saving the time for all participants.
This is only one of the techniques we use to mitigate project risks at Designveloper. The focus on effective project risk management has been contributing significantly to our successful operation as a leading company in web and software development in Vietnam. It is a mindset that enables us to convert challenges into opportunities and provide outstanding results for our clients.
In Designveloper, we always aim at enhancing our project risk management actions. Below are a couple examples of the advancements we’ve made.
To reduce the waiting time, we have adopted continuous deployment. This enables us to provide value fast and effectively. We release a minimum feature rather than a big feature. It helps us to collect the input from our customers and keep on improving. What this translates into for our customers is that they start to derive value from the product quickly and that they have near-continuous improvement rather than have to wait for a “perfect” feature.
We also hold regular “sync-up” meetings between teams to keep the information synchronized and transparent from input (requirements) to output (product). Changes are known to all teams and thus teams can prepare to respond in a flexible and best manner.
Some of these developments in project risk management have enabled us to complete projects successfully, and be of an excellent service to our clients. They show our support of the never-ending improving and our capability to turn threats into opportunities. The strength of Designveloper is largely attributed to the fact that we do not just control project risks – we master them.
To conclude, project risk management is an important element of nearly all successful projects. It is all about identification of possible problems and organization necessary measures that will result in the success of the project. The case studies addressed in this article illustrate the significance and implementation of project risk management in different settings and fields. They show what efficient risk management can result in.
We have witnessed the advantages of solid project risk management at Designveloper. The combination of our approach, powered by our track record and professionalism, has enabled us to complete projects that met all client’s requirements. We are not only managing project risks but rather mastering them.
We trust you have found this article helpful in understanding project risk management and its significance in the fast-changing, complicated project environment of today. However, one needs to mind that proper project management is not only about task and resource management but also risk management. And at Designveloper, our team is there to guide you through those risks and to help you realize your project’s objectives.
Also published on

Share post on

Insights worth keeping. Get them weekly.

Get in touch
Simply register below to receive our weekly newsletters with the newest blog posts
Read more topics

To read this content please select one of the options below:
Please note you do not have access to teaching notes, leadership, governance and the mitigation of risk: a case study.
Managerial Auditing Journal
ISSN : 0268-6902
Article publication date: 2 February 2015
The purpose of this study is to examine how managers in financial institutions satisfy themselves of the effectiveness of risk mitigation strategy and management control. It studies the co-opting of accounting tools within a single financial institution case study, examining the recursive and emergent characteristics of risk management practice.
Design/methodology/approach
Adopting a field study approach within the strategy-as-practice perspective, the paper provides insights into the role of actor perceptions of risk and accounting as a calculative practice in the adaptive enactment of risk strategy.
Results highlight the interactions between risk management strategy, management controls and actor interests at Lehman Brothers. The actions and reactions of risk management decision-makers such as Executive Committee and Board members are examined to better understand the role of accounting and leadership.
Research limitations/implications
Results of this study may not be generalised beyond this single case study.
Practical implications
The paper emphasises that concern for the social relations and the performative interests of actors in a risk management network needs to be understood and considered in accounting research. It is argued that the market prices of tradable financial asset will continue to be opaque without these insights.
Originality/value
This study explores an under-researched topic in the accounting literature in examining how management controls are affected by and, in turn, affect risk strategising.
- Financial markets
- Risk management
- Strategy as practice
- Lehman Brothers
- Management control
Rooney, J. and Cuganesan, S. (2015), "Leadership, governance and the mitigation of risk: a case study", Managerial Auditing Journal , Vol. 30 No. 2, pp. 132-159. https://doi.org/10.1108/MAJ-08-2014-1078
Emerald Group Publishing Limited
Copyright © 2015, Emerald Group Publishing Limited
Related articles
All feedback is valuable.
Please share your general feedback
Report an issue or find answers to frequently asked questions
Contact Customer Support
Case Study: Companies Excelling in Risk Management

In this article
In the modern business landscape, navigating uncertainties and pitfalls is essential for sustainable growth and longevity. Effective risk management emerges as a shield against potential threats – and it also unlocks opportunities for innovation and advancement. In this article, we will explore risk management and its significance and criteria for excellence. We will also examine case studies of two companies that have excelled in this domain. Through these insights, we aim to glean valuable lessons and best practices. As such, businesses across diverse industries can fortify their risk management frameworks.
The Significance of Risk Management
Risk management is vital for the sustenance and prosperity of companies, regardless of their size or industry. At its core, it is the identification, assessment and mitigation of potential risks that may impede organisational objectives or lead to adverse outcomes. Having a robust risk management approach means businesses can safeguard their assets, reputation and bottom line.
The statistics are somewhat alarming. According to research , 69% of executives are not confident with their current risk management policies and practices. What’s more, only 36% of organisations have a formal enterprise risk management (ERM) programme.
Proactive risk management isn’t just a defensive measure; rather, it is necessary for sustainability and growth. With 62% of organisations experiencing a critical risk event in the last three years, it is important to be proactive. By identifying and addressing potential risks, organisations can become more resilient to external shocks and internal disruptions. This means they’re better able to survive through difficult times and maintain operational continuity. Moreover, a proactive stance enables companies to seize strategic advantages. It allows them to innovate, expand into new markets and capitalise on emerging trends with confidence.

Criteria for Excellence in Risk Management
Achieving excellence in risk management means adhering to several key criteria:
- Ability to Identify Risks: Exceptional risk management begins with identifying potential risks comprehensively. This involves a thorough understanding of both internal and external factors that could impact the organisation. It includes market volatility, regulatory changes, cybersecurity threats and operational vulnerabilities.
- Assessment of Risks: Once identified, risks must be assessed to gauge their potential impact and likelihood of occurrence. This involves using risk assessment methodologies like quantitative analysis, scenario planning and risk heat mapping, to prioritise risks based on their severity and urgency.
- Mitigation Strategies and Control Measures: Effective risk management relies on proactive mitigation strategies to minimise the likelihood of risk occurrence and mitigate its potential impact. This may involve implementing control measures, diversifying risk exposure, investing in risk transfer mechanisms such as insurance and enhancing resilience through business continuity planning.
- Adaptability to Change: Organisations need to be ready to adapt to emerging risks and changing circumstances. This requires a culture of continuous learning and improvement. This means lessons are learned from past experiences to enhance risk management practices and anticipate future challenges.
- Leadership Commitment: Effective leaders demonstrate a clear understanding of the importance of risk management. They know how to allocate adequate resources, support and incentives to prioritise risk management initiatives.
- Strong Risk Culture: A strong risk culture permeates every level of the organisation. This involves a mindset where risk management is viewed as everyone’s responsibility.
- Robust Risk Management Frameworks: Finally, excellence in risk management requires robust frameworks and processes to guide risk identification, assessment and mitigation efforts. This includes defining clear roles and responsibilities, implementing effective governance structures and leveraging technology and data analytics to enhance risk visibility and decision-making.
Company A: Case Study in Risk Management Excellence
Now, let’s take a look at a case study that highlights risk management excellence in practice.
ApexTech Solutions is a company known for its exemplary risk management practices. Founded in 2005 by visionary entrepreneur Sarah Lawson, ApexTech began as a small start-up in the tech industry. It specialises in software development and IT consulting services.
Over the years, under Lawson’s leadership, the company expanded its offerings and diversified into various sectors, including cybersecurity solutions, cloud computing and artificial intelligence. Today, ApexTech is a prominent player in the global technology market, serving clients ranging from small businesses to Fortune 500 companies.
Risk management strategies and successes
ApexTech’s journey to risk management excellence can be attributed to several key strategies and initiatives:
- Comprehensive Risk Assessment: ApexTech conducts regular and thorough risk assessments to identify potential threats and vulnerabilities across its operations.
- Investment in Technology and Innovation: ApexTech prioritises investments in cutting-edge technologies such as AI-driven analytics, predictive modelling and threat intelligence solutions.
- Customer-Centric Approach: ApexTech tailors its risk management solutions to meet specific needs and preferences. This fosters trust and long-term partnerships.
- Cybersecurity Measures: ApexTech has made cybersecurity a top priority. The company employs a multi-layered approach to cybersecurity to mitigate the risk of cyberattacks.
- Continual Improvement and Adaptation: ApexTech fosters a culture of continual improvement and adaptation. The company encourages feedback and collaboration among employees at all levels so they can identify areas for improvement and implement solutions to mitigate risks effectively.
By proactively identifying and addressing operational risks, such as supply chain disruptions and regulatory compliance challenges, ApexTech has maintained operational continuity and minimised potential disruptions to its business operations.
ApexTech Solutions serves as a compelling example of a company that has excelled in risk management excellence by embracing proactive strategies, leveraging advanced technologies and fostering a culture of innovation and adaptation.
Company B: Case Study in Risk Management Excellence
TerraSafe Pharmaceuticals is a renowned company in the pharmaceutical industry, dedicated to developing and manufacturing innovative medications to improve global health outcomes. Established in 1998 by Dr Elena Chen, TerraSafe initially focused on the production of generic drugs to address critical healthcare needs.
Over the years, the company has expanded its portfolio to include novel biopharmaceuticals and speciality medications.
TerraSafe Pharmaceuticals has a holistic approach to identifying, assessing and mitigating risks across its operations:
- Rigorous Quality Assurance Standards: TerraSafe prioritises stringent quality assurance measures throughout the drug development and manufacturing process. This ensures product safety, efficacy and compliance with regulatory requirements.
- Investment in Research and Development (R&D): TerraSafe allocates significant resources to research and development initiatives. These are aimed at advancing scientific knowledge and discovering breakthrough therapies. With its culture of innovation and collaboration, the company mitigates the risk of product obsolescence.
- Regulatory Compliance and Risk Monitoring: TerraSafe maintains a dedicated regulatory affairs department. This team stays abreast of evolving regulatory requirements and industry standards. They monitor regulatory changes proactively and engage with regulatory authorities to ensure timely compliance with applicable laws and standards. This reduces the risk of non-compliance penalties and legal disputes.
- Supply Chain Resilience: TerraSafe works closely with its suppliers and logistics partners to assess and mitigate supply chain risks like raw material shortages, transportation disruptions and geopolitical instability. It implements contingency planning and diversification of sourcing strategies.
- Focus on Patient Safety and Ethical Practices: The company adheres to stringent ethical guidelines and clinical trial protocols to protect patient welfare and maintain public trust in its products and services.
By investing in R&D and adhering to rigorous quality assurance standards, TerraSafe has successfully developed and commercialised several breakthrough medications that address unmet medical needs and improve patient outcomes. What’s more, the company’s proactive approach to regulatory compliance has facilitated the timely approval and market authorisation of its products in key global markets. This has enabled the company to expand its geographic footprint and reach new patient populations.
Key Takeaways and Best Practices
Despite being in different industries, both companies share similarities. Both ApexTech and TerraSafe Pharmaceuticals know the importance of proactive risk management. They have procedures in place that work to identify, assess and mitigate risks before they escalate. What’s more, both companies are led by visionary leaders who set the tone for decision-making. They prioritise building a strong risk culture with all employees knowing their role in risk management.

Best practices and strategies employed
- Conducting Regular Risk Assessments: Both companies conduct regular and comprehensive risk assessments to identify potential threats and vulnerabilities across their operations.
- Investing in Training and Education: Both invest in training and education programmes so that employees are equipped with the knowledge and skills necessary to identify and manage risks effectively. Employees at all levels contribute to risk management efforts.
- Collaboration and Communication: Both companies know the importance of collaboration and communication in risk management. They create channels for open dialogue and information sharing. Stakeholders collaborate on risk identification, assessment and mitigation efforts.
- Continual Improvement: Both companies have a culture of continual improvement. They encourage feedback and innovation to adapt to changing circumstances and emerging risks.
- Tailored Risk Management Approaches: Both companies develop customised risk management frameworks and strategies that align with their objectives and priorities.
Emerging Trends in Risk Management
One of the most prominent trends in risk management is the increasing integration of technology into risk management processes. Advanced technologies such as artificial intelligence (AI), machine learning and automation are revolutionising risk assessment, prediction and mitigation. These technologies mean companies can analyse vast amounts of data in real time. This allows them to identify patterns and trends and predict potential risks more accurately.
Data analytics is another key trend reshaping risk management practices. Companies are leveraging big data analytics tools and techniques to gain deeper insights. By analysing historical data and real-time information, they can identify emerging risks, detect anomalies and make more informed risk management decisions.
Cybersecurity risks have become a major concern. Threats such as data breaches, ransomware attacks and phishing scams pose significant risks to companies’ data, operation and reputation. Companies are investing heavily in cybersecurity measures and adopting proactive approaches to protect their digital assets and mitigate cyber risks.
Companies are integrating global risk management into their overall risk management strategy too. They are monitoring global developments, assessing the impact of global risks on their business operations and developing contingency plans.
The Role of Leadership
Leadership plays a pivotal role in shaping organisational culture and driving initiatives that promote risk management excellence. Effective leaders recognise the importance of risk management but also actively champion its integration into the fabric of the organisation. Effective leaders:
- Set the Tone: Leaders set the tone by articulating a clear vision and commitment to risk management from the top down.
- Lead by Example: Leaders demonstrate their own commitment to risk management through their actions and decisions.
- Empower Employees: Leaders empower employees at all levels to actively participate in risk management efforts. They encourage employees to voice their concerns and contribute.
- Provide Resources and Support: Effective leaders invest in training and development programmes to enhance employees’ risk management skills and knowledge.
- Encourage Innovation: Leaders encourage employees to think creatively and experiment with new approaches to risk management.
- Promote Continuous Improvement: Leaders create opportunities for reflection and evaluation to identify areas for improvement and drive learning.
Encouraging a Risk-Aware Culture
For organisations to identify, assess and mitigate risks at all levels effectively, they need to encourage a risk-aware culture. Here are some tips for encouraging a risk-aware culture:
Communication and transparency:
- Encourage open communication channels where employees feel comfortable discussing risks and raising concerns.
- Provide regular updates on the organisation’s risk landscape, including emerging risks and mitigation strategies.
- Foster transparency in decision-making processes, particularly regarding risk-related decisions.
Education and training:
- Provide comprehensive training programmes on risk management principles, processes and tools for employees at all levels.
- Offer specialised training sessions on specific risk areas relevant to employees’ roles and responsibilities.
- Incorporate real-life case studies and examples to illustrate the importance of risk awareness and effective risk management.
Empowerment and ownership:
- Empower employees to take ownership of risk management within their respective areas of expertise.
- Encourage employees to identify and assess risks in their day-to-day activities and propose mitigation strategies.
- Recognise and reward employees who demonstrate proactive risk awareness and contribute to effective risk management practices.
Integration into performance management:
- Include risk management objectives and key performance indicators (KPIs) in employee performance evaluations.
- Link performance bonuses or incentives to successful risk management outcomes and adherence to risk management protocols.
- Provide feedback and coaching to employees on their risk management performance, highlighting areas for improvement and best practices.

Challenges in Risk Management
Challenges in risk management are inevitable, even for companies excelling in this domain. Despite their proactive efforts, all organisations encounter obstacles that can impede their risk management practices. Here are some common challenges and strategies for addressing them:
Complexity and interconnectedness:
- Challenge: The modern business environment is increasingly complex and interconnected, making it challenging for organisations to anticipate and mitigate all potential risks comprehensively.
- Strategy: Implement a holistic risk management approach that considers both internal and external factors impacting the organisation. Create cross-functional collaboration and information sharing to gain a comprehensive understanding of risks across departments and business units.
Rapidly evolving risks:
- Challenge: Risks are constantly evolving due to technological advancements, regulatory changes and global events such as pandemics or geopolitical shifts. Organisations may struggle to keep pace with emerging risks and adapt their risk management strategies accordingly.
- Strategy: Stay informed about emerging trends and developments that may impact the organisation’s risk landscape. Maintain flexibility and agility in risk management processes to respond promptly to new challenges.
Resource constraints:
- Challenge: Limited resources, including budgetary constraints and staffing limitations, can hinder organisations’ ability to invest adequately in risk management initiatives and tools.
- Strategy: Prioritise risk management activities based on their potential impact on organisational objectives and allocate resources accordingly. Leverage technology and automation to streamline risk management processes and maximise efficiency.
Compliance and regulatory burden:
- Challenge: Meeting regulatory requirements and compliance standards can be burdensome and complex.
- Strategy: Stay abreast of regulatory developments and ensure compliance with applicable laws and regulations. Implement robust governance frameworks and internal controls to demonstrate regulatory compliance and mitigate legal and reputational risks. Invest in compliance training and education for employees.
Human factors and behavioural biases:
- Challenge: Human factors such as cognitive biases, organisational politics and resistance to change can undermine effective risk management practices, leading to decision-making errors and oversight of critical risks.
- Strategy: Raise awareness about common cognitive biases and behavioural tendencies that may influence risk perception and decision-making. Create a culture of psychological safety where employees feel comfortable challenging assumptions and raising concerns about potential risks.
Conclusion: Striving for Excellence
In this article, we have explored the importance of effective risk management for businesses. We have delved into the criteria for excellence in risk management, showcasing companies such as ApexTech Solutions and TerraSafe Pharmaceuticals that exemplify these principles through their proactive strategies and robust frameworks.
From embracing technology and fostering a culture of innovation to prioritising regulatory compliance and empowering employees, these companies have demonstrated remarkable achievements in navigating complex risk landscapes and achieving sustainable success.
However, it’s essential to recognise that even companies excelling in risk management face challenges. By acknowledging these and implementing strategies to address them, organisations can enhance their resilience and effectiveness in managing risks over the long term.

Assessing Risk
Study online and gain a full CPD certificate posted out to you the very next working day.
Take a look at this course
About the author

Louise Woffindin
Louise is a writer and translator from Sheffield. Before turning to writing, she worked as a secondary school language teacher. Outside of work, she is a keen runner and also enjoys reading and walking her dog Chaos.
Similar posts

The Future of Disability Awareness: Changing Narratives and Perceptions

The Role of Employers in Promoting Disability Inclusion in the Workplace

Time Management Mastery for Senior Managers

Understanding Hoarding: Psychological and Social Perspectives
Celebrating our clients and partners.

Privacy Overview
- Sign up for free
- SafetyCulture
Risk Mitigation
Discover all there is to risk mitigation, how it fits into risk management, and how to apply it in an organization.

What is Risk Mitigation?
Risk mitigation is the strategy that organizations use to lessen the effects of business risks. It’s similar to the risk reduction process, wherein potential business threats are identified before the organization takes the necessary steps to lessen the effects of these factors.
Some of the threats and risks that modern organizations, businesses, and enterprises deal with include cybersecurity threats, natural disasters, and anything that may cause damage to the equipment, personnel, and facilities of an organization.
Why Is Risk Mitigation Important?
Risk mitigation is the process of understanding certain risks and threats, accepting that they exist, and taking the appropriate measures to reduce their effects in case they happen. It is a part of the risk management process and is necessary to prepare an organization for any threats to its operations and processes.
Instead of eliminating threats, risk mitigation focuses on the unavoidable threats and reducing their impact. This can include natural disasters and other threats that may cause issues in production and other processes.
These are threats that cannot be eliminated and are completely out of the company’s control. Risk mitigation is there so that if these events occur, the company has the right measures to ensure that the damage the organization sustains is kept to the bare minimum.
Types of Risk Mitigation
Risk mitigation isn’t a one-size-fits-all model. Each organization has its own take on it and its own approach to reducing the effects of certain unavoidable threats. However, some of the common techniques used for risk mitigation include:
Risk Transfer
This involves transferring the risk allocation between different parties. For example, if an organization gets materials or products from a third party supplier before distributing them, they can put all the risk for those certain materials in the hands of the third party instead.
Risk Acceptance
This involves accepting a certain risk and the threats it has for an organization for a certain period of time. The organization can focus on mitigating other risks and threats during this time.
Risk Avoidance
This is the strategy that an organization uses when the consequences of certain risks are too high for them to mitigate the risk. In these cases, it might be best for an organization to take measures to eliminate and avoid the risk altogether.
For example, if a certain process is deemed risky for safety and other reasons, risk avoidance would be not utilizing the process for worker safety.
Risk Monitoring
This involves keeping a close eye on different processes and teams to assess risks as they happen. From there, measures can be taken to minimize the effect of these risks.
Risk mitigation is pre-emptive. A great example of this is when an organization practices regular and proper maintenance of its equipment. This way, there’s a smaller chance that their equipment breaks down. If the equipment breaks down for unavoidable reasons, regular maintenance can ensure that the damage isn’t too bad. It also makes sure that the repairs won’t be as costly compared to if the organization didn’t practice regular maintenance.
A Step-by-Step Guide to Risk Mitigation
The risk mitigation process can be fairly complex. Companies regularly face a wide range of different risks in their day-to-day activities. This is why a risk mitigation team is necessary for modern companies looking to comprehensively reduce the effects of certain risks.
While each company has its method and approach, most risk mitigation strategies follow similar processes. Here are some key steps organizations and teams use to mitigate risk.
Identifying the Risks
The first step in mitigating risks is understanding which risks are present in the first place. When identifying risks, it’s important to leave no stone unturned. So, aside from data risks and breaches, organizations need to consider natural disaster risks, mechanical risks, and everything involved with their process.
Additionally, all risk mitigation strategies must include the employee’s needs and safety. Before formulating a strategy for risk mitigation, risk identification is the first step organizations need to take.
Create Your Own Risk Mitigation Plan Checklist
Eliminate manual tasks and streamline your operations.
Assessing Risks
Once the risks are laid out, it’s time for the team to assess the risk. During this phase, it’s important to quantify the risks and identify the risk levels of certain threats. This process also involves checking the measures and controls in place to reduce the effects of certain threats.
Prioritizing Certain Risks
Once the risks are properly leveled and quantified, the team can then figure out which risks to prioritize. Prioritizing certain risks is a key part of risk mitigation, as companies have to strongly emphasize the risks that can have the most detrimental effect on the organization, its processes, and its employees.
When the risk levels are properly assessed, the organization can easily determine which risks to prioritize and what measures are required to mitigate the risks.
Monitoring Risks
Risks and risk levels can change depending on several factors. This is why monitoring and tracking the risks throughout the organization is important. That way, the team can determine when the severity of the risks increases and when measures need to be changed. Additionally, it also helps them stay compliant with different regulations in place to reduce risk .
Implementation & Adjustments
Once there is a proper plan for risk mitigation, the next step is to implement the plan throughout the organization. This involves placing all appropriate measures, briefing and training employees, and most importantly, making adjustments to the strategy as needed.
There’s a chance that there are some required changes after seeing the risk mitigation plan . It’s important to adjust when the team learns something new to ensure the safety of all employees and processes and the organization’s compliance with regulations.
How to Mitigate Risks Effectively with SafetyCulture
Why safetyculture.
Risk mitigation is a complex process that can be hard to implement. Every part of the process, from the risk assessment to implementation, can be challenging for an organization. To make the entire process easier for the organization, tools such as SafetyCulture (formerly iAuditor) can be a huge help.
SafetyCulture is a comprehensive workplace tool packed with features to boost productivity, efficiency, and safety. However, the app also has a range of features available that can help organizations with their risk mitigation strategy. These features include:
- Create risk mitigation checklists from a range of templates available on SafetyCulture
- Establish a robust reporting system to allow employees to report issues as they happen and help teams identify risks in the workplace
- Collect crucial insights and data on risk mitigation measures to assess their effectiveness
- Generate reports from inspections to ensure that all processes are running smoothly
- Automate the monitoring of equipment to identify and catch issues the second they occur
- Facilitate workplace communication so that employees and managers have a clear line of communication to express any concerns, issues, and newly identified risks.
FAQs about Risk Mitigation
What is the difference between risk mitigation & risk management.
Risk mitigation is a part of the larger risk management process. While risk management deals with organizational risks, mitigation focuses on the effects of unavoidable risks and how to minimize them.

What Is the Most Common Form of Risk Mitigation?
Generally, organizations use a combination of all four types of risk mitigation to create a customized plan for their needs. This is why it’s crucial to have a dedicated and skilled team to analyze the organization and create a risk mitigation plan.
How Do You Identify Risks?
Identifying risks can be tough; however, it’s important to leave no stone unturned when doing so. This means that teams need to consider the risks involving equipment, natural disasters, safety risks, and anything else a company may face while conducting operations.
What Are the Four Types of Risk Mitigation?
Risk transfer, acceptance, avoidance, and monitoring are the four most common types of risk mitigation. Most organizations combine all types of risk mitigation to create a comprehensive and customized plan for their needs.

Leon Altomonte
Related articles

- Reputational Risk
Learn more about reputational risk, why it’s important that businesses properly manage it, and how to effectively implement risk mitigation strategies.
- Find out more

- Reputation Management
This guide will discuss what reputation management is, why it’s important, and ways in which business leaders can maintain their organization’s healthy image

- Environmental Aspects and Impacts
Explore the intricacies of environmental aspects and impacts of the organization’s practices to enhance the company’s sustainability, compliance, and competitive advantage.
Related pages
- Process Hazard Analysis Software
- EHS Risk Assessment Software
- Integrated Risk Management Software
- Operational Risk Management Software
- Risk Based Inspection Software
- Risk Mitigation Strategies
- Risk Assessment Examples
- Contract Risk Assessment Checklist
- Point of Work Risk Assessment Template
- 7 Best Risk Assessment Templates
- 5×5 Risk Matrix Template
- Risk Mitigation Plan Template
Risk management methodology in the supply chain: a case study applied
- S.I. : Risk Management Decisions and Value under Uncertainty
- Open access
- Published: 10 August 2021
- Volume 313 , pages 1051–1075, ( 2022 )
Cite this article
You have full access to this open access article

- M. J. Hermoso-Orzáez ORCID: orcid.org/0000-0002-6430-3233 1 &
- J. Garzón-Moreno 1
14k Accesses
11 Citations
Explore all metrics
A Correction to this article was published on 28 February 2022
This article has been updated
This work provides a general risk management procedure applied to synchronized supply chains. After conducting a literature review and taking the international standard ISO 28000 and ISO 31000 as a reference. The most important steps that enable organizations to carry out supply chain risk management are described. Steps such as defining the context, identifying and analyzing risks or avoiding them, controlling them and mitigating them are some of the main points of this work. On the other hand, we carried out a practical case in which the execution of this procedure is carried out in a real supply chain located in the city of Jaén. In this specific case study, the most important risks and those that require early treatment will be discussed. In addition, a series of suggestions and ideas will be established, by way of conclusions, that allow said organization to improve the results that we have obtained in risk management.
Similar content being viewed by others

The Model for Risk Management and Mastering Them in Supply Chain

Supply Chain Risk Management

Categorizing Supply Chain Risks: Review, Integrated Typology and Future Research
Avoid common mistakes on your manuscript.
1 Introduction
Most of the companies there are frequently alterations in their operation that cause disruptions in their daily operations (Artikis, 2016 ). These types of alterations are a consequence of potential risks that exist in the environment in which the business activity takes place (Prakash et al., 2020 ). Identifying and analyzing the risks of supply chain disruption is essential to prevent disaster scenarios (Shareef et al., 2020 ). Recent studies analyze the impact of supply risks on the company's optimal purchasing decisions (Zhang et al., 2020 ) and the importance of correctly identifying the source of supply risks (Guo et al., 2016 ).
In a globalized world, where the flow of products and / or services of many organizations have an international reach, it is essential to be able to manage the risk or at least (Xue et al., 2020 ), to have plans that mitigate (He & Yang, 2018 ) to a greater or lesser extent the potential risks to which one can Face any organization (Schauer et al., 2019 ). The configuration and coordination analyzes can be used as a foundation for further research in the context of integrating manufacturing network and supply chain theory (Rudberg & Olhager, 2003 ). On the other hand, Risk management using decision methods (AHP) (analytical hierarchy process) to face solutions with a value under uncertainty (Álvarez-lópez, 2016 ) is presented as a practical and innovative tool (Choi et al., 2017 ). There are some recently published review papers on risk management in the supply chain operations processes under uncertain environments. For example (Colicchia, 2012 ) use a rigorous literature review methodology, called systematic literature network analysis, to identify future research directions of supply chain risk management and to recognize streams of research that appear to be most promising. Heckmann et al. ( 2015 ) systematically define supply chain risk concepts, terminologies, and risk measuring and modeling methods from related fields. Fahimnia et al. ( 2015 ) use bibliometric and network analysis tools to identify key research clusters/topics, interrelationships, and generative research areas on quantitative models for managing supply chain risks. Chiu and Choi ( 2016 ) review the use of mean-risk models for analytical supply chain risk analysis. Govindan and Jepsen ( 2017 ) review the risks related to suppliers in service supply chains. Snyder et al. ( 2016 ) examine operations management literature on supply chain disruptions and provide an overview of the research within six supply chain processes (Snyder et al., 2016 ).
The result of this work is the elaboration of an applied methodology that allows companies to carry out a risk management of their supply chain in a useful and logical way (Senna et al., 2020 ) In parallel to the explanation of the procedure, we will carry out a practical case of risk management for a real supply chain located in the city of Jaén (Spain).
One of the objectives of this document is to demonstrate the importance of the risk management of a supply chain to guarantee the success of the organization (Fernando et al., 2018 ) Supply chains need great care to function properly and, risk analysis is the most powerful tool to minimize problems in the near future (da Silva et al., 2020 ).
At all times, the international standard related to the management of supply chain risks, ISO 28000, will be used as a reference and other standards that have been considered convenient, such as ISO 31000 (Leitch, 2010 ) (project risk management) or (UNE-EN- IS0 9001, 2015 ) (quality management). Both ISO 31000 (UNE-EN-31000 AENOR, 2018 ) and ISO 28000 (UNE-EN-ISO 2800 AENOR, 2008 ) reflect the need for risk management not only in the supply chain, but in all parts of an organization (Blos et al., 2016 ) Both require more reflection than many organizations do on the subject (Hermoso-Orzáez et al., 2020 ).
2 Methodology and objectives
There are studies that used the integrated approach consisting of AHP to solve multi-criteria decision-making problems (MCDM) with criteria weights (Sarkar & Biswas, 2021 ) for risk treatment. Este documento tiene como objetivo identificar, clasificar y priorizar los riesgos de la cadena de suministro que enfrentan las pequeñas y medianas empresas de fabricación de pan y derivados para desarrollar una metodología de gestión de riesgos de la cadena de suministro (Alora & Barua, 2020 ). With this study we intend a triple objective:
Risk detection, risk mitigation, and risk recovery, Reduce risk management in supply chains to a single procedure through the study and collection of numerous methods and documents related to the subject (DuHadway et al., 2019 )
Apply this procedure to a practical case in a current supply chain, measuring the results and assessing them for possible measures that can reduce the probability of occurrence of each one or reduce or mitigation its impact on the chain.
To make the reader aware of the importance of risk management in supply chains and the corresponding role they must acquire within organizations.
The methodology that is summarized in this document, we find stages that are more qualitative, such as definition of links or description of phases, and stages where it will be necessary to use numerical techniques that allow us to quantify, evaluate and prioritize the risks that are going trying during the early stages (Machado Nardi et al., 2020 ) The methodology for proper risk management consists of six steps characterized by a descriptive content in most of them and a logical chronology that helps and complements the beginning of its next phase. (Felfel et al., 2018 ) There are high impact research works that include and measure qualitative elements with methodologies designed to be qualitative, inductive and exploratory, thus involving multiple data collection methods and tools. More specifically, during the first stage of empirical analysis, these studies map and analyze preferences and perceptions of product quality at both the consumer and supply chain level.These qualitative insights may not be given adequate value initially. But it is precisely in the following stages or steps of risk monitoring and control that we are going to adjust its real impact on the supply chain (Tenorio et al., 2021 ).
2.1 Define the general process and establish the context of the supply chain to analyse
Correct risk management requires a detailed knowledge of the company, the market in which it operates and the legal, social, political and cultural environment that surrounds it.
In order for a company to initiate an analysis to make an improvement, it must know at what point it is to, from there, perform an assessment or diagnosis. These states of maturity include information, talent, workers, their objectives, values, their policy, the activities of each process, etc. Organizations must know what their position is within the chain to which they belong. Within this aspect we have two options: that the organization occupies most of the supply chain to which it belongs (the same company is responsible for most of the activities) or that the organization occupies a link within the chain supply (vertical integration is less).
Our case study will focus on "PanJaén", a family business located in the city of Jaén (Spain). This company in the services sector offers its customers a wide variety of breads, coming to work with more than 10 types of flour (some organic) for its preparation. Other of its products are savory, whether snacks or puff pastry, and cakes. In addition, during all seasons they merge the most avant-garde and innovative styles of the market to offer products of all kinds, such as mantecados or roscones de Reyes at Christmas time.
It is defined as a company experienced by a family totally related to the bakery sector and known for the quality of its artisan products. They presume to use quality raw materials, ecological ingredients and be in continuous training and qualification, integrating any technological advance for their productive development. In addition, these bakeries are in an expansion process, that is, they increasingly incorporate new products in their stores to serve the citizens of Jaén.
All the activities that “PanJaén” controls in its supply chain are in the city mentioned. Some of the general aspects of our study company are those found in Table 1 .
On the one hand, the information obtained up to this point, allows to place the entire supply chain (except the domain of the suppliers) under the same location. There will be risks that do not matter to those responsible for “PanJaén”, such as those related with customs or exchange rates.
On the other hand, knowing the main characteristics of the corporate environment of the organization, such as the objective or its policies, we will have a guide by which to make decisions about preventive measures to avoid the risks detected.
2.2 Separate the process into groups of related tasks and systematically consider the characteristics of each operation
The supply chain has different links with specific planning and execution and dependent on the rest. Therefore, we can differentiate, in general, three large blocks for all supply chains. These blocks will be supply, production and distribution. These three links are of general application, that is, depending on the supply chain we are studying the links may vary and can be all considered, depending on the interdependence they have with each other and the need to differentiate them. (Ventura et al., 2013 ).
In the “PanJaén” supply chain, we will classify four groups: suppliers, production, distribution and points of sale.
2.2.1 Suppliers
Suppliers are those companies that supply others with goods or services necessary for the proper functioning of the business. "PanJaén" has several suppliers of raw material, one of them being the main one for the elaboration of all its products. This first supplier supplies them with almost all the necessary elements, such as flour, yeast, baking powder or butter. The raw material of this supplier represents the highest percentage in the company's products.
Another provider supplies you with eggs, milk, sugar and salt.
A third supplier is the one in charge of the complements, that is to say, those components (like the decorative ones) that accompany the main product and that are normally edible. There are many products sold accompanied by edible flowers, chocolate chips or colored balls that are purchased and applied directly to the target piece.
And finally, a fourth supplier is the one that supplies the assembly, that is, the materials that the company needs to be able to transport its products, such as covers, bags or boxes for the cakes. These, unlike the previous ones, are not edible and most of them have the company logo, as well as contact information, since they have a direct relationship with the customer.
2.2.2 Production
It corresponds to the internal processes that comprise the activities and manufacturing tasks that occur within the company. In other words, a production process is a system of actions that are related to each other and whose objective is none other than to transform elements, systems or processes. For this, some input factors are needed that, throughout the process, will increase in value thanks to the transformation.
In our case study, all production processes are carried out in the same physical place established in the industrial polygon of the capital Polígino de los Olivares s/n Jaén (Spain), except for a final baking that occurs at the point of sale. According to "PanJaén", the key to its products is in slow fermentation. This process is done since the water is mixed with the flour and goes until the first minutes of baking. First, a pre-fermentation is done slowly that will favor the final fermentation in order to be precise in the furnace jump. This is the key to improving the quality of bread, since it manages to respect and take care of the benefits that each of its stages generates.
This company has tunnel ovens with independent temperature controls throughout the oven. These ovens help to easily adjust the different temperatures during the baking cycle and optimize the first bake. Once the final result is achieved, they are packaged and go to the destination physical stores, giving way to the next link in the chain. Subsequently, at the point of sale, a second baking is carried out, which lasts approximately 15 min.
2.2.3 Distribution
It is made up of the different delivery processes until reaching the customer. The first thing that comes to mind when talking about distribution is the section from when the product is ready to be delivered to the final customer until this happens, but this is not always the case. A company that belongs to an intermediate link in its supply chain is a customer and at the same time a provider of other links in the same chain, but it is not the end customer (Ocampo & Ospina, 2016 ). “PanJaén” uses a subcontracted fleet that carries out this work. Logically it is done on a daily basis due to the products with which it works. This link is, without a doubt, the one with the least dominance of the company “PanJaén” (together with the suppliers) since it does not dominate it in its entirety. Road maps, vehicle maintenance, packaging and management of entrances and exits of the means of distribution are planned and coordinated by “PanJaén” and by the transport company.
2.2.4 Points of sale
They are the places where customers directly access products, that is, physical stores. Here, the customer can observe all the products that the company offers and buy them at the same time. There are almost 20 points that "PanJaén" has in the city, so they are accessible to virtually the entire population.
Its opening hours are from 7:00 a.m. to 9:30 p.m., seven days a week. These establishments, as I have mentioned before, have ovens where the second baking of the bread is produced to achieve greater splendor for the customer.
2.3 Risk identification
No matter how much a company strives to control its processes, a crisis may arise from the weakest link. Even this link can be several levels away from the company that is directly affected (such as a supplier that provides a transport service for the distribution of food in a vehicle that does not meet the necessary quality requirements).
In general, supply chains are made up of similar agents. However, the risks for two similar chains may vary depending on various factors such as the activity to which they belong, the agents participating in it, the place where they are developed or the number of customers they satisfy. It is therefore difficult to assume that a particular risk for a supply chain has the same importance and value as that same risk in another supply chain.The biggest drawback of the risk is based on its great diversity, its multitude of origins, its variable consequences and the complex interrelation with the rest. The identification of risks involves naming the risk without explaining or quantifying it. Logically, people who work in a part of the supply chain have a greater facility to identify the risks of that part. That is why the definition and functional separation of parts of the supply chain is really important to carry out a successful risk identification.
Knowledge is an important resource in the supply chain and a critical determinant of the competitiveness of the supply chain (Jayaram & Pathak, 2013 ). This is developed both at the organizational level and at the individual level. While some authors focus on knowledge as a firm attribute, others point to the individual as the place of knowledge creation. When using the individual-level perspective of the knowledge-based vision, the company's ability to manage supply chain risk will depend on the risk mitigation competence of its supply chain managers. Therefore, we seek to better understand the factors that affect the risk mitigation competence of the manager (Ambulkar et al., 2015 ).
The risks of the supply chain can also encapsulate, for example, the risk of suppliers (delays in receiving raw material or poor quality material). Within an organization, internal risk factors, such as those related to forecast errors, failures, capacity problems and inventory problems, should also not be overlooked. Another example would be operational risks, related to the internal activity of the organization (Rogers et al., 2016 ).
Through the use of the qualitative methods “What if…?” And “Brainstorm”, the main risks that exist in the supply chain we are studying are collected (ITM Platform, 2016 ) (UNE-EN 31,010 2011). The risks identified in the “PanJaén” supply chain have been obtained from a list of their own elaboration for the first assessment of their impact using sources such as the Iowa State University College (Amling & Daugherty, 2020 ), the International Journal of Logistics and Applications Research (Rogers et al., 2016 ) and the International Journal of Production Research (Blos et al., 2016 ). The identified risks appear in Table 2 . These have been ordered according to their meaning and we have obtained a total of five risk groups: operational, direct process to the product/service, suppliers, safety and labor rights.
2.4 Risk analysis and assessment
The purpose of analyzing the risks is to obtain a list in which the risks of the chain are prioritized, which determines the relevance that should be given to each of the elements mentioned. With this prioritization, it will be much easier to visualize the importance that each risk has within the supply chain.
We will use the "Hierarchical Analytical Process, AHP". The AHP model was developed by the mathematician Saaty ( 2008 ) and consists of formalizing the intuitive understanding of complex problems by building a hierarchical model. The basis of the process is based on the fact that it allows numerical values to be given to the judgments given by people, managing to measure how each element of the hierarchy contributes to the immediately higher level from which it emerges. (Khalilzadeh & Derikvand, 2018 ; Delgado-Galván et al., 2011 ; Aznar & Guijarro, 2012 ). The process will consist of two phases: a first qualitative analysis and a second quantitative analysis. For the qualitative analysis, we will use the probability and impact matrix where the evaluator, in this case the organization, will determine for each risk these two characteristics. Probability refers, as we know, to the feasibility of something happening. The impact, on the other hand, refers to the consequences they would have on the supply chain (Ramanathan, 2001 ) (Wang et al., 2008 ).
Thus, we ask that each risk of the 14 identified be assigned a probability of occurrence between four categories (very low, low, medium or high) and an impact on the organization (mild, moderate, high or catastrophic) (Zamora Aguas et al., 2013 ). From here we will look for the relationship between the different risk groups we have. This relationship will be achieved by comparing the rating of each risk group with the rest of the rating and, depending on that comparison, we will establish the importance of one group over the other (Díaz Córdova et al., 2017 ),
Once we have each risk defined, we can assign a general probability and impact to the risk group. This allocation is given by an average of the probabilities and impacts of the risks that form that group. For example, all operational risks have an average probability, so the probability of the group of "Operational risks (1)" will have an average probability. Its impact will be high since two of the risks have this impact, while the remaining two have it moderate and catastrophic.
The next step will be to rate the risk group according to the probability and impact we have previously assigned. This rating will be determined according to Table 3 , with four possible levels (Ayuso-Muñoz et al., 2017 ).
For example, for the “Suppliers” risk group, its probability is low and its impact is high, so it will have a high rating. We will obtain a total of 5 ratings, since there are 5 types of risks we have. Once we perform this procedure for all groups, we will have as a result Table 4 , which we show below (He & Yang, 2018 ).
From here we will look for the relationship between the different risk groups we have. This relationship will be achieved by comparing the rating of each risk group with the rest of the rating and, depending on that comparison, we will establish the importance of one group over the other through Table 5 (Díaz Córdova et al., 2017 ; Khalilzadeh & Derikvand, 2018 ).
The "Linguistic variable" column refers to the importance of one risk group over another. As can be seen in Table 4 , when we are going to compare two risk groups, we will always compare the one with the highest rating with the other. In our case, we see that the risk group that has a rating above is 2, with a critical rating. The rest have a high rating, so Group 2 has a strong importance over the rest (Hermoso-Orzáez et al., 2020 ; Yusof & Salleh, 2013 ).
Once we have the relationships between the different risks, we will assign them numerical values. To do this, we will use the author Saaty comparison scales, which are shown in Table 6 (Hermoso-Orzáez et al., 2019 ; Saaty, 2008 ).
When two risks are equally important, even if they are two critical risks, the weight of one over the other will be low. The greater the weight of one risk with respect to another, the greater the importance it has over it. The intermediate values of the scales also represent that group, that is, if one risk has a strong importance over another, the value that we will assign not only can be 5, but we could also assign the values 4 or 6. These values in this Scales can be used as margins when the risks are of very similar importance, as is our case.
Looking at our results, of 5 groups of risks that we have, 4 have a high rating, that is, when we compare a risk of those four with the rest we can use the values of the scale (1, 2, 3) to prioritize in small magnitude those 4 values of equal rating. Logically, we will not be able to apply high values, such as 5 or 6 between two risk groups with the same rating, because among those risks there is not so much clear difference. Thus, we will begin by comparing the risk groups among them, assigning values of the scales corresponding to their comparison. For example, for risks 4 and 5, which have a high rating, their score will move in low values. Finally we decided that those of type 3 will have a little more importance over those of 4 because their probability of occurrence is greater, so that group 3 will have value 2 when compared with group 4.
In the end, we will add the columns to see the total in each risk. Table 7 shows the results.
The next step will be to weigh the table. It will be done by dividing each of the column values by the total calculated above. In this way we will obtain the weighting of each risk when compared to another, so we will need to average the weights in a new column.
That result will be the weighting of our risk group, which if multiplied by 100 will result in a percentage. The calculations of this step are reflected in Table 8 (Aznar & Guijarro, 2012 ; Ramanathan, 2001 ).
We note that the sum of all weights is "1", so they have been done correctly. The table that really interests us is the following (Table 9 ), with the importance that each group of risks must have when managing them.
We already have our final weights. We see that the most important risk is number 2 (Risks related to the direct process to the product / service), followed by risk group number 5 and 1 (Blos et al., 2016 ).
2.4.1 Consistency analysis of the AHP methodology
Before continuing, we will check the consistency of our results, as there are times that when it comes to rating the risks, the relationships established initially do not make sense. When the matrices are of a larger size, there are occasions that the criteria with which the risks are qualified are contrasted with each other and do not really reflect the importance of one risk over another. Thus, we have to verify that it is not our case and that the judgments carried out are consistent. (Baudry et al., 2018 ; Park et al., 2019 ).
To do this, we will calculate the consistency ratio that is given by the division of two parameters (1). This relationship will be more correct as it approaches 0. We will consider our rating reasonable as long as this ratio is less than 0.1. The two parameters that define this relationship are the consistency index and random consistency (Aznar & Guijarro, 2012 ; De Brucker et al., 2013 ).
2.4.1.1 Formula 1-consistency ratio
First, we will multiply the initial matrix by the average vtor (weights of each risk group). The result will be a vector that we will call “Total row vector”.
2.4.1.2 Formula 2-vector calculation total row
Next, we divide each term of this “Total row vector” by the average vector, resulting in a new vector that will be around the values of the size of our matrix (in this case the value 5). Ideally, the quotients should be the same number as the size of the matrix, indicating that the coherence is excellent. But as this does not happen, we will have to calculate the average of the quotients, which will correspond to \(\lambda_{\max }\) . All these calculations are reflected in Table 9 .
We calculate the consistency index, which is given by the formula ( 3 ).
2.4.1.3 Formula 3-consistency index calculation
To know what the value of the random consistency is, "RI", we move to Table 10 . The values of this variable are established depending on the size of the matrix we are studying. This consistency is the average consistency of 10,000 randomly constructed matrices and will help us move from the consistency index to the consistency ratio of a matrix.
Upon fulfilling the condition, we verify that the criteria for rating our risks are correctly performed, that is, they do not contradict each other.
We already have our final weights. We see that the most important risk is number 2 (Risks related to the direct process to the product / service), followed by risk group number 5 and 1.
The whole process must be checked for the consistency of the results, as there are times that when it comes to rating the risks, the relationships established initially do not make sense. When the matrices are of a larger size, there are occasions that the criteria with which the risks are qualified are contrasted with each other and do not really reflect the importance of one risk over another. Thus, we have to verify that it is not our case and that the judgments carried out are consistent.
This consistency relationship is given by the division of two parameters. We will consider our rating reasonable as long as this ratio is less than 0.1. The two parameters that define this relationship are the consistency index and random consistency. (Valladão et al., 2019 ).Upon fulfilling the condition, we verify that the criteria for rating our risks are correctly performed, that is, they do not contradict each other (Aznar & Guijarro, 2012 ). Once we have achieved a prioritization of risk groups, we will do the same process for each specific risk within its category. That is, we will carry out this process five times, and we will see what prioritization each risk has within its group to, finally, be able to compare the 15 risks suffered by the supply chain we are studying.
The result would be as shown in Table 11 below.
Once the prioritization of all the risks within your group has been calculated, we can make a final table where the importance of each risk group will appear on the one hand and, on the other, the importance of each risk within your group. Thus, on a percentage scale, we will see that priority occupies each of the 14 risks identified in the beginning, giving it a position of 1 to 14 possible, 1 being the most important risk of studying and 14 the least. Table 12 shows the order of importance of the risks, which have a color assigned in their box that follows the criteria of Table 13 .
2.4.2 Risk management
In risk management, good knowledge and classification of the risks obtained during the analysis process are necessary to be able to make decisions about future actions to reduce, mitigate or avoid them. Decision-making to deal with risks is often conditioned by ethical, legal, financial or strategic considerations.
It is very important to identify the risks that need treatment and those that do not. This decision of whether or not to treat risk, and how to do it, may depend on the costs and benefits of accepting the risk and/or implementing controls to mitigate, reduce or eliminate it.
In our case study, the most important risk is 2.1, which represents the risk of "Poor quality of the final product". Then we have 5.2, which represents the risk of "poor staff training," and third we have the risk of "poor customer service."
The following Fig. 1 shows a 3D bar graph that allows us to observe it visually.
3D bar diagram of the prioritization of risks in "PanJaén". (Own elaboration)
2.5 Risk monitoring and control
As part of the risk management process, risks and controls should be monitored and reviewed on a regular basis. This monitoring must establish and maintain procedures to be able to track and evaluate the performance not only of the risks to which it is subject, but to be able to follow its own risk management system as a whole.
This evaluation of the plans, procedures and capacities should be carried out periodically through actions that the organization considers as it has been analyzed throughout the risk management process, such as performance evaluations or reports. That is why monitoring and review should take place at all stages of the process (UNE-EN 31,010 2011 ).
This monitoring and control process can be carried out by two agents: management or independent staff through audits.
The objective of this step will be to verify that:
The hypotheses established in relation to risks continue to be valid.
The assumptions on which risk assessment has been based, including external and internal contexts, continue to be valid.
The degree of compliance with the risk management policy, objectives and goals is monitored.
Risk assessment techniques have been properly applied.
The recording of data and the results of the follow-up that facilitates subsequent analysis actions.
2.6 Risk mitigation
The risks can be reduced o mitigated through supply chain redesign such as diversification or modularity in processes and design (Kleindorfer & Saad, 2005 ), strategic inventory stockpiling (Chopra & Sodhi, 2004 )), risk pooling (Sheffi, 2003 ), principles from TQM Total Quality Management (Lee & Whang, 2005 ), or reducing supply chain complexity (Manuj & Mentzer, 2008 ). Using the traditional classification of risk frequency and impact (Norrman & Jansson, 2004 ), appropriate risk levels can be determined. Identifying general risk levels for Force Majeure disruptions and designing appropriate procedural safeguards and prevention mechanisms such as earthquake-proofing or fire facilities, backup inventory or suppliers, and contingency plans can effectively reduce the impact of a disruption.
Reducing the risk of Inside Jobs and other opportunistic behavior within the supply chain is more reliant on relationships than processes put in place.
These approaches are presented in Fig. 2 and connected to the different phases of risk management (DuHadway et al., 2019 ).
Effective risk management strategies (Own elaboration)
Reducing the risk of poor customer services, or bad quality of final products within a supply chain is manageable through setting up appropriate processes with a supply chain such as carrying safety stock and using reliable supplies (Tomlin, 2006 ), using a list of approved or preferred suppliers who have been pre-certified to some degree of reliability (Gosling et al., 2010 ), or using a risk management process to identify and manage risk levels for inadvertent disruptions which occur within the supply chain. Certain safeguards might be taken such as securing against theft (Sullivan, 2010 )(Sullivan, 2010 ), but in general, there are limited actions that a firm can take to prevent a targeted disruption. Recognizing that the entire supply chain might be exposed in the case of a disruption and strategically developing a balanced supply chain that is not extremely dependent on the contribution from a single firm can alleviate some of the risk, but there is no simple solution to eliminate targeted.
For our study case, the risk that most concerns those responsible for the supply chain is related to the final quality of the product. This may be due to several reasons:
The product has direct contact with the buyer, who is the one who finally makes sense of the supply chain. The customer expects a quality of the product they buy and this quality may not be what the customer expected, both better and worse.
The organization is not really aware of the quality of its products, that is, it does not know the real thinking of the client exactly. For this reason, when assigning a value to the probability and impact of this risk, those responsible for the chain are worried about something they cannot control, a fact that is logical because it is beyond their reach.
The good or bad quality of the final product has part of many risks that we have been analyzing before, such as raw material, poor staff knowledge or breakage through packaging. That is why quality represents, with this percentage so something, the consequences of many actions along the supply chain.
On the one hand, we know that the organization defines its products of a high quality, both in its elaboration, result and customer service. In fact, the objective of this company is “Create a quality brand image”. So, when customers go to their points of sale or buy on demand, they expect excellent quality, which is the quality that the organization claims to offer. So, could we lessen the impact of this risk in case it occurs? The answer would rather be no. If a customer is disappointed with one of their products, the impact would be catastrophic. So we will try to treat and mitigate the risk by playing with the probability of its occurrence.
There are many factors that influence the quality of "PanJaén" products. In fact, they are found along the supply chain. To analyze the causes of this risk, we will use one of the methods explained in the “Risk analysis and assessment” step, as we will analyze a risk. The method that we will use will be "Analysis of cause and effect (fish bone)", as can be seen in Fig. 3 . We will try to explain this Fig. 3 , cause and effect analysis for the risk "Poor quality of the final product". We have different causes from different points in the supply chain and a negative final effect or risk that we want to eliminate, treat or mitigate.

Cause and effect analysis for the risk "Bad quality of the final product." (Own elaboration)
3.1 Raw material
The poor conservation that the raw material presents with respect to time, either in the places of production, due to the inventory, or at the same point of sale, makes the product quality worse.On the other hand, the complements are pieces that accompany the final product, such as nuggets or edible wrappings. These, normally, are added directly to the product to be sold, so you have to be careful with their taste since they are not treated throughout the process.Finally in this group, the components of the raw material are essential, as many of the clients look for certain properties in the bread and ours may not comply with them. Thus, we must be clear about each of the properties of each component for treatment.
3.2 Manufacturing
It can be greatly affected by ignorance of the processes. The ignorance is not only of the personnel, but that a process in general is wrong and, although the personnel carry it out correctly, the result is not the ideal one. This may occur, for example, in the stages of component blends.On the other hand, product burns are crucial, as they give an undesirable appearance and taste. Because our bread has a double baking, you have to plan well the conditions of each of them and constantly monitor them.
3.3 Point of sale
The physical conditions of the establishment, such as cleanliness or smell, cause the client's expectations to decline. In the same way, the treatment of the shopkeeper influences the clients and the way of attending or taking the products.On the other hand, the products must have a strategic distribution not only intended for consumption, but also for the mixture of odors that may arise.
3.4 Physical appearance
This is one of the most direct aspects with the client, because it includes the attractiveness of the product that can be given by its touch or its shape. On many occasions, the customer has an opinion about a cake or a loaf of bread simply by looking at it, regardless of its taste.
If we perform an ABC classification of our risks, the result is as shown in Fig. 4 . We can see that only a few risks produce very negative effects.
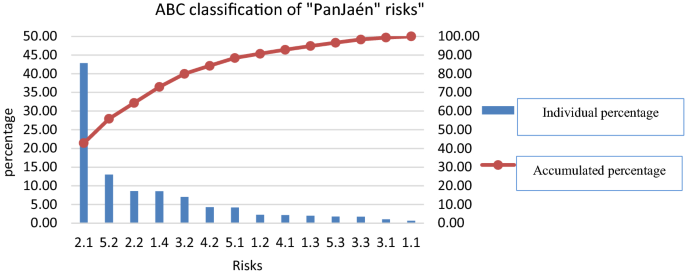
ABC classification of "PanJaén" risks. (Own elaboration)
We see that the first five risks occupy 80% of the prioritization (Group A of the classification), while the other nine add up to 20% among all. Therefore, the Plan of Measures among the five main risks could be the focus of proposing measures to reduce their probability and impact (Lo & Tang, 2019 ) See Table 14 . In this table, we identify each risk with the causes that originate it in the supply chain and the measures to be taken to avoid or mitigate it.
4 Discussion
The risk of poor quality of the final product may be given by the uncertainty of the organization about the opinions of its customers, so it would be important to take measures to inform us about the opinion of the customers about our products, as the rest of the tasks of the supply chain are under the control of the organization.
One possible measure would be for the supply chain to conform to some global standard that accredits the quality objective, such as ISO 9001(UNE-EN- IS0 9001 2015). This international standard takes into account the activities of the organization, focusing on all the elements of quality management. with which a company must have to have an effective system that allows it to manage and improve the quality of its products or services. (Khalilzadeh & Derikvand, 2018 ).
Another possible measure would be the creation of an application App movil aplications phone, for the mobile phone that rewards customer loyalty. Through this application, created by the company, consumers would have the possibility to value all products without having to do so in front of the workers. In addition, each time customers make a purchase, they can pass their identification code (on the phone screen) through a reader who is at the point of sale, transmitting the purchase data to the application. Thus, both clients and the organization would win:
The application, knowing the products that each customer purchases, can customize the suggestions and offer discounts and offers for their next purchases.
On the other hand, the organization will add more value to its chain and attract a greater number of customers. You can instantly report all your products without the need for a customer to enter the point of sale to learn about a new product.
5 Conclusion
This work allows us to conclude that the supply chain is valued by two key strategic concepts: its vulnerability and its resilience. Risk management is a fundamental tool for its control and future of the company.
Organizations will always be exposed to different types of risks that arise as an organization progresses in its activity. These risks will be characterized by their probability of occurrence and their impact on the organization. These variables can initially be assessed subjectively or qualitatively by the risk manager. Being able to seem not dependent on or outside the organization. That is, the risk exists and due to the circumstances of the moment, it will have a certain probability and impact. This is where risk management itself begins, which allows organizations to identify, analyze and quantitatively assess risks through techniques such as the use of "Hierarchical Analytical Process, AHP", presented in this study. That allows hierarchical ordering of risks, to later be able to treat and manage them appropriately, avoid them, mitigate them or eliminate them.
When an incident occurs and it is acted upon after its occurrence, the organization must be aware that early risk management allows a less demanding and faster reaction to that emergency, so risk management is an improvement process The flexibility between chain actors continues to increase.
Another of the great conclusions that we obtain from this study is the following: a supply chain can effectively challenge its vulnerabilities when all the actors that comprise it frequently share information. This will build trust, increase visibility, and decrease uncertainty in the network. Collaboration is related to visibility, as it includes the organization's willingness to share risk. Therefore, an organization regardless of its location or operating environment is part of a complex supply chain and has political, economic, competitive, logistical or infrastructure concerns. Therefore, up-to-date information flows are required regarding the products and services produced, which are highly coordinated within and outside the limits of the organization itself. All this leads us to affirm that information and its transfer are key in the processes of identification and treatment of risks.
Risk management in supply chains is increasingly important not only for the activities carried out in them but also for managers. Logically, organizations are not born with risk management in place but are created as events occur and according to the perspectives that managers acquire with their knowledge and experience.
Finally, it should be noted that the risk management process should never be an arbitrary process, but rather carefully crafted and prepared. The key tool to carry out this entire process is the creation of a department dedicated to risk management that analyzes and determines the scope of each situation and the measures to be taken, being aware that a crucial element is a strong communication. between all the members of this department and the different links in the chain. All this will give us the ability to face, avoid mitigating or eliminating the risks that affect us, whatever their nature. In this way, we will start the path towards a strong, flexible and competitive chain.
Looking at our case study, it can be seen that many of those factors that influence quality are risks that we have already identified, so the measures we take will be directed towards these risks that affect quality. In this way, we will reduce the probability and impact of these risks and we will also reduce the probability of occurrence of our main risk.
The risk of poor quality of the final product is observed as the main risk to be treated due to its impact on the supply chain of food production companies, on the final customer. It does not always have to occur in its entirety due to the combination of factors throughout the supply chain, but can be given by the uncertainty of the organization about the opinions of its customers. Therefore, it would be important to take measures to inform us about the opinion of customers about the final products placed in the hands of the consumer, since the rest of the tasks of the supply chain are under the direct control of the organization. In this process, the transmission of information along the supply chain is essential for risk management. In this sense, the use of new technologies such as Mobile Apps, which allow the customer to assess quality directly and interactively, is shown to be a powerful tool for the future for interactive risk management.
Change history
28 february 2022.
A Correction to this paper has been published: https://doi.org/10.1007/s10479-022-04583-w
Alora, A., & Barua, M. K. (2020). Development of a supply chain risk index for manufacturing supply chains. International Journal of Productivity and Performance Management . https://doi.org/10.1108/IJPPM-11-2018-0422
Article Google Scholar
Álvarez-lópez, I. R. A. A. (2016). Optimal allocation of a fixed production under price uncertainty. Annals of Operations Research . https://doi.org/10.1007/s10479-014-1702-7
Ambulkar, S., Blackhurst, J. V., & Cantor, D. E. (2015). Supply chain risk mitigation competency: An individual-level knowledge-based perspective. International Journal of Production Research, 54 (5), 1398–1411. https://doi.org/10.1080/00207543.2015.1070972
Amling, A., & Daugherty, P. J. (2020). Logistics and distribution innovation in China. IJPDLM, 50 (3), 323–332. https://doi.org/10.1108/IJPDLM-07-2018-0273
Artikis, P. T. (2016). Deriving advantage over a crisis by incorporating a new class of stochastic models for risk control operations. Annals of Operations Research, 247 (2), 823–831. https://doi.org/10.1007/s10479-015-1896-3
Ayuso-Muñoz, J. L., Yagüe-Blanco, J. L., & Capuz-Rizo, S. F. (2017). Lecture Notes in Management and Industrial Engineering Project Management and Engineering Research (Vol. 49). http://www.springer.com/series/11786
Aznar, J., & Guijarro, F. (2012). New Valuation Methods: Multicriteria Models. (Universitat Politécnica de Valencia, Ed.) ((2 a Ed.). Valencia (Spain). https://riunet.upv.es/bitstream/handle/10251/19181/TOC_6083_02_01.pdf?sequence=3
Baudry, G., Macharis, C., & Vallée, T. (2018). Range-based multi-actor multi-criteria analysis: A combined method of multi-actor multi-criteria analysis and monte carlo simulation to support participatory decision making under uncertainty. European Journal of Operational Research, 264 (1), 257–269. https://doi.org/10.1016/j.ejor.2017.06.036
Blos, M. F., Hoeflich, S. L., Dias, E. M., & Wee, H.-M. (2016). A note on supply chain risk classification: Discussion and proposal. International Journal of Production Research, 54 (5), 1568–1569. https://doi.org/10.1080/00207543.2015.1067375
Chiu, C. H., & Choi, T. M. (2016). Supply chain risk analysis with mean-variance models: A technical review. Annals of Operations Research, 240 (2), 489–507. https://doi.org/10.1007/s10479-013-1386-4
Choi, T. M., Govindan, K., Li, X., & Li, Y. (2017). Innovative supply chain optimization models with multiple uncertainty factors. Annals of Operations Research, 257 (1–2), 1–14. https://doi.org/10.1007/s10479-017-2582-4
Chopra, S., & Sodhi, M. M. S. (2004). Managing risk to avoid: Supply-chain breakdown. MIT Sloan Management Review , 46 (1).
Colicchia, F. S. (2012). Supply chain risk management: A new methodology for a systematic literature review. Supply Chain Management: An International Journal, 17 (4), 403–418.
da Silva, E. M., Ramos, M. O., Alexander, A., & Jabbour, C. J. C. (2020). A systematic review of empirical and normative decision analysis of sustainability-related supplier risk management. Journal of Cleaner Production, 244 , 118808. https://doi.org/10.1016/j.jclepro.2019.118808
De Brucker, K., MacHaris, C., & Verbeke, A. (2013). Multi-criteria analysis and the resolution of sustainable development dilemmas: A stakeholder management approach. European Journal of Operational Research, 224 (1), 122–131. https://doi.org/10.1016/j.ejor.2012.02.021
Delgado-Galván, X., Herrera, M., Izquierdo, J., & Pérez-García, R. (2011). Applications of AHP Methodology for decision making in the management of the supply network. In: Conference: XI SEREA, Seminario Iberoamericano de planificación, proyecto y operación de abastecimiento de aguaAt: Morelia, Mexico (p. 11).
Díaz Córdova, J. F., Coba Molina, E., & Navarrete López, P. (2017). Fuzzy logic and financial risk. A proposed classification of financial risk to the cooperative sector. Contaduria y Administracion, 62 (5), 1687–1703. https://doi.org/10.1016/j.cya.2017.10.001
DuHadway, S., Carnovale, S., & Hazen, B. (2019). Understanding risk management for intentional supply chain disruptions: Risk detection, risk mitigation, and risk recovery. Annals of Operations Research, 283 (1–2), 179–198. https://doi.org/10.1007/s10479-017-2452-0
Fahimnia, B., Tang, C. S., Davarzani, H., & Sarkis, J. (2015). Quantitative models for managing supply chain risks: A review. European Journal of Operational Research, 247 (1), 1–15. https://doi.org/10.1016/j.ejor.2015.04.034
Felfel, H., Ben, W., Omar, Y., & Faouzi, A. (2018). Stochastic multi-site supply chain planning in textile and apparel industry under demand and price uncertainties with risk aversion. Annals of Operations Research, 271 (2), 551–574. https://doi.org/10.1007/s10479-018-2980-2
Fernando, Y., Walters, T., Ismail, M. N., Seo, Y. W., & Kaimasu, M. (2018). Managing project success using project risk and green supply chain management: A survey of automotive industry. International Journal of Managing Projects in Business, 11 (2), 332–365. https://doi.org/10.1108/IJMPB-01-2017-0007
Gosling, J., Purvis, L., & Naim, M. M. (2010). Supply chain flexibility as a determinant of supplier selection. International Journal of Production Economics, 128 (1), 11–21. https://doi.org/10.1016/j.ijpe.2009.08.029
Govindan, K., & Jepsen; M. B. . (2017). Supplier risk assessment based on trapezoidal intuitionistic fuzzy numbers and ELECTRE TRI-C: A case illustration involving service suppliers. Journal of the Operational Research Society . https://doi.org/10.1057/jors.2015.51
Guo, S., Zhao, L., & Xu, X. (2016). Impact of supply risks on procurement decisions. Annals of Operations Research . https://doi.org/10.1007/s10479-013-1422-4
He, B., & Yang, Y. (2018). Mitigating supply risk: An approach with quantity flexibility procurement. Annals of Operations Research, 271 (2), 599–617. https://doi.org/10.1007/s10479-018-2840-0
Heckmann, I., Comes, T., & Nickel, S. (2015). A critical review on supply chain risk - Definition, measure and modeling. Omega (united Kingdom), 52 , 119–132. https://doi.org/10.1016/j.omega.2014.10.004
Hermoso-Orzáez, M. J., Orejón-Sánchez, R. D, Gago-Calderón, A. (2020). Analysis and Risk Management in Projects of Change to Led in Street Lighting According to ISO-21500 and UNE-EN-62198. In: C.-R. S. F. (eds) Ayuso Muñoz J.L., Yagüe Blanco J.L. (Ed.), Project Management and Engineering Research (1 a ed., pp. 405–424). Adolfo López-Paredes, INSISOC, University of Valladolid, Valladolid, Spain: Springer, Cham. https://doi.org/10.1007/978-3-030-54410-2_29
Hermoso-Orzáez, M. J., Cámara-Martínez, J., Rojas-Sola, J. I., & Gago-Calderon, A. (2019). Analytical and economic methodology for storage of large heavyweight equipment in industrial processes. Economic Research-Ekonomska Istrazivanja . https://doi.org/10.1080/1331677X.2019.1696692
Jayaram, J., & Pathak, S. (2013). A holistic view of knowledge integration in collaborative supply chains. International Journal of Production Research, 51 (7), 1958–1972. https://doi.org/10.1080/00207543.2012.700130
Khalilzadeh, M., & Derikvand, H. (2018). A multi-objective supplier selection model for green supply chain network under uncertainty. Journal of Modelling in Management, 13 (3), 605–625. https://doi.org/10.1108/JM2-06-2017-0062
Kleindorfer, P. R., & Saad, G. H. (2005). Managing disruption risks in supply chains. Production and Operations Management, 14 (1), 53–68.
Lee, H. L., & Whang, S. (2005). Higher supply chain security with lower cost: Lessons from total quality management. International Journal of Production Economics, 96 (3), 289–300. https://doi.org/10.1016/j.ijpe.2003.06.003
Leitch, M. (2010). ISO 31000:2009-The new international standard on risk management. Risk Analysis, 30 (6), 887–892. https://doi.org/10.1111/j.1539-6924.2010.01397.x
Lo, A., & Tang, Z. (2019). Pareto-optimal reinsurance policies in the presence of individual risk constraints. Annals of Operations Research, 274 (1–2), 395–423. https://doi.org/10.1007/s10479-018-2820-4
Machado Nardi, V. A., Auler, D. P., & Teixeira, R. (2020). Food safety in global supply chains: A literature review. Journal of Food Science, 85 (4), 883–891. https://doi.org/10.1111/1750-3841.14999
Manuj, I., & Mentzer, J. T. (2008). Global supply chain risk management strategies. International Journal of Physical Distribution and Logistics Management, 38 (3), 192–223. https://doi.org/10.1108/09600030810866986
Norrman, A., & Jansson, U. (2004). Ericsson’s proactive supply chain risk management approach after a serious sub-supplier accident. International Journal of Physical Distribution and Logistics Management, 34 , 434–456.
Ocampo, P. C., & Ospina, R. P. (2016). Marketing and supply chain in relation to the auto parts sector in Colombia. Sinapsis, 8 , 21–41.
Google Scholar
Park, B., Nam, T., & Yeo, G. (2019). Study on location selection of integrated depot of warehouse stores utilizing AHP method. Journal of Digital Convergence, 17 (2), 135–144. https://doi.org/10.14400/JDC.2019.17.2.135
ITM Platform. (2016). Don’t let the vase break: a dozen techniques to identify risks. . Projects, Program,Portfoilo . https://www.itmplatform.com/es/blog/que-no-se-te-rompa-el-jarron-una-docena-de-tecnicas-para-identificar-riesgos/
Prakash, S., Kumar, S., Soni, G., Jain, V., & Rathore, A. P. S. (2020). Closed-loop supply chain network design and modelling under risks and demand uncertainty: An integrated robust optimization approach. Annals of Operations Research, 290 (1–2), 837–864. https://doi.org/10.1007/s10479-018-2902-3
Ramanathan, R. (2001). A note on the use of the analytic hierarchy process for environmental impact assessment. Journal of Environmental Management, 63 (1), 27–35. https://doi.org/10.1006/jema.2001.0455
Rogers, H., Srivastava, M., Pawar, K. S., & Shah, J. (2016). Supply chain risk management in India – practical insights. International Journal of Logistics Research and Applications, 19 (4), 278–299. https://doi.org/10.1080/13675567.2015.1075476
Rudberg, M., & Olhager, J. (2003). Manufacturing networks and supply chains: An operations strategy perspective. Omega, 31 (1), 29–39. https://doi.org/10.1016/S0305-0483(02)00063-4
Saaty, T. L. (2008). Decision making with the analytic hierarchy process (AHP). International Journal of Services Sciences, 1 (1), 83–98. https://doi.org/10.1504/IJSSCI.2008.017590
Sarkar, B., & Biswas, A. (2021). Pythagorean fuzzy AHP-TOPSIS integrated approach for transportation management through a new distance measure. Soft Computing . https://doi.org/10.1007/s00500-020-05433-2
Schauer, S., Polemi, N., & Mouratidis, H. (2019). Correction to MITIGATE: A dynamic supply chain cyber risk assessment methodology. Journal of Transportation Security . https://doi.org/10.1007/s12198-018-0197-x
Senna, P., Reis, A., Santos, I. L., Dias, A. C., & Coelho, O. (2020). A systematic literature review on supply chain risk management: Is healthcare management a forsaken research field? Benchmarking . https://doi.org/10.1108/BIJ-05-2020-0266
Shareef, M. A., Dwivedi, Y. K., Kumar, V., Hughes, D. L., & Raman, R. (2020). Sustainable supply chain for disaster management: structural dynamics and disruptive risks. Annals of Operations Research . https://doi.org/10.1007/s10479-020-03708-3
Sheffi, Y. (2003). Supply chain management under the threat of international terrorism. The International Journal of Logistics Management, 12 (2), 1–11.
Snyder, L. V., Atan, Z., Peng, P., Rong, Y., Schmitt, A. J., & Sinsoysal, B. (2016). OR/MS models for supply chain disruptions: a review. IIE Transactions . https://doi.org/10.1080/0740817X.2015.1067735
Sullivan, A. K. (2010). Piracy in the Horn of Africa and its effects on the global supply chain. Journal of Transportation Security, 3 (4), 231–243. https://doi.org/10.1007/s12198-010-0049-9
Tenorio, M., Pascucci, S., Verkerk, R., & Dekker, M. (2021). What does it take to go global? The role of quality alignment and complexity in designing international food supply chains. Supply Chain Management-an International Journal . https://doi.org/10.1108/SCM-05-2020-0222
Tomlin, B. (2006). On the value of mitigation and contingency strategies for managing supply chain disruption risks. Management Science, 52 (5), 639–657. https://doi.org/10.1287/mnsc.1060.0515
UNE-EN 31010. .Risk management. Risk appreciation techniques (2011). :AENOR (Spain). https://www.une.org/encuentra-tu-norma/busca-tu-norma/norma?c=N0047287
UNE-EN- IS0 9001. ISO 9001. (2015). Normas9000. Obtenido de http://www.normas9000.com/content/que-es-iso.aspx (2015). file:///C:/Users/UJA/Downloads/009001NEIS106_ES.pdf
UNE-EN-31000 AENOR. UNE-EN-ISO 31000-Risk Management (2018). Spain. https://www.aenor.com/normas-y-libros/buscador-de-normas/UNE?c=N0059900
UNE-EN-ISO 2800 AENOR. UNE-EN-ISO 2800.Specifications for security management systems for the supply chain (2008). Spain.
Valladão, D., Silva, T., & Poggi, M. (2019). Time-consistent risk-constrained dynamic portfolio optimization with transactional costs and time-dependent returns. Annals of Operations Research, 282 (1–2), 379–405. https://doi.org/10.1007/s10479-018-2991-z
Ventura, J. A., Valdebenito, V. A., & Golany, B. (2013). A dynamic inventory model with supplier selection in a serial supply chain structure. European Journal of Operational Research, 230 (2), 258–271. https://doi.org/10.1016/j.ejor.2013.03.012
Wang, Y. M., Luo, Y., & Hua, Z. (2008). On the extent analysis method for fuzzy AHP and its applications. European Journal of Operational Research, 186 (2), 735–747. https://doi.org/10.1016/j.ejor.2007.01.050
Xue, K., Li, Y., Zhen, X., & Wang, W. (2020). Managing the supply disruption risk: Option contract or order commitment contract? Annals of Operations Research, 291 (1–2), 985–1026. https://doi.org/10.1007/s10479-018-3007-8
Yusof, N. A. M., & Salleh, S. H. (2013). Analytical Hierarchy Process in Multiple Decisions Making for Higher Education in Malaysia. Procedia - Social and Behavioral Sciences, 81 , 389–394. https://doi.org/10.1016/j.sbspro.2013.06.448
Zamora Aguas, J. P., Adarme, W. A., & Arango Serna, M. D. (2013). Supply risk analysis: Applying system dynamics to the Colombian healthcare sector. Ingenieria e Investigacion, 33 (3), 76–81.
Zhang, J., Chan, F. T. S., & Xu, X. (2020). The optimal order decisions of a risk-averse newsvendor under backlogging. Annals of Operations Research . https://doi.org/10.1007/s10479-020-03636-2
Download references
Open Access funding provided thanks to the CRUE-CSIC agreement with Springer Nature.
Author information
Authors and affiliations.
Department of Graphic Engineering Design and Projects, University of Jaén, Jaén, Spain
M. J. Hermoso-Orzáez & J. Garzón-Moreno
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to M. J. Hermoso-Orzáez .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Hermoso-Orzáez, M.J., Garzón-Moreno, J. Risk management methodology in the supply chain: a case study applied. Ann Oper Res 313 , 1051–1075 (2022). https://doi.org/10.1007/s10479-021-04220-y
Download citation
Accepted : 28 July 2021
Published : 10 August 2021
Issue Date : June 2022
DOI : https://doi.org/10.1007/s10479-021-04220-y
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Supply chain
- Multi-criterion analysis
- decision analysis
- Product quality
- Consistency
- Find a journal
- Publish with us
- Track your research

IT Assessment Risk Mitigation
In only 2 weeks of working with a university, a set of recommendations minimizing data center risk by protecting the current infrastructure and architecting for improved cooling was developed., project background.
A major renovation of the campus center (housing the data center) was beginning. As a part of the renovation, an elevator was being added to the building, and the elevator shaft needed to go through the university’s data center. The CIO wanted to understand the risk to the school’s computing infrastructure.
The Strategy
We met with members of the IT department to understand the current data center layout and inventory. Meeting with the facilities team (including architect and construction vendor), we were able to identify areas of data center risk and make recommendations for avoiding risk. Our recommendations were scaled appropriately for the size and criticality of the university’s data center.
We also provided detailed documentation of the data center layout, including equipment placement and cable paths. During our assessment, we identified opportunities for data center expansion, improved cooling, and new cable layouts.
Proven Results
- Steps were taken to reduce dust and vibration during construction and install devices to reduce EMI during the elevator’s operation.
- Plans were made to migrate racks 90 degrees, allowing for hot aisle/cold aisle operation.
- Cabinet doors were changed to grills to improve airflow and cooling.
More Successful Projects

Business Resiliency Assessment and Planning

Business Continuance Recovery Planning

IT Assessment - Full Evaluation
Uncover opportunities for it excellence.
Terra Gaines, Senior Account Manager for Harvard Partners has been in the Staffing Industry for 17 years, supporting multiple industry verticals and market segments including: IT, Cybersecurity, Semi-Conductor, Tech Integrators, Finance & Medical to name a few. Her personal and professional passions have always been people centric and she’s extremely proud of providing white glove service to each client and manager that she serves.
Terra is originally from Bakersfield, CA however, relocated to San Antonio, TX in 2020 in which she now calls “home”. She’s the proud mother of 3 sons: Alec, Hayden and Logan as well as a Scottish Terrier (Bleu) and Rescue Cat (Blake). In her spare time, she enjoys spending time with family and friends, hiking, swimming, gardening and volunteering in her community.
Jill Gearhart, Director Client Services, has over 20 years of Account Management experience in technology service areas across IT Consulting & Staffing, Cloud, Datacenter, Networking & Communications. Jill’s focus is in Client Engagement, proposing and ensuring the successful delivery of services from the Harvard Partners Portfolio tailored to attain each Client’s desired business outcomes, including the Staffing of essential resources.
Prior to joining Harvard Partners in 2014, she held a high-level Account Management position at a global technology company now known as Lumen (formerly CenturyLink), where she was appointed to multiple Excellence Advisory boards in several Enterprise product areas, domestic and abroad, over the span of 11 years. Notably, after the Qwest-CenturyLink Merger in 2010, and the acquisition of Savvis thereafter, she was instrumental in the integration between organizations in the effort to build a seamless customer experience. Through continual engagement with Enterprise client organizations throughout her tenure, she has had the privilege of collaborating on solutions and individual resources needed to answer numerous business objectives, whether expanding into new markets or advancing operational efficiency and resiliency.
Education: Bachelor’s of Science, Business Administration, Bryant University, Cum Laude
Chris Callaghan is the Director of Architecture Services and is responsible for overseeing the architectural services arm of Harvard Partners. This includes everything from to architecture approach strategy, to candidate selection & vetting, to engagement leadership. Chris has years of technology architecture consulting experience ranging from boutique architectural services companies to larger, established consulting companies. He’s played multiple roles, from individual contribution to client and consultant management.
Prior to joining Harvard Partners, he was the Engagement Lead and Consultant Manager at Systems Flow, Inc. where he was responsible for client engagement management, consultant management, architectural services, SOW negotiation/creation/signing, training, etc. Prior to that, he worked as an Enterprise Solutions Architect for a large reinsurance firm under Fairfax Holdings.
Gary Gardner is the Managing Director of Harvard Partners and an Information Technology executive with over 30 years of global Investment Management experience. He has a broad range of knowledge of Investment Management systems including investment research, portfolio management, trading, compliance, back office, CRM, and client reporting. Gary has expertise with technical infrastructure, operational risk, business continuity, SOX compliance, SSAE16 certification, vendor management, and cloud services.
Prior to joining Harvard Partners, he was the Chief Technology Officer at Batterymarch Financial Management, Inc. and GMO LLC where he was responsible for IT leadership and technical strategy for high computational and data-intensive quantitative asset management environments. Gary also held senior technology positions at Santander Global Advisors and Baring Asset Management.
Education: Gary studied Management Information Systems at Northeastern University.
Steve Walsh is a Managing Partner at Harvard Partners. Steve has been a career business leader for companies such as Hewlett Packard, EMC, Centerstone Manhattan Software, ClearEdge Partners, and Alliance Consulting.
Prior to joining Harvard Partners Steve was the worldwide leader for the Storage Consulting practice at Hewlett Packard. In this role, Steve was responsible for more than 500 employees encompassing sales, pursuit, portfolio, and delivery. Under Steve’s stewardship Storage Consulting built offerings to help clients assess and design complex storage infrastructures and develop state-of-the-art backup, recovery, and business continuance strategies. Steve grew the Storage Consulting Practice at HP by over 200% and introduced 20 new value-added offerings.
In addition to Hewlett Packard Steve has worked for companies both large and small. At ClearEdge Partners Steve advised C-level Fortune 500eExecutives on their IT purchasing and supply chain strategies, saving his clients millions over his tenure. Steve also has been a business leader at Alliance Consulting, where he built a practice to more than 200 consultants and 10 strategic offerings. Steve started his career at EMC Corporation from 1986 to 1998.
Education: Boston College School of Management, Computer Science
Matt Ferm is a F ounder and Managing Partner of Harvard Partners. Matt’s focus is on IT Assessments, IT Governance, and Program Management. Prior to Harvard Partners, Matt spent 17 years with Wellington Management Company, LLP. As an Associate Partner and Director of Enterprise Technologies, Matt was responsible for managing the global physical computing infrastructure of this financial services firm. This includes data centers, servers, voice and data networks, desktops, laptops, audio/video hardware, messaging (email, IM, etc.), security administration, disaster recovery, production control, monitoring, market data services, storage systems, and capacity planning.
During his career at Wellington, Matt managed the Operational Resilience, Resource Management, Systems Engineering, IT Client Services, and IT Strategic Development groups, chaired the firm’s Year 2000 efforts and was a member of the firms IS Priorities Committee, Project Review Committee (Chair), Systems Architecture Committee (Chair), Year 2000 Committee (Chair), Operational Resilience Committee, Incident Review Committee and Web Oversight Committee.
Prior to joining Wellington Management in 1992, Matt served as Director of Financial Services Markets for Apollo Computer, Hewlett-Packard, and Oki Electric where he managed the marketing of Unix workstations to the Financial Services industry. In 1985, Matt was Manager, New Business Development for Gregg Corporation (now IDD/Dow Jones/SunGard), a small investment database software company. Matt got his start in 1981 on Wall Street, working in the Custody Department of Bankers Trust and the MIS department of E.F. Hutton. Matt received his BA in Economics from Queens College, the City University of New York in 1982, and is a member of the Society for Information Management.
Education: Queens College, City University of New York – BA in Economics
Jason Young is a Senior Technical Recruiter at Harvard Partners and has more than 13 years of experience in recruiting and talent acquisition. Jason’s focus is on leading recruiting efforts and ensuring expectations are met or exceeded between our client’s needs and our candidate’s experience to deliver. Throughout his career, he’s filled immediate needs with high-level IT and business professionals. He also developed sourcing strategies and built strong relationships with IT specialists, leaders, and executives in a variety of industries.
Prior to joining Harvard Partners in 2018, Jason had a successful career with Advantage Technical Resourcing, (formerly TAC Worldwide Companies). He began his career in IT Staffing with Advantage as a Sourcing Recruiter, finding top-tier candidates for the Sr. Recruiters. He quickly advanced to be the sole recruiter of a national high-volume staffing program. His accomplishments with this program led to him being an MSA recruiter for a large global enterprise client. He provided them with a wide range of talent for more than five years.
Education: Bachelor’s of Arts, Psychology, Framingham State University
Lisa Brody is the Talent Operations Manager at Harvard Partners and her focus is on managing the recruiting practice. Lisa has over 30 years of experience in recruiting and talent acquisition. She has successfully brought top-tier Information Technology and Business Professionals to our clients, with a purpose, to fill immediate needs as well as, create an ongoing strategy to find IT specialists, leaders, and executives in a variety of industries.
Prior to joining Harvard Partners in 2016, Lisa reveled in an accomplished career with Advantage Technical Resourcing, (formerly TAC Worldwide Companies) from the rise of the organization, serving in several specialized recruiting and talent management roles. She was a lead MSA recruiter for large global enterprise clients for over a decade, providing a wide range of talent. Throughout her advancement, she has consistently, cultivated a strong reputation among candidates and clients for competency, professionalism, and results.
Education: Massachusetts Bay Community College, Wellesley, MA Associate of Science, Retail Management
- Compliance Checklists
- In-Depth Guides
- Framework Templates
- Customer Stories
Your Trusted Resource for Risk Management

What Is Risk Mitigation? And Why Is It Important?
Risks are inevitable in business. Businesses must reduce their exposure to risks and find ways to mitigate them to remain competitive in business. The ultimate goal of risk mitigation is to minimize the likelihood and severity of adverse events while enhancing an organization’s ability to navigate uncertainties.
This blog explores the concept of risk mitigation and highlights its significance in managing and reducing potential threats to organizations.

What Is Risk Mitigation?
Identification and acknowledgment of risks that affect the operations, profitability, security, or reputation of the business is the first step. Developing strategies to mitigate these risks is the next and the most essential step! Risk mitigation is an important step in risk management that includes identifying the risk, assessing the risk, and mitigating the risk.
Risk mitigation can be defined as taking steps to reduce or minimize risks. When you devise a strategy for reducing prospective risks and working with an action plan, it is important that you choose a strategy that relates to your company’s profile and nature of business.
Here’s why risk mitigation is important:
– A robust risk mitigation plan helps establish procedures to avoid risks, minimize risks, or reduce the impact of the risks on organizations.
– It guides organizations on how they can bear and control risks. This helps a business in achieving its objectives.
– The ability to understand and control risks makes an organization more confident and helps in making the right business decisions.
– It increases the stability of the organization and reduces its legal liability.
– It protects the people involved and the company from any potential harm.
Different Types of Risk Mitigation Responses
Let’s take a close look at different management strategies for mitigating risks:
Accepting a risk does not reduce the impact of it on the organization. However, risk acceptance is considered as a valid option. Accepting risks involve identifying and analyzing risks and bringing these risks into the attention of stakeholders so that everyone involved are aware of the risks and its consequences. The most common reason for accepting a risk is that the cost of mitigation options might outweigh the benefit.
This is exactly the opposite of the accepting risk. If the risk poses unwanted consequences, the organization chooses to avoid the action that leads to the exposure of the risk. Not starting a project that involves high unwanted risks avoids the risk completely.
Risk transfer is the involvement of handing over the risk or a part of risk to a third-party. A conventional means to transfer risk is to outsource some services to a third-party. Many organizations outsource payroll, recruitment services to third party. It might involve some drawbacks and take out some control from your organization.
Businesses use this tactic most often in risk mitigation. It may include reducing the probability of the occurrence of the risk, or the severity of the consequences of the risk. If the organization cannot reduce the occurrence of the risk, then it needs to implement controls. Implementing controls should aim at reducing the chances of the risk occurring or finding out the cause for the risks and try avoiding it. Implementing appropriate controls depends on an organization’s decision making process and the nature of the business. One typical example for reducing a type of risk could be using a component tested and available in the market than subcontracting to create the same to a third-party.
Creating a Risk Management and Risk Mitigation Plan
Risk management and mitigation process consists of identifying, assessing and mitigating risks. There are different steps involved in creating a risk mitigation plan. These include:
● Identify Risks
All the risks must be noted distinctively. This includes every risk big or small, that may harm the organization. The identified risk can be added to a risk register.
● Define and Describe Risks
Define and describe a risk. Describe the intensity of the risk and the areas it will impact.
● Allot Risks
All risks that are identified and described must be forwarded to respective entities to take action on mitigating them. The person handling the individual risk is answerable to the management about it.
● Categorize Risks
There are different types of risks, such as business risks and non-business risks. You can also categorize risks as small risks, medium risks, and high risks. Then, there are risks which you can afford to take and those that should be avoided.
● Minimizing Risks
This is the main part of risk mitigation, which involves taking actions to minimize risks. Appropriate actions should be taken to control risks and dodge them when they come up, so they don’t become a barrier in achieving business objectives.
Best Practices for Risk Mitigation
Here are some ways businesses can make their risk mitigation strategies more effective:
● Promote Transparency
There should be complete transparency in an entire organization. Even minor miscommunication or misinformation could lead to big problems. Therefore, its important that each step is clearly discussed and known to each stakeholder to mitigate risks.
● Build a Team
Many businesses have experts in their team who deal with risks tactfully and also know the consequences if risks occur. Businesses should appoint such experts to oversee risk mitigation in an organization, and also hold team members responsible for each type of risk.
● Reporting
Regular reporting provides a clear picture of the situation and the actions that need to be taken. Thus, management should encourage all teams to regularly report on the risks they’re managing and controlling.
● Evaluate carefully
Evaluation of risks helps you identify which risks might occur, and when and where. This helps you create better risk management plans.
● Share objectives with your team
Each stakeholder must have one common goal: to cut down risks that come their way. No personal interest should be involved. This helps keep everyone on the same page and upholds the business ethics and interests.
Wrapping up
While risks are an inherent part of every business, risk mitigation helps businesses minimize the impact of certain risks, while acknowledging and accepting others.
VComply provides an effective way for businesses to track and mitigate risk. VComply helps manage and automate the risk management processes such as risk assessment and risk treatment. The best risk mitigation strategies involve maintaining a risk register, regular reporting, teamwork, and planning.
Related Articles

The 5 Stages of Policy Management

Four Mistakes to Avoid While Implementing Policy Management

What is GRC Reporting and Why is it Important?
Fill out the form to download the datasheet., a single source of truth for your grc operations.
Ready to set up a trial of VComply and automate your compliance process?


Chipotle Case Study: Either Manage Risk or Disclose Lack of Risk Management
Steven Minsky | Feb. 9, 2016
Back in 2009, we blogged about the SEC’s decision to require board-level accountability for ERM . This decision was based on the conclusion that inadequate risk management allowed the regulatory failures that ultimately led to the financial crisis. As we wrote in that post, “boards are now required by the SEC to report in-depth on how their organizations identify risk, set risk tolerances, and manage risk/reward trade-offs throughout the enterprise.”
That blog detailed an important ruling: it refers not only to integrated risk management competency at the executive level, but at all employee levels that have an impact on company performance. This perfectly mirrors a risk management mantra – risk should make up a part of everyone’s – not just risk managers’ – job description.
In 2007 , regulators released Sarbanes-Oxley Audit Standard 5 (SOX AS5), which holds management accountable for the risk of misstated company financials. The SEC disclosure rule is similar in the sense that it uses materiality, not specific risks, as a measure of what needs to be mitigated. It differs, however, in the sense that it applies to all risks, not only financial concerns, and does not take into account an organization’s size. In other words, everyone should be concerned with ERM compliance.
This leads to a fork in the road; organizations need to either adopt an effective risk management program or bite the bullet and disclose their ineffectiveness. There is no third option – maintaining ineffective risk management tools without disclosure is considered negligence, and is easier to prove than fraud is.
Chipotle’s recent fiasco demonstrates the results of poor risk management
According to Business Insurance , Chipotle’s problems don’t end with a host of recent salmonella outbreaks, which have been linked to food sold in numerous branches. The company also “failed to disclose that its ‘quality controls were inadequate to safeguard consumer and employee health,’ according to a civil lawsuit.”
The company is now suffering a major reduction in share prices (“35% since the end of October”), reduced sales (December sales were down 30% in some locations), and a marred reputation that relies upon the appeal of safe, sustainably grown food. The manner in which the company misled shareholders is almost entirely responsible for the civil suit.
Chipotle introduced a great innovation in the food industry: fresh, healthy, locally sourced fast food. However, the company failed to implement the risk management necessary to support that innovation. Enterprise risk management is as much about enabling innovation as it is about facilitating compliance, health, and safety. The check-the-box approach of disclosing the “usual risks” was made unacceptable back in 2010, if ever it was acceptable. Every business innovates, and every business therefore needs to find the unique risks it introduces, get them covered, and disclose them to shareholders.
Had Chipotle’s management implemented an enterprise risk management solution, either of two outcomes would have occurred:
- Food might never have been contaminated, since ERM extends to a robust vendor risk management methodology that helps identify risks associated with a company’s supply chain.
- Even if the outbreaks had still happened, Chipotle would have been able to use enterprise risk management reporting capabilities to evidence its risk program. This would have avoided regulatory penalties, provided evidence of control activities, and guided risk disclosure, all of which would have eliminated liability for non-disclosure of risk.
These outcomes aren’t just possible, they’ve happened before . In 2009, a Morgan Stanley executive was found to have evaded internal controls. The company itself avoided prosecution thanks to the robustness of its internal policies and procedures. Unlike Chipotle, Morgan Stanley “maintained a system of internal controls meant to ensure accountability,” and pointed to these systems when asked about the adequacy of its risk management program.
There is never a 100-percent guarantee that surprises won’t happen. Sometimes, human error and external threats can’t be predicted. What’s important is minimizing the likelihood of those surprises, and ERM software accomplishes just that. At the very least, a robust, well-documented solution provides an easy way for organizations to maintain full disclosure and avoid regulatory action.
Adopt Risk-Based Vendor Management
We look at actions you can take that will help streamline your vendor management process in this webinar!
My Favorites List
Submit your Favorites List and our experts will reach out to you with more information. You will also receive this list as an e-mail which you can share with others. Here are the solutions you've added to your list so far:

The importance of risk management in project planning and execution
- July 25, 2024

The process of planning and executing a project is a world in itself. Here, ideas transform into reality with the support of investment. There's a cost attached to every step of execution. Even the most carefully planned projects face problems during this stage. This is when risk management comes into the picture. It wouldn't be an understatement to call it a factor responsible for the success of any project.
You are expected to foresee pitfalls and prepare strategies to navigate them. Especially to establish a career in investment banking, you must have a solid understanding of this concept. Keep reading to explore the importance of risk management and the complex world of project planning.
What is risk management?
Innovation, business ventures or financial undertakings have in-built risks. If left unattended, these risks can waste resources. They can also derail the project's progress. Here's when risk management saves the day!
Risk management is a systematic process. Through it, you can identify, analyse, and control potential risks to the project. By implementing effective risk management practices, organisations can navigate challenges. Also, they can increase their chances of achieving their goals. Thus, understanding the importance of risk management is crucial for ensuring the success and sustainability of any venture.
Performing risk management involves the following steps.
- Assess the likelihood and impact of risks.
- Develop strategies to mitigate risks.
- Track the effectiveness of these strategies.
What is the importance of risk management?
Prima facie, risk management helps in anticipating potential risks. During the planning phase, you must assess probable risks. By working on this, you can avoid potential failures and costly delays.
Keep reading to explore other benefits offered by risk management.
Decision-making process : As you can see, risk management carries a structured approach. This arrangement improves your decision-making capability. It gives you the knowledge to deal with uncertainties that obstruct the success of your project. By managing risks, companies make better decisions. They are also prepared to look for alternative solutions while optimising project timelines.
Team confidence : Another benefit of this process concerns the team. When there is a backup plan for things that might not go as expected, it helps the team stay positive and happy. In a positive environment, your subordinates will perform in a good mood. This will help in completing the project within the deadline.
Investment protection : Another importance of risk management lies in protecting investments. It prepares the project for success. This not only preserves the project's integrity but also safeguards the reputation of the stakeholders involved. For any given project, stakeholders can be clients, regulatory bodies, employees, and investors.
Risk management reduces uncertainties in your project. Thus, it ensures success. With this, you can enhance transparency and build stronger relationships with stakeholders. You can do this by considering their concerns during the risk assessment.
Improving communication : Any strong risk management framework depends on communication between departments. In the initial stage, you will need inputs from different departments. This will help you understand the project's complexities. Moving on, this cooperation helps in clarifying roles, dividing responsibilities, and enhancing the coordination of the overall project.
How to perform risk management?
Begin by performing risk identification. Once that is done, start assessing its probable impact. It is important to know the likelihood of these risks occurring. The next step is to collaborate with stakeholders. Implement one or more mitigation strategies from the following.
- Process changes
- Contractual arrangements
- Resource allocation
- Insurance contracts
- Contingency plans
You must regularly monitor risks and control them. As a last step, maintain documentation of risks, their assessments and mitigation plans.
Start a career in investment banking
Risk management is a structured process. It identifies, assesses, and mitigates risks that carry the potential to derail a project from its objectives. Through this process, you can ensure the efficient utilisation of resources and protect your investment from failure. Learn more about the importance of risk management with our industry-recognised certification.
Imarticus Learning is a leading educational platform that offers investment banking courses with job-specific curricula. Explore our Certified Investment Banking Operations Professional program for your career growth in the world of investment banking!
Share This Post
Subscribe to our newsletter, get updates and learn from the best, more to explore.

Your Ultimate Guide to Becoming a Chartered Financial Analyst
Your ultimate guide to acca exam dates: stay ahead of the curve, our programs.

Certified Investment Banking Operations Professional

Chief Financial Officer Programme
Global Senior Leadership Programme Specialisation: Chief Finance Officer
Advanced Management Programme In Financial Services And Capital Markets

Senior Leadership Programme In Fintech

Chartered Financial Analyst (CFA)

Certified Management Accountant
Certified Public Accountant
Do you want to boost your career, drop us a message and keep in touch.

Keep In Touch
The state of AI in early 2024: Gen AI adoption spikes and starts to generate value
If 2023 was the year the world discovered generative AI (gen AI) , 2024 is the year organizations truly began using—and deriving business value from—this new technology. In the latest McKinsey Global Survey on AI, 65 percent of respondents report that their organizations are regularly using gen AI, nearly double the percentage from our previous survey just ten months ago. Respondents’ expectations for gen AI’s impact remain as high as they were last year , with three-quarters predicting that gen AI will lead to significant or disruptive change in their industries in the years ahead.
About the authors
This article is a collaborative effort by Alex Singla , Alexander Sukharevsky , Lareina Yee , and Michael Chui , with Bryce Hall , representing views from QuantumBlack, AI by McKinsey, and McKinsey Digital.
Organizations are already seeing material benefits from gen AI use, reporting both cost decreases and revenue jumps in the business units deploying the technology. The survey also provides insights into the kinds of risks presented by gen AI—most notably, inaccuracy—as well as the emerging practices of top performers to mitigate those challenges and capture value.
AI adoption surges
Interest in generative AI has also brightened the spotlight on a broader set of AI capabilities. For the past six years, AI adoption by respondents’ organizations has hovered at about 50 percent. This year, the survey finds that adoption has jumped to 72 percent (Exhibit 1). And the interest is truly global in scope. Our 2023 survey found that AI adoption did not reach 66 percent in any region; however, this year more than two-thirds of respondents in nearly every region say their organizations are using AI. 1 Organizations based in Central and South America are the exception, with 58 percent of respondents working for organizations based in Central and South America reporting AI adoption. Looking by industry, the biggest increase in adoption can be found in professional services. 2 Includes respondents working for organizations focused on human resources, legal services, management consulting, market research, R&D, tax preparation, and training.
Also, responses suggest that companies are now using AI in more parts of the business. Half of respondents say their organizations have adopted AI in two or more business functions, up from less than a third of respondents in 2023 (Exhibit 2).

Future frontiers: Navigating the next wave of tech innovations
Join Lareina Yee and Roger Roberts on Tuesday, July 30, at 12:30 p.m. EDT/6:30 p.m. CET as they discuss the future of these technological trends, the factors that will fuel their growth, and strategies for investing in them through 2024 and beyond.
Gen AI adoption is most common in the functions where it can create the most value
Most respondents now report that their organizations—and they as individuals—are using gen AI. Sixty-five percent of respondents say their organizations are regularly using gen AI in at least one business function, up from one-third last year. The average organization using gen AI is doing so in two functions, most often in marketing and sales and in product and service development—two functions in which previous research determined that gen AI adoption could generate the most value 3 “ The economic potential of generative AI: The next productivity frontier ,” McKinsey, June 14, 2023. —as well as in IT (Exhibit 3). The biggest increase from 2023 is found in marketing and sales, where reported adoption has more than doubled. Yet across functions, only two use cases, both within marketing and sales, are reported by 15 percent or more of respondents.
Gen AI also is weaving its way into respondents’ personal lives. Compared with 2023, respondents are much more likely to be using gen AI at work and even more likely to be using gen AI both at work and in their personal lives (Exhibit 4). The survey finds upticks in gen AI use across all regions, with the largest increases in Asia–Pacific and Greater China. Respondents at the highest seniority levels, meanwhile, show larger jumps in the use of gen Al tools for work and outside of work compared with their midlevel-management peers. Looking at specific industries, respondents working in energy and materials and in professional services report the largest increase in gen AI use.
Investments in gen AI and analytical AI are beginning to create value
The latest survey also shows how different industries are budgeting for gen AI. Responses suggest that, in many industries, organizations are about equally as likely to be investing more than 5 percent of their digital budgets in gen AI as they are in nongenerative, analytical-AI solutions (Exhibit 5). Yet in most industries, larger shares of respondents report that their organizations spend more than 20 percent on analytical AI than on gen AI. Looking ahead, most respondents—67 percent—expect their organizations to invest more in AI over the next three years.
Where are those investments paying off? For the first time, our latest survey explored the value created by gen AI use by business function. The function in which the largest share of respondents report seeing cost decreases is human resources. Respondents most commonly report meaningful revenue increases (of more than 5 percent) in supply chain and inventory management (Exhibit 6). For analytical AI, respondents most often report seeing cost benefits in service operations—in line with what we found last year —as well as meaningful revenue increases from AI use in marketing and sales.
Inaccuracy: The most recognized and experienced risk of gen AI use
As businesses begin to see the benefits of gen AI, they’re also recognizing the diverse risks associated with the technology. These can range from data management risks such as data privacy, bias, or intellectual property (IP) infringement to model management risks, which tend to focus on inaccurate output or lack of explainability. A third big risk category is security and incorrect use.
Respondents to the latest survey are more likely than they were last year to say their organizations consider inaccuracy and IP infringement to be relevant to their use of gen AI, and about half continue to view cybersecurity as a risk (Exhibit 7).
Conversely, respondents are less likely than they were last year to say their organizations consider workforce and labor displacement to be relevant risks and are not increasing efforts to mitigate them.
In fact, inaccuracy— which can affect use cases across the gen AI value chain , ranging from customer journeys and summarization to coding and creative content—is the only risk that respondents are significantly more likely than last year to say their organizations are actively working to mitigate.
Some organizations have already experienced negative consequences from the use of gen AI, with 44 percent of respondents saying their organizations have experienced at least one consequence (Exhibit 8). Respondents most often report inaccuracy as a risk that has affected their organizations, followed by cybersecurity and explainability.
Our previous research has found that there are several elements of governance that can help in scaling gen AI use responsibly, yet few respondents report having these risk-related practices in place. 4 “ Implementing generative AI with speed and safety ,” McKinsey Quarterly , March 13, 2024. For example, just 18 percent say their organizations have an enterprise-wide council or board with the authority to make decisions involving responsible AI governance, and only one-third say gen AI risk awareness and risk mitigation controls are required skill sets for technical talent.
Bringing gen AI capabilities to bear
The latest survey also sought to understand how, and how quickly, organizations are deploying these new gen AI tools. We have found three archetypes for implementing gen AI solutions : takers use off-the-shelf, publicly available solutions; shapers customize those tools with proprietary data and systems; and makers develop their own foundation models from scratch. 5 “ Technology’s generational moment with generative AI: A CIO and CTO guide ,” McKinsey, July 11, 2023. Across most industries, the survey results suggest that organizations are finding off-the-shelf offerings applicable to their business needs—though many are pursuing opportunities to customize models or even develop their own (Exhibit 9). About half of reported gen AI uses within respondents’ business functions are utilizing off-the-shelf, publicly available models or tools, with little or no customization. Respondents in energy and materials, technology, and media and telecommunications are more likely to report significant customization or tuning of publicly available models or developing their own proprietary models to address specific business needs.
Respondents most often report that their organizations required one to four months from the start of a project to put gen AI into production, though the time it takes varies by business function (Exhibit 10). It also depends upon the approach for acquiring those capabilities. Not surprisingly, reported uses of highly customized or proprietary models are 1.5 times more likely than off-the-shelf, publicly available models to take five months or more to implement.
Gen AI high performers are excelling despite facing challenges
Gen AI is a new technology, and organizations are still early in the journey of pursuing its opportunities and scaling it across functions. So it’s little surprise that only a small subset of respondents (46 out of 876) report that a meaningful share of their organizations’ EBIT can be attributed to their deployment of gen AI. Still, these gen AI leaders are worth examining closely. These, after all, are the early movers, who already attribute more than 10 percent of their organizations’ EBIT to their use of gen AI. Forty-two percent of these high performers say more than 20 percent of their EBIT is attributable to their use of nongenerative, analytical AI, and they span industries and regions—though most are at organizations with less than $1 billion in annual revenue. The AI-related practices at these organizations can offer guidance to those looking to create value from gen AI adoption at their own organizations.
To start, gen AI high performers are using gen AI in more business functions—an average of three functions, while others average two. They, like other organizations, are most likely to use gen AI in marketing and sales and product or service development, but they’re much more likely than others to use gen AI solutions in risk, legal, and compliance; in strategy and corporate finance; and in supply chain and inventory management. They’re more than three times as likely as others to be using gen AI in activities ranging from processing of accounting documents and risk assessment to R&D testing and pricing and promotions. While, overall, about half of reported gen AI applications within business functions are utilizing publicly available models or tools, gen AI high performers are less likely to use those off-the-shelf options than to either implement significantly customized versions of those tools or to develop their own proprietary foundation models.
What else are these high performers doing differently? For one thing, they are paying more attention to gen-AI-related risks. Perhaps because they are further along on their journeys, they are more likely than others to say their organizations have experienced every negative consequence from gen AI we asked about, from cybersecurity and personal privacy to explainability and IP infringement. Given that, they are more likely than others to report that their organizations consider those risks, as well as regulatory compliance, environmental impacts, and political stability, to be relevant to their gen AI use, and they say they take steps to mitigate more risks than others do.
Gen AI high performers are also much more likely to say their organizations follow a set of risk-related best practices (Exhibit 11). For example, they are nearly twice as likely as others to involve the legal function and embed risk reviews early on in the development of gen AI solutions—that is, to “ shift left .” They’re also much more likely than others to employ a wide range of other best practices, from strategy-related practices to those related to scaling.
In addition to experiencing the risks of gen AI adoption, high performers have encountered other challenges that can serve as warnings to others (Exhibit 12). Seventy percent say they have experienced difficulties with data, including defining processes for data governance, developing the ability to quickly integrate data into AI models, and an insufficient amount of training data, highlighting the essential role that data play in capturing value. High performers are also more likely than others to report experiencing challenges with their operating models, such as implementing agile ways of working and effective sprint performance management.
About the research
The online survey was in the field from February 22 to March 5, 2024, and garnered responses from 1,363 participants representing the full range of regions, industries, company sizes, functional specialties, and tenures. Of those respondents, 981 said their organizations had adopted AI in at least one business function, and 878 said their organizations were regularly using gen AI in at least one function. To adjust for differences in response rates, the data are weighted by the contribution of each respondent’s nation to global GDP.
Alex Singla and Alexander Sukharevsky are global coleaders of QuantumBlack, AI by McKinsey, and senior partners in McKinsey’s Chicago and London offices, respectively; Lareina Yee is a senior partner in the Bay Area office, where Michael Chui , a McKinsey Global Institute partner, is a partner; and Bryce Hall is an associate partner in the Washington, DC, office.
They wish to thank Kaitlin Noe, Larry Kanter, Mallika Jhamb, and Shinjini Srivastava for their contributions to this work.
This article was edited by Heather Hanselman, a senior editor in McKinsey’s Atlanta office.
Explore a career with us
Related articles.

Moving past gen AI’s honeymoon phase: Seven hard truths for CIOs to get from pilot to scale

A generative AI reset: Rewiring to turn potential into value in 2024
Implementing generative AI with speed and safety
2022 was the year that generative artificial intelligence (AI) exploded into the public consciousness, and 2023 was the year it began to take root in the business world. 2024 thus stands to be a pivotal year for the future of AI, as researchers and enterprises seek to establish how this evolutionary leap in technology can be most practically integrated into our everyday lives.
The evolution of generative AI has mirrored that of computers, albeit on a dramatically accelerated timeline. Massive, centrally operated mainframe computers from a few players gave way to smaller, more efficient machines accessible to enterprises and research institutions. In the decades that followed, incremental advances yielded home computers that hobbyists could tinker with. In time, powerful personal computers with intuitive no-code interfaces became ubiquitous.
Generative AI has already reached its “hobbyist” phase—and as with computers, further progress aims to attain greater performance in smaller packages. 2023 saw an explosion of increasingly efficient foundation models with open licenses, beginning with the launch of Meta’s LlaMa family of large language models (LLMs) and followed by the likes of StableLM, Falcon, Mistral, and Llama 2 . DeepFloyd and Stable Diffusion have achieved relative parity with leading proprietary models. Enhanced with fine-tuning techniques and datasets developed by the open source community, many open models can now outperform all but the most powerful closed-source models on most benchmarks, despite far smaller parameter counts.
As the pace of progress accelerates, the ever-expanding capabilities of state-of-the-art models will garner the most media attention. But the most impactful developments may be those focused on governance, middleware, training techniques and data pipelines that make generative AI more trustworthy , sustainable and accessible, for enterprises and end users alike.
Here are some important current AI trends to look out for in the coming year.
Reality check: more realistic expectations
- Multimodal AI
Small(er) language models and open source advancements
Gpu shortages and cloud costs, model optimization is getting more accessible, customized local models and data pipelines, more powerful virtual agents, regulation, copyright and ethical ai concerns, shadow ai (and corporate ai policies).
When generative AI first hit mass awareness, a typical business leader’s knowledge came mostly from marketing materials and breathless news coverage. Tangible experience (if any) was limited to messing around with ChatGPT and DALL-E. Now that the dust has settled, the business community now has a more refined understanding of AI-powered solutions.
The Gartner Hype Cycle positions Generative AI squarely at “Peak of Inflated Expectations,” on the cusp of a slide into the “Trough of Disillusionment” [1] —in other words, about to enter a (relatively) underwhelming transition period—while Deloitte’s “State of Generated AI in the Enterprise “ report from Q1 2024 indicated that many leaders “expect substantial transformative impacts in the short term.” [2] The reality will likely fall in between: generative AI offers unique opportunities and solutions, but it will not be everything to everyone.
How real-world results compare to the hype is partially a matter of perspective. Standalone tools like ChatGPT typically take center stage in the popular imagination, but smooth integration into established services often yields more staying power. Prior to the current hype cycle, generative machine learning tools like the “Smart Compose” feature rolled out by Google in 2018 weren’t heralded as a paradigm shift, despite being harbingers of today’s text generating services. Similarly, many high-impact generative AI tools are being implemented as integrated elements of enterprise environments that enhance and complement, rather than revolutionize or replace, existing tools: for example, “Copilot” features in Microsoft Office, “Generative Fill” features in Adobe Photoshop or virtual agents in productivity and collaboration apps .
Where generative AI first builds momentum in everyday workflows will have more influence on the future of AI tools than the hypothetical upside of any specific AI capabilities. According to a recent IBM survey of over 1,000 employees at enterprise-scale companies , the top three factors driving AI adoption were advances in AI tools that make them more accessible, the need to reduce costs and automate key processes and the increasing amount of AI embedded into standard off-the-shelf business applications.
Multimodal AI (and video)
That being said, the ambition of state-of-the-art generative AI is growing. The next wave of advancements will focus not only on enhancing performance within a specific domain, but on multimodal models that can take multiple types of data as input. While models that operate across different data modalities are not a strictly new phenomenon—text-to-image models like CLIP and speech-to-text models like Wave2Vec have been around for years now—they’ve typically only operated in one direction, and were trained to accomplish a specific task.
The incoming generation of interdisciplinary models, comprising proprietary models like OpenAI’s GPT-4V or Google’s Gemini, as well as open source models like LLaVa, Adept or Qwen-VL, can move freely between natural language processing (NLP) and computer vision tasks. New models are also bringing video into the fold: in late January, Google announced Lumiere, a text-to-video diffusion model that can also perform image-to-video tasks or use images for style reference.
The most immediate benefit of multimodal AI is more intuitive, versatile AI applications and virtual assistants. Users can, for example, ask about an image and receive a natural language answer, or ask out loud for instructions to repair something and receive visual aids alongside step-by-step text instructions.
On a higher level, multimodal AI allows for a model to process more diverse data inputs, enriching and expanding the information available for training and inference. Video, in particular, offers great potential for holistic learning. “There are cameras that are on 24/7 and they’re capturing what happens just as it happens without any filtering, without any intentionality,” says Peter Norvig, Distinguished Education Fellow at the Stanford Institute for Human-Centered Artificial Intelligence (HAI). [3] “AI models haven’t had that kind of data before. Those models will just have a better understanding of everything.”
In domain-specific models—particularly LLMs—we’ve likely reached the point of diminishing returns from larger parameter counts. Sam Altman, CEO of OpenAI (whose GPT-4 model is rumored to have around 1.76 trillion parameters), suggested as much at MIT’s Imagination in Action event last April: “I think we’re at the end of the era where it’s going to be these giant models, and we’ll make them better in other ways,” he predicted. “I think there’s been way too much focus on parameter count.”
Massive models jumpstarted this ongoing AI golden age, but they’re not without drawbacks. Only the very largest companies have the funds and server space to train and maintain energy-hungry models with hundreds of billions of parameters. According to one estimate from the University of Washington, training a single GPT-3-sized model requires the yearly electricity consumption of over 1,000 households; a standard day of ChatGPT queries rivals the daily energy consumption of 33,000 U.S. households. [4]
Smaller models, meanwhile, are far less resource-intensive. An influential March 2022 paper from Deepmind demonstrated that training smaller models on more data yields better performance than training larger models on fewer data. Much of the ongoing innovation in LLMs has thus focused on yielding greater output from fewer parameters. As demonstrated by recent progress of models in the 3–70 billion parameter range, particularly those built upon LLaMa, Llama 2 and Mistral foundation models in 2023, models can be downsized without much performance sacrifice.
The power of open models will continue to grow. In December of 2023, Mistral released “Mixtral,” a mixture of experts (MoE) model integrating 8 neural networks, each with 7 billion parameters. Mistral claims that Mixtral not only outperforms the 70B parameter variant of Llama 2 on most benchmarks at 6 times faster inference speeds, but that it even matches or outperforms OpenAI’s far larger GPT-3.5 on most standard benchmarks. Shortly thereafter, Meta announced in January that it has already begun training of Llama 3 models, and confirmed that they will be open sourced. Though details (like model size) have not been confirmed, it’s reasonable to expect Llama 3 to follow the framework established in the two generations prior.
These advances in smaller models have three important benefits:
- They help democratize AI: smaller models that can be run at lower cost on more attainable hardware empower more amateurs and institutions to study, train and improve existing models.
- They can be run locally on smaller devices: this allows more sophisticated AI in scenarios like edge computing and the internet of things (IoT). Furthermore, running models locally—like on a user’s smartphone—helps to sidestep many privacy and cybersecurity concerns that arise from interaction with sensitive personal or proprietary data.
- They make AI more explainable: the larger the model, the more difficult it is to pinpoint how and where it makes important decisions. Explainable AI is essential to understanding, improving and trusting the output of AI systems.
The trend toward smaller models will be driven as much by necessity as by entrepreneurial vigor, as cloud computing costs increase as the availability of hardware decrease.
“The big companies (and more of them) are all trying to bring AI capabilities in-house, and there is a bit of a run on GPUs,” says James Landay, Vice-Director and Faculty Director of Research, Stanford HAI. “This will create a huge pressure not only for increased GPU production, but for innovators to come up with hardware solutions that are cheaper and easier to make and use.” 1
As a late 2023 O’Reilly report explains, cloud providers currently bear much of the computing burden: relatively few AI adopters maintain their own infrastructure, and hardware shortages will only elevate the hurdles and costs of setting up on-premise servers. In the long term, this may put upward pressure on cloud costs as providers update and optimize their own infrastructure to effectively meet demand from generative AI. [5]
For enterprises, navigating this uncertain landscape requires flexibility, in terms of both models–leaning on smaller, more efficient models where necessary or larger, more performant models when practical–and deployment environment. “We don’t want to constrain where people deploy [a model],” said IBM CEO Arvind Krishna in a December 2023 interview with CNBC , in reference to IBM’s watsonx platform. “So [if] they want to deploy it on a large public cloud, we’ll do it there. If they want to deploy it at IBM, we’ll do it at IBM. If they want to do it on their own, and they happen to have enough infrastructure, we’ll do it there.”
The trend towards maximizing the performance of more compact models is well served by the recent output of the open source community.
Many key advancements have been (and will continue to be) driven not just by new foundation models, but by new techniques and resources (like open source datasets) for training, tweaking, fine-tuning or aligning pre-trained models. Notable model-agnostic techniques that took hold in 2023 include:
- Low Rank Adaptation (LoRA): Rather than directly fine-tuning billions of model parameters, LoRA entails freezing pre-trained model weights and injecting trainable layers—which represent the matrix of changes to model weights as 2 smaller ( lower rank ) matrices—in each transformer block. This dramatically reduces the number of parameters that need to be updated, which, in turn, dramatically speeds up fine-tuning and reduces memory needed to store model updates.
- Quantization: Like lowering the bitrate of audio or video to reduce file size and latency, quantization lowers the precision used to represent model data points—for example, from 16-bit floating point to 8-bit integer—to reduce memory usage and speed up inference. QLoRA techniques combine quantization with LoRA.
- Direct Preference Optimization (DPO): Chat models typically use reinforcement learning from human feedback (RLHF) to align model outputs to human preferences. Though powerful, RLHF is complex and unstable. DPO promises similar benefits while being computationally lightweight and substantially simpler.
Alongside parallel advances in open source models in the 3–70 billion parameter space, these evolving techniques could shift the dynamics of the AI landscape by providing smaller players, like startups and amateurs, with sophisticated AI capabilities that were previously out of reach.
Enterprises in 2024 can thus pursue differentiation through bespoke model development, rather than building wrappers around repackaged services from “Big AI.” With the right data and development framework , existing open source AI models and tools can be tailored to almost any real-world scenario, from customer support uses to supply chain management to complex document analysis.
Open source models afford organizations the opportunity to develop powerful custom AI models—trained on their proprietary data and fine-tuned for their specific needs—quickly, without prohibitively expensive infrastructure investments. This is especially relevant in domains like legal, healthcare or finance, where highly specialized vocabulary and concepts may not have been learned by foundation models in pre-training.
Legal, finance and healthcare are also prime examples of industries that can benefit from models small enough to be run locally on modest hardware. Keeping AI training, inference and retrieval augmented generation (RAG) local avoids the risk of proprietary data or sensitive personal information being used to train closed-source models or otherwise pass through the hands of third parties. And using RAG to access relevant information rather than storing all knowledge directly within the LLM itself helps reduce model size, further increasing speed and reducing costs.
As 2024 continues to level the model playing field, competitive advantage will increasingly be driven by proprietary data pipelines that enable industry-best fine-tuning.
With more sophisticated, efficient tools and a year’s worth of market feedback at their disposal, businesses are primed to expand the use cases for virtual agents beyond just straightforward customer experience chatbots .
As AI systems speed up and incorporate new streams and formats of information, they expand the possibilities for not just communication and instruction following, but also task automation. “2023 was the year of being able to chat with an AI. Multiple companies launched something, but the interaction was always you type something in and it types something back,” says Stanford’s Norvig. “In 2024, we’ll see the ability for agents to get stuff done for you . Make reservations, plan a trip, connect to other services.”
Multimodal AI, in particular, significantly increases opportunities for seamless interaction with virtual agents. For example, rather than simply asking a bot for recipes, a user can point a camera at an open fridge and request recipes that can be made with available ingredients. Be My Eyes, a mobile app that connects blind and low vision individuals with volunteers to help with quick tasks, is piloting AI tools that help users directly interact with their surroundings through multimodal AI in lieu of awaiting a human volunteer.
Explore IBM watsonx™ Assistant: market-leading conversational AI with seamless integration for the tools that power your business →
Elevated multimodal capabilities and lowered barriers to entry also open up new doors for abuse: deepfakes, privacy issues, perpetuation of bias and even evasion of CAPTCHA safeguards may become increasingly easy for bad actors. In January of 2024, a wave of explicit celebrity deepfakes hit social media; research from May 2023 indicated that there had been 8 times as many voice deepfakes posted online compared to the same period in 2022. [6]
Ambiguity in the regulatory environment may slow adoption, or at least more aggressive implementation, in the short to medium term. There is inherent risk to any major, irreversible investment in an emerging technology or practice that might require significant retooling—or even become illegal—following new legislation or changing political headwinds in the coming years.
In December 2023, the European Union (EU) reached provisional agreement on the Artificial Intelligence Act . Among other measures, it prohibits indiscriminate scraping of images to create facial recognition databases, biometric categorization systems with potential for discriminatory bias, “social scoring” systems and the use of AI for social or economic manipulation. It also seeks to define a category of “high-risk” AI systems, with potential to threaten safety, fundamental rights or rule of law, that will be subject to additional oversight. Likewise, it sets transparency requirements for what it calls “general-purpose AI (GPAI)” systems—foundation models—including technical documentation and systemic adversarial testing.
But while some key players, like Mistral, reside in the EU, the majority of groundbreaking AI development is happening in America, where substantive legislation of AI in the private sector will require action from Congress—which may be unlikely in an election year. On October 30, the Biden administration issued a comprehensive executive order detailing 150 requirements for use of AI technologies by federal agencies; months prior, the administration secured voluntary commitments from prominent AI developers to adhere to certain guardrails for trust and security. Notably, both California and Colorado are actively pursuing their own legislation regarding individuals’ data privacy rights with regard to artificial intelligence.
China has moved more proactively toward formal AI restrictions, banning price discrimination by recommendation algorithms on social media and mandating the clear labeling of AI-generated content. Prospective regulations on generative AI seek to require the training data used to train LLMs and the content subsequently generated by models must be “true and accurate,” which experts have taken to indicate measures to censor LLM output.
Meanwhile, the role of copyrighted material in the training of AI models used for content generation, from language models to image generators and video models, remains a hotly contested issue. The outcome of the high-profile lawsuit filed by the New York Times against OpenAI may significantly affect the trajectory of AI legislation. Adversarial tools, like Glaze and Nightshade —both developed at the University of Chicago—have arisen in what may become an arms race of sorts between creators and model developers.
Learn how IBM® watsonx.governance™ accelerates responsible, transparent and explainable AI workflows →
For businesses, this escalating potential for legal, regulatory, economic or reputational consequences is compounded by how popular and accessible generative AI tools have become. Organizations must not only have a careful, coherent and clearly articulated corporate policy around generative AI, but also be wary of shadow AI: the “unofficial” personal use of AI in the workplace by employees.
Also dubbed “shadow IT” or “BYOAI,” shadow AI arises when impatient employees seeking quick solutions (or simply wanting to explore new tech faster than a cautious company policy allows) implement generative AI in the workplace without going through IT for approval or oversight. Many consumer-facing services, some free of charge, allow even nontechnical individuals to improvise the use of generative AI tools. In one study from Ernst & Young, 90% of respondents said they use AI at work. [7]
That enterprising spirit can be great, in a vacuum—but eager employees may lack relevant information or perspective regarding security, privacy or compliance. This can expose businesses to a great deal of risk. For example, an employee might unknowingly feed trade secrets to a public-facing AI model that continually trains on user input, or use copyright-protected material to train a proprietary model for content generation and expose their company to legal action.
Like many ongoing developments, this underscores how the dangers of generative AI rise almost linearly with its capabilities. With great power comes great responsibility.
Moving forward
As we proceed through a pivotal year in artificial intelligence, understanding and adapting to emerging trends is essential to maximizing potential, minimizing risk and responsibly scaling generative AI adoption.
1 “Gartner Places Generative AI on the Peak of Inflated Expectations on the 2023 Hype Cycle for Emerging Technologies,” Gartner, 16 August 2023
2 ”Deloitte’s State of Generative AI in the Enteprrise Quarter one report,” Deloitte, January 2024
3 ”What to Expect in AI in 2024,” Stanford University, 8 December 2023
4 ”Q&A: UW researcher discusses just how much energy ChatGPT uses,” University of Washington, 27 July 2023
5 “Generative AI in the Enterprise,” O’Reilly, 28 November 2023
6 ”Deepfaking it: America’s 2024 election coincides with AI boom,” Reuters, 30 May 2023
7 ”How organizations can stop skyrocketing AI use from fueling anxiety,” Ernst & Young, December 2023
More from Artificial intelligence
Introducing probable root cause: enhancing instana’s observability.
3 min read - We are thrilled to announce an enhancement to Instana® with the introduction of the probable root cause capability, now available in public preview starting from release 277. This capability delivers superior insights, allowing quick identification of the source of a system fault—with little to no investigation time. Probable root cause Working with IBM Research®, we designed an algorithm that use causal AI and differential observability to analyze data modalities such as traces and topology to identify unhealthy entities after an…
Self-service that delights customers: How the IBM Partner Ecosystem is harnessing generative AI assistants in the banking and financial sectors
4 min read - Thanks to the transformative benefits promised by generative artificial intelligence (AI), the banking and financial sectors are at a turning point. From redefining a bank’s competitive edge in customer relationships to streamlining core banking operations and strengthening cyber-resiliency, AI technologies can unlock numerous new capabilities. Institutions are already seizing the opportunity. The 2024 Global Outlook for Banking and Financial Markets from the IBM Institute for Business Value (IBM IBV) revealed that 78% of the 600 executives surveyed tactically deploy generative…
Meta releases new Llama 3.1 models, including highly anticipated 405B parameter variant
7 min read - On Tuesday, July 23, Meta announced the launch of the Llama 3.1 collection of multilingual large language models (LLMs). Llama 3.1 comprises both pretrained and instruction-tuned text in/text out open source generative AI models in sizes of 8B, 70B and—for the first time—405B parameters. The instruction-tuned Llama 3.1-405B, which figures to be the largest and most powerful open source language model available today and competitive with the best proprietary models on the market, will be available on IBM® watsonx.ai™ today where…
IBM Newsletters

IMAGES
VIDEO
COMMENTS
4 Reasons Why Risk Management Is Important. 1. Protects Organization's Reputation. In many cases, effective risk management proactively protects your organization from incidents that can affect its reputation. "Franchise risk is a concern for all businesses," Simons says in Strategy Execution. "However, it's especially pressing for ...
Managing Risks: A New Framework. Smart companies match their approach to the nature of the threats they face. Summary. Risk management is too often treated as a compliance issue that can be solved ...
How do different organisations use Predict! to manage their risks and opportunities? Read our risk management case studies to learn from their experiences and insights. Find out how Predict! helps them to achieve their strategic objectives, deliver projects on time and budget, and improve their risk culture.
The theoretical aspects of risk management are crucial, but seeing them applied in real-world scenarios brings the concepts to life. Here are two case studies that showcase how Project Managers identified, assessed, and mitigated risks to achieve project success: Case Study 1: Launching a New Software Product.
Establishing an enterprise risk management (ERM) system is widely viewed as providing firms with the tools and processes needed to build resilience and expertise, enabling them to manage the consequences of crises that have led to the collapse of major firms across different industries globally. Intended for use in advanced accounting, auditing, and finance courses, this case study (of a true ...
Risk Management―The Revealing Hand. by Robert S. Kaplan and Anette Mikes. This article explores the role, organization, and limitations of risk identification and risk management, especially in situations that are not amenable to quantitative risk modeling. It argues that firms can avoid the artificial choice between quantitative and ...
The purpose of this effort is to develop an Emergency and Risk Management Case Studies Textbook designed to provide a resource for practitioners and students in the crisis, disaster, and risk management disciplines that displays various best practices, lessons learned, and success stories, through in-depth case studies.
Once the risk is identified it is documented in detail; subsequently the concerned stakeholders undertake possible risk management and mitigation processes. A comprehensive review of the situation and critical feedback are usually required that may ultimately lead to changes in the organizational polices and structures; particularly in case of ...
Risk is an effect, in terms of a positive or negative deviation from expected outcomes, resulting from uncertainty (ISO 31000, 2018), that can affect economic performance, business continuity, reputation, and environmental and social outcomes of an organization.Risk management (RM) supports companies in achieving their goals, exploring new opportunities, and reducing potential losses in an ...
global financial crisis. The concern is that top-down risk management will inhibit innovation and entrepreneurial activities. We disagree and argue that risk management should function as a Revealing Hand to identify, assess, and mitigat risks in a cost- e efficient manner. Done well, the Revealing Hand of risk management adds value to firms
of the year 2019. The outcome of the study will act as a risk management tool for project managers, principal investigators, grant writers and to Horizon 2020 pro-ject administrators. 1.2 Objectives and research questions The main aim of this thesis is to study risk and risk mitigation actions in project management.
5 Project Risk Management Case Studies. It is now high time to approach the practical side of project risk management. This section provides selected five case studies that explain the need and application of project risk management. Each case study gives an individual approach revealing how risk management can facilitate success of the project.
Purpose. The purpose of this study is to examine how managers in financial institutions satisfy themselves of the effectiveness of risk mitigation strategy and management control. It studies the co-opting of accounting tools within a single financial institution case study, examining the recursive and emergent characteristics of risk management ...
Company A: Case Study in Risk Management Excellence. Now, let's take a look at a case study that highlights risk management excellence in practice. ApexTech Solutions is a company known for its exemplary risk management practices. Founded in 2005 by visionary entrepreneur Sarah Lawson, ApexTech began as a small start-up in the tech industry.
Risk mitigation is the process of understanding certain risks and threats, accepting that they exist, and taking the appropriate measures to reduce their effects in case they happen. It is a part of the risk management process and is necessary to prepare an organization for any threats to its operations and processes.
The Study investigated to acquire an overall idea about risk and its consequences in construction field and the process required for its management. The effect of risk on assessment of a project ...
In these studies, mixed adherence to the RNR-principles in risk management plans was found, indicating the gap between assessment and management. An alternative method of evaluating risk management plans could be a quality rating scale, such as the Quality Checklist for Case Formulation (McMurran & Bruford, Citation 2016). Future studies should ...
This work provides a general risk management procedure applied to synchronized supply chains. After conducting a literature review and taking the international standard ISO 28000 and ISO 31000 as a reference. The most important steps that enable organizations to carry out supply chain risk management are described. Steps such as defining the context, identifying and analyzing risks or avoiding ...
Steps were taken to reduce dust and vibration during construction and install devices to reduce EMI during the elevator's operation. Plans were made to migrate racks 90 degrees, allowing for hot aisle/cold aisle operation. Cabinet doors were changed to grills to improve airflow and cooling. Business Resiliency Assessment and Planning. Case STudy.
ges. It is an integral element of management. based on a holistic approach to risk, i.e. risk. is a collection of many di erent factors .". Szczepaniak (2013) distinguishes four . steps in the ...
Applies risk management principles to the respective portfolio, program, and project management performance domains within the context of an enterprise risk management (ERM) approach, using examples and a working case study; and; Contains information for practitioners applying risk management techniques, tools, processes, and good practices ...
Risk mitigation is an important step in risk management that includes identifying the risk, assessing the risk, and mitigating the risk. Risk mitigation can be defined as taking steps to reduce or minimize risks. When you devise a strategy for reducing prospective risks and working with an action plan, it is important that you choose a strategy ...
Chipotle Case Study: Either Manage Risk or Disclose Lack of Risk Management. Back in 2009, we blogged about the SEC's decision to require board-level accountability for ERM. This decision was based on the conclusion that inadequate risk management allowed the regulatory failures that ultimately led to the financial crisis.
By implementing effective risk management practices, organisations can navigate challenges. Also, they can increase their chances of achieving their goals. Thus, understanding the importance of risk management is crucial for ensuring the success and sustainability of any venture. Performing risk management involves the following steps. Assess ...
Gen AI high performers are also much more likely to say their organizations follow a set of risk-related best practices (Exhibit 11). For example, they are nearly twice as likely as others to involve the legal function and embed risk reviews early on in the development of gen AI solutions—that is, to "shift left." They're also much more ...
In one study from Ernst & Young, 90% of respondents said they use AI at work. That enterprising spirit can be great, in a vacuum—but eager employees may lack relevant information or perspective regarding security, privacy or compliance. This can expose businesses to a great deal of risk.